Inside Rhysida: Unmasking the Ransomware Group’s Expanding Darkweb Infrastructure
Rhysida is a double-extortion ransomware group that emerged in mid-2023 and rapidly established itself as an active threat actor across multiple regions and industries. Known for publishing victim data on Tor-based leak sites and pressuring organizations through public-facing “auctions,” the group has built a reputation for opportunistic targeting and a consistently expanding portfolio of victims. Since their first appearance, Rhysida has been linked to hundreds of attacks, with healthcare, education, manufacturing, and government entities appearing frequently among their published victims.
Despite their visibility on leak sites, much of Rhysida’s operational ecosystem remains fragmented across hidden services, communication channels, and dispersed infrastructure that typically surfaces only through darkweb-level observation. Their public pages reveal only a fraction of the systems they rely upon for hosting, communication, and data distribution, making infrastructure-centric analysis essential for understanding their operational footprint.
This report examines Rhysida through that lens. Using StealthMole, it explores how an individual incident leads back to the broader network that supports the group’s activities. Rather than focusing exclusively on victims, the report follows the group’s presence across the darkweb, tracking domains, communication points, and technical signals that collectively illustrate how Rhysida maintains and operates its ransomware ecosystem.
Incident Trigger and Initial Investigation
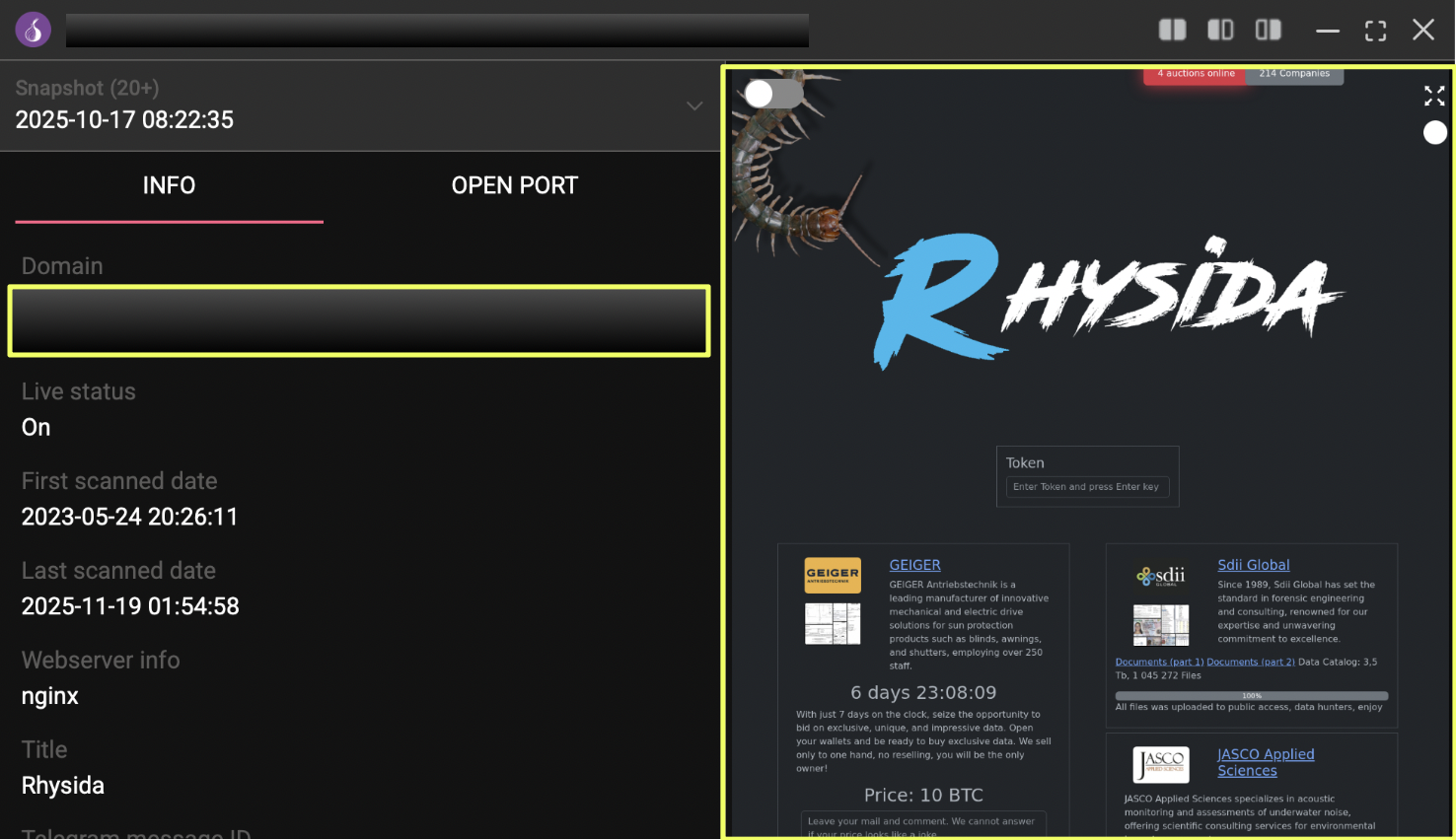
The investigation began on 18 November 2025, when StealthMole’s Ransomware Monitoring module indexed a new victim listing published by the Rhysida ransomware group. The alert was triggered from Rhysida’s primary Tor leak site:
Primary Rhysida Leak Site:
http://rhysida*******************************************7cad.onion/
At the time of detection, the group had posted Heart South Cardiovascular Group, a healthcare provider in the United States, as one of their newest victims. This entry was automatically parsed and timestamped within the platform, marking the starting point for the broader investigation.
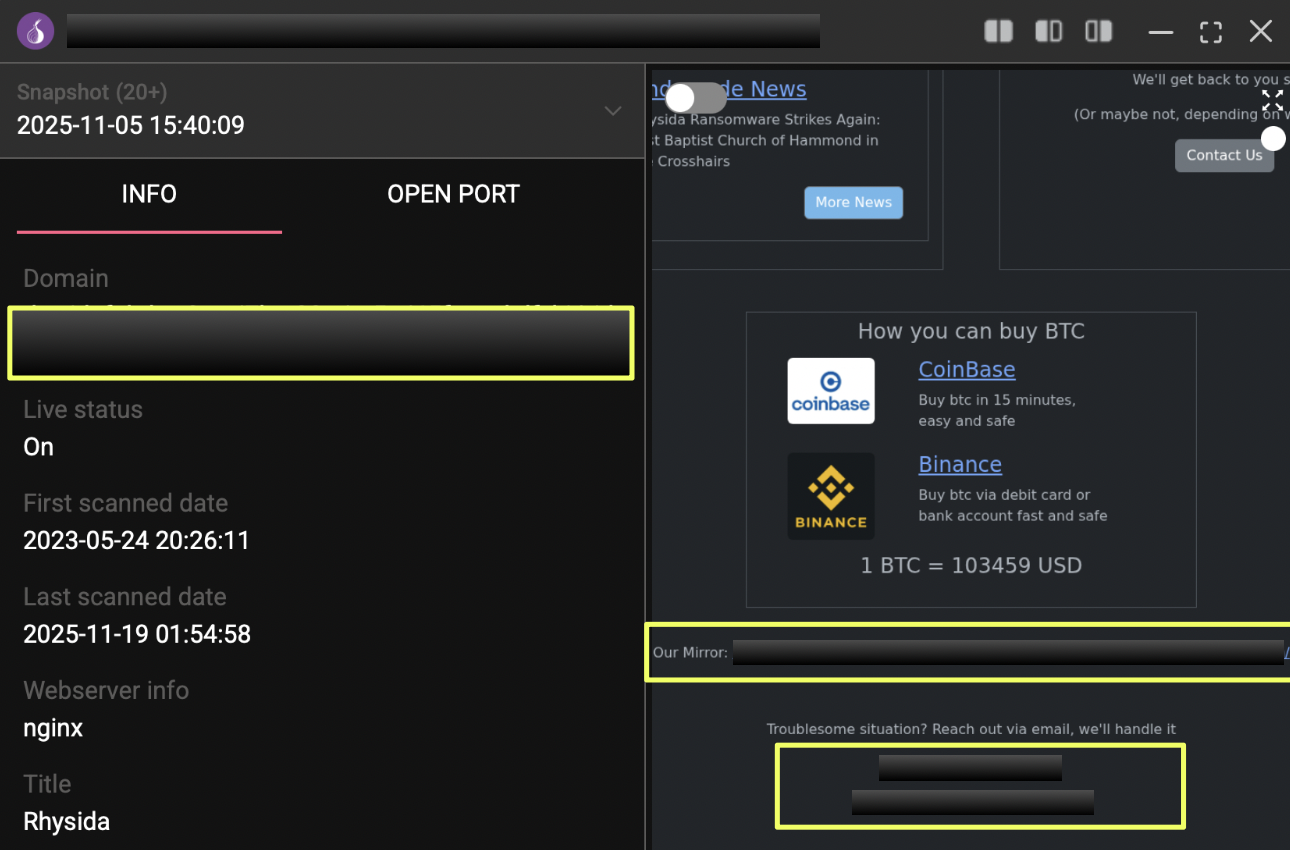
Following the initial trigger, the primary domain served as the central pivot for all subsequent steps. The first layer of analysis involved reviewing the structure and content of the leak site, which contained multiple references relevant to Rhysida’s operations. Among these was a secondary mirror explicitly listed on the site:
Mirror Listed on Leak Site:
http://rhysida*****************************************6yegad.onion/
The same page also displayed the group’s communication channels, revealing two operational email addresses used for victim communication and support:
- rhy***********a@onionmail.org
- rhy***********g@onionmail.org
These initial identifiers formed the foundation of the investigation. Using them as anchor points allowed StealthMole’s darkweb and Telegram tracking modules to surface additional domains, infrastructure components, and historical references tied to Rhysida, which are detailed in the subsequent sections of this report.
Infrastructure Discovery
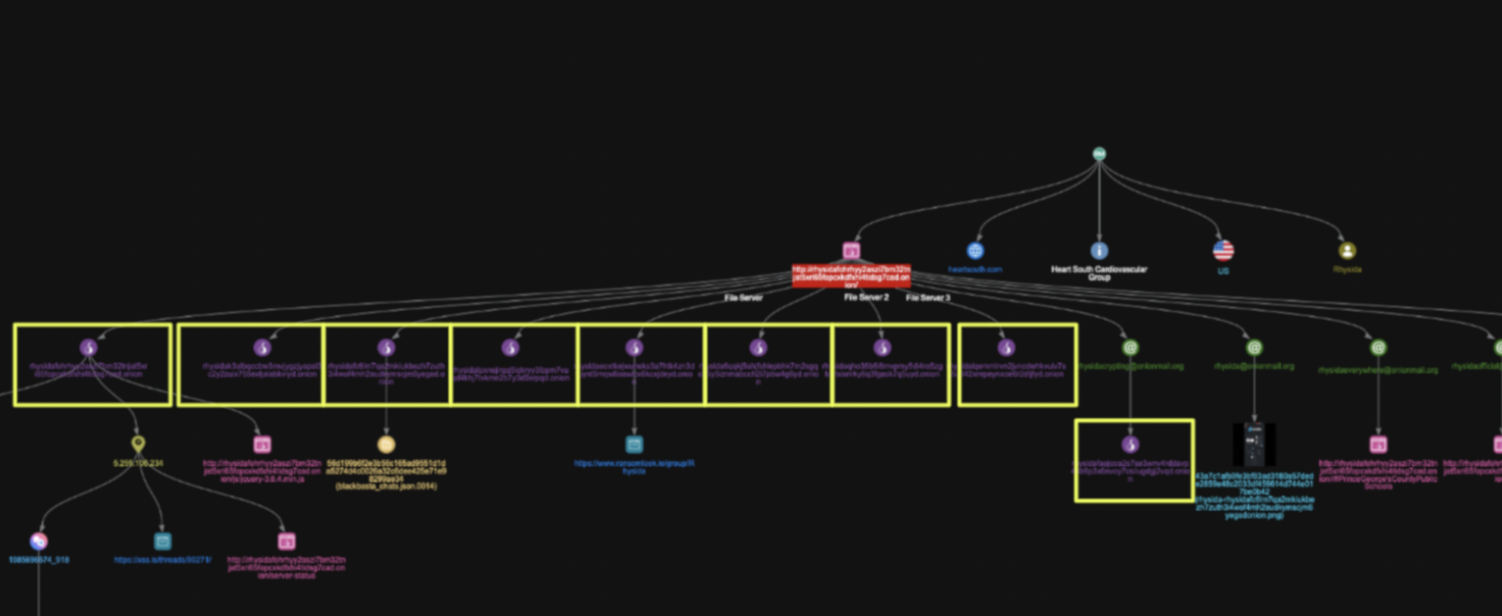
The initial indicators extracted from Rhysida’s leak site served as pivot points for uncovering a broader network of hidden services and communication assets linked to the group. Through StealthMole’s Darkweb Tracker, Telegram Tracker, and correlated pivots on domains and email identifiers, multiple layers of Rhysida’s operational infrastructure surfaced, revealing a diverse ecosystem spanning Tor hidden services, email points, backend systems, and external references embedded across the darkweb.
Onion Services
The investigation began with the primary leak site and its official mirror, both publicly listed by Rhysida:
- Primary Leak Site:
http://rhysidafohrhyy2aszi7bm32tnjat5xri65fopcxkdfxhi4tidsg7cad.onion/ - Official Mirror:
http://rhysidafc6lm7qa2mkiukbezh7zuth3i4wof4mh2audkymscjm6yegad.onion/
Further pivots across StealthMole’s darkweb tracker uncovered several additional Tor v3 domains associated with Rhysida. These included mirrors, file-delivery endpoints, and alternate service hosts the group appears to use for distributing stolen data or maintaining redundancy:
- rhysida*********************************************deyd.onion
- rhysida*********************************************5uyd.onion
- rhysida*********************************************jfyd.onion
- rhysida*********************************************viyd.onion
- rhysida*********************************************rpqd.onion
- rhysida*********************************************g6yd.onion
A seventh domain appeared through a StealthMole email-based pivot, expanding the set further:
- rhysida*********************************************2vqd.onion
Each address was identified through pivots on verified Rhysida infrastructure, either through the leak site, onionmail email addresses, or automated indexing across StealthMole’s darkweb tracker. Collectively, these domains reflect Rhysida’s reliance on multiple hidden services to maintain availability, distribute stolen files, and segment operational roles across their ecosystem.
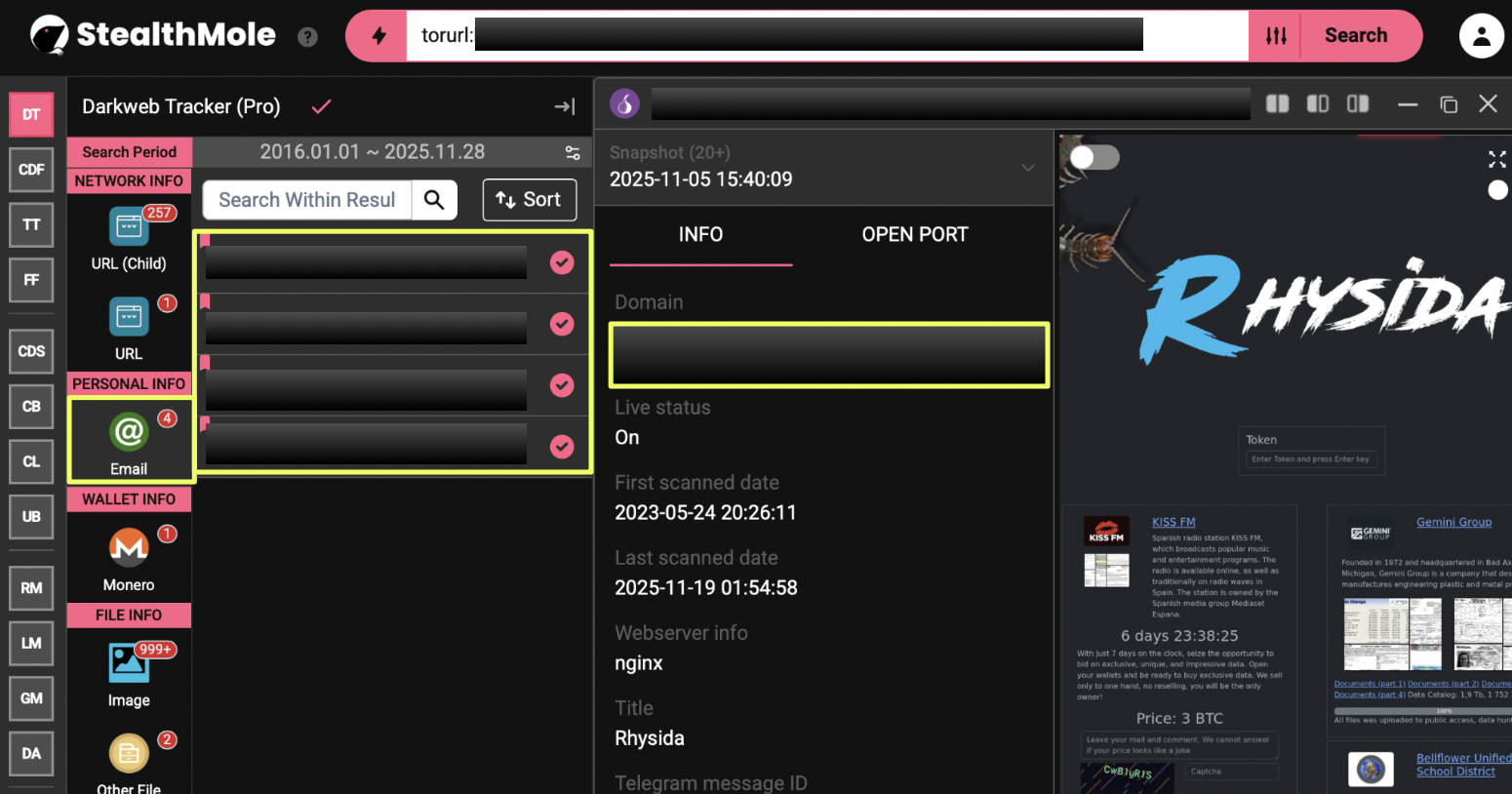
Email Infrastructure
Rhysida maintains a set of onionmail addresses for negotiation, victim communication, and administrative contact. Two of these were present on the leak site, while two more surfaced through StealthMole’s Darkweb Tracker:
- Listed on Leak Site:
- rhy***********a@onionmail.org
- rhy***********g@onionmail.org
- Identified via StealthMole Correlation:
- rhy***********e@onionmail.org
- rhy***********l@onionmail.org
The discovery of additional addresses through tracking modules suggests segmentation in communication channels, an approach commonly used by ransomware groups to manage negotiation workflows, data publishing operations, or internal coordination.
Surface Infrastructure
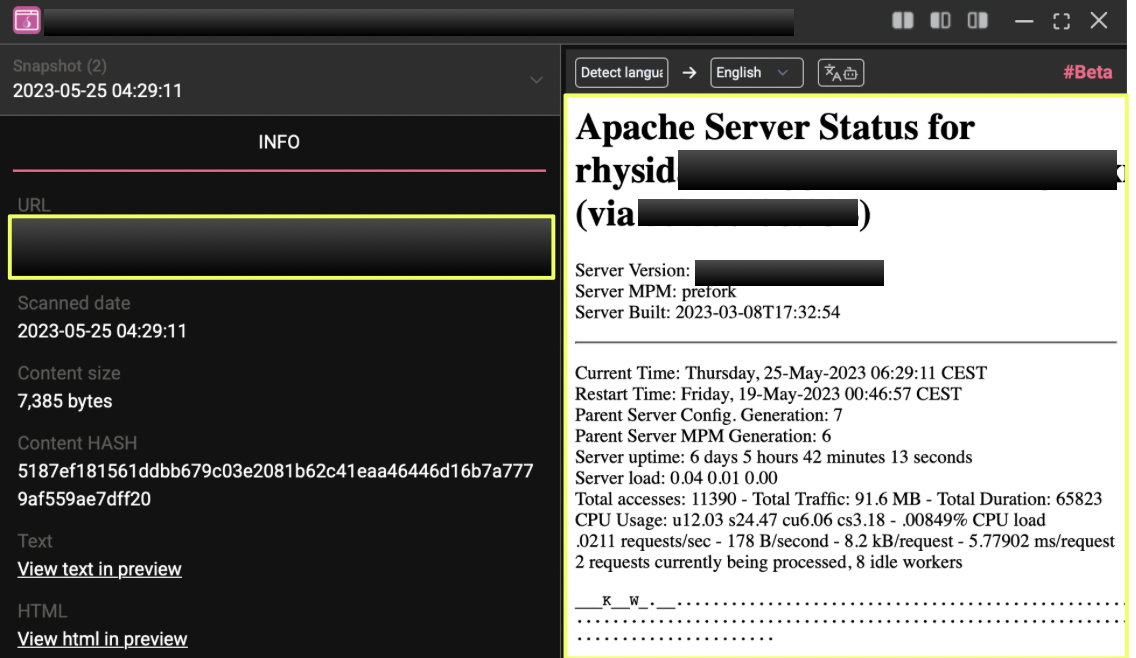
A notable finding emerged when StealthMole traced the primary onion domain to an exposed Apache server-status page. This page inadvertently revealed backend infrastructure tied to Rhysida’s hosting environment:
- Backend IP Address: 5.***.**6.**4
- Location: N***********s
- Host Organization: The I**************e Group B.V.
- Server Details: Apache/2.*.**, with worker activity logs and uptime metadata visible
The exposed server-status interface indicated that requests to Rhysida’s hidden service were being routed through this surface-facing server, providing insight into their hosting configuration and revealing internal operational details not intended for public access.
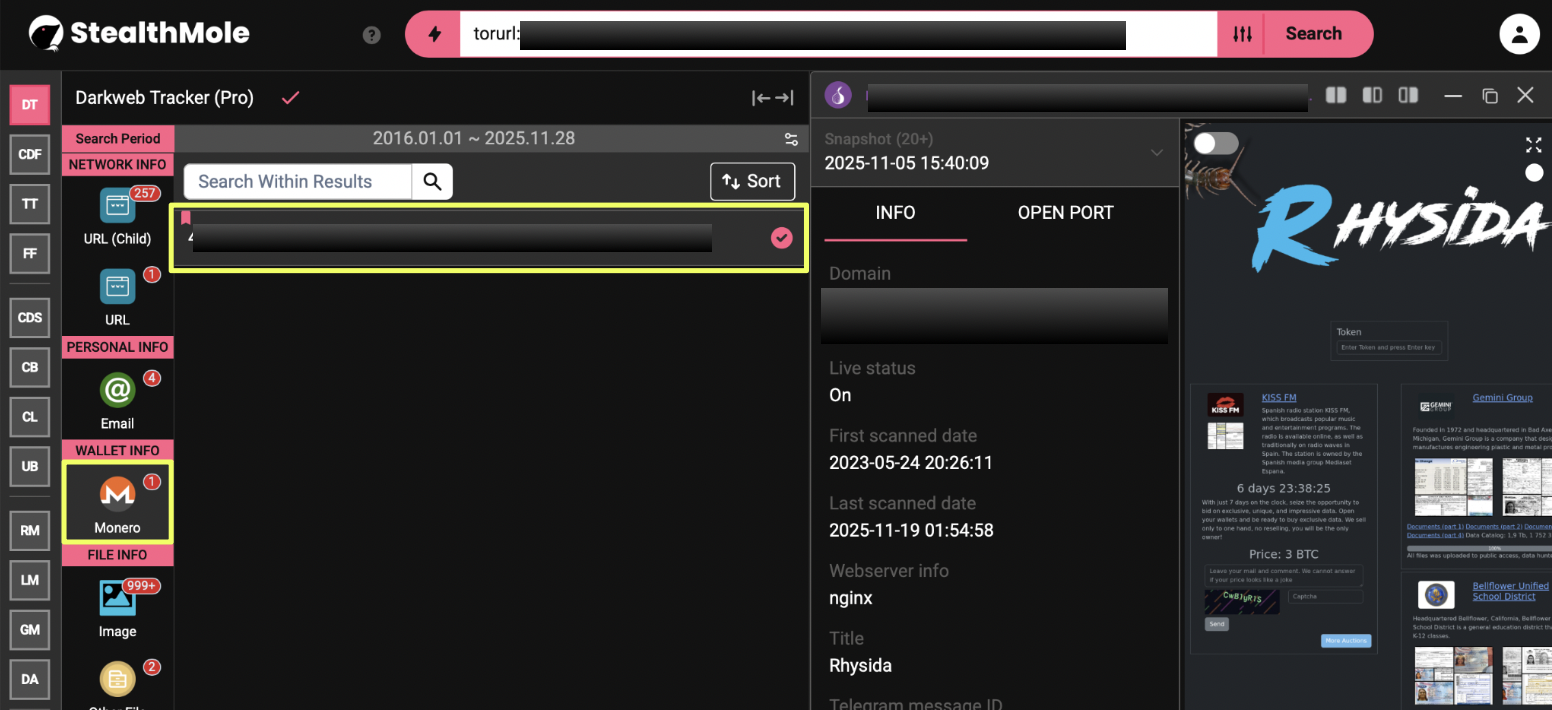
Cryptocurrency Address
During the investigation, a Monero address resembling a file-host reference appeared in proximity to Rhysida-related infrastructure:
- 453v***********************************************VJpjxa
While structurally valid as a Monero wallet, its association with Rhysida remains unconfirmed based on the evidence provided. It is therefore included here as an unverified financial artifact pending further validation.
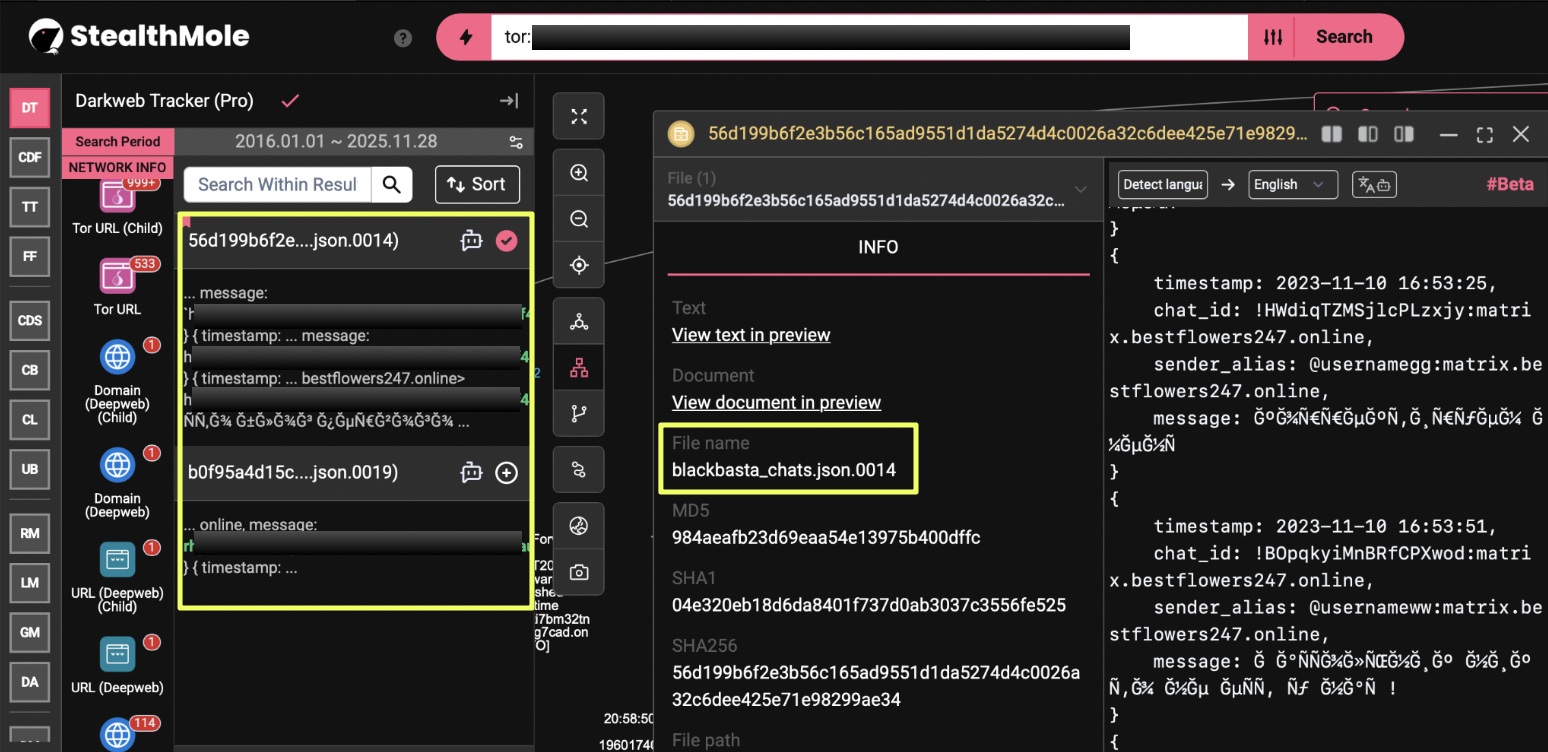
Cross-Group Mentions
As part of StealthMole’s darkweb correlation, one Rhysida mirror was referenced inside leaked Black Basta chat logs (blackbasta_chats.json.0014 and .0019). The reference does not imply collaboration or shared infrastructure; however, it demonstrates how ransomware operators monitor or reference each other’s leak sites within underground circles.
Assessment
The infrastructure uncovered during this investigation reflects a threat actor that prioritizes redundancy, distribution, and compartmentalization across its operational ecosystem. The large amount of Tor hidden services: spanning leak sites, mirrors, and file-hosting endpoints, suggests a deliberate effort to ensure availability regardless of takedowns or internal failures. While many ransomware groups maintain two or three onion addresses, the volume of additional service endpoints tied to Rhysida indicates a strategy built around maintaining persistent accessibility for victims, media, and competing actors browsing the darkweb. The emergence of further domains through pivots on their own communication channels reinforces the likelihood that these services support parallel functions rather than serving merely as backups.
The expansion of Rhysida’s email infrastructure reinforces this pattern. Maintaining multiple onionmail accounts allows the group to partition communication streams, separate negotiation workflows, and minimize dependency on a single address that could be suspended or flooded with traffic. The fact that new emails surfaced only through darkweb tracking rather than the public leak site highlights that Rhysida’s operational channels extend beyond what is intentionally presented to victims. This layered approach to communication helps protect the group from disruptions while allowing them to manage interactions with multiple victims simultaneously.
One of the most revealing aspects of the investigation is the exposure of backend server information through an improperly restricted server-status interface. The visibility of request logs and host details demonstrates operational oversight and suggests that not all components of Rhysida’s infrastructure are hardened to the same standard. While their use of distributed Tor services reflects intentional resilience, the misconfigured surface infrastructure introduces points of weakness that can unintentionally disclose hosting details, operational timings, and behavioral patterns. Such inconsistencies are characteristic of groups that scale infrastructure rapidly while prioritizing functionality over secure configuration.
The appearance of Rhysida domains within another ransomware group’s leaked chats underscores how their infrastructure circulates in broader cybercriminal environments. Although the reference does not imply collaboration, it illustrates that Rhysida’s services are well-known and frequently referenced across underground communities. This, combined with early Telegram mentions of their leak site, positions Rhysida as a group that is both visible and closely watched within the ecosystem.
Overall, the findings depict an actor that blends deliberate redundancy with occasional operational lapses. Rhysida maintains a dispersed network of hidden services and communication channels to support its double-extortion model, yet elements of their backend configuration reveal exploitable blind spots. The infrastructure mapped through this investigation provides a clearer view of the systems sustaining their operations and highlights both the resilience and weaknesses inherent in their approach.
Conclusion
The investigation into Rhysida’s activity demonstrates how a single victim posting can unfold into a broader view of a ransomware group’s operational landscape when examined through an infrastructure-first approach. By following the traces that surfaced across darkweb platforms, StealthMole was able to reveal components of the group’s ecosystem that are not visible through their public leak site alone. This layered perspective highlights the importance of examining both the content actors intentionally publish and the peripheral signals they leave behind.
The mapping of hidden services, communication channels, and backend elements provides a clearer understanding of how Rhysida maintains its presence, distributes stolen material, and sustains its extortion model. While their public-facing operations appear straightforward, the underlying network supporting those activities is far more extensive and dynamic. The patterns observed throughout this investigation underscore the value of correlating disparate data points to uncover deeper structures behind ransomware campaigns.
As Rhysida continues to add new victims and expand its footprint, visibility into the infrastructure that enables its operations becomes increasingly important. The findings in this report reinforce the role of continuous darkweb monitoring in identifying changes within threat actor ecosystems, surfacing new service endpoints, and tracking how groups evolve over time.
Editorial Note
As with all darkweb investigations, the findings presented in this report reflect what could be observed, indexed, and correlated at the time of analysis. Cyber investigations are fluid, often changing without warning, and visibility into hidden services is never absolute.
This report represents a snapshot of Rhysida’s operational footprint based solely on verifiable evidence collected through StealthMole’s monitoring and tracking capabilities. The goal is not to claim completeness, but to demonstrate how a structured, tool-driven investigative approach can surface meaningful insights even within uncertain and constantly shifting environments.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Malicious Group

.svg)
.svg)
.svg)