Operation Endgame: Unmasking the Rhadamanthys Stealer Network

The latest phase of Operation Endgame, carried out in November 2025, marked one of the most extensive coordinated actions against cybercrime infrastructure to date. With 1,025 servers disrupted and multiple darkweb services seized, the operation targeted several malware ecosystems that had quietly supported large-scale credential theft, access brokering, and criminal automation for years.
Among the key targets were three major cybercrime enablers: the Rhadamanthys infostealer, the VenomRAT remote access trojan, and the Elysium botnet. Authorities reported that the main suspect behind VenomRAT was arrested in Greece on 3 November 2025, underscoring the operation’s reach across both infrastructure and individuals.
From these three targeted ecosystems, this report focuses specifically on Rhadamanthys. Operation Endgame created a rare opening to examine how this stealer operated behind the scenes, both in its earlier stages and in its most recent form, and to explore how its operators adjusted as law-enforcement pressure increased.
Using StealthMole’s darkweb tracking and correlation capabilities, this investigation set out to map Rhadamanthys’ presence across hidden services, forum activity, and communication platforms. What began with seized domains quickly expanded into a deeper view of the ecosystem surrounding Rhadamanthys and the actor known as “K********e,” whose activity spans forums, encrypted messengers, and multiple anonymised communication channels.
Incident Trigger & Initial Investigation
The investigation began shortly after Operation Endgame concluded, when post-takedown monitoring showed early signs that parts of the Rhadamanthys ecosystem had been caught in the wider disruption. Although law-enforcement agencies did not publicly detail any infrastructure associated with the stealer, the broader impact of the operation suggested that some of its assets may have been indirectly affected.
To validate this, StealthMole’s darkweb tracking tools were used to perform an initial reconnaissance sweep across hidden services, archived listings, and historical references tied to Rhadamanthys. The first objective was simply to understand whether any remnants of the stealer’s presence had surfaced following the enforcement wave. This involved scanning for changes to known identifiers, mirrors, or service states, particularly signs of domain seizures or sudden inactivity that could indicate collateral impact.
This initial sweep confirmed that enough signal remained across the darkweb to justify a deeper examination. With that confirmation, the investigation shifted toward systematically mapping Rhadamanthys’ operational footprint, beginning with its most visible references and gradually expanding into less obvious assets connected through forum activity, legacy documentation, communication handles, and infrastructure breadcrumbs.
Preliminary Infrastructure Validation
Early results began to surface once StealthMole’s darkweb tracker correlated activity linked to Rhadamanthys across multiple hidden services. As Operation Endgame unfolded, law-enforcement actions specifically included the Rhadamanthys stealer among their designated targets, and several elements of its ecosystem showed clear signs of disruption.
Two long-standing onion domains associated with Rhadamanthys transitioned into seized states in the immediate aftermath of Endgame’s enforcement wave. Although none of these domains were mentioned in official law-enforcement communication, their sudden transition into seized states aligned closely with the broader timing and style of Endgame-related disruptions.
- stealerskymtni3tiagmx3pqktjgkm2iigwj6e2touws773emrfjvoyd.onion
- rhadwikiwwzr6sfzygsr3qh7lwu5ghnaoupxwpsj2xuxjcgcebikh7id.onion
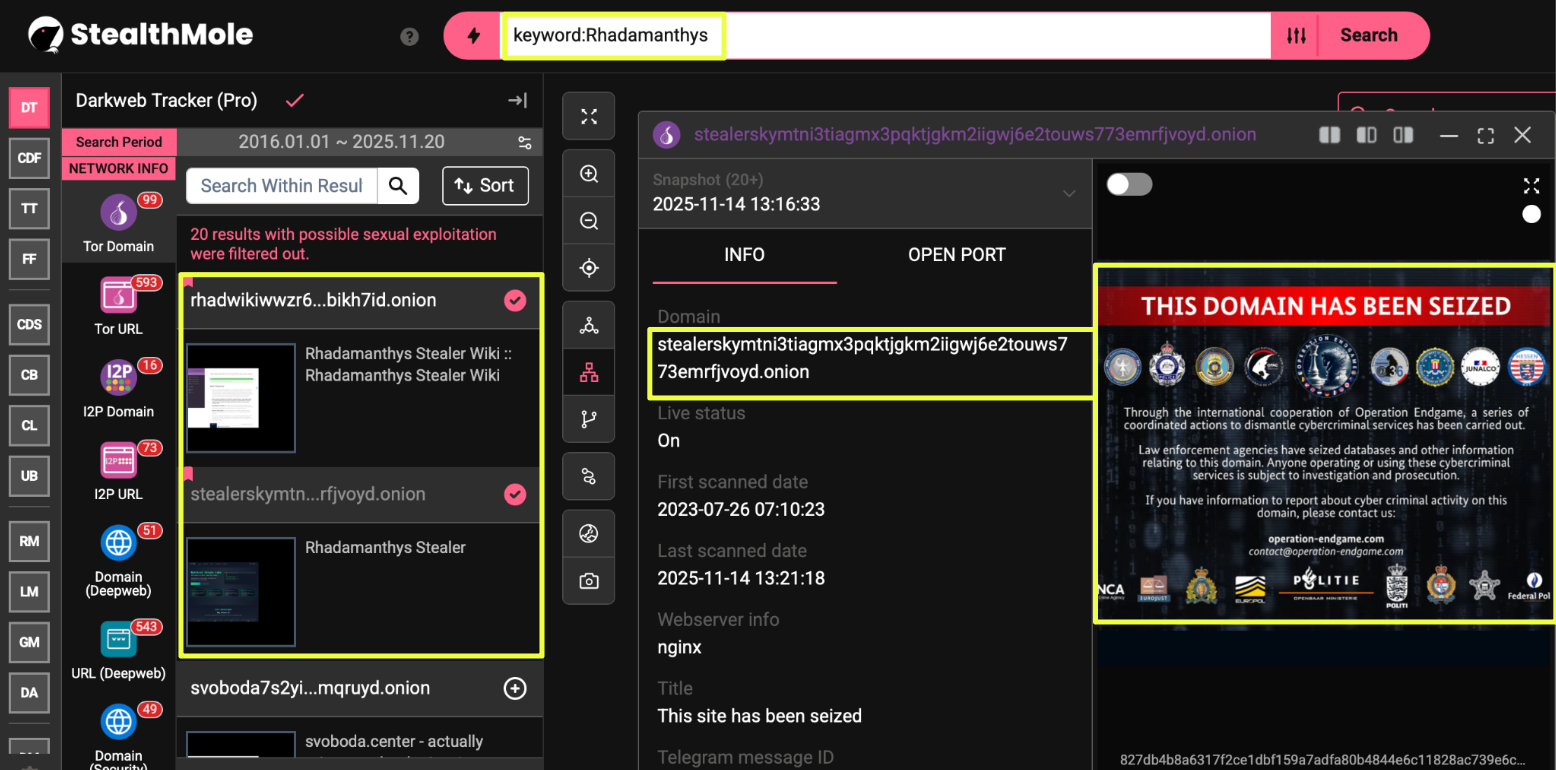
These domains had historically served as core components of the Rhadamanthys ecosystem, functioning as its primary public-facing site and its accompanying technical documentation hub. Their seizure provided concrete confirmation that the operation had directly targeted the stealer’s infrastructure, creating reliable starting points for deeper investigation.
Using these domains as initial anchors, StealthMole connected them to additional traces distributed across forum posts, legacy sales material, and communication channels associated with Rhadamanthys activity. The consistency of these overlaps indicated that the stealer maintained a structured and traceable presence across the darkweb, even before the takedown occurred.
With these validated entry points in place, the investigation could move beyond initial scanning and begin systematically reconstructing the ecosystem that supported Rhadamanthys: its infrastructure, operators, and the broader network of services that sustained its operations.
Rhadamanthys’ Primary Website
The primary Rhadamanthys website now displays an Operation Endgame seizure banner. Using StealthMole’s historical indexing capabilities, the pre-takedown state of the website was recovered, providing a clear view of how the stealer was marketed and presented to buyers before law-enforcement intervention.
- stealerskymtni3tiagmx3pqktjgkm2iigwj6e2touws773emrfjvoyd.onion
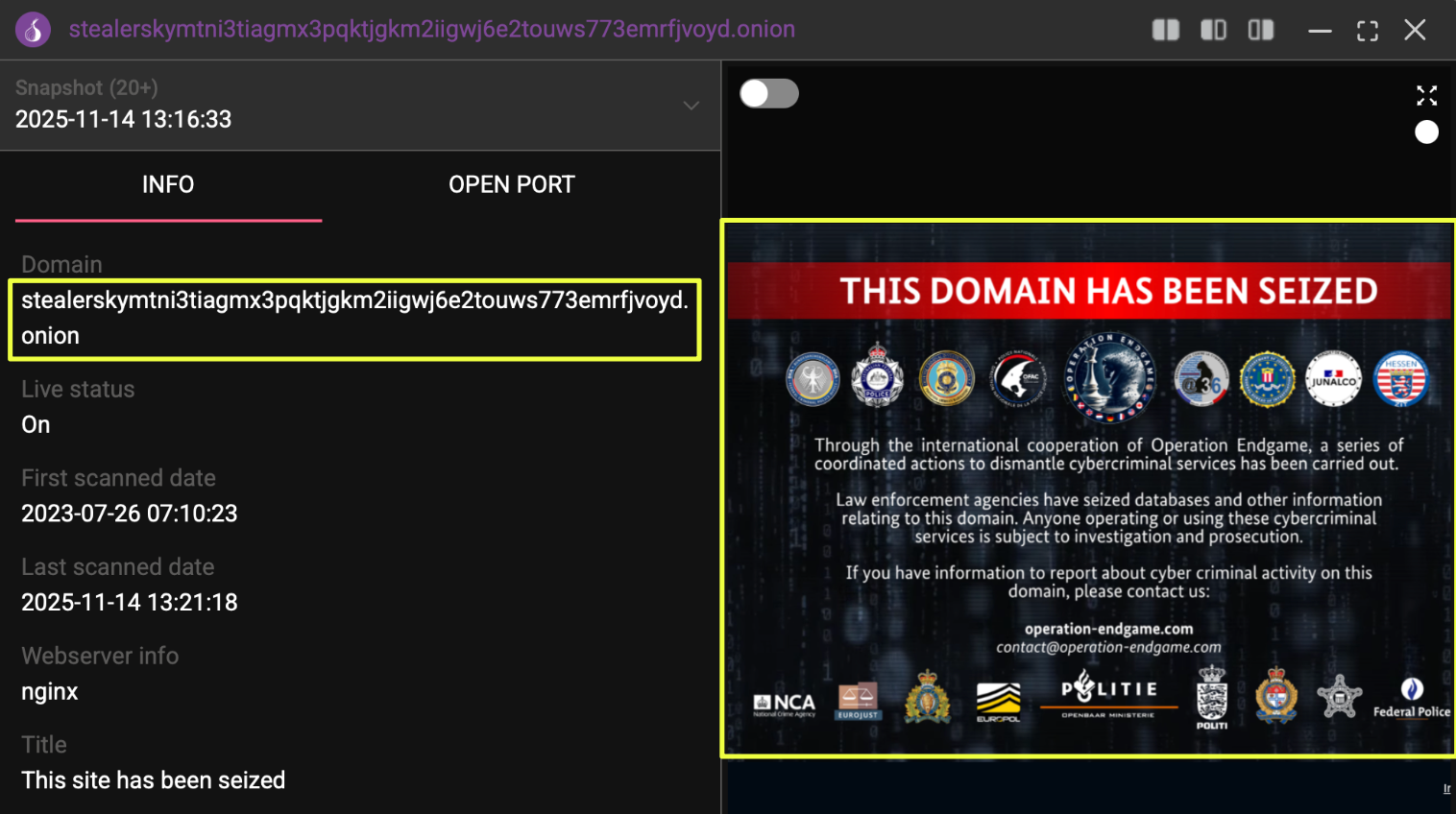
The archived version showed a polished interface with structured navigation and prominent branding, positioning Rhadamanthys as a fully developed commercial service rather than a basic commodity stealer. The landing page highlighted its advertised capabilities, including browser data extraction, credential harvesting, system profiling, and support for multiple cryptocurrency wallets. These features were presented in a modular format consistent with the way later documentation described the product.
The website also promoted direct communication channels for buyers. A “Contact us” section included a large email-style icon and a set of platform badges, indicating the preferred communication routes. The most prominent link pointed users to a designated Telegram group, which served as the primary space for customer queries and updates. Additional references included identifiers resembling XMPP-style contact points, reinforcing that the operation maintained multiple parallel communication pathways.
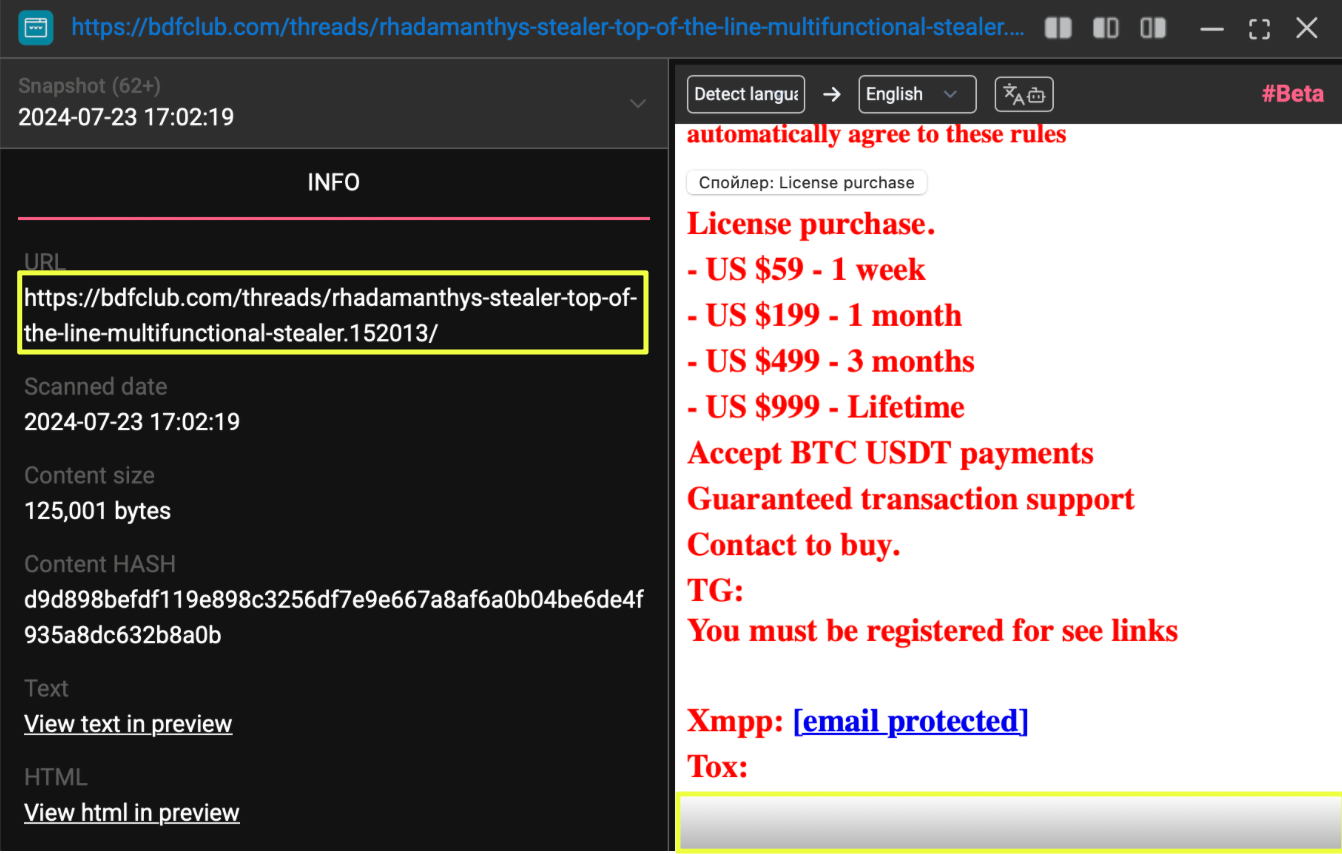
Pricing information was clearly displayed and offered in several subscription tiers. The pre-takedown snapshots showed the following structure:
- $59 — 1 week
- $199 — 1 month
- $499 — 3 months
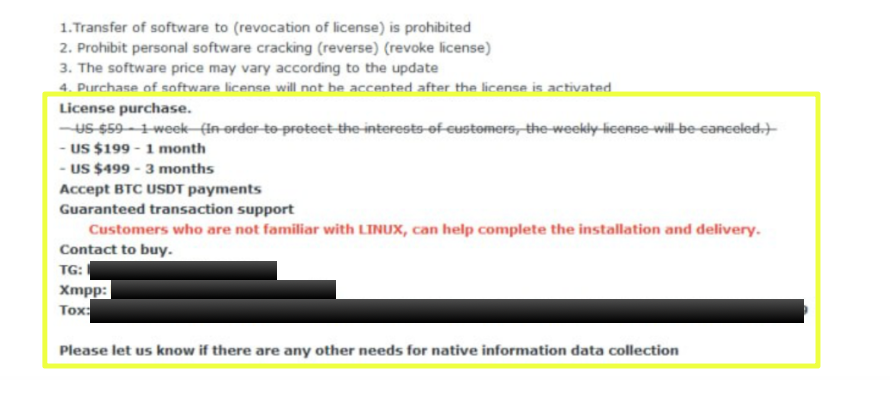
These pricing tiers matched the figures that later appeared in forum threads associated with Rhadamanthys, providing consistency across platforms.
Overall, StealthMole’s historical indexing revealed a well-organized, customer-oriented service with a clear product presentation, structured communication channels, and a mature pricing model. The primary website served as the central hub of the Rhadamanthys ecosystem until its seizure during Operation Endgame.
Wiki Site: Technical Documentation & Backend Operations
Alongside the primary website, Rhadamanthys maintained a dedicated technical wiki, which was also seized under Operation Endgame. Using StealthMole’s historical indexing capabilities, the pre-takedown state of this wiki was accessible, revealing a comprehensive internal knowledge base intended for customers who had purchased access to the stealer.
- rhadwikiwwzr6sfzygsr3qh7lwu5ghnaoupxwpsj2xuxjcgcebikh7id.onion
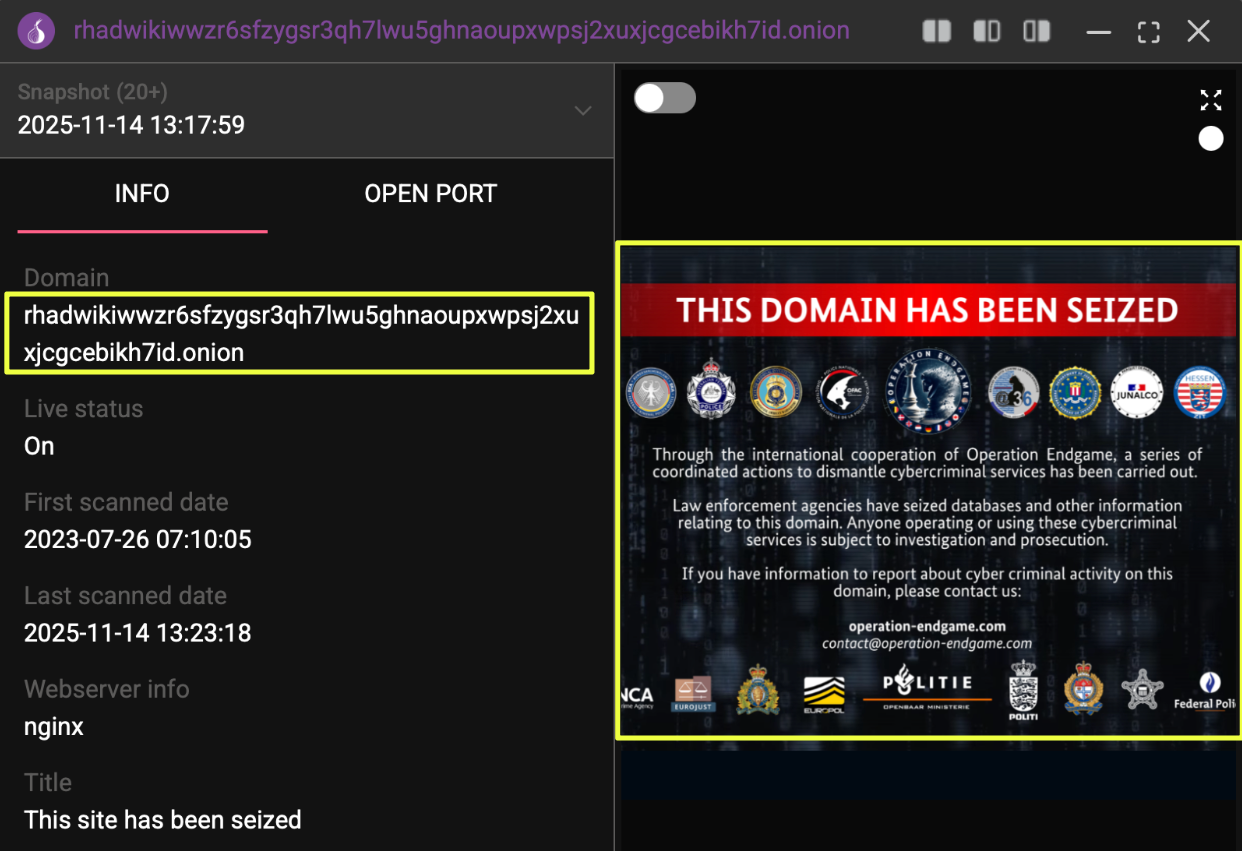
The wiki served as the operational backbone of Rhadamanthys, functioning as a step-by-step deployment guide rather than a marketing asset. It provided detailed instructions on setting up the backend server, configuring the panel, activating licenses, generating builds, and retrieving logs. Each section was written in a direct, procedural format aimed at ensuring operators could self-deploy the stealer with minimal guidance.

The server installation pages outlined the full environment requirements, including the expected Linux configuration, system libraries, web server dependencies, and database setup. Videos showed clear instructions for configuring the backend and connecting service components, indicating that the stealer relied on a structured, panel-based architecture. These steps reflected a design that favored stability and repeatability over experimentation.
Another section covered license activation, explaining how buyers were expected to retrieve their unique activation key, apply it within the panel, and verify successful registration. This process emphasized Rhadamanthys’ subscription model, reinforcing what was already visible in the pricing tiers on the main website.
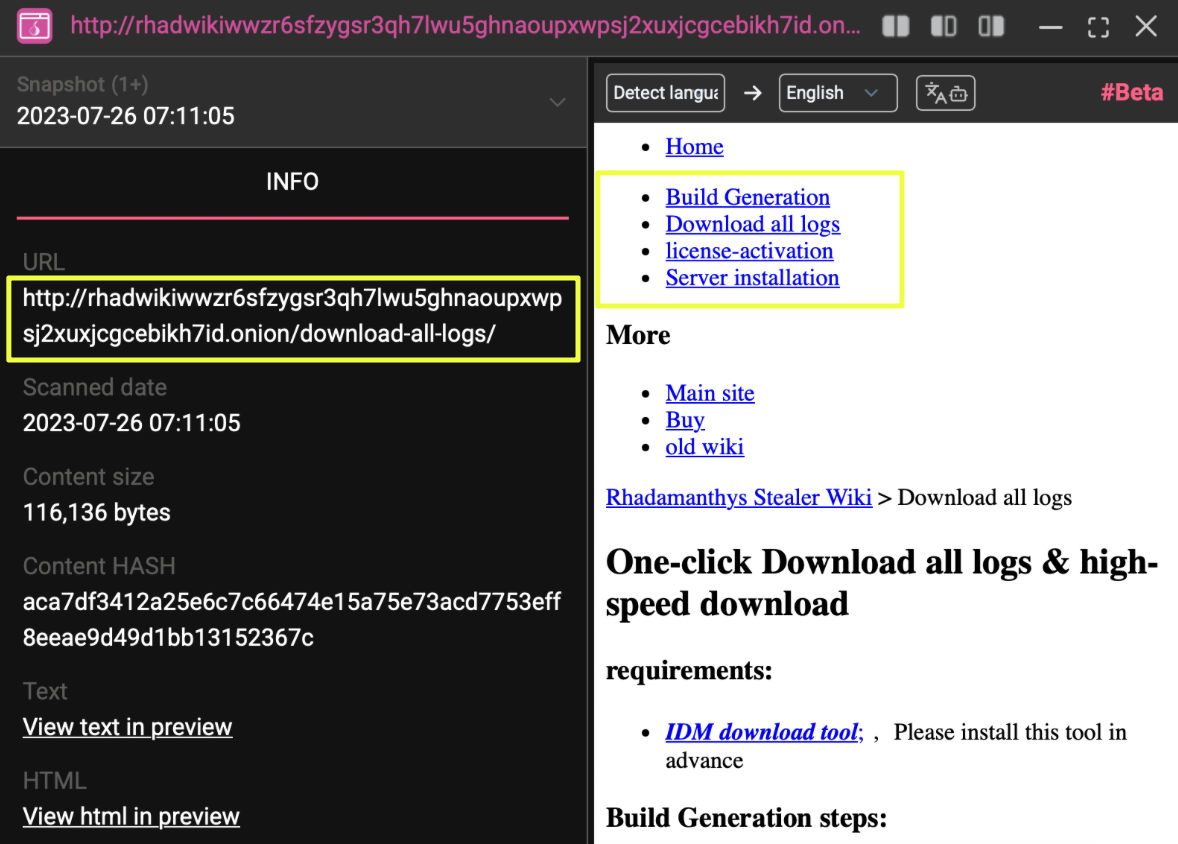
The log retrieval documentation described a multi-step process where stolen data was packaged server-side and made available for download. The wiki noted that log packaging depended on CPU and disk throughput, and that operators needed to wait while the backend generated downloadable archives. Once ready, the system allowed users to export a structured download list through IDM (Internet Download Manager), enabling high-volume log retrieval through automated batch downloads.
Additionally, the wiki contained a section dedicated to build generation, walking customers through configuring their desired payload settings. Screenshots showed parameters for selecting build versions, adjusting stealer behaviors, and generating the final executable. This exposed part of the internal toolchain used to produce customized stealer builds for each subscribed operator.
Most of the pages were last updated around mid-2023, indicating an actively maintained documentation ecosystem throughout that period. The wiki’s level of detail, combined with a clean, organized layout, demonstrated that Rhadamanthys operated more like a structured SaaS-style service than a one-off malware project.
Communication & Operator Infrastructure
Rhadamanthys maintained a broad communication footprint across multiple encrypted and semi-public platforms, allowing its operator to interact with buyers, issue updates, and provide customer support. Using StealthMole, several consistent identifiers surfaced that collectively mapped the stealer’s communication ecosystem. These channels offered critical insight into how the operation sustained its market presence and managed user interactions.
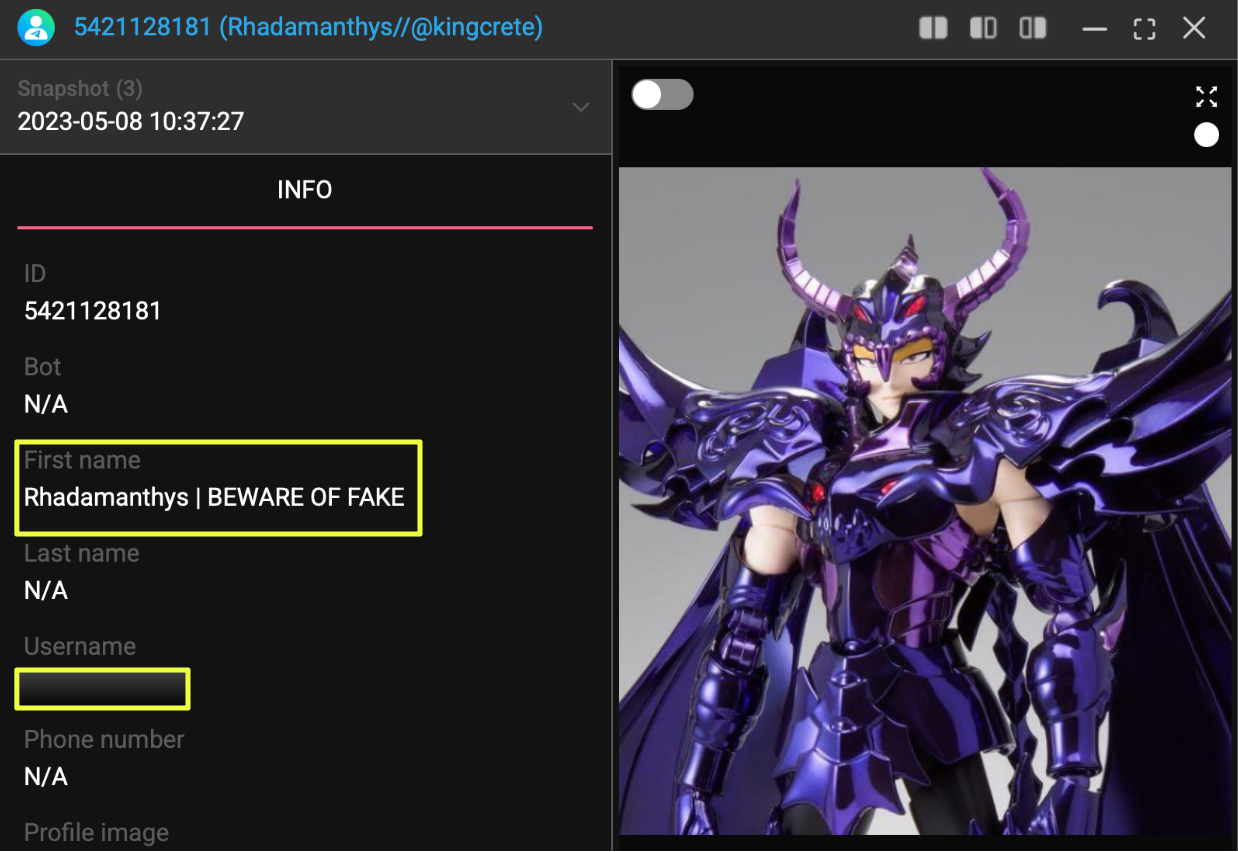
The primary contact channel promoted on the Rhadamanthys website was Telegram, where a linked group functioned as the main hub for inquiries and announcements. StealthMole’s Telegram Tracker revealed additional activity tied to the same ecosystem, including messages posted by the user titled “Rhadamanthys | BEWARE OF FAKE //@K********e” inside other channels. This handle, which incorporated the operator’s known alias, appeared repeatedly across multiple platform traces, reinforcing Telegram’s role as an active node in the stealer’s support structure.
- https://t.me/rh*******q
- https://t.me/K********e
- https://t.me/K****e2025
- https://t.me/K******e35
- https://t.me/rh*******q
- https://t.me/rh*******r
Beyond Telegram, the operation relied on encrypted messaging protocols designed to preserve anonymity. One of the most significant identifiers was a TOX ID, discovered through StealthMole’s correlation engine:
- 5B************************************************************9

This TOX ID surfaced again in an archived BDF Club thread attributed to suspected operator K********e, where it was listed as an official contact channel for purchasing and support. The presence of this identifier across both the forum and the broader ecosystem demonstrated consistency in the operator’s communication methods over time.
The investigation also uncovered multiple XMPP (Jabber) accounts, each tied to the same operator identity. These included:
- rha*********s@exploit.im
- K********e2025@xabber.de
- K********e2022@thesecure.biz
Each of these addresses appeared separately across hidden-service metadata, historical listings, and customer-facing materials. Their structure and distribution suggested that XMPP served as a secondary communication layer, particularly for higher-sensitivity exchanges or for users preferring non-Telegram channels.
Taken together, these communication channels formed a decentralized but coherent network centered on the operator known as “K********e.” The repetition of the same identifiers across Telegram, TOX, XMPP, and older forum posts indicated a long-running operational pattern rather than fragmented or temporary identities. This structure served as the connective tissue of the Rhadamanthys ecosystem, enabling support, sales, and coordination across its lifespan.
Operator Profiling: K********e
Throughout the investigation, the alias “K********e” emerged as the most consistently referenced identity across Rhadamanthys-related infrastructure, communication channels, and historical forum activity. Using StealthMole’s Telegram and darkweb tracking tools, multiple traces connected this alias directly to the operation’s sales, support, and distribution channels, forming a clear focal point for understanding the stealer’s operator.
One of the most substantial data sources tied to this alias came from an archived BDF Club thread dated October 2022, where K********e served as the author of a full sales post advertising Rhadamanthys. This thread included extensive product descriptions, screenshots of early panel versions, feature lists, licensing terms, and payment information. The presentation style closely mirrored the structure observed on the primary Rhadamanthys website, suggesting a consistent approach to how the operator marketed the stealer across different platforms.
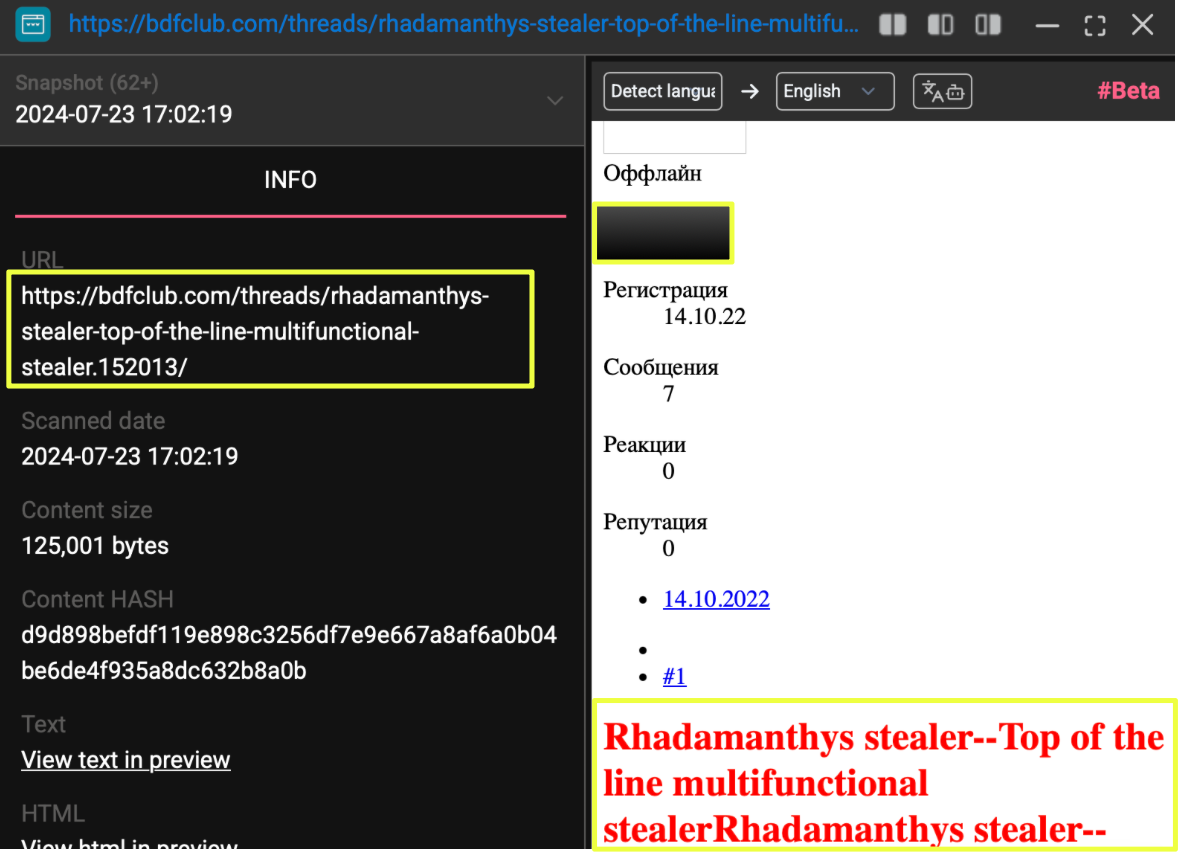
The thread showed K********e describing Rhadamanthys as a modular, actively maintained product with support for browser credential theft, cryptocurrency wallet extraction, system reconnaissance, and multiple export formats. The post also contained lists of supported wallets, messengers, FTP clients, and password managers, written in a matter-of-fact style that aligned with the technical documentation found later on the wiki. This overlap between the older forum material and the more recent internal documentation highlighted a continuity in the operator’s presentation of the product.
Licensing details in the thread matched the pricing tiers visible on the primary website, offering weekly, monthly, and lifetime access options payable in cryptocurrency. The payment model was accompanied by terms of service emphasizing restrictions on redistribution, cracking attempts, and VirusTotal submissions, reflecting an effort to preserve the operational integrity of the stealer.
Communication information included in the post aligned with the identifiers discovered elsewhere in the ecosystem. The thread listed the same TOX ID found via StealthMole, and contact details consistent with the messaging channels tied to K********e in the later stages of the investigation. This reinforced the conclusion that the same operator maintained a stable identity across forums, hidden services, and encrypted communication platforms.
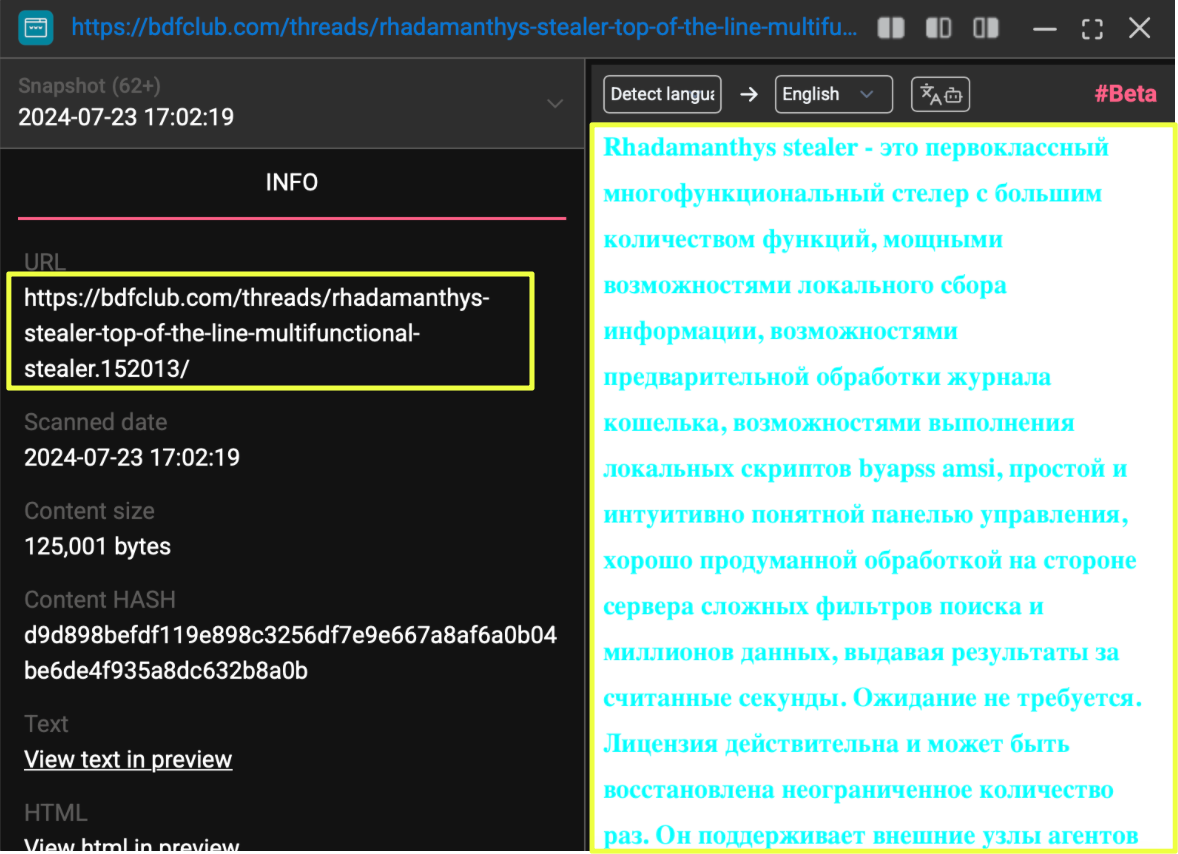
At the end of the thread, a Russian-language duplicate of the same information appeared, repeating the product features, terms, and contact instructions. The presence of two full-language versions suggested an intention to reach a broader audience within the underground marketplace, rather than limiting the offering to English-speaking buyers.
Conclusion
The 2025 phase of Operation Endgame created a rare moment of visibility into long-running malware ecosystems, and Rhadamanthys stood out as one of the most structurally organized among them. By using StealthMole’s historical indexing, darkweb tracking, and telegram tracking tools, this investigation was able to reconstruct how the stealer operated across its primary website, technical wiki, encrypted communication channels, and earlier forum activity.
The now-seized domains provided the initial entry points, but it was the consistency of identifiers: the same handles, contact methods, and technical materials appearing across multiple platforms and time periods, that ultimately revealed the underlying cohesion of the Rhadamanthys operation. The alias “K********e” remained central throughout, reflecting a stable operator identity that persisted across darkweb sites, Telegram channels, TOX, XMPP accounts, and legacy marketplace posts.
While the takedown removed the active infrastructure, the surviving historical traces show that Rhadamanthys functioned as a mature, customer-facing stealer service with layered documentation, structured deployment workflows, and a deliberately maintained communication network. The findings presented in this report capture that ecosystem as it existed prior to Operation Endgame and outline the operational patterns that defined its presence within the underground market.
Editorial Note
As with all darkweb investigations, the findings presented in this report are based solely on observable infrastructure, archived material, and communication traces available through StealthMole’s indexing and correlation tools at the time of analysis. While the report reconstructs the operational ecosystem surrounding Rhadamanthys with a high level of detail, it does so without making assumptions about actors or motivations beyond the evidence captured. Darkweb environments are fluid, and infrastructure can shift quickly; therefore, this report should be viewed as a snapshot of the stealer’s ecosystem leading up to Operation Endgame rather than a definitive account of all activity connected to it.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Infostealer
.svg)
.svg)
.svg)