Revisiting the Lazarus Operator: Mapping Park Jin Hyok’s Digital Footprint Using StealthMole
This investigation revisits the trail of Park Jin Hyok, the North Korean programmer linked to some of the most consequential cyber operations of the past decade, using StealthMole’s darkweb intelligence platform.
In 2022, an anonymous user known as AgainstTheWest released a collection of emails, IPs, and aliases allegedly tied to the Lazarus Group (APT38). Most researchers dismissed it as an echo of the US Department of Justice’s (DOJ) 2018 indictment. However, when those same identifiers were analyzed through StealthMole, a different picture began to surface: one that connected old aliases to new leaks, dormant domains to live servers, and historic front companies to recent credential exposures.
This report does not seek to re-tell the Lazarus story, it reconstructs it. By tracing the remnants of Park’s known infrastructure through Combo Binder, Credential Lookout, and Darkweb Tracker, the investigation uncovers fragments of a network that refused to disappear quietly. Some addresses had long been sanctioned, others forgotten, yet each left behind just enough residue to outline a still-evolving web of identities, domains, and IP trails.
Incident Trigger and Initial Investigation
The investigation began with a trace on a known Ethereum (ETH) wallet previously sanctioned for its role in the Ronin Bridge exploit, an attack attributed to the Lazarus Group. When this address, 0x09************************f96, was queried through StealthMole’s Darkweb Tracker, it returned several associated wallets, each bearing transaction histories consistent with sanctioned clusters.
These addresses included:
- 0x3cf********************************073
- 0xa0***********************************e4b
- 0x53***********************************fc1
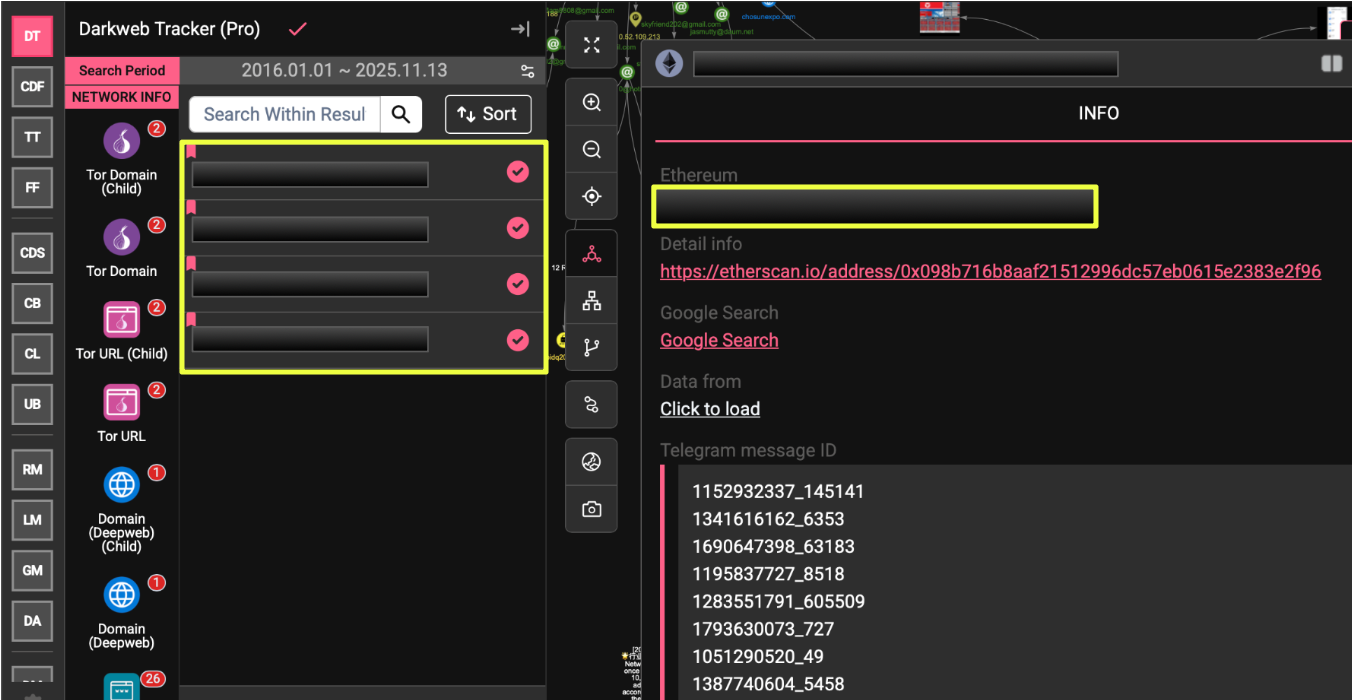
All were tagged as OFAC-sanctioned or Ronin Bridge Exploiter entities on-chain, confirming alignment with previously attributed Lazarus infrastructure. The wallet activity pattern, timestamps, and funding paths matched the broader APT38 laundering model: initial funding from compromised exchanges, consolidation into secondary wallets, and gradual distribution through mixers and bridge contracts.
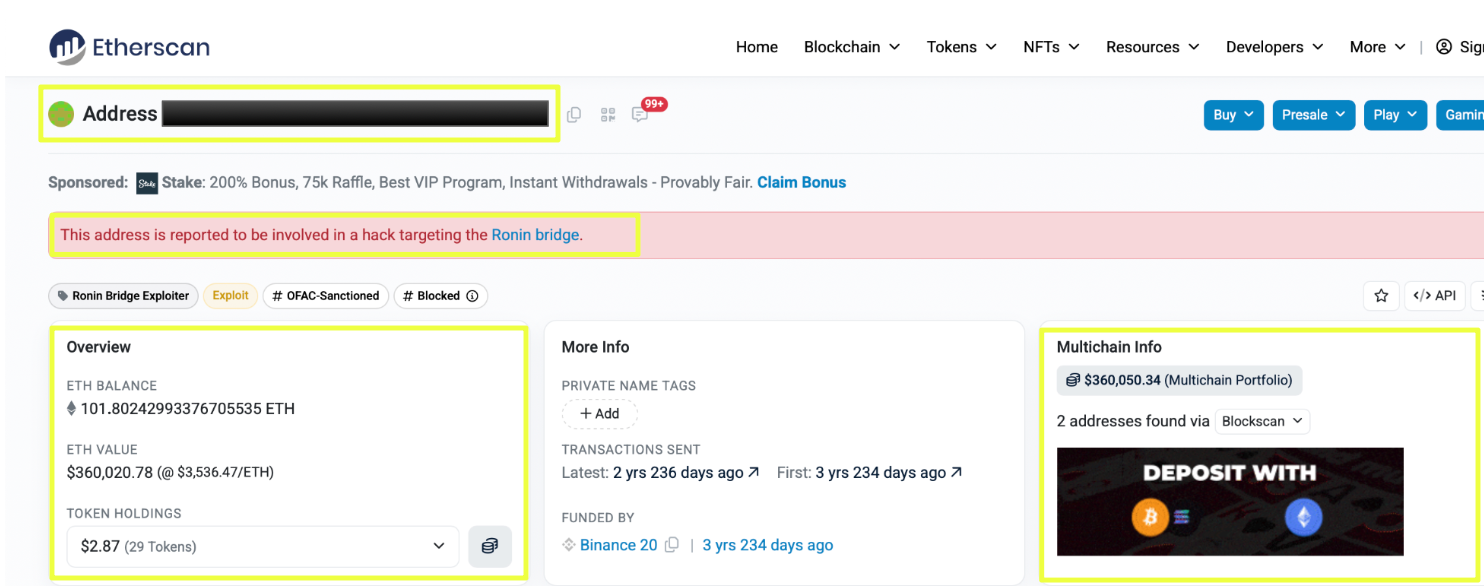
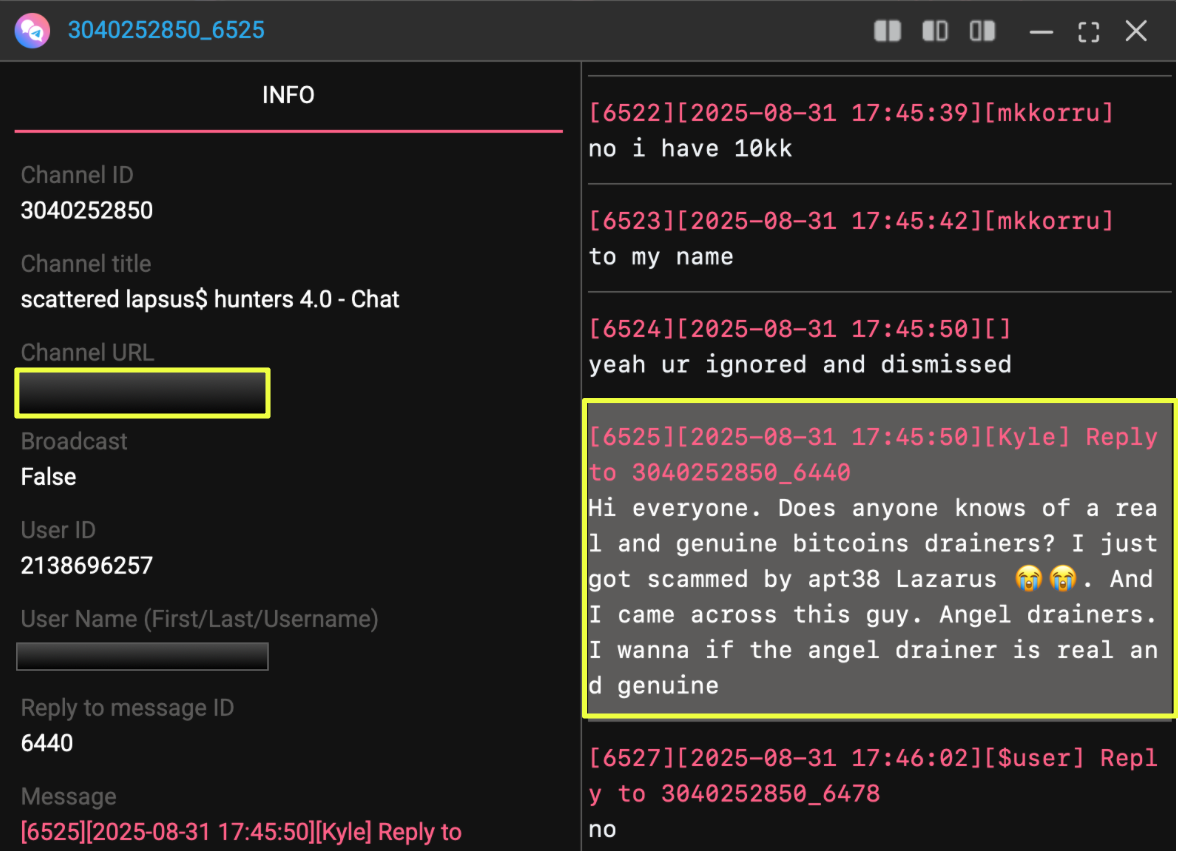
To validate whether these on-chain artifacts could connect to personal identifiers, the investigation pivoted toward off-chain indicators. StealthMole Telegram Tracker was used to surface any mentions of the group, revealing channels discussing Lazarus-linked scams and reposts of the FBI’s wanted bulletin for Park Jin Hyok. These independent mentions established that the operator’s identity remained a live subject of discussion within underground circles, a useful signal for attribution continuity.
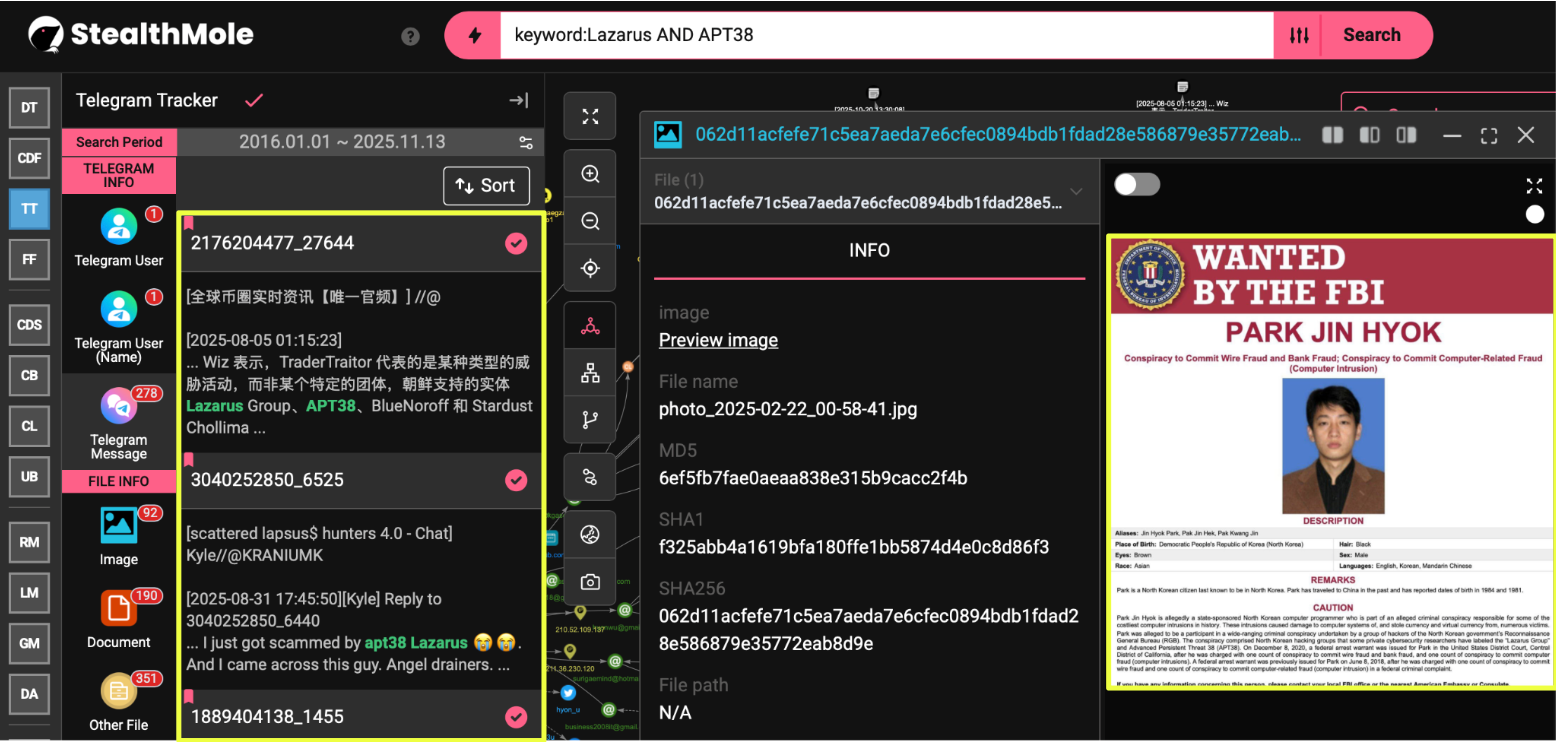
From there, the keyword “Park Jin Hyok” was run through StealthMole’s Darkweb Tracker, returning historical mentions and leaked datasets containing one of the earliest associated email addresses: bu*********it@gmail.com. This discovery served as the pivot point for the next phase, a deep cross-correlation of leaked credentials, IP metadata, and domain associations tied to Park’s alias ecosystem.
Expanded Investigation and Findings
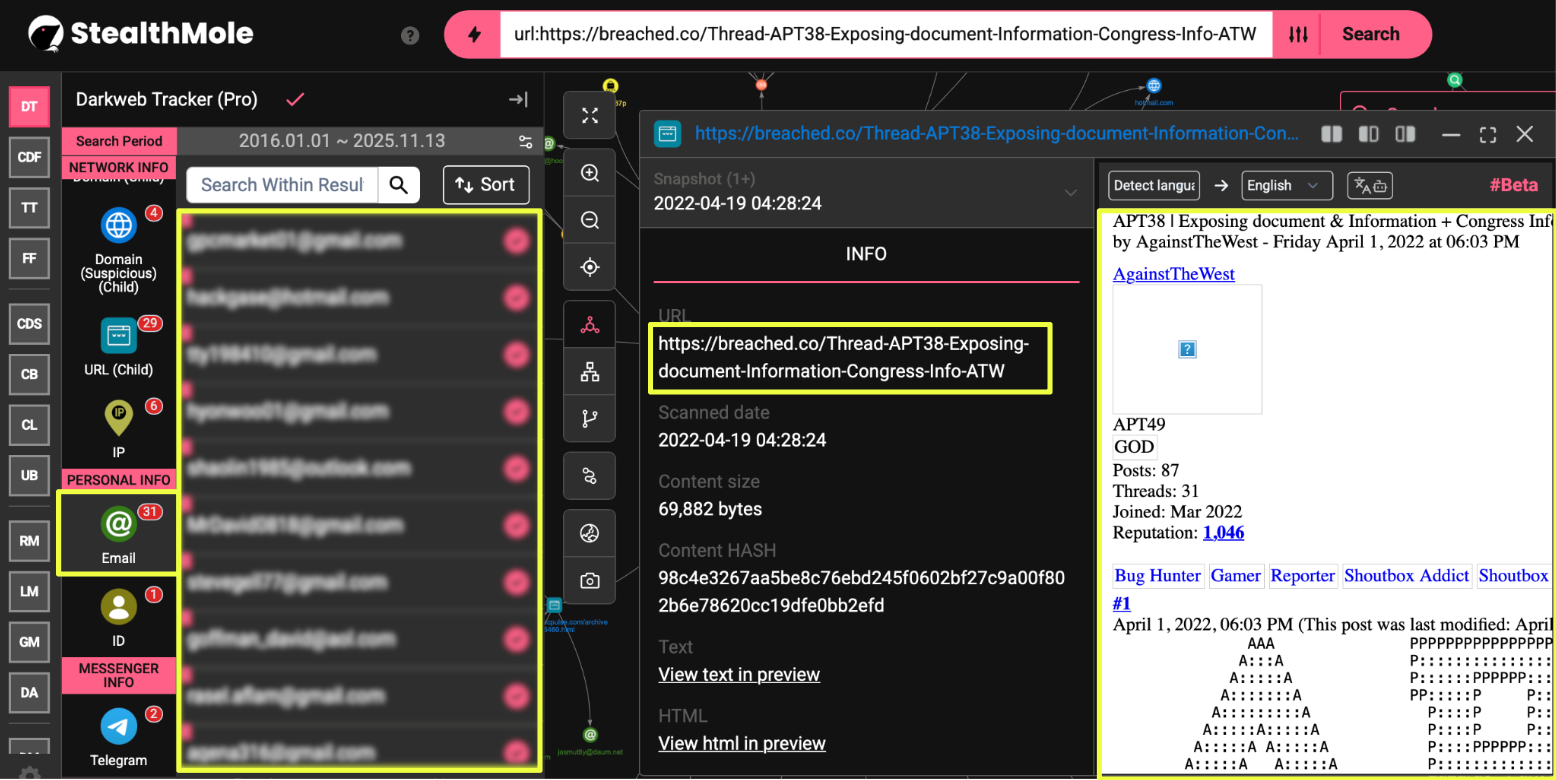
Following the Ethereum wallet correlation, the investigation expanded to examine identifiers historically tied to Park Jin Hyok. The process began with the StealthMole query on the email address bu*********it@gmail.com, which surfaced a 2022 BreachForums thread authored by the user AgainstTheWest (ATW). The post claimed to expose datasets related to APT38 and included a comprehensive list of emails, IP addresses, aliases, and domains allegedly connected to Park and the broader Lazarus network.
While the ATW thread was not new to the intelligence community, its contents provided a valuable foundation for re-validation. Each identifier listed in the post was independently re-run through StealthMole’s Combo Binder, Credential Lookout, ULP, and Compromised Data Set modules. This approach allowed verification of which accounts had appeared in credential leaks after 2022, signaling persistent exposure and possible continued operational or personal use.
Across multiple queries, several addresses including pk******@hotmail.com, su******d@hotmail.com, ha*****e@hotmail.com, and h****_u@hotmail.com, returned new credential leak results extending into 2024 and 2025. These findings indicate that the original identifiers were not isolated to legacy datasets but have re-emerged in newer breach compilations. This pattern suggests either ongoing credential reuse, alias persistence across different operations, or the continued recycling of Lazarus-linked data within underground trading communities.
Parallel to the email correlation, StealthMole’s Darkweb Tracker identified Telegram discussions and reposts referencing Lazarus Group, APT38, and Park Jin Hyok. Channels such as t.me/fr*****d, t.me/bi****jr, and t.me/laz*****ic contained repeated mentions of the group’s past exploits, including community warnings about scams allegedly conducted under the “Lazarus” label. While these channels do not provide direct attribution, their visibility reinforces that Lazarus-linked narratives remain active within dark-web ecosystems.
To verify the infrastructure components, the domain hoonet.com, publicly known as the operational facade of the Chosun Expo Joint Venture, was run through StealthMole’s Combo Binder. The search returned 26 credential entries tied to internal mailboxes such as r*****@hoonet.com and r*****k@hoonet.com. Although these accounts do not directly overlap with Park’s known aliases, the timeline continuity and domain ownership align closely with Chosun Expo’s historical operations, further connecting the dataset to the Lazarus infrastructure ecosystem.
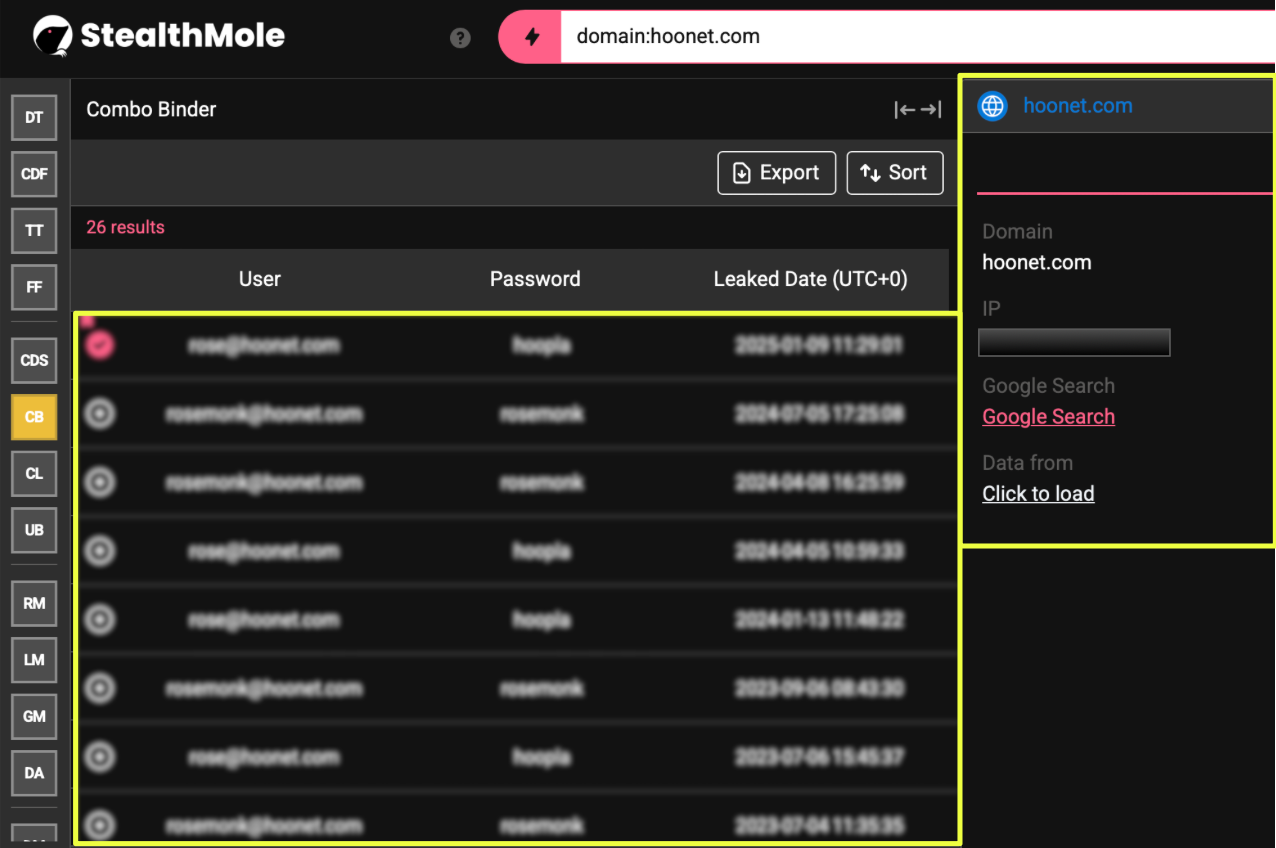
Taken together, the findings highlight how fragments from old disclosures can retain analytical value when cross-verified through modern datasets. Each confirmed overlap adds credibility to the persistence of the Lazarus digital ecosystem, emphasizing the group’s long-term operational continuity across both cryptocurrency and credential-based activity.
Infrastructure Correlation and Analysis
With the verified datasets in place, the next phase focused on establishing infrastructure continuity, linking the accounts, domains, and IP ranges to known Lazarus and APT38 operations. Using StealthMole’s integrated tools, each verified indicator was cross-referenced across DNS, WHOIS, and credential datasets to identify overlapping ownership patterns and operational signatures.
1. Credential Exposure Analysis
StealthMole’s Combo Binder, Credential Lookout, and Compromised Data Set (CDS) modules revealed recurring exposure patterns across multiple Lazarus-linked email addresses. Each entry was cross-checked for leak source, date range, and password reuse, establishing continuity between historical identifiers and recent breach activity.
| Email Address | Passwords | Timeline |
| pia*******23@163.com | $1$8************1 | Oct 2016; Oct 2020 |
| pkj******0@hotmail.com | a***********r | Leaked 12 Times Between April 2021 and February 2025 |
| jon*********2@gmail.com | "j******u" | April 2016 |
| sur*********d@hotmail.com | Pg******5; 1*****4; pg**********@ | Leaked 23 Times Between December 2022 and February 2025 |
| ha********e@hotmail.com | mD********D; md********d; "ha*********e; GO************= | Leaked 11 Times Between Oct 2013 and February 2025 |
| hy*****_u@hotmail.com | 1q**********r | Leaked Twice Between July 2023 and February 2025 |
| gp*********3@gmail.com | Gp*********3 | July 2023 |
All seven email accounts originally cited in the ATW breach resurfaced in recent (2023–2025) credential datasets. The recurrence of these identifiers, especially those tied to Chosun Expo (gpcmarket) and Lazarus-linked aliases (hyon_u, hackgase), demonstrates operational persistence rather than isolated historical exposure. The combination of old and new leaks indicates ongoing credential circulation, either through data reuse by the actor or continued underground redistribution of legacy dumps.
2. Domain and Corporate Infrastructure
Domain analysis confirmed a recurring link between the Chosun Expo Joint Venture and its associated domain hoonet.com, both previously documented as Lazarus front entities. StealthMole’s Combo Binder results revealed multiple internal @hoonet.com accounts exposed between 2022 and 2025.
| Domain / Entity | Associated Accounts | Leak | Timeline | Observed Patterns | Notes |
| hoonet.com | r******@hoonet.com, ro****k@hoonet.com, nik******e@hoonet.com | 26 | 2022-2025 | Shared weak credential reuse (ro*****k, 12*****p) | Domain historically owned by Chosun Expo JV; modern exposures indicate post-sanction persistence. |
| chosunexpo.com | No direct leaks found | — | — | Domain inactive but referenced in prior DOJ filings | Front entity of Lazarus; infrastructure inactive but continues to appear in secondary references. |
| oiaglobal.com | Referenced (no confirmed ownership) | — | — | Possibly spoofed or third-party used for relay | Requires further correlation to confirm association. |
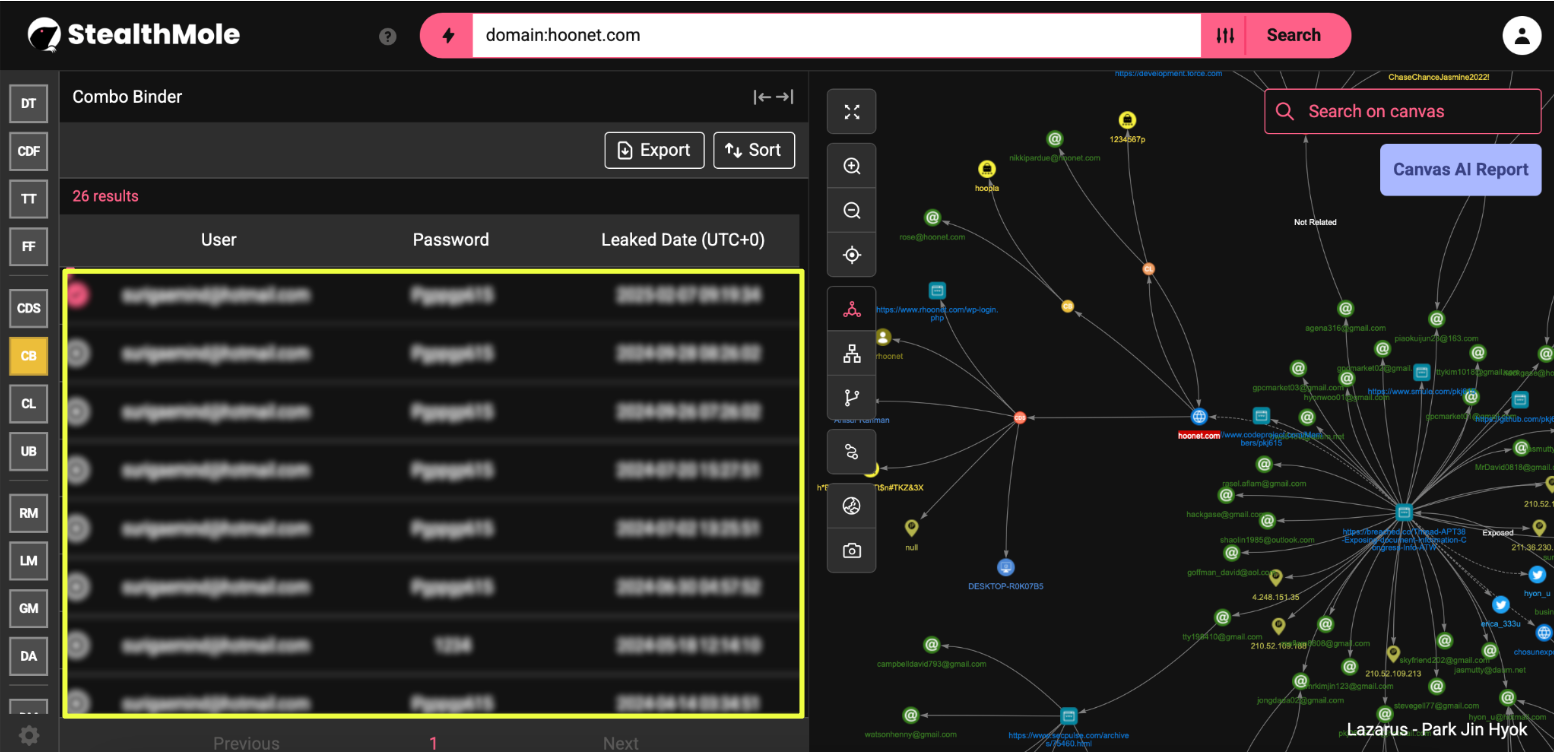
The persistence of hoonet.com credentials long after its documented role as a Chosun Expo front strongly supports the hypothesis of infrastructure recycling. Even if no active hosting remains, its digital footprint continues to appear in modern combo lists and leak aggregations, suggesting reuse by derivative operators or persistence within underground data ecosystems.
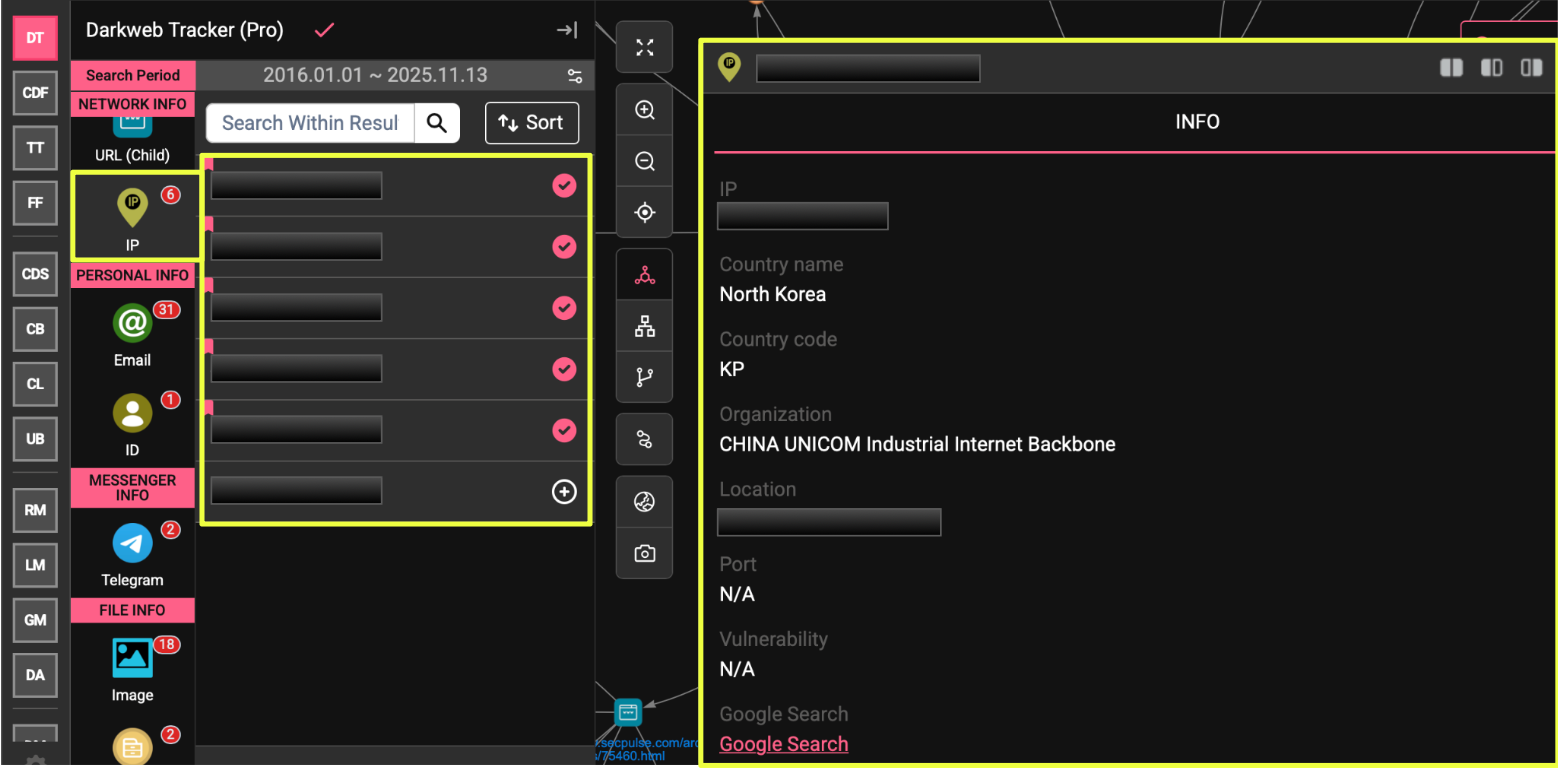
3. Network Infrastructure and IP Correlation
IP intelligence provided additional validation of legacy Lazarus connectivity, matching known North Korea–linked and Chinese backbone addresses attributed to Chosun Expo operations.
| IP Address | Origin / ASN | Country | Attribution Context | Notes |
| 2**.5*.**9.1*7 | China Unicom Industrial Internet Backbone | CN | Recurrent in Lazarus operational ranges | Strong correlation with DPRK-linked network infrastructure. |
| 2**.5*.**9.**8 | China Unicom Industrial Internet Backbone | CN | Identified in 2022 breach and corroborated in StealthMole data | Confirmed Lazarus network artifact. |
| 2**.*2.**9.**3 | China Unicom Industrial Internet Backbone | CN | Matches Chosun Expo operational IP block | Direct alignment with historic Lazarus indicators. |
| 2**.*6.**0.1*0 | LG DACOM Corporation | KR | Likely external relay or test node | Possible intermediary node; requires further review. |
| 4.**8.**1.*5 | Microsoft Corp. (Azure) | US | Possible transient proxy or decoy | May represent external hosting during transient operations. |
Taken together, the credential leaks, domain persistence, and IP correlations form a multi-dimensional dataset pointing to long-term survivability and adaptation within the Lazarus infrastructure.
While no single artifact conclusively confirms present-day actor activity, the aggregate evidence suggests that portions of the group’s operational footprint have remained active, repurposed, or unintentionally preserved across dark-web ecosystems.
Assessment
The collected evidence reinforces long-standing attributions connecting Park Jin Hyok and the Lazarus Group (APT38) to the broader infrastructure of Chosun Expo Joint Venture and its related digital assets. By revalidating previously known identifiers through StealthMole’s datasets, this investigation demonstrates that many of the group’s legacy elements, once thought to be inactive, continue to appear within contemporary leak and infrastructure records.
The findings do not introduce a new actor attribution but rather solidify and modernize an existing one. Multiple indicators, including reused email aliases (pk*****0@hotmail.com, hy***_u@hotmail.com, ha*****e@hotmail.com) and persistent infrastructure markers present clear continuity with the digital footprint documented in the 2018 U.S. Department of Justice indictment and the 2022 BreachForums dataset released by AgainstTheWest.
However, while this overlap substantiates Lazarus’ enduring infrastructure presence, it does not confirm current operator activity. Some identifiers may persist through data recirculation, archival breaches, or community reuse rather than through direct operational maintenance by DPRK entities.
Overall, the evidence establishes a high-confidence linkage between historical Lazarus identifiers and present-day data exposures. The persistence of known emails, domain artifacts, and IP blocks within StealthMole’s 2023–2025 datasets confirms that parts of this infrastructure remain discoverable and, potentially, intermittently utilized.
Conclusion
This investigation reaffirms that the digital footprint of Park Jin Hyok and the Lazarus Group (APT38) continues to manifest across modern dark-web and credential datasets. By re-examining legacy indicators through StealthMole’s analytical environment, fragments once confined to historical reports were correlated with fresh exposures, uncovering a clear pattern of infrastructure persistence and identifier reuse spanning more than a decade.
The convergence of credential leaks, domain metadata, and network indicators demonstrates that elements of Lazarus’ infrastructure have not entirely disappeared from the digital landscape. Instead, they continue to resurface across successive breach compilations and leak forums, suggesting either ongoing reuse by Lazarus-linked operators or sustained circulation of their historical assets within the underground ecosystem.
While none of the evidence points to active campaigns directly attributable to Park Jin Hyok at present, the persistence of these artifacts highlights the enduring analytical relevance of legacy indicators. What were once static evidentiary fragments now serve as dynamic correlation anchors for identifying derivative or successor operations.
The Lazarus infrastructure, though fractured and partially dormant, remains traceable in pieces. Each fragment contributes to the broader understanding of how state-linked actors preserve, repurpose, and outlive their exposed assets in the evolving threat landscape.
Editorial Note
As with all dark-web investigations, attribution remains an evolving process rather than a definitive conclusion. While the evidence presented here draws strong technical and temporal links between historical Lazarus infrastructure and modern data exposures, such connections must be interpreted within the broader context of data reuse, false flagging, and leak recirculation common in the underground ecosystem.
This analysis reflects a moment in time, a reconstruction based on available datasets, corroborated evidence, and StealthMole’s intelligence capabilities. Future discoveries may either reinforce or refine these linkages as additional sources emerge. The objective of this report is not to claim final attribution, but to demonstrate how methodical data correlation and platform-driven verification can transform historical intelligence into actionable contemporary insight.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: North Korea Threat Actor

.svg)
.svg)
.svg)