A Family, Not a Team: Deconstructing Hacktivist of Garuda’s Operational Infrastructure
Hacktivist of Garuda (HoG) presents itself as a single collective, but the evidence tells a far more layered story. What began as a minor Indonesian defacement crew has grown into a sprawling hacktivist ecosystem operating across Telegram, abandoned Twitter accounts, buried defacement mirrors, and a revolving door of individual operators who all work under the same banner, sometimes in harmony, sometimes not at all. Their activity spans political campaigns, opportunistic intrusions, and moments of unexpected sophistication, producing a footprint that is far larger than their public image suggests.
Using StealthMole’s darkweb, Telegram, and defacement intelligence tools, we traced HoG’s evolution from early 2022 through 2025. The investigation surfaced official channels, operator chatter, recycled infrastructure, mid-level data leaks, and a pattern of ideological messaging that shifts depending on which operator is speaking that day. Over two hundred confirmed defacements, some claimed by the group, many carried out by individual members, reveal a decentralized actor model that makes HoG both noisy and difficult to pin down.
This report follows that trail: who they are, how they talk, what they target, and how their infrastructure fits together. The sections ahead connect the scattered pieces into a coherent picture of a hacktivist label that functions less like a team and more like a loose cyber-family, one whose influence has quietly expanded across Southeast Asia’s hacktivist landscape.
Incident Trigger & Initial Discovery
The investigation began with a simple query: “Hacktivist of Garuda” run through StealthMole’s DarkWeb Tracker. At first glance, the results suggested an obscure Indonesian defacement crew with scattered mentions across low-traffic forums. But the deeper we pushed the keyword, the more the picture shifted. What looked like a fringe actor began resurfacing across Telegram archives, suspended Twitter accounts, forgotten Zone-H mirrors, and traces of data leaks posted under half-finished aliases.
The real turning point came when StealthMole’s Defacement Alert tool attributed a concentrated cluster of intrusions to the HoG name. The volume didn’t match their public presence; it hinted at a network operating under shared branding rather than a single operator. This prompted secondary pivots: first into Telegram infrastructure, then into darkweb forum activity, where the group’s ideological contradictions and multi-operator fingerprints started to appear.
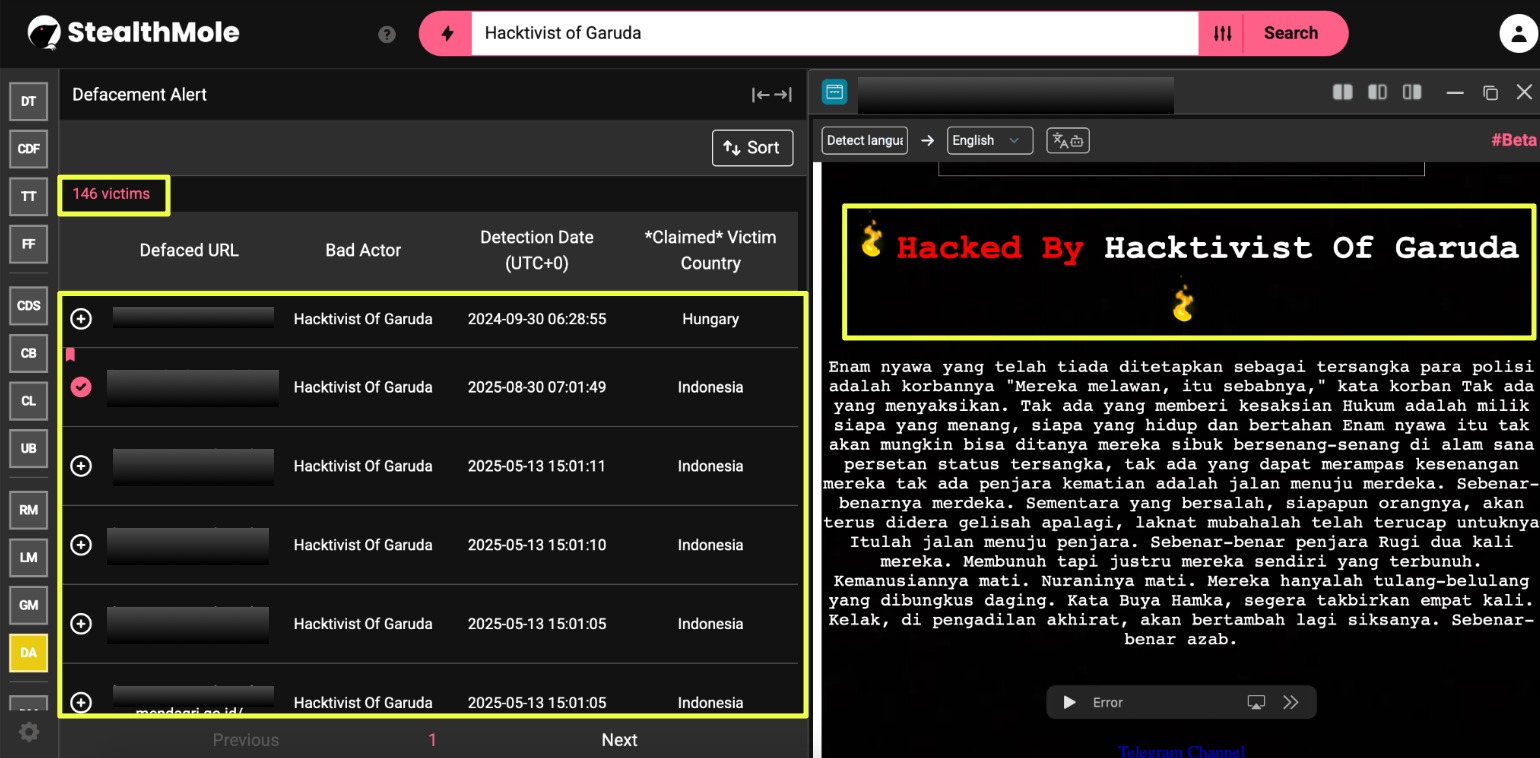
From that initial keyword search, the investigation widened rapidly. Each platform revealed a different side of HoG: political agitation on Telegram, chaotic experimentation on defacement mirrors, and operator-level slip-ups on Breached forums. What began as routine mapping of a minor threat actor quickly unfolded into a deeper examination of a decentralized hacktivist ecosystem hiding behind a single name.
Operational Footprint & Activity Trends
At first glance, Hacktivist of Garuda’s operations appear to follow the familiar rhythm of Southeast Asian defacement crews: opportunistic intrusions, recycled slogans, and a steady stream of compromised websites with flashy banners. But StealthMole reveals a more layered pattern: one that blends political signaling, personal reputation-building, and sporadic attempts at deeper data access.
The group’s public-facing activity is driven largely by defacements, many of which carry ideological messaging that shifts depending on the individual operator behind them. Some intrusions champion pro-Palestine or pro-Muslim narratives, while others present a softer, almost diplomatic tone, framing HoG as a peace-loving collective. This inconsistency is not a flaw in the data, it reflects the reality that HoG functions as an umbrella label used by multiple actors with varying motivations.
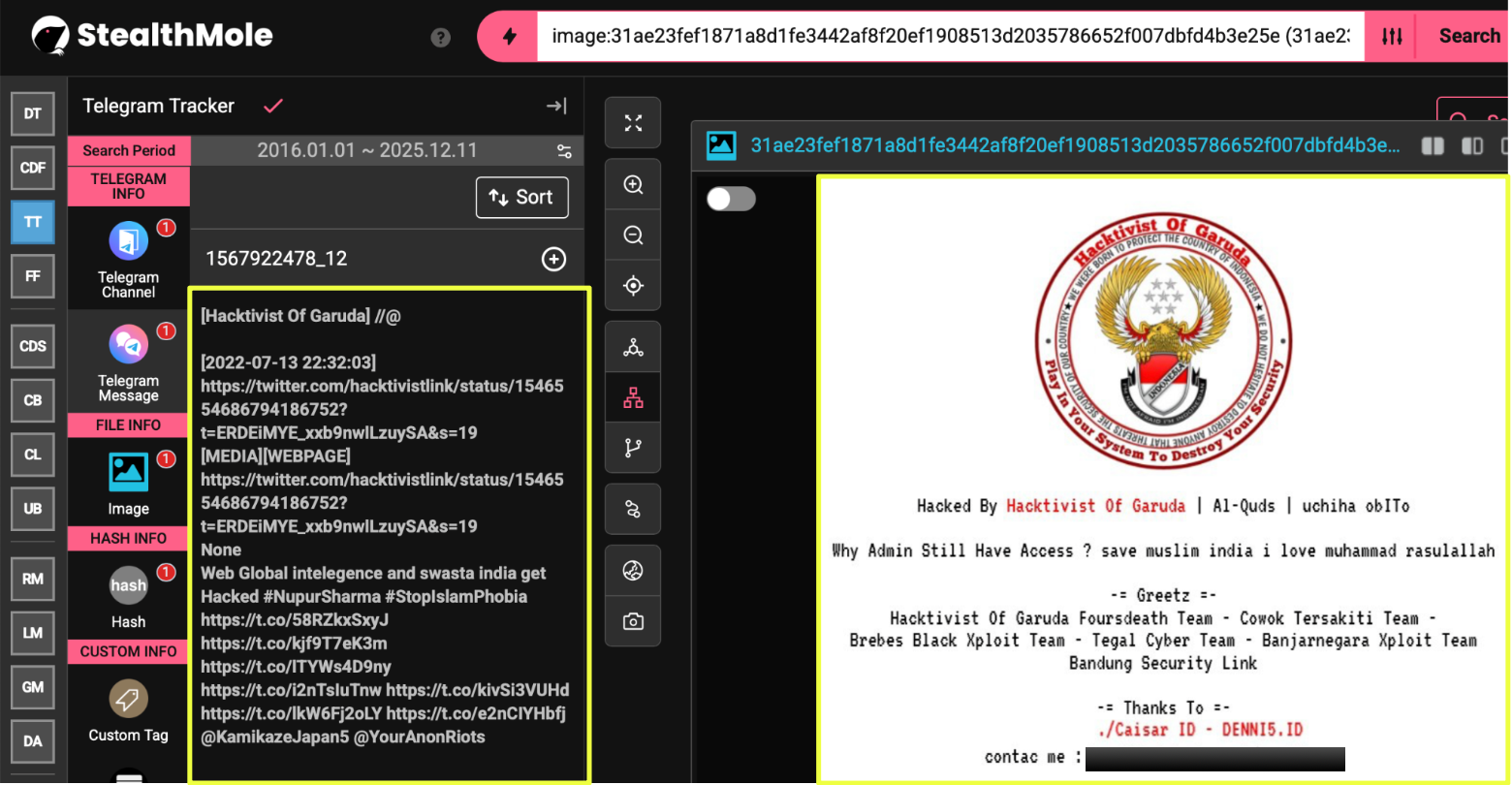
A significant proportion of HoG’s activity is directed at Indian and Israeli websites, ranging from small municipal portals to privately operated services with low security baselines. These targets are selected less for strategic impact and more for the narratives they help sustain. When pro-Palestine sentiment rises or regional controversies flare, HoG’s defacements mirror that ideological momentum almost instantly. Conversely, their compromises of Indonesian websites, including government-linked systems, appear driven by convenience rather than conviction, underscoring a willingness to exploit domestic vulnerabilities despite public claims of national pride.
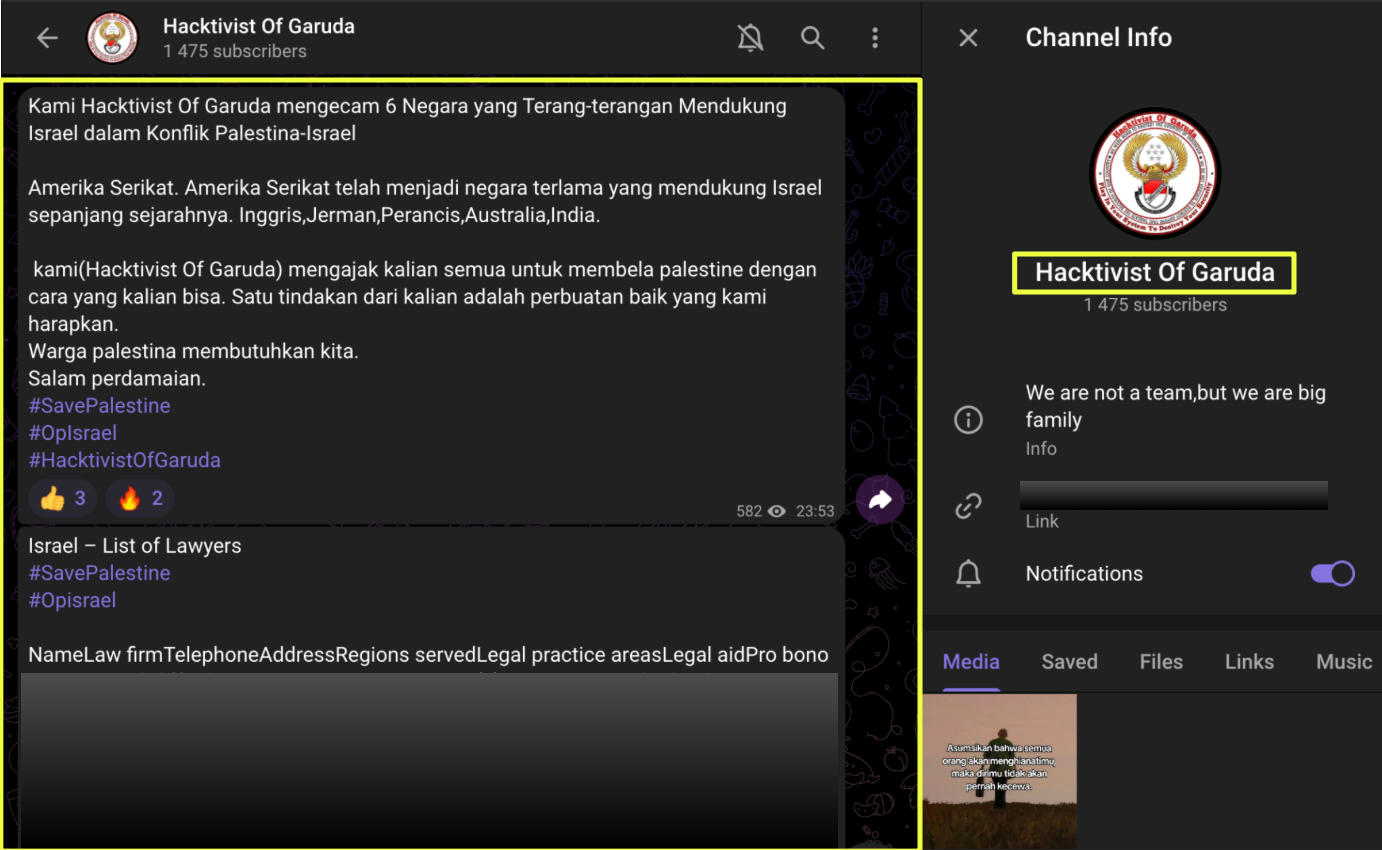
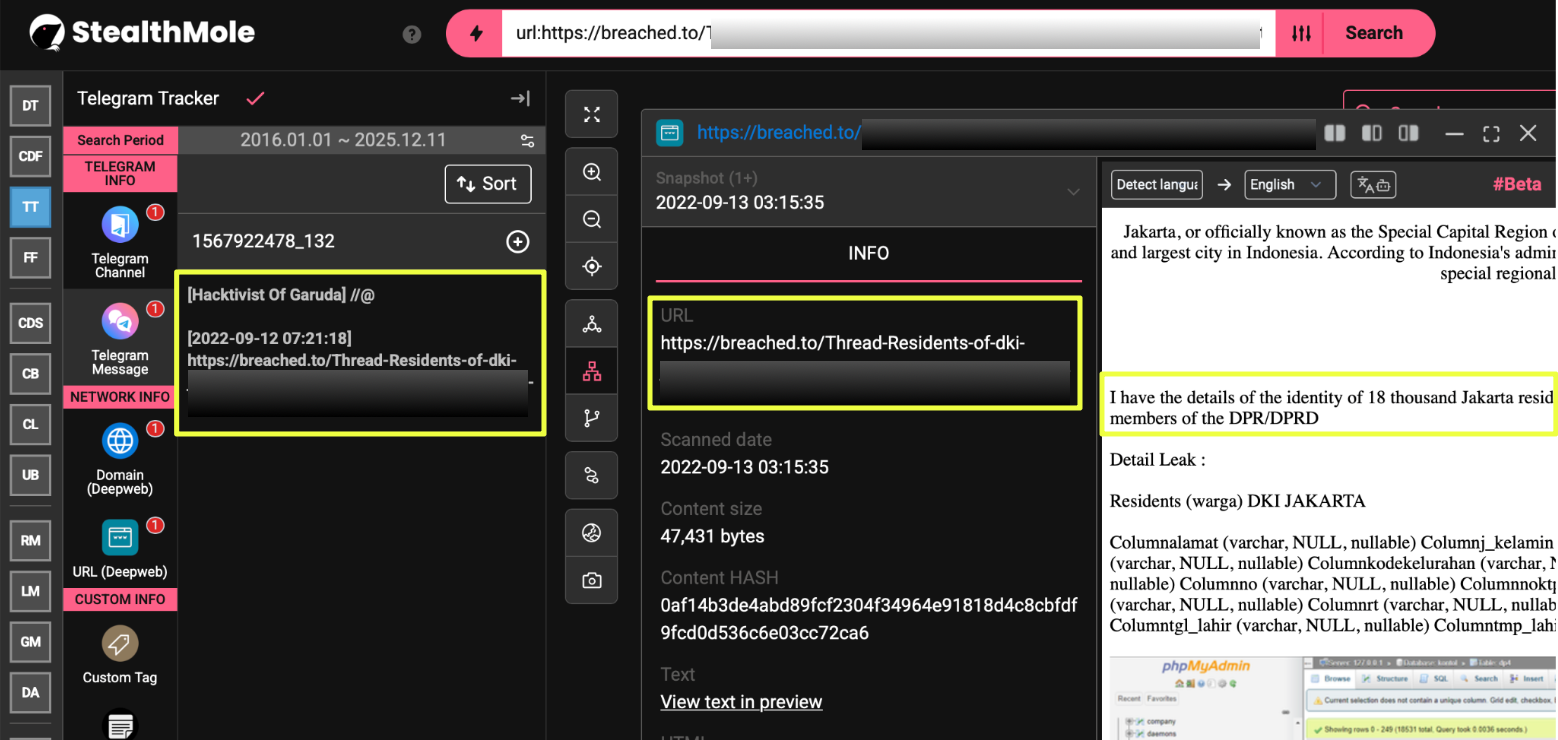
Alongside these political statements, the investigation surfaced evidence of mid-level database compromises and minor data leaks, including one instance of leaked Indonesian citizen data posted to a darkweb forum. These events, while not technically advanced, demonstrate that HoG occasionally ventures beyond website defacement into more consequential attacks, typically when the target aligns with their ideological momentum or when an individual operator seeks visibility.
Across all incidents, a clear pattern emerges: HoG prioritizes visibility over precision, volume over sophistication, and narrative impact over operational secrecy. Their criminal activity is less about sustained campaigns and more about maintaining relevance within the regional hacktivist ecosystem. The sections ahead break down how these behaviours manifest across platforms, operators, and timelines.
Actor Infrastructure
Hacktivist of Garuda’s infrastructure reflects the group’s identity: decentralized, loosely coordinated, and built from whatever platforms its individual operators can access. Rather than a single command node, HoG relies on a constellation of Telegram channels, throwaway Twitter accounts, shared Gmail inboxes, and opportunistic use of community Discord servers. This patchwork structure is not accidental, it is the natural outcome of a label that multiple Indonesian hacktivists adopt and abandon fluidly over time.
Telegram Infrastructure (Confirmed)
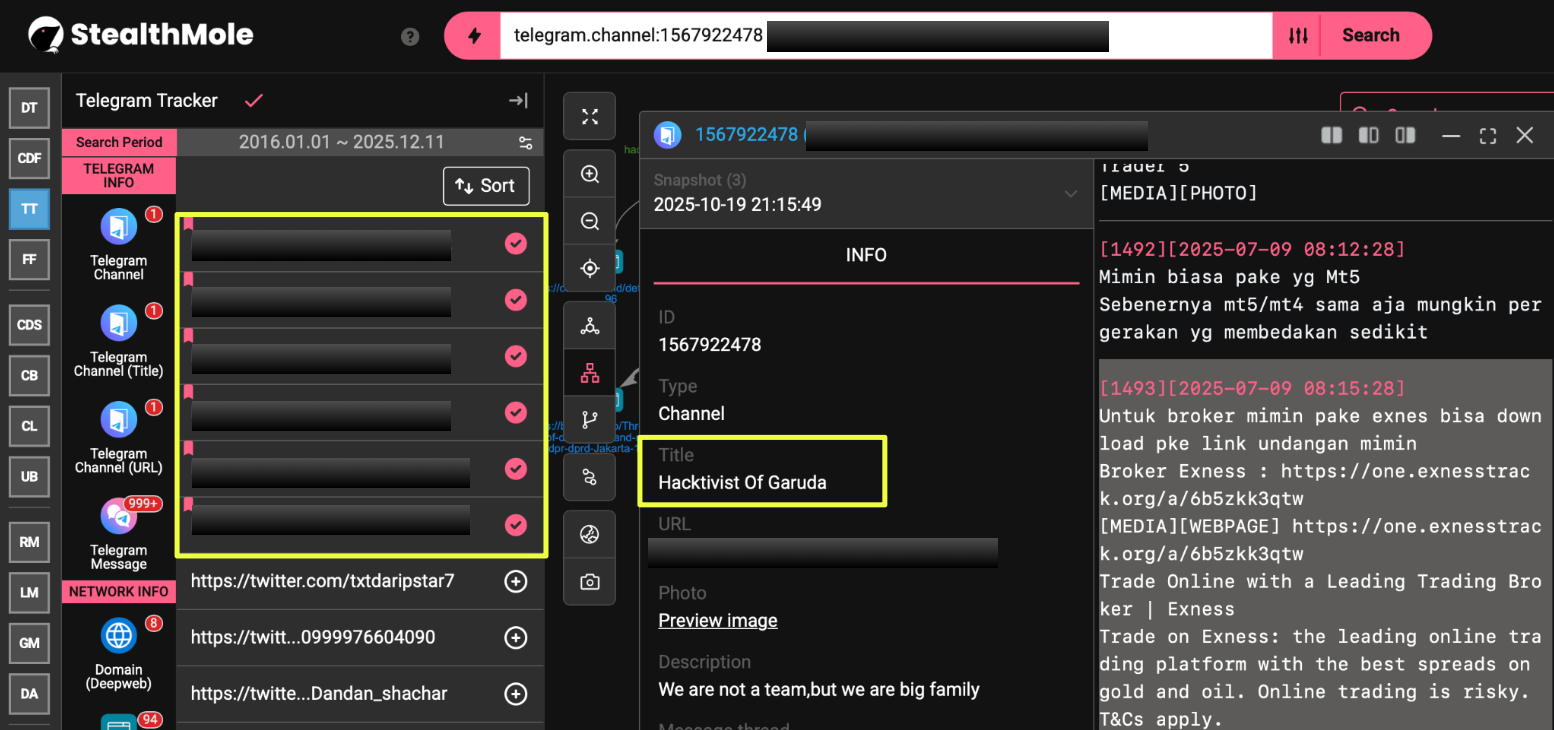
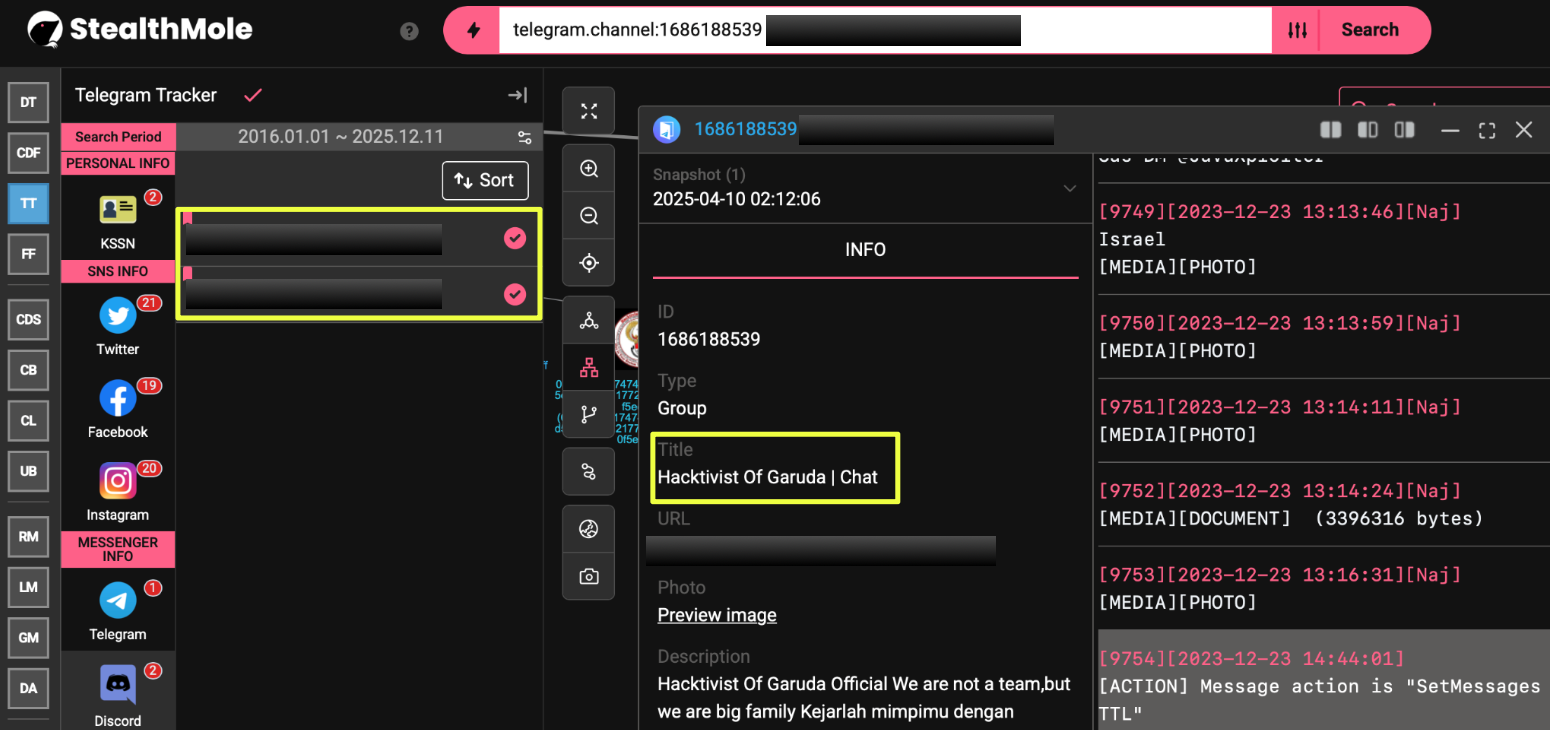
StealthMole’s Telegram Tracker surfaced two channels tied directly to HoG’s activity:
- https://t.me/Hack***al: their main broadcast channel, active since July 13, 2022.
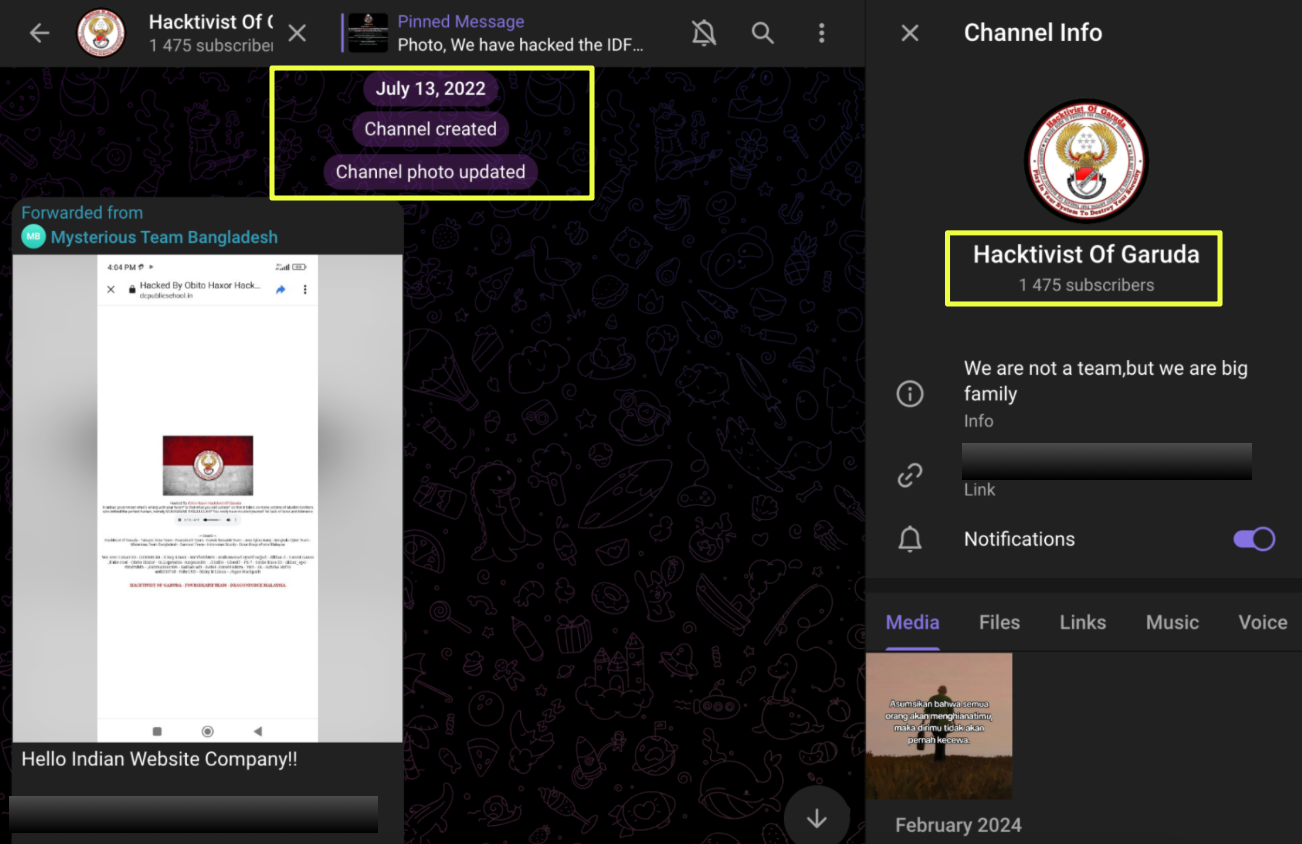
- https://t.me/Hack****k: a smaller chat-oriented channel created in September 2022, used for operator discussions, target sharing, and political amplification.
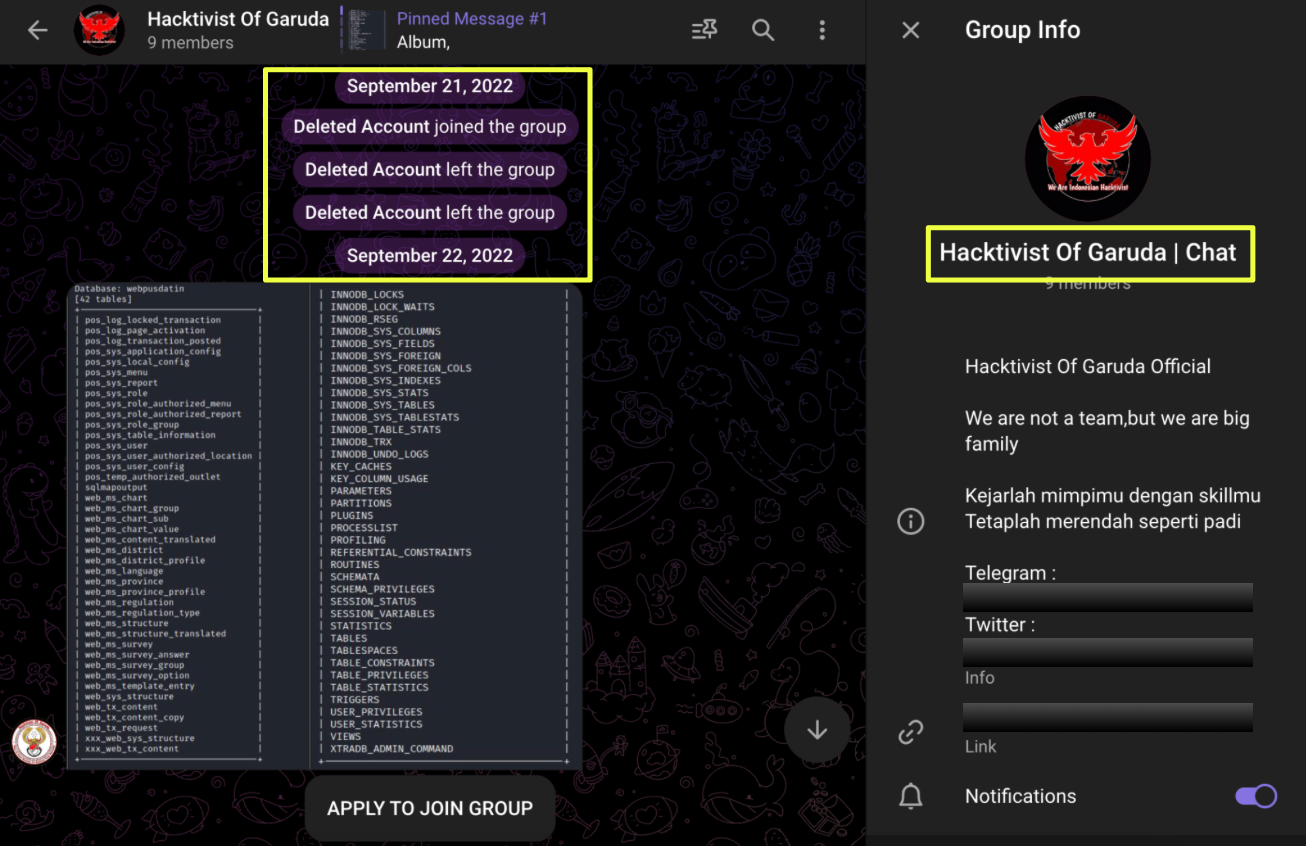
The two channels function in tandem: one shapes HoG’s public messaging, while the other captures the internal conversations that reveal the group’s operational rhythm.
Email Infrastructure (Confirmed)
Across defacements and shared banners, the investigation identified three Gmail addresses used interchangeably:
- hack****************a@gmail.com
- hack****************6@gmail.com
- hack****************6@gmail.com
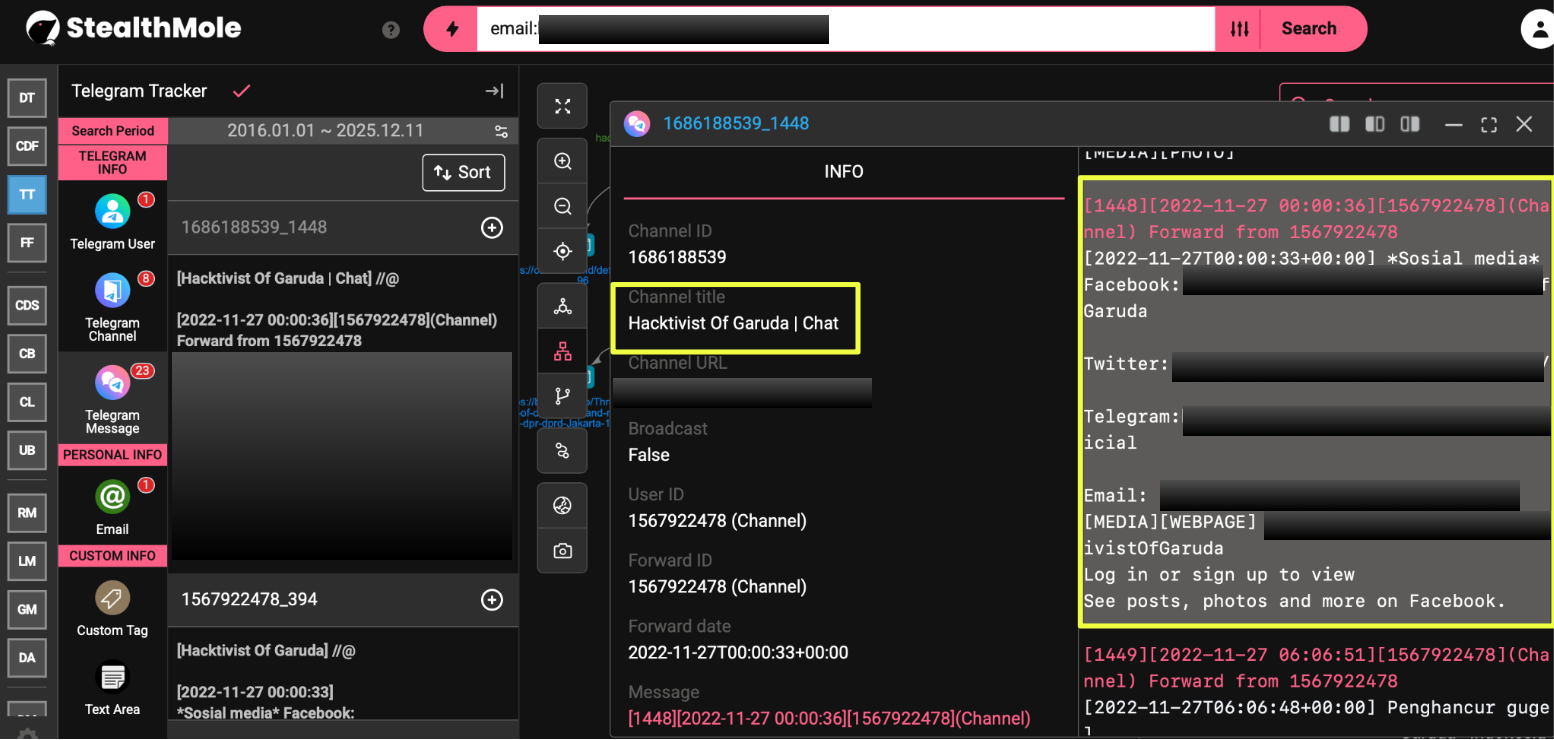
These addresses appear in signatures, recruitment lines, and contact sections, implying shared access among multiple operators rather than a single point of control. Their consistency across years of activity makes them reliable anchors for attribution pivots.
Twitter Footprint (Suspended + Active Accounts)
HoG’s presence on Twitter is wide but unstable. The group has repeatedly recreated accounts under slight naming variations after suspensions:
Suspended accounts:
- https://twitter.com/id_hacktivist
- https://twitter.com/hacktivistlink
- https://twitter.com/_Hacktivistlink
- https://twitter.com/hg_officiall
- https://twitter.com/HacktivistOf
Active but not yet confirmed as official:
- https://twitter.com/b***_ID (pending validation as an operator-owned account)
The repeated suspensions and rapid recreation of similar handles illustrate how HoG maintains continuity by attaching familiar naming patterns to new accounts, preserving identity even as individual operators rotate in and out.
Discord Presence (Indirect / Ecosystem-Level)
Two Discord servers surfaced during StealthMole’s Telegram pivoting, but neither appears directly controlled by HoG:
- https://discord.gg/g********X: associated with a DDoS operations community, mentioned in channels tied to shared hacktivist campaigns.
- https://discord.gg/U*****K: linked to OpsBadai, a regional hacktivist operation involving multiple Southeast Asian groups.
These servers are better understood as part of the ecosystem HoG participates in rather than components of HoG’s own infrastructure. They are rally points for broader hacktivist activity where HoG operators occasionally appear but do not act as hosts or administrators.
Other Platforms
Additional traces extend HoG’s infrastructure beyond Telegram and Twitter:
- Facebook: https://facebook.com/Hack*******a matches HoG’s visual branding and messaging pattern.
- Darkweb forum presence: a banned Breached.to account posting leaked Indonesian data under the HoG name.
- Defacement mirrors: dozens of Zone-H entries signed with HoG branding, confirming consistent attribution across unrelated targets.
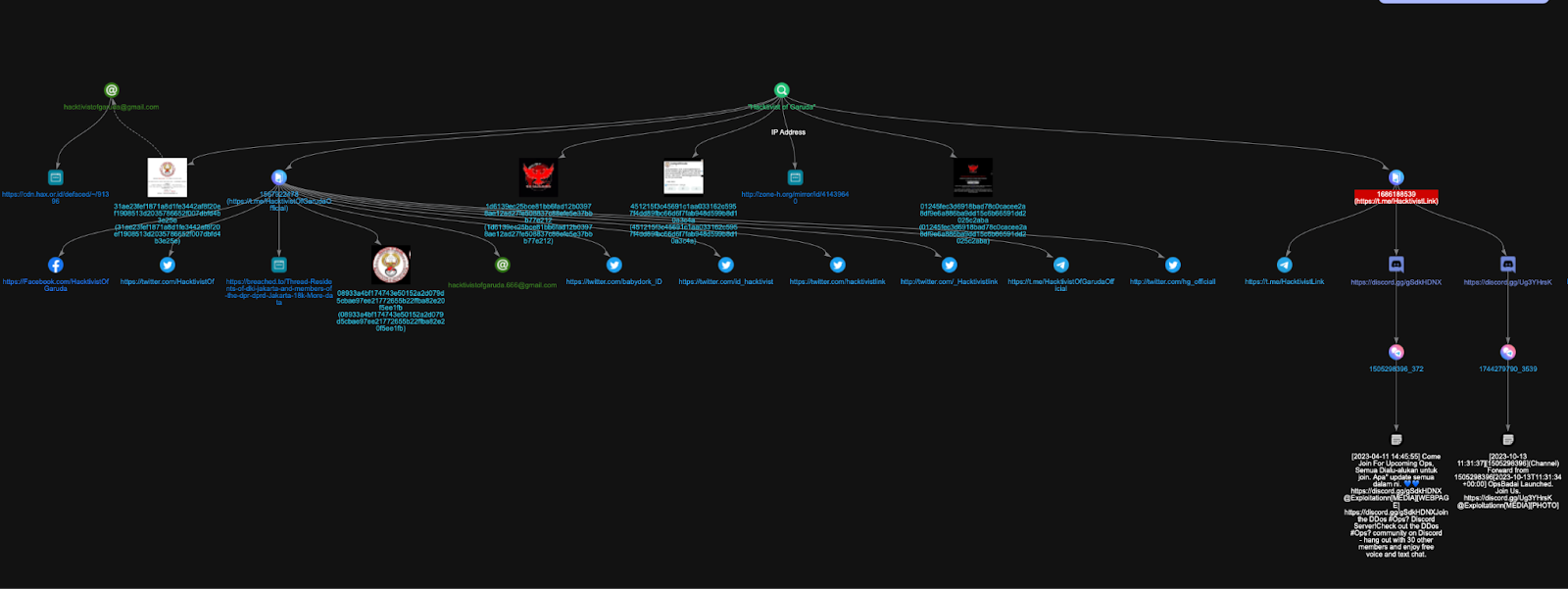
Across all these platforms, a clear picture emerges: Hacktivist of Garuda does not operate as a single team but as a distributed brand adopted by multiple Indonesian actors. Their infrastructure is resilient precisely because it is fragmented: Telegram anchors their messaging, Gmail handles their external communication, Twitter broadcasts their visibility, and Discord serves as auxiliary space during broader regional operations.
Operator Structure & Identity Signals
Hacktivist of Garuda does not function as a single, coherent unit. Instead, the label is carried by a rotating cast of Indonesian hacktivists who treat “HoG” less as an organization and more as a shared identity. This helps explain the group’s contradictory ideological messaging, uneven technical skill, and the wide variance in tone across their defacements and Telegram posts. When one operator speaks of peace and unity, another may declare solidarity with Palestine or frame an intrusion as retaliation against India, each revealing a different voice behind the same banner.
StealthMole’s pivots across defacement mirrors, Telegram channels, and suspended Twitter accounts highlight several operators who appear repeatedly within HoG-branded activity. Handles such as Caisar ID, DENNI5.ID, X’Boy Linux, Obito Haxor, Ghost7, and MrPL4Nkt0N recur across signatures, greetz lists, and internal chat posts. Their activity levels vary widely: while Hacktivist of Garuda claimed just over a hundred defacements in the examined period, individual operators like Caisar ID exceeded that output alone, suggesting parallel, semi-independent campaigns conducted under personal branding.
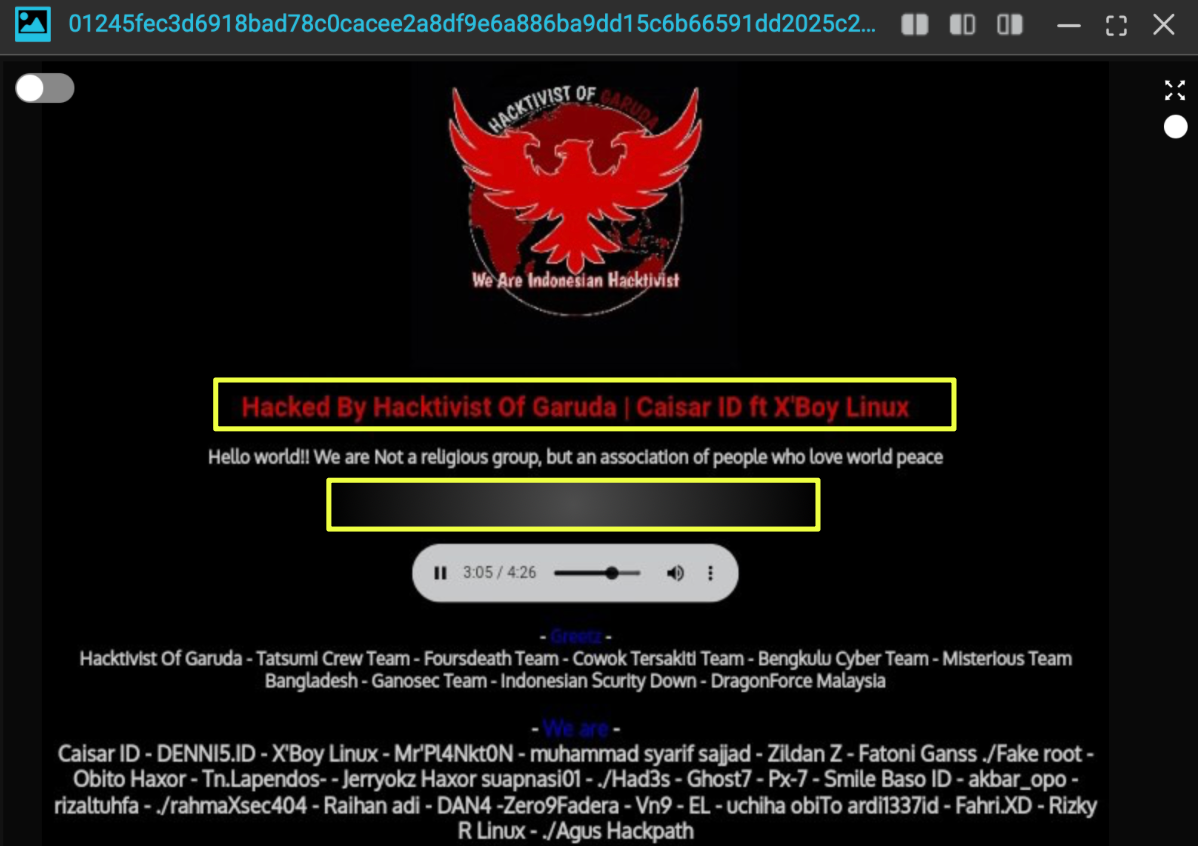
Identity leakage is subtle but present. Operators frequently write in colloquial Indonesian, reference specific regions such as Tegal or Bengkulu, and interact with other local crews, reinforcing their geographic clustering. Occasional mistakes, such as posting data leaks under a personal handle on darkweb forums or taking screenshots while logged into HoG’s Twitter account, further indicate young, low-OPSEC actors comfortable blurring personal and collective identities. The result is a structure that thrives on decentralization: a family of operators connected by shared culture and aesthetic, not hierarchy.
Conclusion
Hacktivist of Garuda represents a threat actor whose influence comes not from technical sophistication, but from its ability to mobilize a flexible identity across a broad pool of operators. The group’s decentralization is its greatest advantage: no single compromise, suspension, or takedown meaningfully disrupts its activity, because the “Garuda” label can be picked up by any motivated member of its ecosystem. This model allows HoG to sustain continuous output despite inconsistent skill levels, shifting ideology, and fragmented leadership.
The group’s behavior suggests a hybrid motivation structure. Political messaging is present, but not consistent enough to define HoG as an ideologically driven organization. Instead, their operations reflect a blend of reactionary activism, peer validation, and opportunistic exploitation. This mix is typical of hacktivist clusters where individual operators seek recognition within regional communities rather than pursuing long-term strategic goals. The recurring collaboration with other Southeast Asian and pro-Palestine hacktivist groups further situates HoG within a loose alliance network rather than a standalone initiative.
While most of HoG’s activity targets low-security websites, their occasional forays into data theft show they are capable of more impactful breaches when circumstances allow. These incidents are not coordinated campaigns but rather isolated efforts driven by individual members. As such, the primary risk posed by HoG lies in their unpredictability: they can pivot quickly, latch onto trending geopolitical events, and generate sudden bursts of activity aimed at symbolic targets.
Editorial Note
Cyber attribution is rarely straightforward, especially when a single banner is used by multiple operators with shifting motives and uneven technical skill. Hacktivist of Garuda illustrates how quickly signals can blur into noise across defacement mirrors, suspended social accounts, and overlapping hacktivist ecosystems. The purpose of this report is not only to map that complexity but to show how StealthMole, across dark web sources, social platforms, and operational artifacts, makes it possible to separate genuine activity from background clutter. In cases like this, clarity depends less on any single data point and more on the toolset’s ability to connect them.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Featured, Malicious Group

.svg)
.svg)
.svg)