Impersonating the Kingpin: Inside the Fake Sinaloa Hitman Empire
The Sinaloa Cartel is one of the most dominant and resilient criminal organizations in the world. Originating in the Mexican state of Sinaloa, the group evolved from a small smuggling network into a major global enterprise. Under the leadership of figures such as Joaquín “El Chapo” Guzmán and Ismael “El Mayo” Zambada, it built a large-scale infrastructure for the trafficking of cocaine, heroin, methamphetamine, and fentanyl into international markets. Unlike many other Mexican cartels that fractured under pressure, the Sinaloa organization maintained its influence through adaptability, internal discipline, and deep connections within political and law enforcement structures.
Beyond its criminal operations, the cartel’s name itself has become a brand. “Sinaloa” carries a reputation for power, reach, and secrecy, representing decades of successful evasion and dominance in the drug trade. The cartel’s legacy has extended far beyond Mexico, shaping how organized crime is perceived globally. Its leaders, networks, and methods are frequently referenced in academic studies, law enforcement briefings, and popular media, contributing to a public image that blends fact, myth, and fear.
As online criminal ecosystems expanded, the Sinaloa identity began appearing across digital platforms in unexpected ways. The name has increasingly been used by unaffiliated actors who exploit its popularity to build credibility or attract attention. On dark web forums and marketplaces, the term “Sinaloa Cartel” often serves as a brand identifier for illicit services, whether genuine or fabricated. This growing trend of brand exploitation provided the backdrop for StealthMole’s investigation, which focused on identifying and analyzing a network of websites that claimed to operate under the Sinaloa Cartel’s name.
Incident Trigger and Initial Investigation
The investigation was initiated after the appearance of a dark web marketplace operating under the name “Sinaloa Cartel Marketplace.” The use of the Sinaloa name on dark web platforms was notable, as the cartel has historically relied on secrecy and trusted intermediaries rather than public-facing platforms. The marketplace presented itself as a service provider for violent contracts, advertising offerings such as assassination, assault, and arson. Its design and language appeared structured and deliberate, suggesting an attempt to build trust among potential users by associating with one of the world’s most recognizable criminal brands.
Using StealthMole’s dark web tracker, the domain was identified and reviewed. Historical indexing showed that the site was first detected in September 2023 and remained active until at least April 2025. The captured snapshots revealed a structured interface with categories labeled “Murder,” “Assault,” “Kidnapping,” and “Weapons,” along with promotional text that promised secure transactions through Bitcoin payments. The page design also included visuals referencing Joaquín “El Chapo” Guzmán and the Sinaloa Cartel, presumably to strengthen its criminal credibility.
- Sinolaicgivwfmh5z5ouhqexr6e5naxbwydbgmlw6bfr46za4ywdajyd.onion
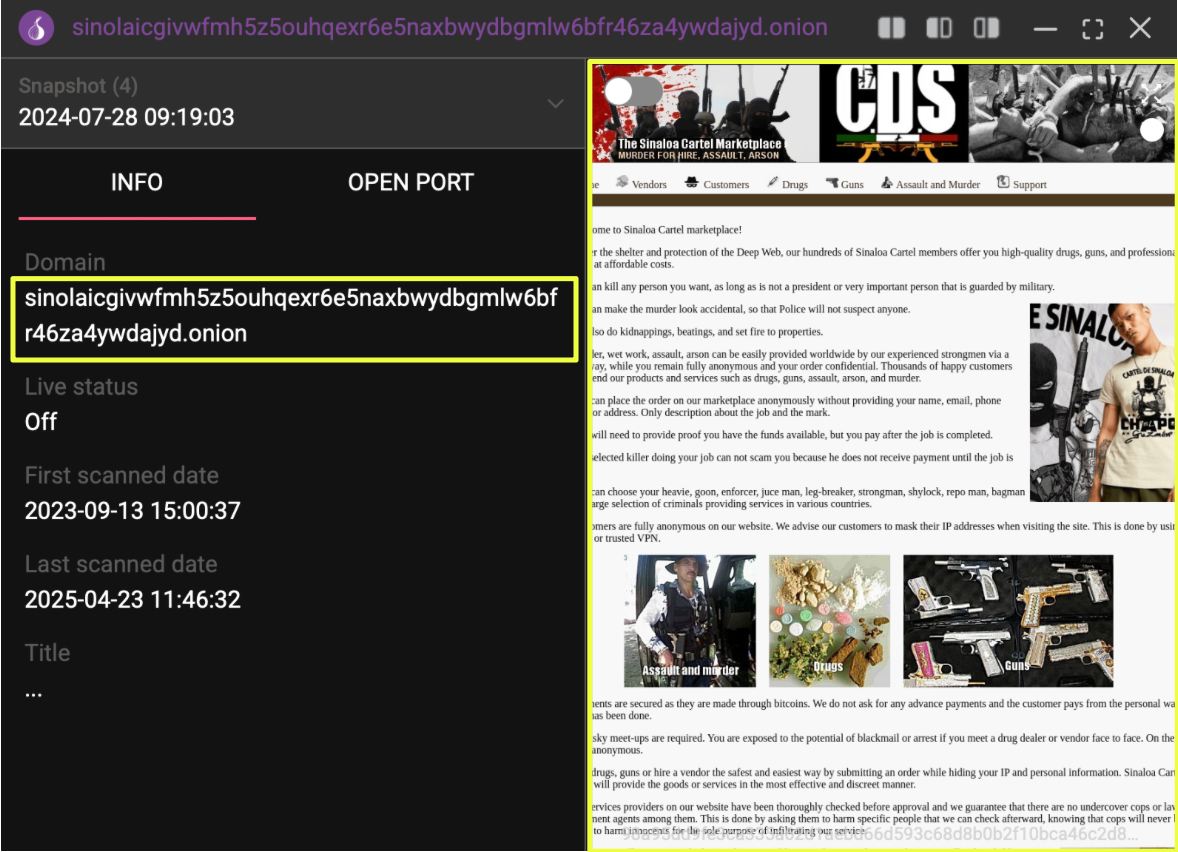
The unusual presentation of a globally recognized cartel name on an openly indexed darkweb marketplace prompted a deeper investigation. Through StealthMole, further contact information was discovered, including sin****@dnmx.su and sin****@dnmx.org, as well as references to a secondary domain, sinolamnqipocijd.onion, which records show was active as early as December 2020. These initial findings suggested that the so-called marketplace was not a recent creation but rather part of a longer-running digital infrastructure that repeatedly resurfaced under different domains yet the same name.
Infrastructure Discovery and Expansion
As the investigation progressed, StealthMole was used to trace the broader infrastructure behind the so-called Sinaloa Cartel Marketplace. This analysis revealed that the marketplace did not exist in isolation but was part of a network of interconnected domains that had appeared and disappeared across several years. Each domain replicated the same design, text, and imagery, indicating a deliberate effort to maintain continuity and preserve credibility among potential users even as individual sites went offline.
One of the earliest related domains, sinolamnqipocijd.onion, was first recorded in December 2020, marking the earliest known instance of this operation. Later versions, including sinolaicgivwfmh5z5ouhqexr6e5naxbwydbgmlw6bfr46za4ywdajyd.onion, remained active between September 2023 and April 2025. Three additional mirrors were also identified and confirmed active until July 2025. All of these domains listed the same contact address, sin****@dnmx.su, suggesting a single operator or coordinated management.
- Sinolamoejhjauat5wyjjnsf5zxk5bfftysqw7z6scbrlecxayoao5yd.onion
- Sinolaiawv52eel4dawsfzlg3svskwgfnee6gq6mkci2dzahbbgx5sad.onion
- Sinolags7muomccqtxt375e2pvvclkqedqo5rbzqh4lo2vzwyehpshid.onion
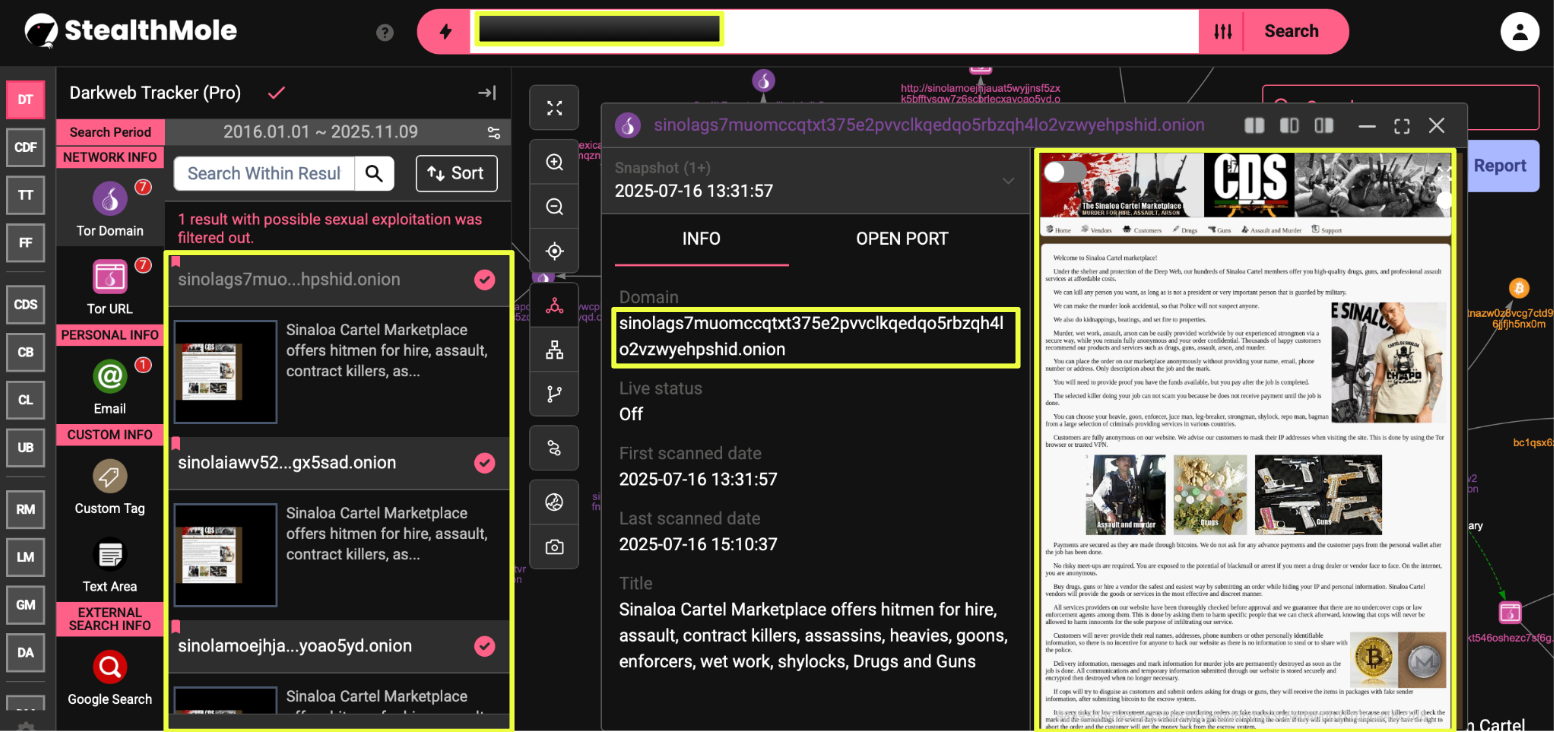
Further examination revealed additional contact variants, including sin***@dnmx.org and sin****@dnmx.cc, which appeared on later mirrors. The transition between these email addresses indicated an effort to maintain operational continuity while evading blacklisting or takedowns. A related site was discovered using the sin****@dnmx.cc address but contained identical content and layout, implying that it was part of the same network operating under a different name. Across all versions, the same photograph of a man wearing a “Cartel de Sinaloa” T-shirt appeared consistently, functioning as a recognizable visual marker for the marketplace’s supposed identity.
- mafia*************************************************4id.onion
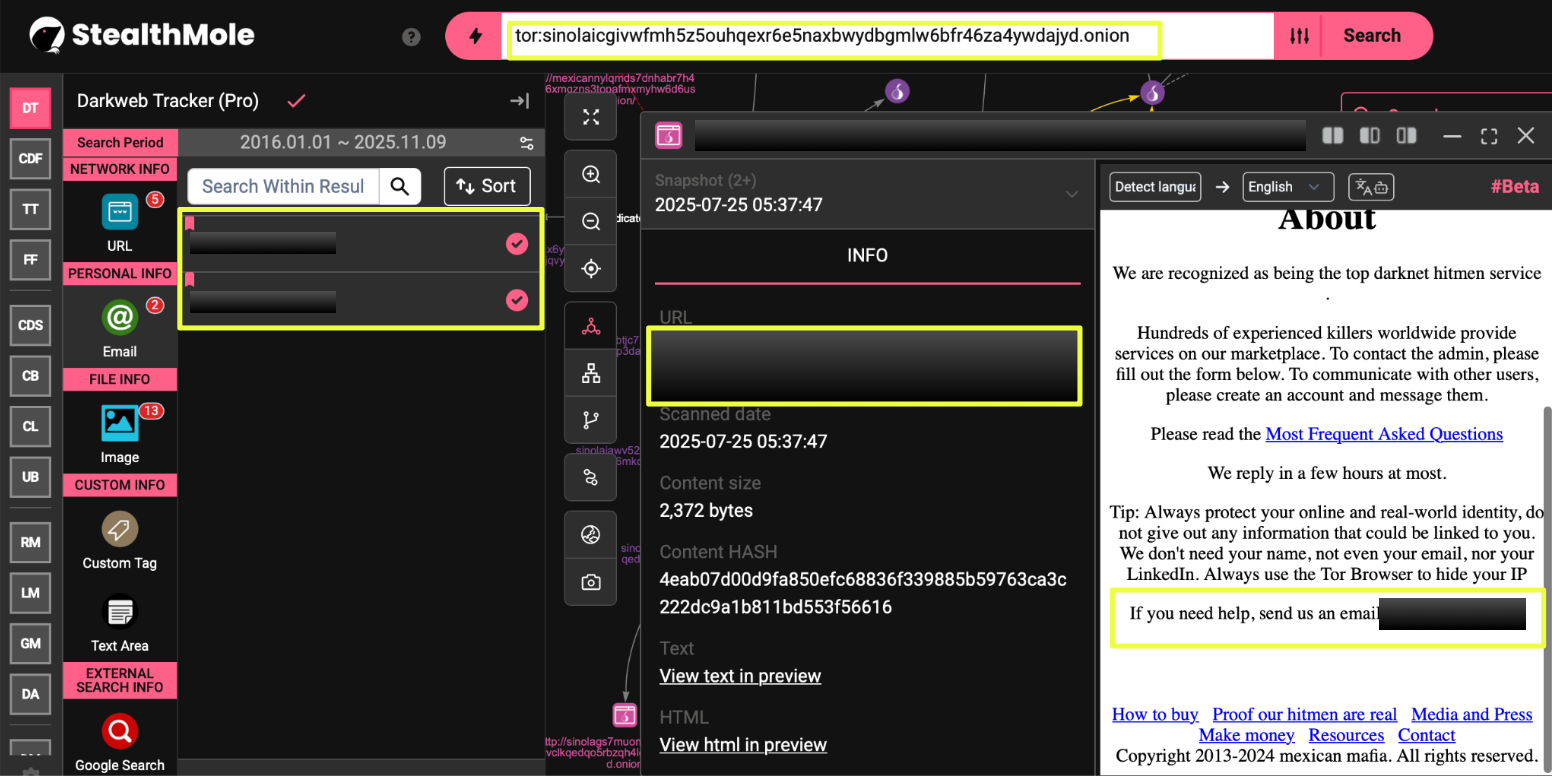
The continuity across these domains, combined with the identical design and communication pattern, suggested that the operation was managed by a single actor or small group rather than an organized criminal organization of the Sinaloa Cartel’s scale. Despite repeated rebranding and migration, the underlying infrastructure, language, and imagery remained consistent, indicating a sustained attempt to impersonate the cartel rather than represent it.
Emergence of New Domains
By mid-2025, additional mirrors of the Sinaloa-branded marketplace began to appear, extending the network’s lifespan beyond earlier estimates. Three new domains were identified. Each site replicated the same layout, imagery, and text found on the earlier versions, indicating that the operators continued to reuse identical templates while rotating hosting environments.
- Xvzkf3mpltwzjne6ybto435okoko27jk7pqc52quzwflmtf5kf3e4byd.onion
- Z63z52bb7strnr3dscguymqvfddaiojpkp5bhpk64f5rcubdrfm2uwqd.onion
- jgs7l************************************************6id.onion
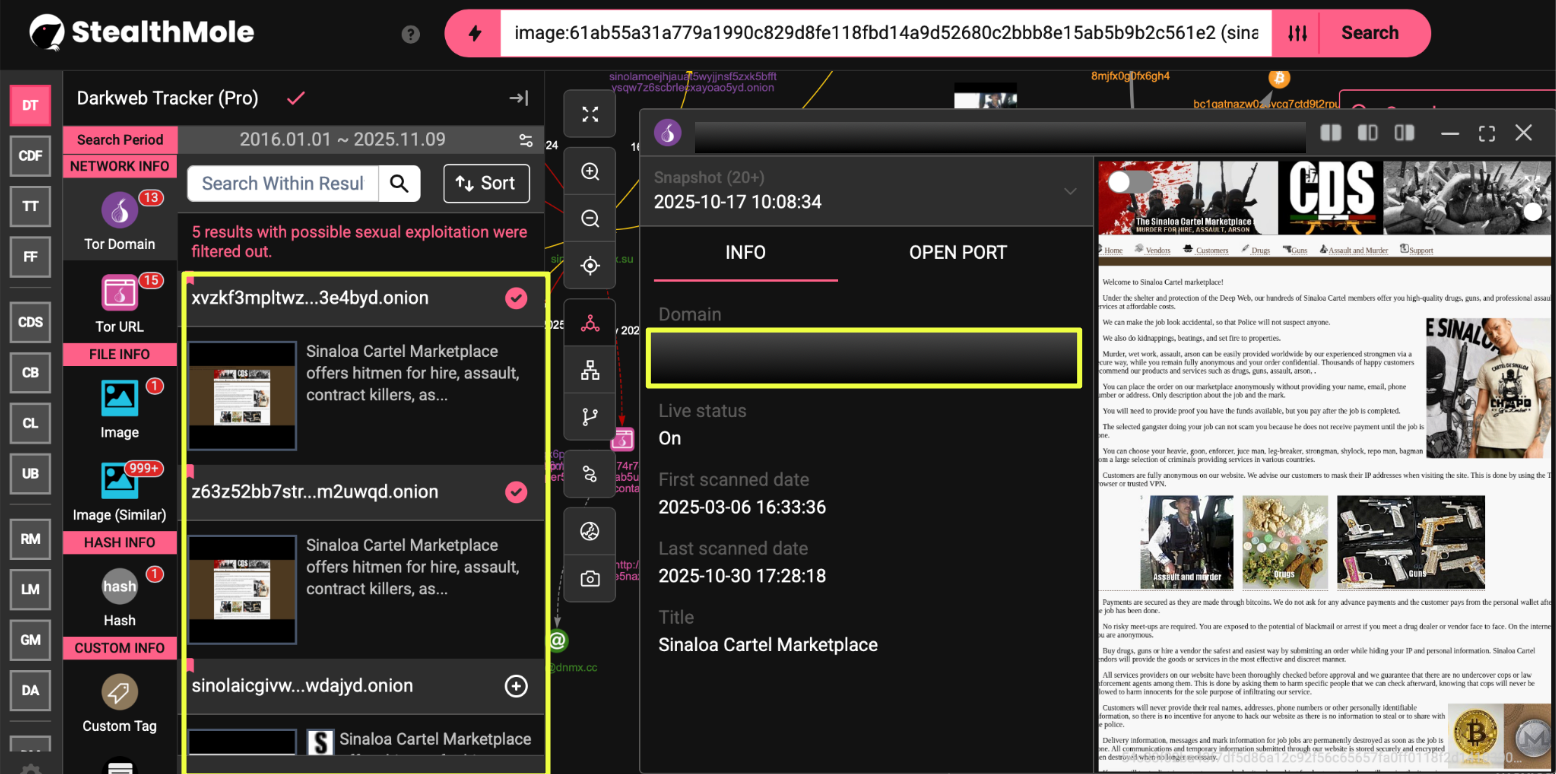
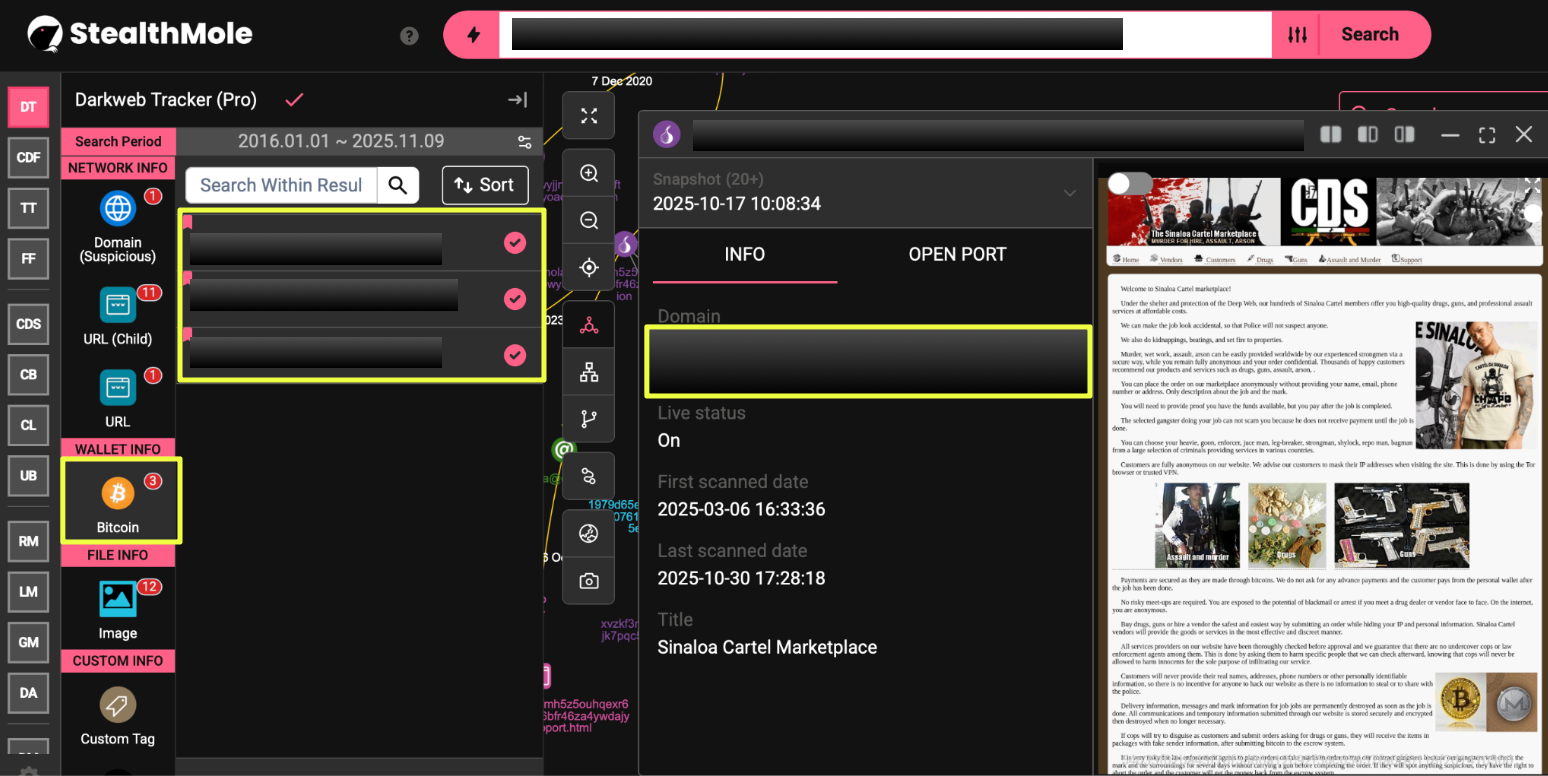
The most recent version remains active and identifies kt5*********f6g.onion as its current “primary” address. The inclusion of this new reference domain suggests a continued migration strategy aimed at maintaining visibility while avoiding takedowns. StealthMole’s tracker recorded this version as active from March 2025 onward, confirming that the operation persisted despite the deactivation of several earlier mirrors.
- jgs7*************************************************6id.onion
Analysis of the active domain revealed three Bitcoin wallet addresses, which were displayed for payment transactions. None of the wallets exhibited notable activity or links to known illicit clusters, suggesting that they may serve as static placeholders to reinforce the marketplace’s appearance of legitimacy rather than as functioning payment channels.
- Bc1q2**********************************gh4
- Bc1qa**********************************x0m
- bc1q***********************************5t7
The discovery of these domains demonstrated that the network continued to adapt its presence through domain rotation and superficial rebranding. Despite these changes, the repetition of identical content, language, and imagery across all sites indicated that the operation was still driven by the same source and continued to rely on the established Sinaloa identity to attract potential users.
Inside the Marketplace Interface
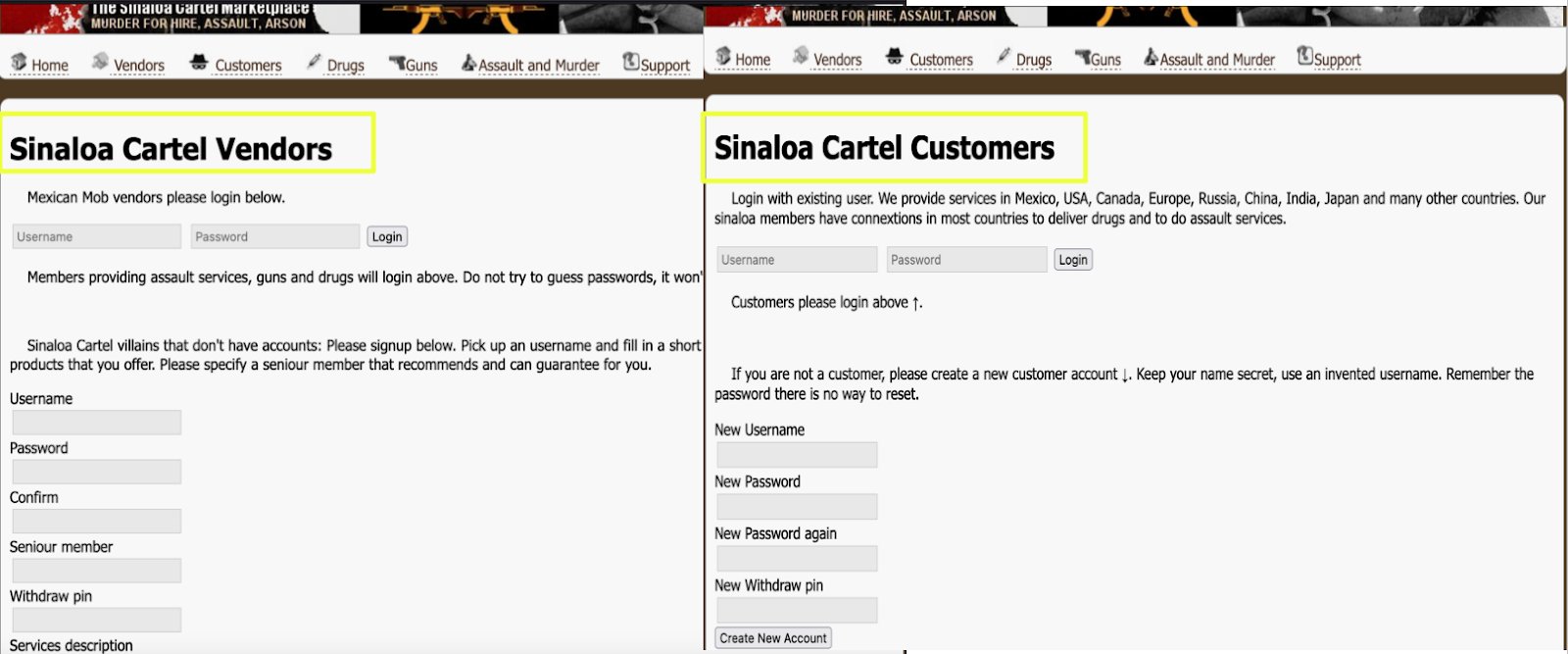
The most recent active version of the marketplace presented a fully functional interface at the time of analysis. The platform featured distinct login pages for “Vendors” and “Customers,” suggesting a simulated multi-user ecosystem. The vendor section claimed to host “Mexican mob members” providing services such as assault, arson, kidnapping, and drug distribution, while the customer interface promoted access to these offerings across multiple countries, including the USA, Canada, Europe, Russia, China, India, and Japan.
- jgs7le*********************************************6id.onion
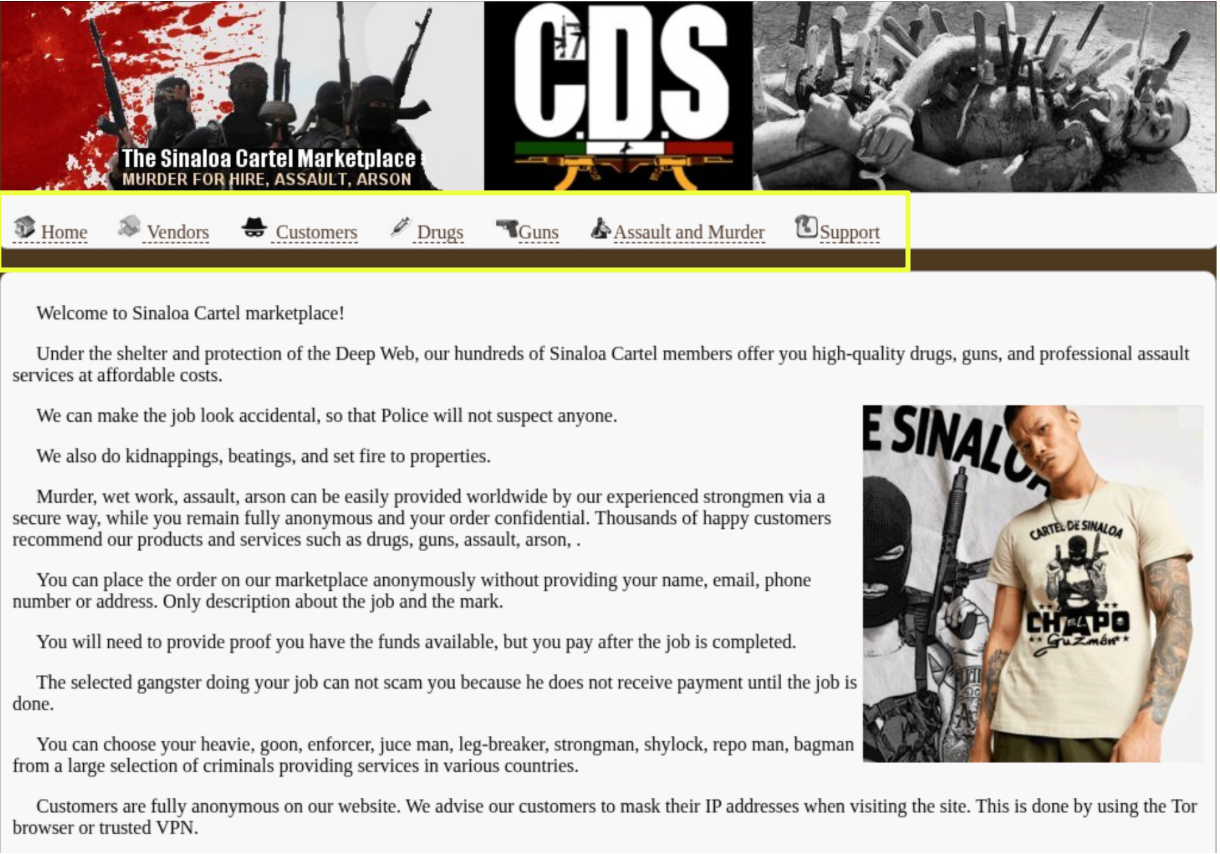
The site was organized into several key sections: Drugs, Guns, and Assault and Murder, each containing lengthy promotional text and imagery designed to imitate legitimate e-commerce language. The “Drugs” section advertised an international supply chain with products such as cannabis, ketamine, ecstasy, opioids, and cocaine, allegedly sourced from Europe, the USA, and India.
Similarly, the “Guns” page detailed weapon categories ranging from handguns and sniper rifles to explosives and grenades, claiming connections to arms smugglers from former Soviet states. The “Assault” section was notably more explicit, outlining alleged “shoot and get away” and “accidental” murder options, with listed starting prices and refund guarantees.
While the platform presented itself as an organized transnational criminal marketplace, several inconsistencies were immediately evident. The use of broken English, poorly formatted instructions, and unrealistic pricing structures undermined its credibility. Moreover, the presence of generic stock imagery, repeated design templates, and exaggerated claims reinforced the conclusion that the site was constructed to mimic the image of a professional cartel-run operation rather than represent an authentic criminal network.
Assessment
The investigation found no evidence linking any of the identified domains to the actual Sinaloa Cartel or to individuals associated with the organization. While the marketplaces consistently used the Sinaloa name, references to Joaquín “El Chapo” Guzmán, and imagery portraying cartel symbolism, these elements appear to have been used purely for branding and intimidation. The uniformity of content, design, and communication style across all discovered domains indicates that the operation was managed by a single actor or a small coordinated group, rather than by a large criminal organization with the resources and structure of the real Sinaloa Cartel.
Linguistic and visual analysis further supports this conclusion. All sites were written entirely in English, a language inconsistent with how genuine Sinaloa affiliates typically communicate online. The promotional text displayed overly polished phrasing and exaggerated marketing claims such as “we can kill any person you want” and “thousands of satisfied customers,” which are hallmarks of fraudulent marketplaces. The recurring use of the same stock-like image of a man wearing a “Cartel de Sinaloa” T-shirt reinforced this theatrical approach, suggesting that the operators were more concerned with creating a convincing façade than conducting real transactions.
The presence of multiple DNMx-based email addresses across different domains shows a deliberate attempt to sustain operational continuity while evading blacklisting or deactivation. This strategy, combined with the frequent introduction of new .onion mirrors, reflects an effort to maintain visibility rather than a genuine logistical need. The same pattern of rebranding and mirror rotation is well-documented among dark web scams designed to appear resilient and active.
StealthMole identified three Bitcoin wallet addresses on the most recent version of the marketplace, yet none displayed any meaningful transaction history. The lack of financial activity further undermines the credibility of the service. In addition, the domain kt5********f6g.onion, promoted as the “primary” Sinaloa site, was publicly listed among scam marketplaces on an independent dark web review forum, confirming that this network is recognized within the cybercriminal community as a fraudulent operation.
Overall, the available evidence points to a long-running impersonation campaign rather than an operational criminal enterprise. The network exploited the Sinaloa Cartel’s notoriety to attract users and create an illusion of legitimacy, likely for the purpose of obtaining cryptocurrency payments from unsuspecting individuals. Its persistence over multiple years suggests that the impersonation proved effective enough to sustain continued replication.
Conclusion
The investigation into the so-called Sinaloa Cartel Marketplace revealed a network of fraudulent dark web domains exploiting one of the world’s most notorious criminal brands. Despite using the Sinaloa name, imagery, and narrative, the operation exhibited none of the linguistic, structural, or behavioral traits associated with authentic cartel-linked activity. Its multilingual presentation, lack of credible financial movement, and frequent replication under new domains all point toward a long-running deception campaign targeting inexperienced dark web users.
Rather than functioning as a genuine criminal infrastructure, the marketplace appears designed to mimic organized crime for profit through fraudulent means. By presenting a façade of professionalism, complete with product listings, vendor systems, and supposed international reach, the operators leveraged the cartel’s fear-based reputation to attract attention and potentially extort funds.
This case underscores the increasing use of criminal identity impersonation within dark web ecosystems. Well-known syndicates such as the Sinaloa Cartel are being repurposed as digital brands by independent actors who rely on their notoriety to build trust and evade scrutiny.
Editorial Note
While every effort has been made to ensure the accuracy and integrity of this analysis, it is important to recognize that attribution within the cyber threat landscape remains inherently uncertain. The connections outlined in this report are derived from open-source intelligence and verified data collected through the StealthMole platform.
Attribution, therefore, should be viewed as probabilistic and may evolve as new intelligence emerges. The purpose of this report extends beyond identifying a single actor, it demonstrates how StealthMole’s integrated toolset, including Dark Web & Telegram Trackers, ULP Binder, and the Compromised Data Set, empowers analysts to correlate domains, aliases, and behaviors across fragmented ecosystems, turning isolated indicators into cohesive, actionable intelligence.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Cartel

.svg)
.svg)
.svg)