SafePay’s Playbook: From Blog Mirrors to File Hosts
Over the past year, the SafePay ransomware group has emerged as one of the most organized and steadily expanding actors on the dark web’s extortion landscape. Since first surfacing in late 2024, SafePay has demonstrated a consistent rhythm of attacks, building an ecosystem that operates more like a self-contained service platform than a loose criminal collective. The group maintains multiple mirrored blogs and dedicated file servers that distribute stolen data, each carefully structured to ensure redundancy and operational continuity even under external pressure.
StealthMole’s analysis of SafePay’s infrastructure, ransom communications, and embedded code artifacts reveals a group focused on control, secrecy, and technical discipline. From subtle traces in its backend scripts to the layered setup of its Tor domains, SafePay’s operations reflect deliberate planning designed to obfuscate identities and safeguard its extortion process. This report draws on dark web intelligence, leaked ransom materials, and StealthMole platform findings to outline how SafePay runs its network, manages victims, and maintains its digital footprint across a shifting landscape of mirrors and hidden servers.
Incident Trigger and Initial Investigation
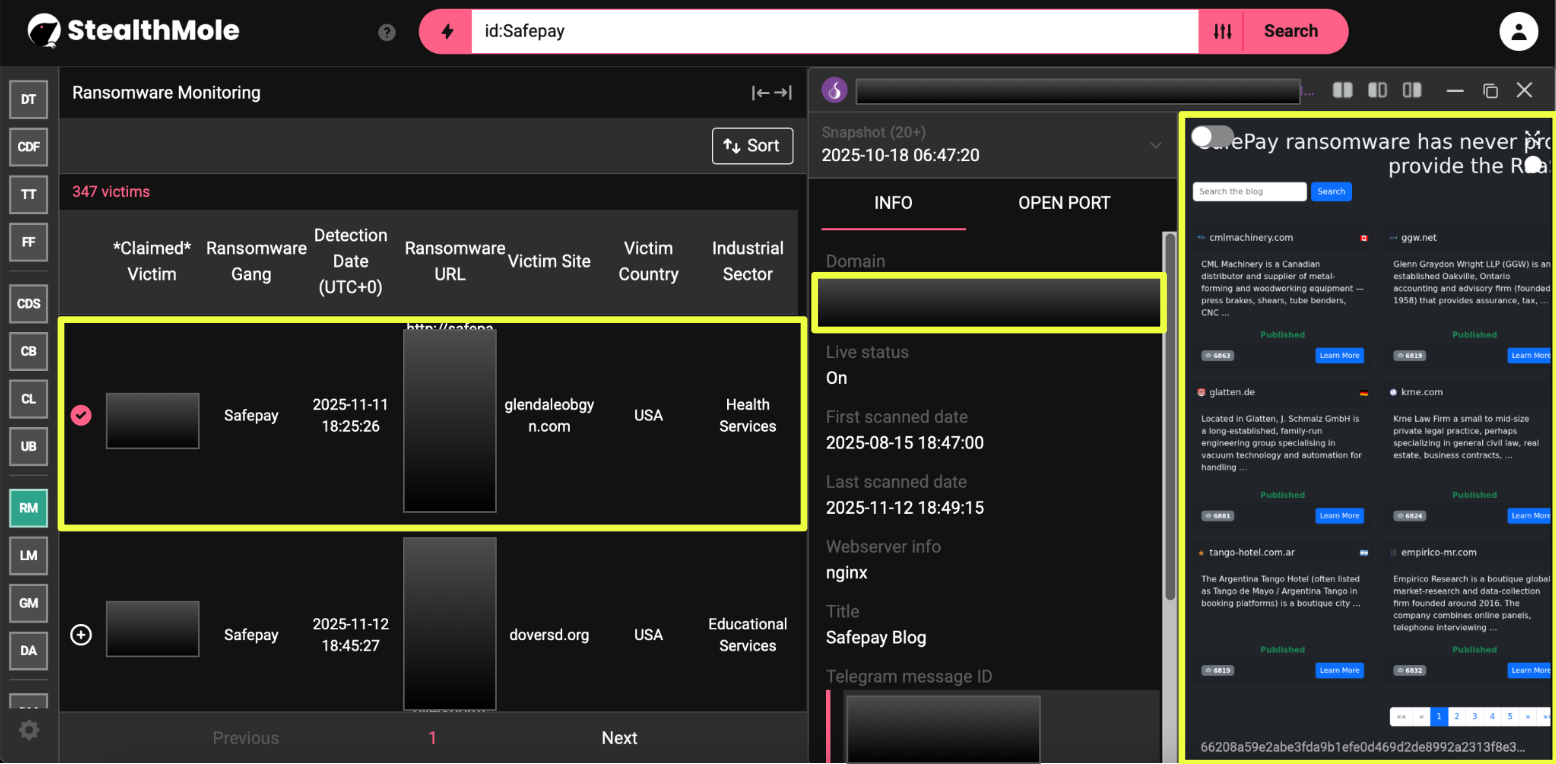
The investigation into SafePay was initiated following a new listing observed on the group’s dark web leak portal in November 2025. The post announced a fresh compromise of g*******gyn.com, a US-based healthcare provider, marking the latest in a long sequence of attacks attributed to SafePay since late 2024. This single event stood out not only because of its timing but because of its context, it appeared amid a rapidly expanding victim roster that has now reached over 340 confirmed organizations across sectors.
- safepay*************************************************oyd.onion
StealthMole’s DarkWeb Tracker was used to trace the G*********N listing back through SafePay’s broader digital footprint. The initial sweep of its primary onion site uncovered an organized web of related domains, mirrored blogs used to announce victims and several dedicated servers hosting stolen data. The structure suggested a deliberate attempt to build redundancy, ensuring SafePay’s presence and extortion mechanisms remain intact even if parts of its network are disrupted or taken down.
The early findings established SafePay as a highly organized actor with a predictable pattern of publication and data exposure. What began as a single-victim observation quickly evolved into a deeper analysis of the group’s infrastructure, content reuse, and operational consistency, forming the basis for the detailed technical mapping presented in the following section.
Infrastructure and Technical Findings
Mapping SafePay’s online infrastructure revealed a deliberately tiered ecosystem built for both resilience and operational anonymity. The group maintains several active and historical onion domains that serve distinct roles within its extortion process. At the top layer are blog-style portals used to publish victim announcements and ransom notes; beneath these sit a network of file-serving nodes, which likely host data exfiltrated from compromised organizations.
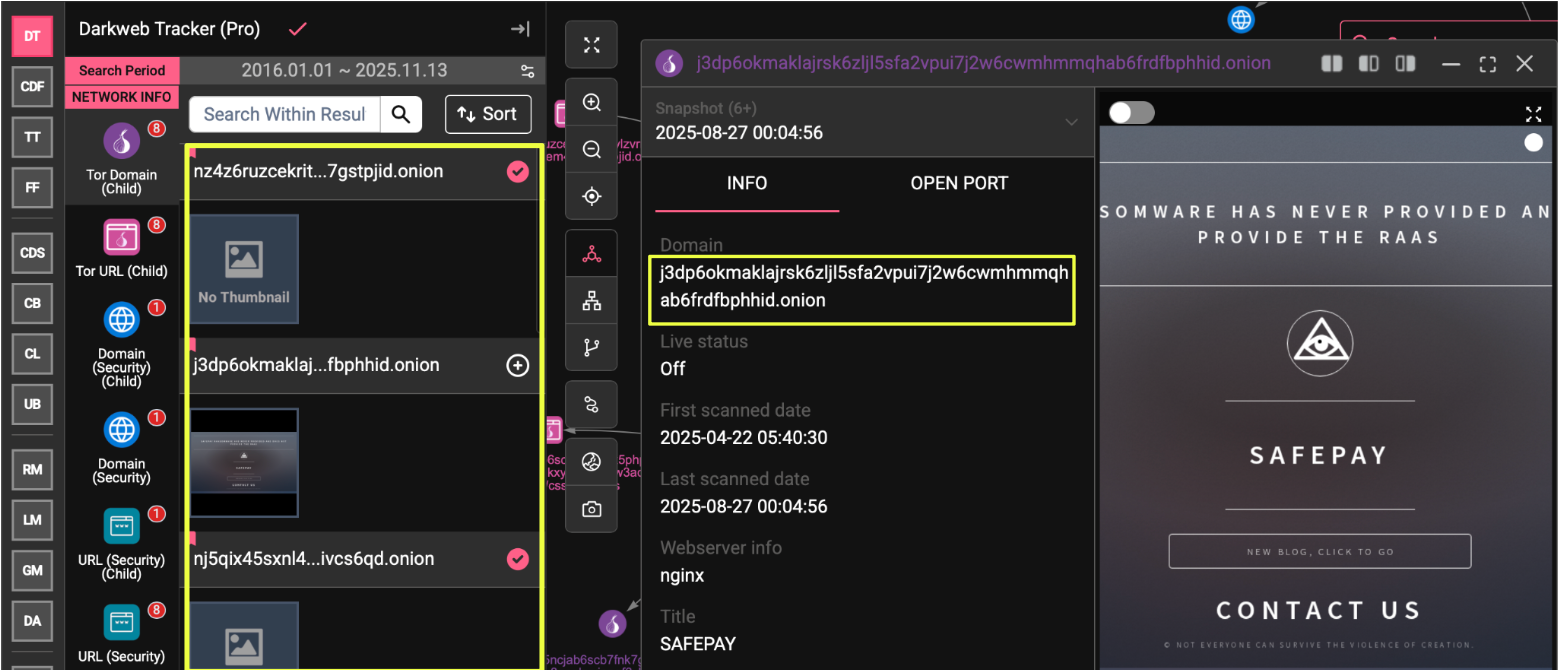
StealthMole’s analysis identified at least eight active onion domains associated with SafePay. Three of these function as blog mirrors, hosting the same set of victim listings, ransom instructions, and public statements. These mirrors share overlapping content hashes and follow identical structural templates, indicating centralized management rather than affiliate-run instances.
- Nj5qix45sxnl4h4og6hcgwengg2oqloj3c2rhc6dpwiofx3jbivcs6qd.onion
- Nz4z6ruzcekriti5cjjiiylzvrmysyqwibxztk6voem4trtx7gstpjid.onion
- j3dp6okmaklajrsk6zljl5sfa2vpui7j2w6cwmhmmqhab6frdfbphhid.onion
The second layer consists of at least five file-serving nodes.
These servers appear to be dedicated repositories for stolen data and may act as staging points for file-sharing with victims or for publishing data dumps after payment deadlines expire. Their layout and naming convention follow the same pattern as other contemporary ransomware leak infrastructures, suggesting SafePay has adopted a modular design consistent with large-scale extortion operations.
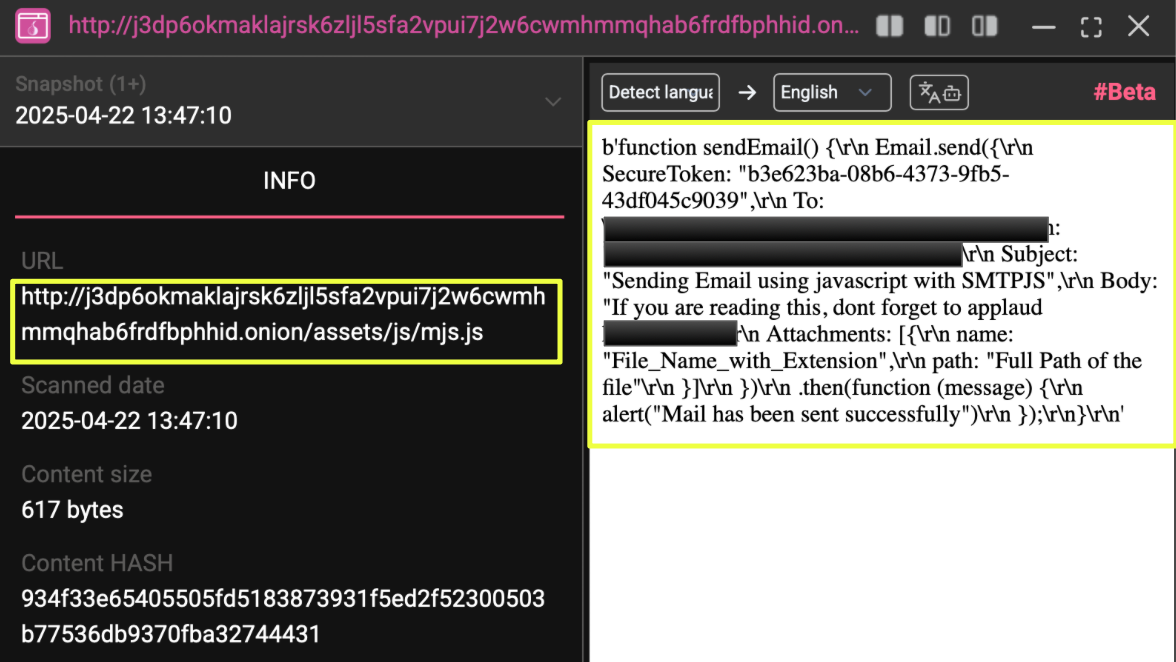
StealthMole’s DarkWeb Tracker revealed further technical consistencies linking these domains. Multiple mirrors contained identical JavaScript and asset hashes, notably a file, which included a ProtonMail address and a hidden developer tag reading “If you are reading this, don’t forget to applaud ka*******72.” While these artifacts alone do not establish attribution, their recurrence across separate mirrors points to shared backend development and a centralized deployment workflow.
- Va**************4@protonmail.com
Overall, these findings demonstrate that SafePay’s infrastructure is not a loose collection of opportunistic servers but a coordinated, version-controlled environment built to sustain long-term operations. The consistent replication of design elements, mirrored content, and embedded code artifacts reflects a level of technical discipline that differentiates SafePay from smaller, affiliate-driven ransomware groups.
Ransom Note and Victim Communication
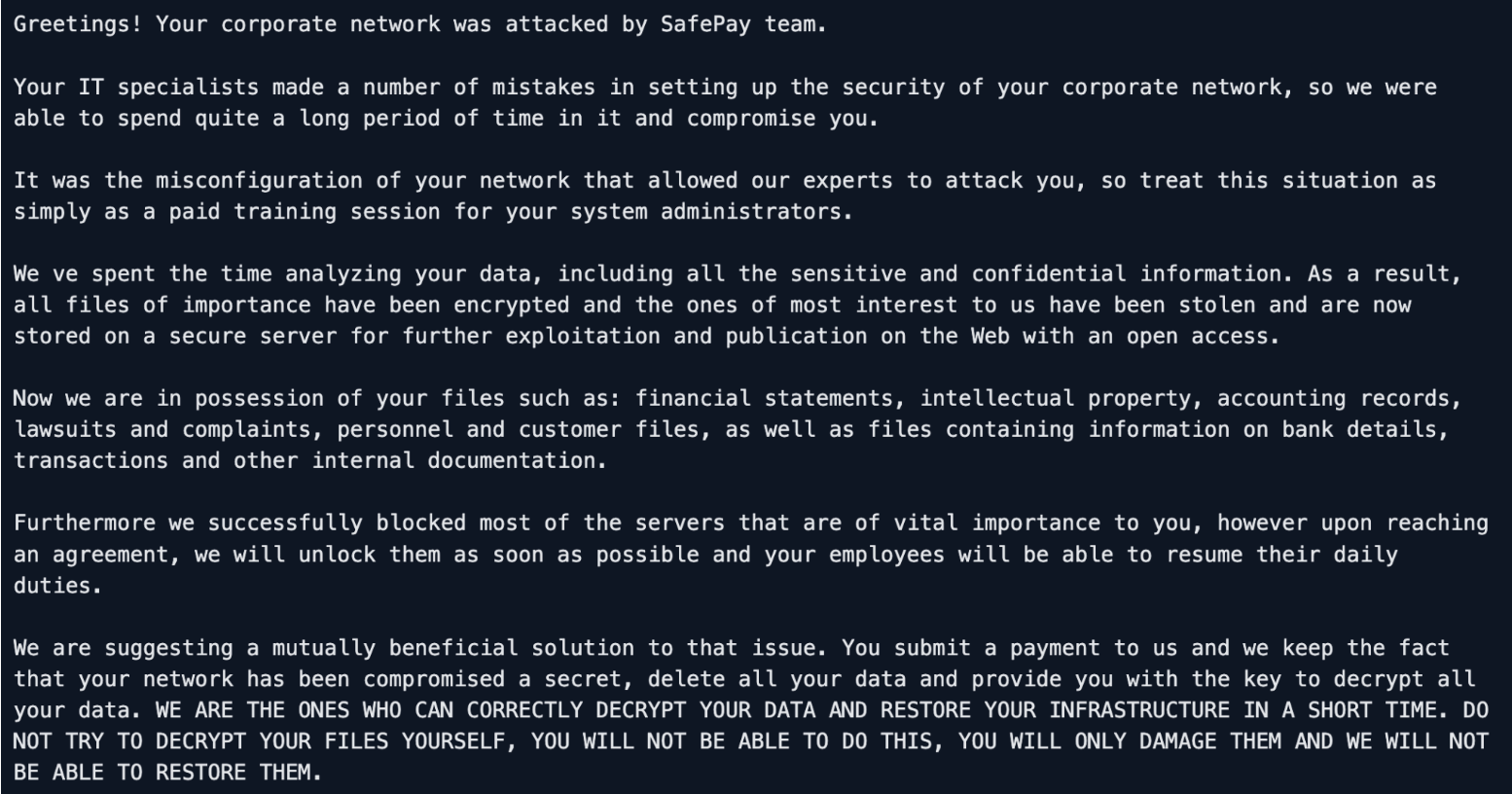
SafePay’s ransom note provides a revealing glimpse into the group’s communication strategy and self-perception. The note opens with a brief statement announcing that the victim’s corporate network has been compromised, followed by an assertion that both encryption and data exfiltration have taken place. Its structure closely mirrors those of other double-extortion operators but stands out for its direct, almost procedural language, written to project professionalism and control rather than overt intimidation.
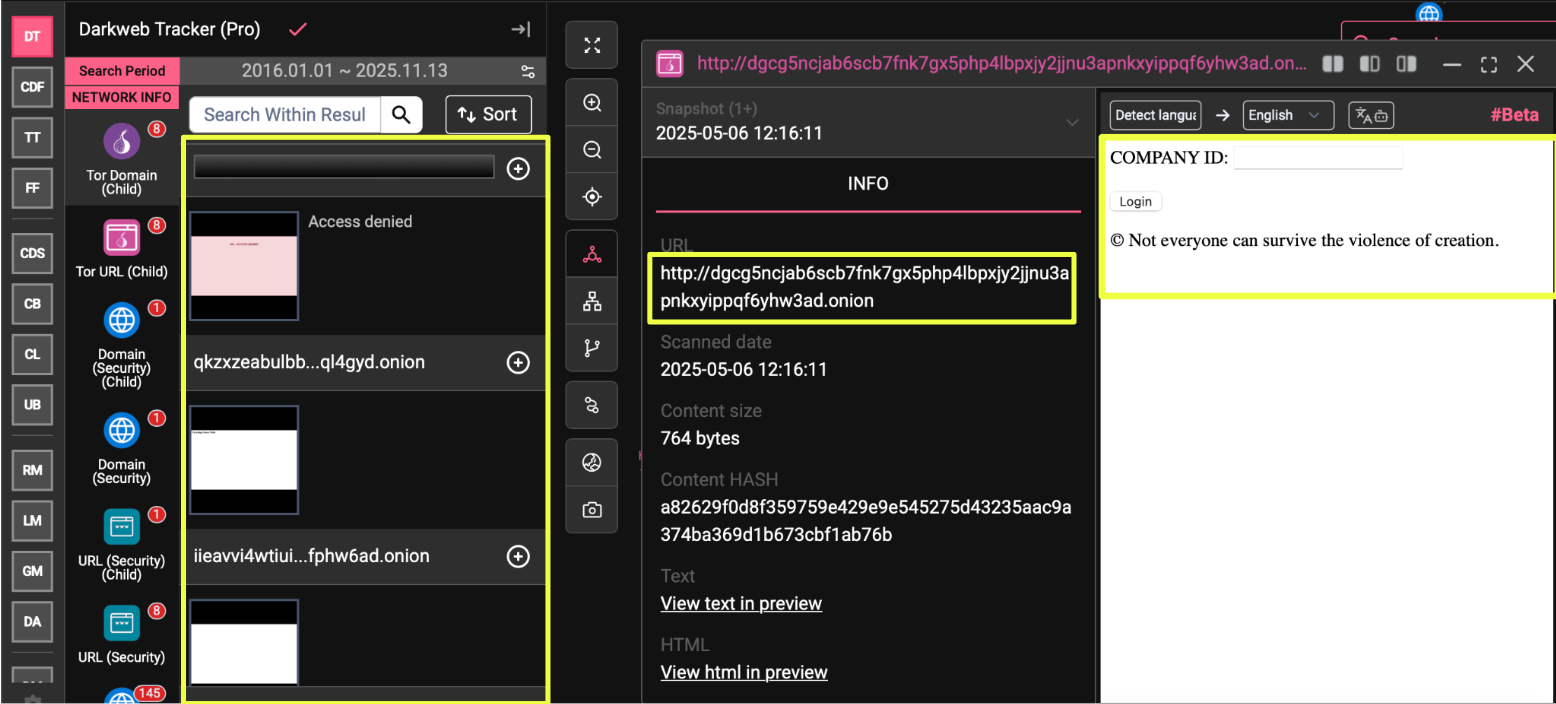
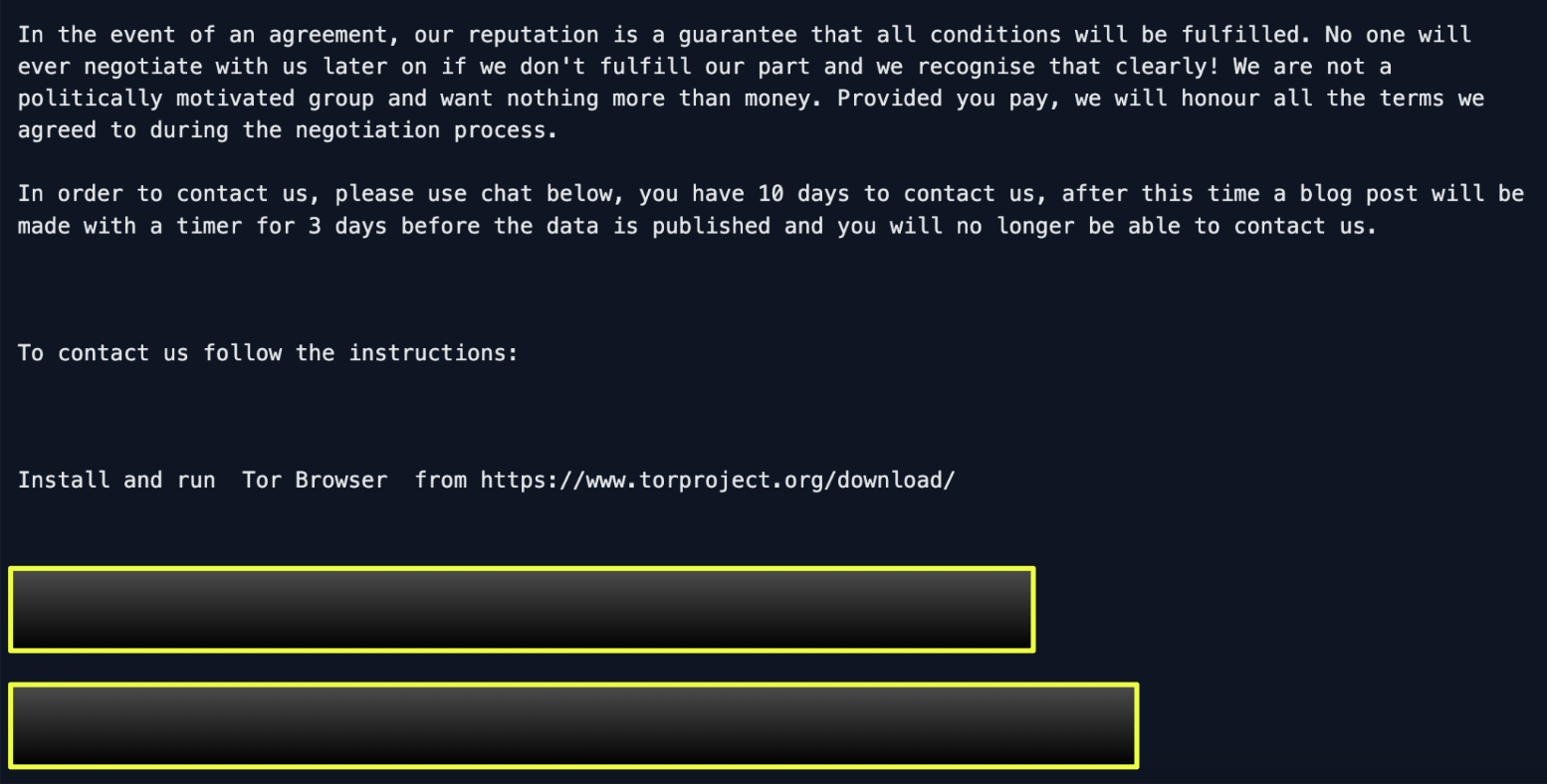
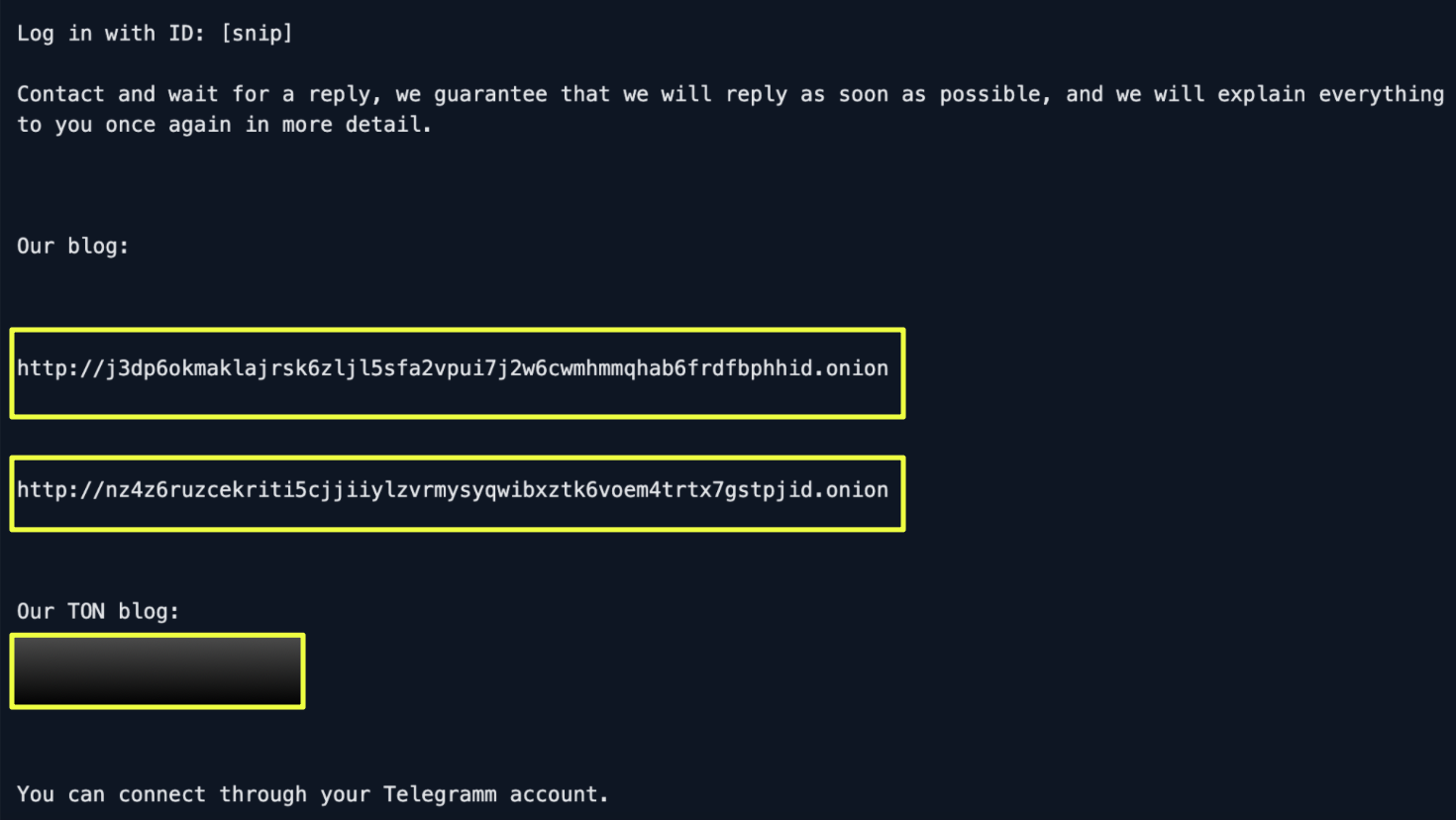
The note instructs victims to access designated portals hosted on two onion domains, where negotiations and payment discussions are expected to occur. Each victim is assigned a unique login ID, which is referenced in the note but not publicly visible, ensuring that communication remains isolated and traceable within the group’s internal system.
- Dgcg5***********************************************3ad.onion
- Oxly5***********************************************2ad.onion
SafePay’s message outlines a 10-day negotiation window, after which a public post is promised on the group’s blog, followed by a 3-day countdown before stolen data is released. This structured timeline suggests an emphasis on predictability and credibility, a tactic designed to maintain pressure on victims while reinforcing the group’s reputation for following through on threats.
Interestingly, the note references Telegram as a secondary communication channel, yet no public handle or link is provided. This omission likely reflects a shift toward controlled, invitation-only interactions, where contact is initiated through the onion portal and moved to private Telegram sessions only after verification. Such a model limits exposure, reducing the risk of impersonation or infiltration while keeping negotiation channels compartmentalized.
The ransom note also references a TON-based site, indicating that SafePay may be experimenting with alternative hosting mechanisms beyond Tor, possibly as redundancy against onion domain takedowns. While the TON entry itself does not appear to be actively used for communication, its inclusion aligns with the group’s strategy of maintaining multiple fallback pathways for victim access.
- tonsitе://s***********.ton
Overall, the tone and structure of SafePay’s ransom note reinforce the impression of an operation that values stability and predictability over spectacle. Its measured language, tiered communication flow, and redundant access channels suggest a businesslike approach, one intended to inspire compliance rather than panic.
Assessment
The collective evidence points to SafePay being a structured and technically disciplined ransomware operation rather than a loose affiliate network. The group’s infrastructure demonstrates clear central management: multiple onion mirrors host identical content and share code-level artifacts, suggesting a unified deployment process maintained by a core team. This level of organization is uncommon among short-lived ransomware brands and implies longer-term operational planning, likely supported by internal tooling and dedicated web development resources.
Unlike many contemporary ransomware collectives, SafePay explicitly states on its leak portal that it has never offered, and does not provide, Ransomware-as-a-Service (RaaS). This self-declaration aligns with the observed technical and behavioral patterns, indicating a closed operational model, where attacks are likely conducted internally by a single, cohesive team rather than by recruited affiliates. The consistency across ransom notes, infrastructure design, and communication tone further supports this claim, as RaaS operations typically exhibit far greater variance between incidents.
SafePay’s decision to maintain separate portals for victim communication and data storage further reflects an emphasis on operational security. By isolating negotiation channels from file-serving infrastructure, the group minimizes traceability and ensures continuity even if one component is compromised. The presence of redundant mirrors, consistent page structures, and fallback mechanisms like the TON reference indicates a focus on resilience, a characteristic typically seen in mature ransomware ecosystems rather than emerging actors.
From a behavioral standpoint, SafePay’s tone, communication patterns, and methodical publishing schedule reinforce its image as a “professionalized” extortion enterprise. The absence of overt aggression in ransom messages, coupled with predictable release timelines, suggests a deliberate effort to position itself as a rational actor, one that prioritizes credibility and reliability to increase the likelihood of victim compliance.
While the embedded code artifacts such as the ProtonMail address and developer tag offer technical fingerprints, they stop short of revealing individual attribution. These fragments, however, confirm a consistent development environment and deployment cycle across mirrors, strengthening the assessment that SafePay operates as a cohesive group rather than a collection of affiliates.
In summary, SafePay represents a medium-to-high maturity ransomware operation distinguished by its stable infrastructure, closed operational model, and controlled communication strategy. Its deliberate avoidance of the RaaS model underscores a preference for centralized control and reduced risk of exposure, traits that position it closer to well-established ransomware collectives than to transient affiliate-driven schemes.
Conclusion
The SafePay investigation reveals a ransomware collective that has evolved beyond opportunistic targeting into a stable, process-driven operation. Its consistent infrastructure design and disciplined disclosure cycle suggest that SafePay’s core strength lies not in innovation but in execution, leveraging reliability and predictability as instruments of coercion. The group’s sustained activity over the past year demonstrates an ability to maintain visibility while avoiding internal leaks or public missteps, a balance few extortion actors achieve for long.
SafePay’s emphasis on centralized control and closed operations reflects a shift in the ransomware ecosystem: fewer public alliances, more private precision. By insulating itself from the risks of affiliate programs and maintaining its own data-leak network, the group has built an ecosystem that is both streamlined and difficult to infiltrate. This structure, coupled with the steady expansion of its victim list, indicates that SafePay is positioned for continued activity into the next operational cycle unless its infrastructure is meaningfully disrupted.
SafePay serves as a reminder that technical resilience and organizational discipline can be as dangerous as advanced tooling. The group’s methods show that the modern ransomware landscape increasingly rewards those who can sustain anonymity and control, not just those who can exploit vulnerabilities.
Editorial Note
As with all dark web investigations, attribution and intent remain probabilistic. While the indicators collected through StealthMole offer a clear view of SafePay’s infrastructure and behavior, the true scale of its internal structure and membership cannot be verified without direct operational access.
The findings in this report are based on observable digital evidence and open-source intelligence rather than law enforcement disclosures or insider testimony. Readers should therefore interpret this assessment as a snapshot of SafePay’s visible ecosystem at the time of analysis, accurate to the data available, but subject to change as the group adapts its tactics and infrastructure.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Malicious Group

.svg)
.svg)
.svg)