Bangladesh Civilian Force: Fragmented Identities Behind a Single Hacktivist Brand
Bangladesh Civilian Force (BCF) is a hacktivist group that presents itself as a civic-minded force operating in digital spaces. Across social media platforms, the group blends political messaging, claims of public interest, and a strong sense of ideological purpose. At first glance, BCF fits the familiar mold of an ideologically driven hacktivist group: vocal, confrontational, and deeply aligned with geopolitical causes.
BCF’s messaging consistently signals clear ideological leanings. Its narratives repeatedly position India and Israel as adversarial actors, while expressing strong support for the Free Palestine movement. This alignment remains stable across platforms, suggesting that ideology, rather than opportunism, sits at the core of the group’s activity.
What complicates this picture is how BCF chooses to exist online. Instead of a single, clearly defined presence, the group operates through multiple identities that share the same name but differ in visuals, tone, and platform behavior. These parallel presences raise immediate questions: are they fragments of a loosely connected movement, deliberate misdirection, or something more coordinated beneath the surface?
This report documents the process of untangling BCF’s online footprint. By following how its identities intersect, overlap, and reinforce one another, the investigation aims to move past surface-level confusion and examine what this structure reveals about the group’s motivations, organization, and intent.
Incident Trigger and Initial Investigation
This investigation began unintentionally. While working on an unrelated case, the name Bangladesh Civilian Force surfaced repeatedly in adjacent material. Initially, it did not appear remarkable. Groups operating under similar naming conventions are common, and early indicators suggested BCF might fall into the category of routine ideological hacktivism.
To validate this assumption, I began with a keyword search for Bangladesh Civilian Force using StealthMole’s dark web and telegram tracking capabilities. Early results immediately pointed toward defacement activity explicitly attributed to BCF. Several defaced websites carried clear attribution banners naming the group, indicating that BCF was not merely an online commentator but an actor claiming direct involvement in cyber activity.
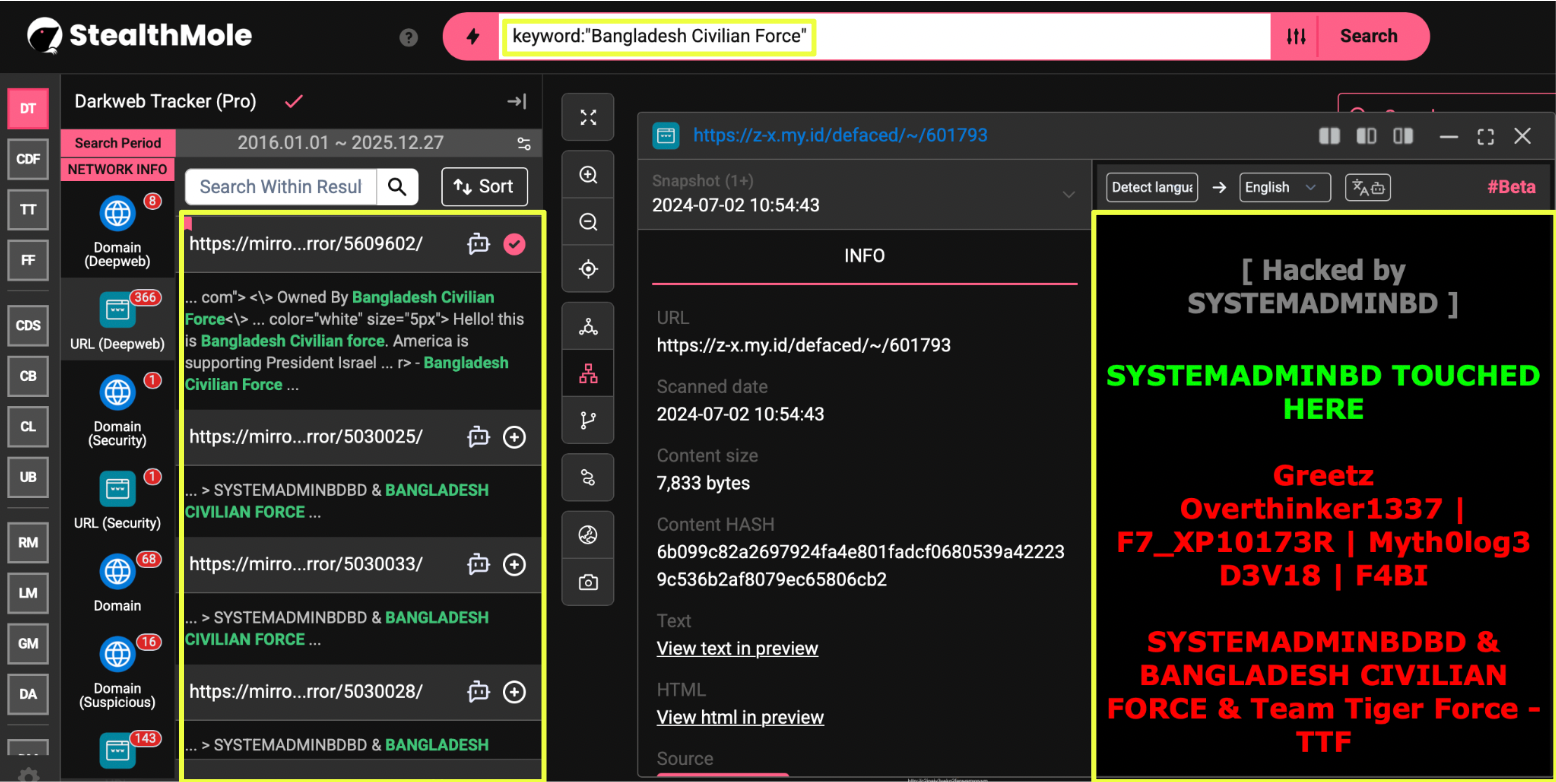
Running the same keyword through StealthMole’s Defacement Alert tool surfaced 14 distinct victims associated with BCF activity between May 2023 and February 2024. This figure reflects only what was captured within StealthMole’s indexed monitoring window and should not be interpreted as a complete count of the group’s operations. Even within this limited dataset, recurring ideological slogans and consistent attribution language suggested an organized effort rather than isolated acts.
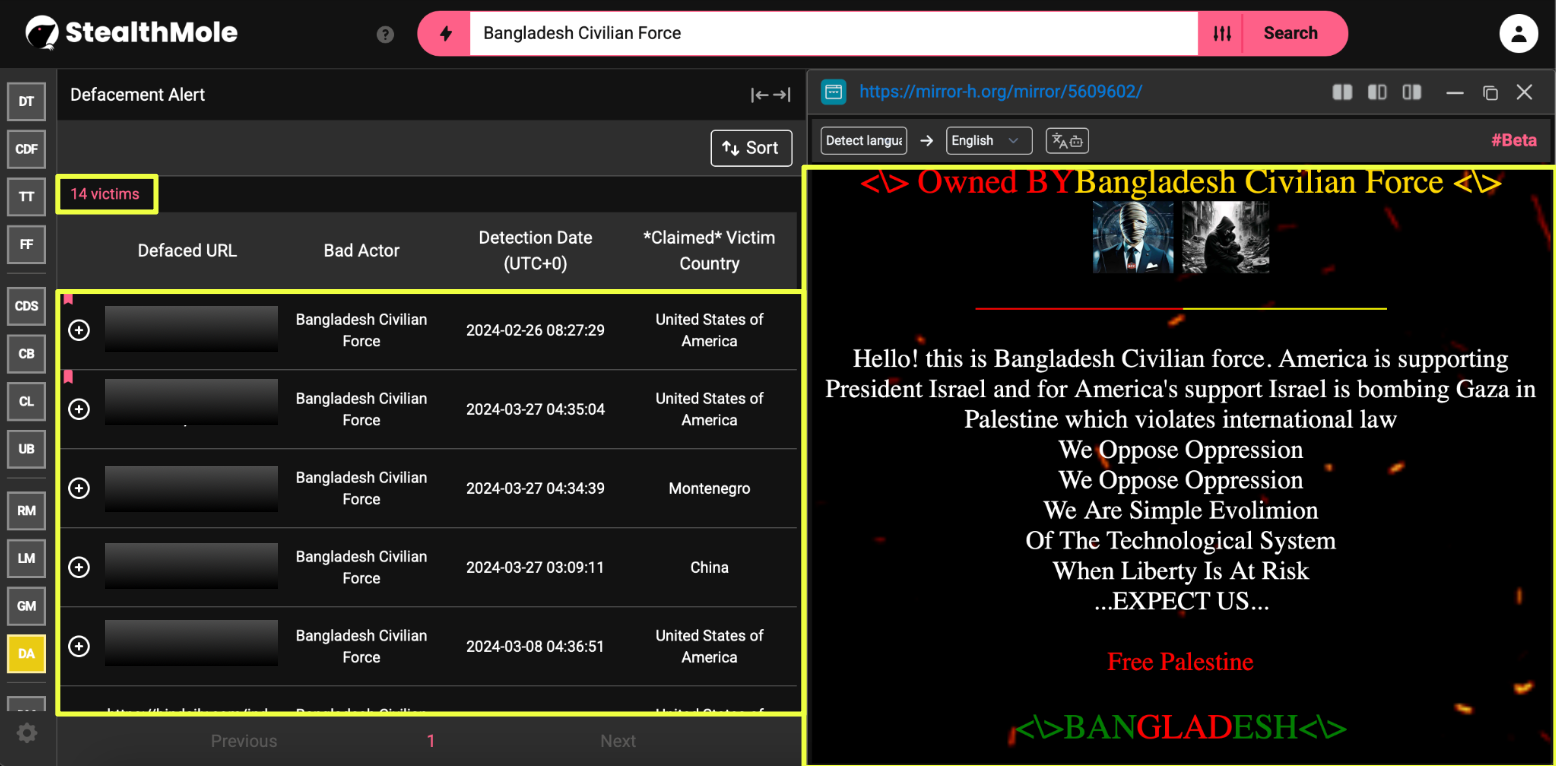
The defacement content repeatedly referenced India and Israel, aligning with broader political messaging observed elsewhere. At this stage, the investigation still appeared relatively straightforward: a politically motivated hacktivist group using defacement as a signaling mechanism. That clarity did not last long.
Telegram as the Operational Backbone
To understand how BCF coordinated its activity, I pivoted to Telegram using StealthMole’s Telegram Tracker. A keyword search led to a channel titled BCF, accessed through the invite link https://t.me/+75*******Vl. Channel metadata revealed that this invite link redirected to https://t.me/bc******l, indicating a username change rather than a separate entity.

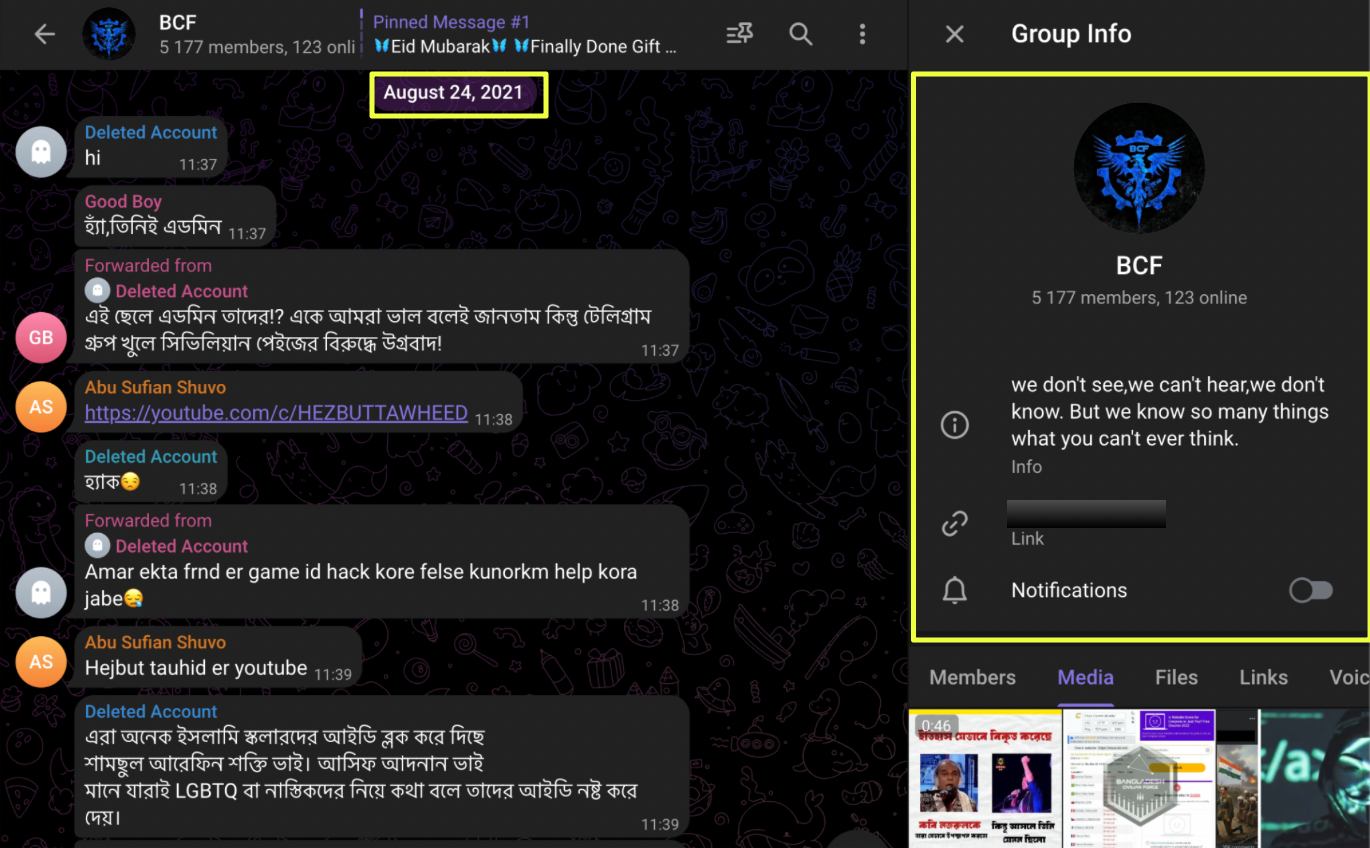
Historical message review showed that the channel’s earliest visible activity dated back to August 2021. During this early phase, the space functioned as a discussion group rather than a broadcast outlet. Members exchanged text messages and voice notes, suggesting an informal community environment rather than a tightly controlled operation.
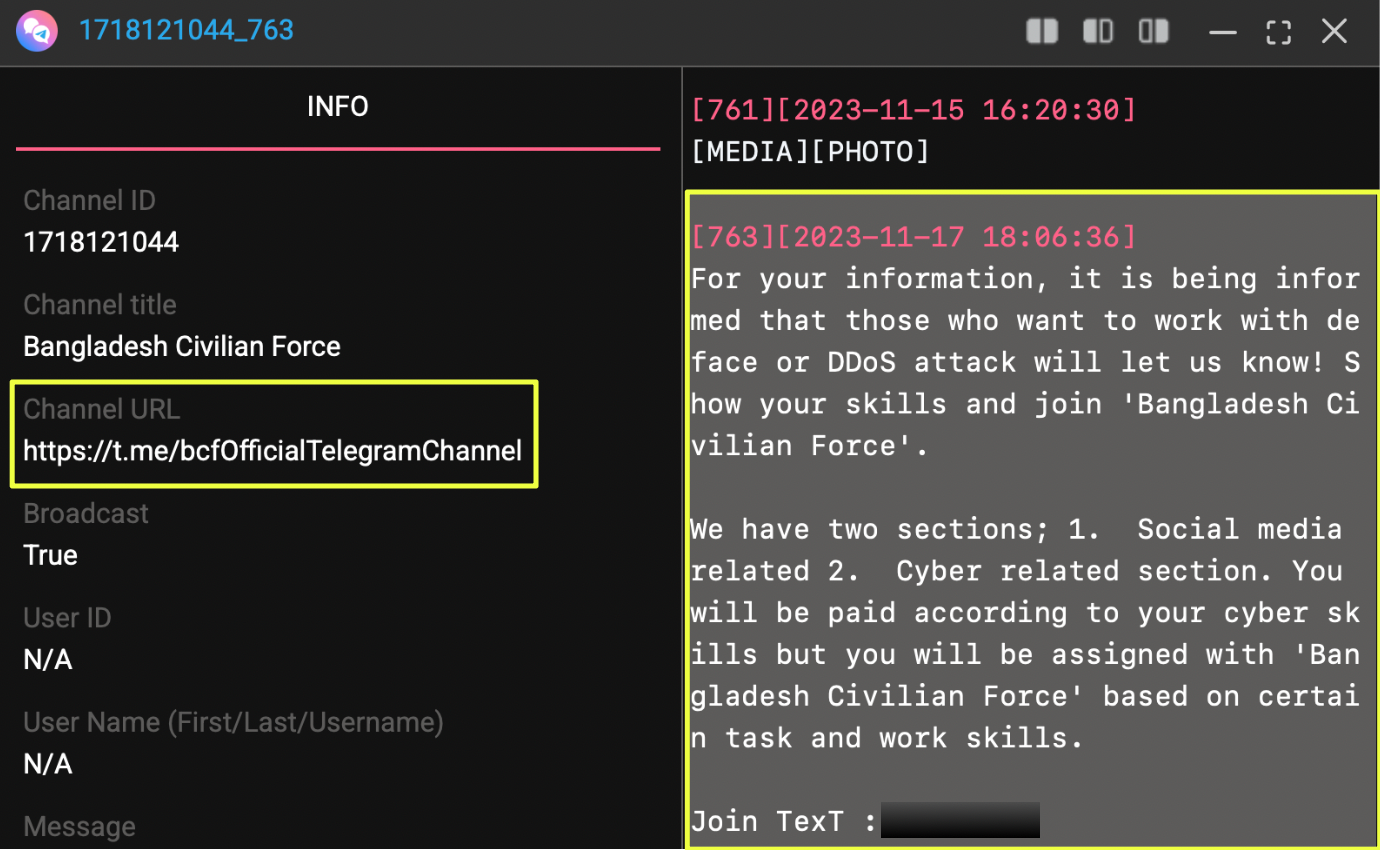
Further analysis uncovered additional Telegram channels tied to the same name, including https://t.me/bcfOfficialTelegramChannel, which is currently inaccessible but available through StealthMole’s historical indexing. This channel was created on 30 September 2022, adding another layer to the timeline.
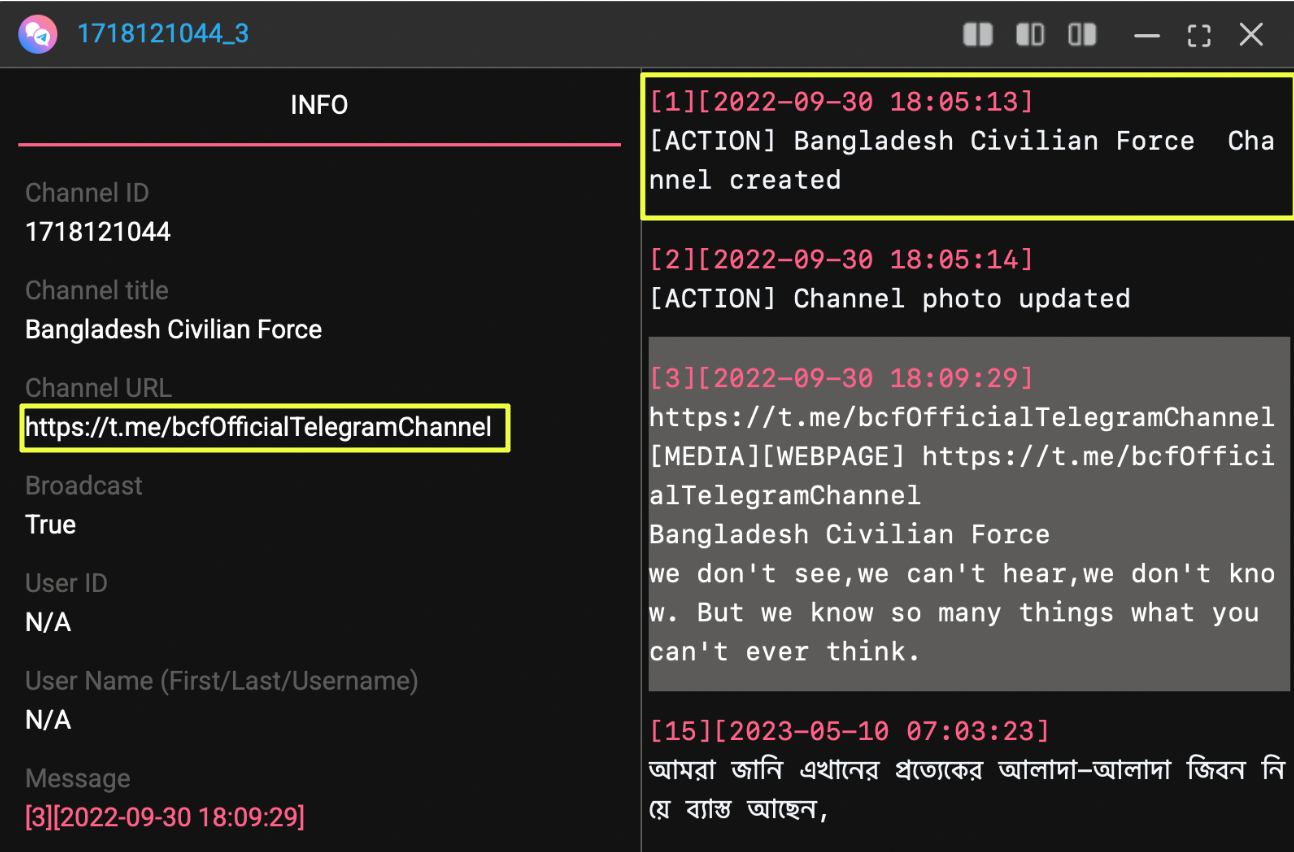
Two more active channels appeared at first to be unrelated.
- https://t.me/Bangla***********F
- https://t.me/bcf**************s
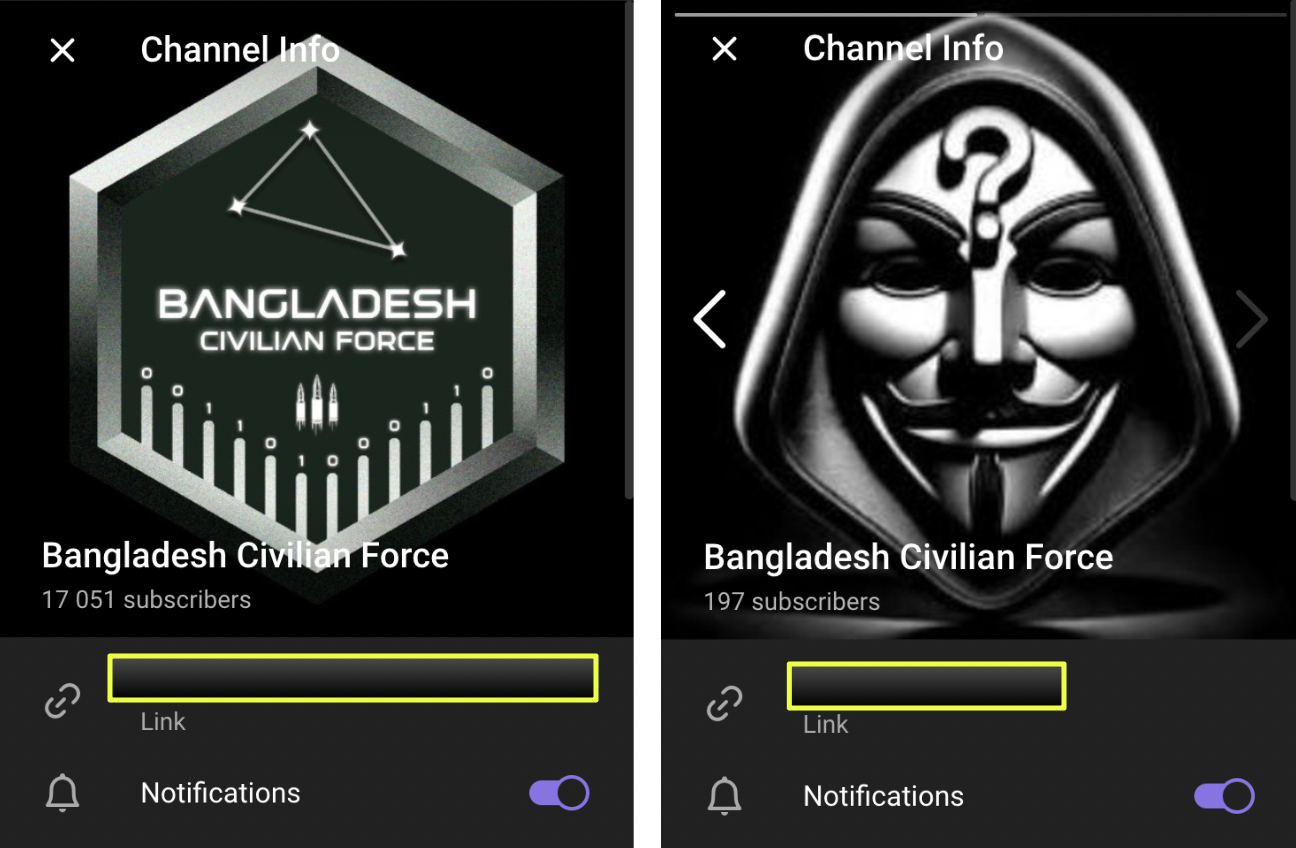
What stood out, however, was behavior rather than appearance. These channels regularly forwarded content from one another. No channel issued warnings about impersonation, and none attempted to establish exclusivity as the “official” BCF presence. This mutual amplification strongly suggests coordination, or at minimum, accepted coexistence under the same banner.
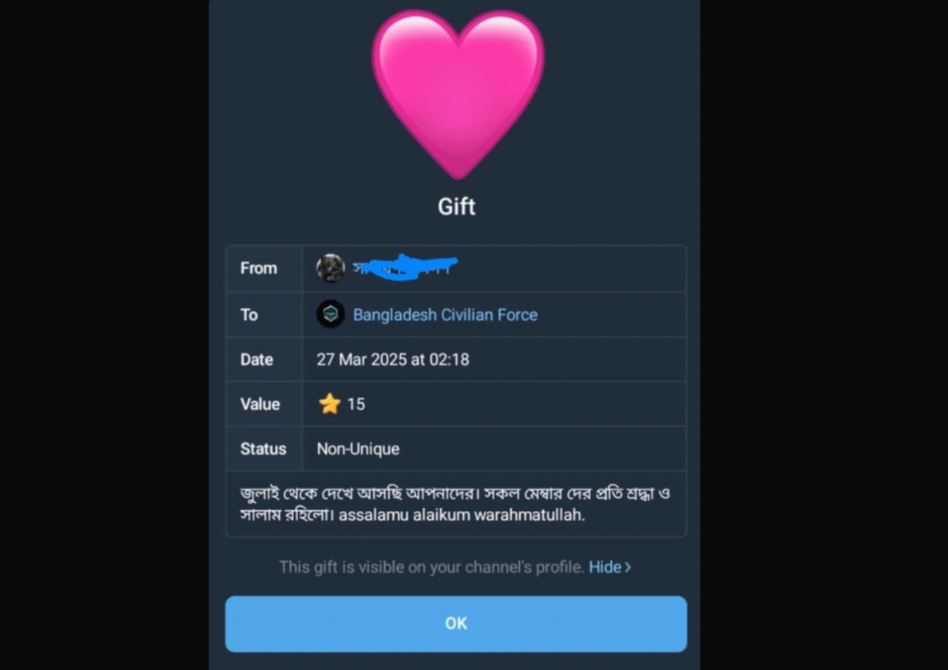
StealthMole also captured instances of Telegram users sending gifts to BCF. While gifts alone do not confirm structured funding, they do indicate sustained engagement and a degree of supporter loyalty within the ecosystem.
Instagram and Recruitment Signals
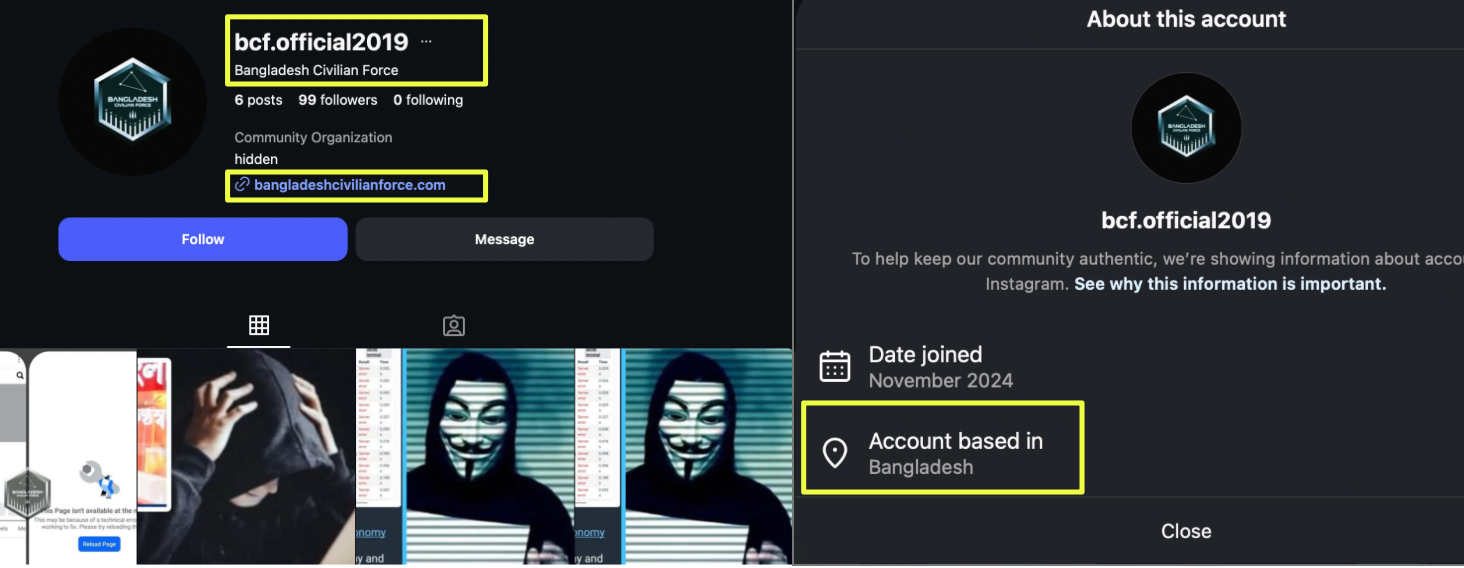
Telegram analysis led to the discovery of multiple Instagram accounts associated with BCF. One account, https://www.instagram.com/bcf.official2019, was created in 2024 and showed limited activity. It used a hexagon-shaped logo and referenced the group’s website, bangladeshcivilianforce.com, mirroring branding seen on other platforms.
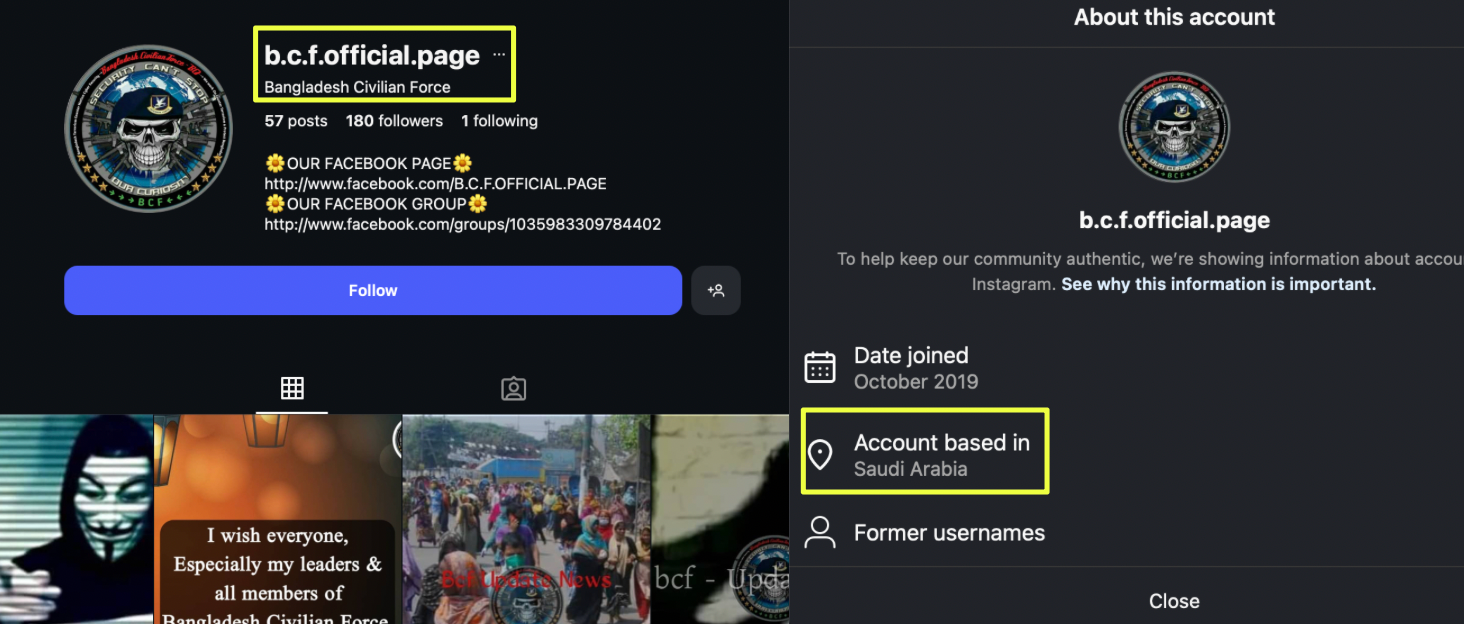
A second Instagram account, https://www.instagram.com/b.c.f.official.page, presented a different profile altogether. Created in October 2019, it used a skull-themed logo and listed its location as Saudi Arabia. This account was more active and, in 2023, published a post explicitly calling for individuals skilled in defacement and DDoS attacks in its related telegram channel. The post outlined two internal sections: social media–related and cyber-related, and stated that participants would be paid based on skill level. Interested individuals were directed to contact a Telegram handle, @cia404.
Using StealthMole, the skull logo was traced back to content associated with the previously identified Telegram infrastructure. This linkage suggests that the recruitment messaging was not an outlier, but part of the same broader ecosystem.
Twitter/X and Website Continuity
BCF’s presence on Twitter/X further reinforced cross-platform continuity. The account https://twitter.com/C********9 remains active and uses the same hexagon logo seen on Telegram and Instagram. The profile references bangladeshcivilianforce.com, strengthening the link between social media activity and the group’s claimed web presence.
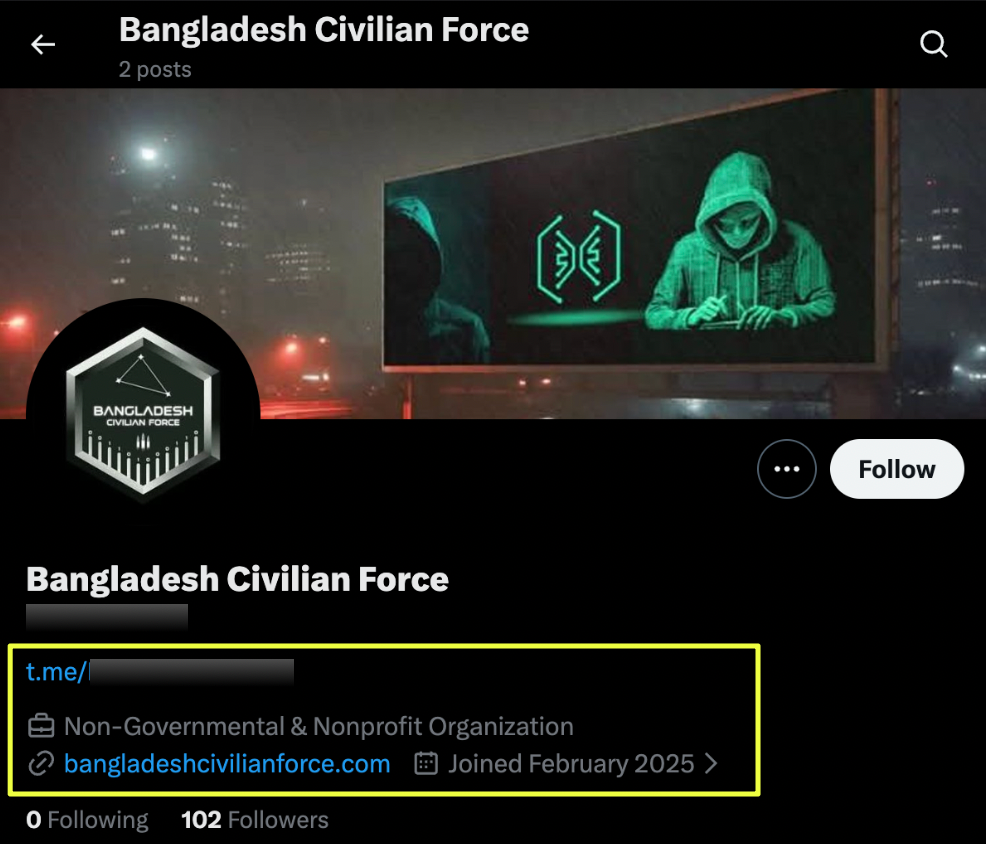
At no point did this account contradict or distance itself from the narratives promoted elsewhere. Instead, it functioned as another amplification node, reinforcing ideological messaging and directing attention back into the broader BCF network.
Facebook as the Visibility Anchor
The most prominent BCF presence appears on Facebook, where a verified page titled Bangladesh Civilian Force commands a following exceeding 800,000 users. The page categorizes itself as a law enforcement agency and lists a founding date of April 2019. Within the scope of this investigation, no independent verification of this status was identified.
- https://www.facebook.com/Bangla*************9
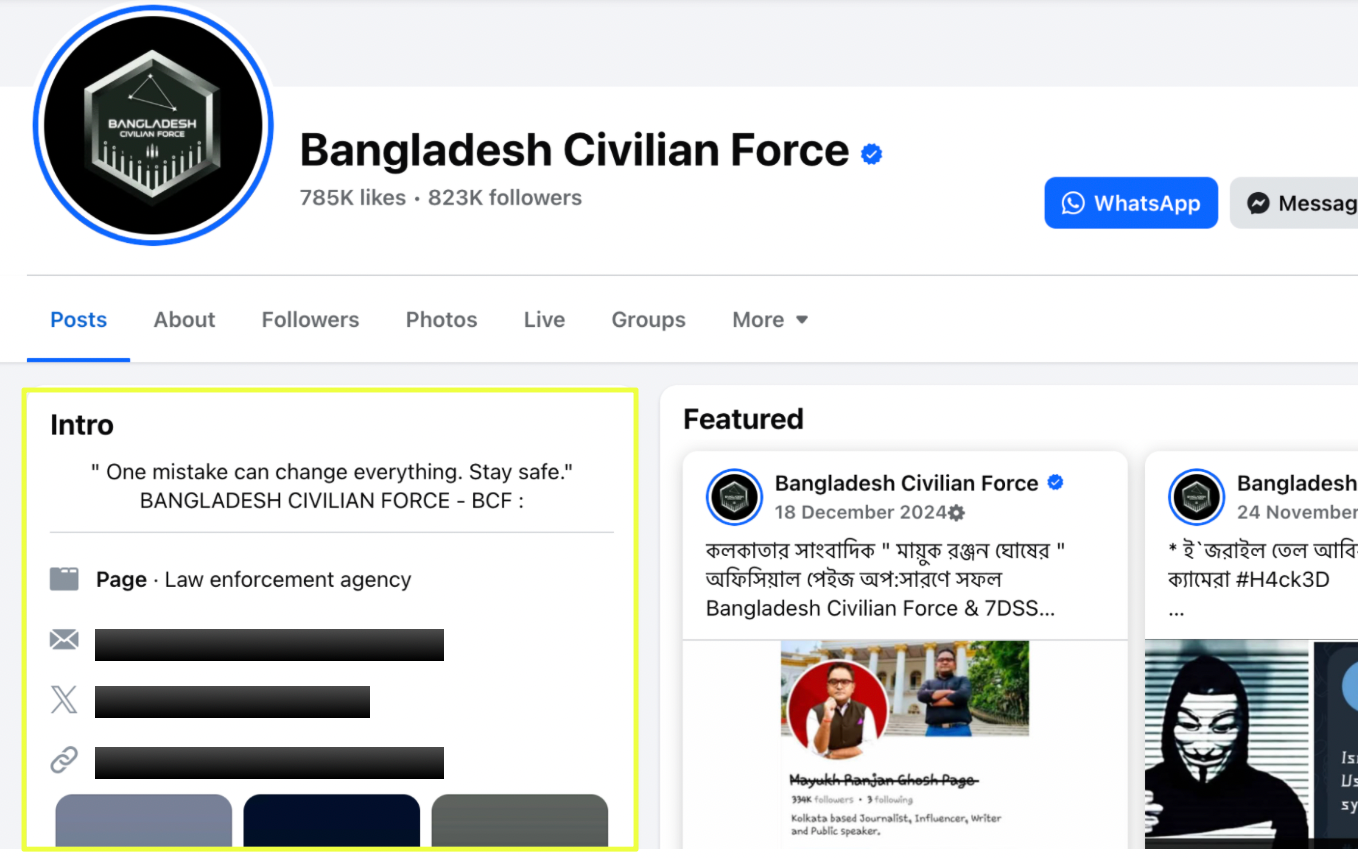
The Facebook page links directly to BCF’s Telegram and Twitter/X accounts and uses the same hexagon logo seen elsewhere. It also introduces a previously unseen contact point: ste*************e@gmail.com. While the function of this email remains unclear, its appearance adds another layer to the group’s outward-facing infrastructure.
Assessment
BCF’s use of multiple identities does not appear accidental. The coexistence of different logos, parallel channels, and varied platform behaviors, combined with consistent cross-posting and the absence of impersonation warnings, points toward intentional fragmentation. Rather than attempting to convincingly masquerade as separate groups, BCF appears to distribute its presence across identities to serve different purposes.
This structure offers practical advantages. It allows the group to absorb platform enforcement actions without collapsing entirely, segment its audience, and maintain momentum even when individual accounts are disrupted. While this fragmentation does introduce attribution challenges for analysts, the openness with which these identities reference one another suggests that evasion is not the primary objective. Resilience and reach appear to matter more than secrecy.
The Instagram account listing its location as Saudi Arabia raises additional questions but does not, on its own, support conclusions about nationality or external sponsorship. Within the dataset, the account’s ideology, messaging, and recruitment language remain aligned with BCF’s broader ecosystem. At this stage, location should be treated as contextual information rather than definitive attribution.
Across all platforms, BCF’s ideological posture remains consistent. India emerges as the primary focus of antagonism, followed by Israel, alongside strong and repeated support for the Free Palestine movement. This consistency suggests a stable ideological core guiding the group’s activity, rather than reactive or trend-driven engagement.
Conclusion
Bangladesh Civilian Force operates less like a single-purpose hacking crew and more like a branded digital movement that blends ideology, influence, and cyber activity. Its fragmented identity structure, rather than indicating chaos or impersonation, appears to be a deliberate design choice that supports longevity and adaptability.
By maintaining multiple identities under a shared narrative framework, BCF sustains visibility, recruits participants, and amplifies its messaging while avoiding dependence on any single platform. Understanding this structure is essential to accurately interpreting the group’s actions and avoiding misattribution driven by surface-level fragmentation.
What makes BCF particularly notable is not the scale of its claimed cyber activity, but the patience and consistency with which it has cultivated its online presence. The group’s ability to sustain attention across years, platforms, and shifting narratives suggests an understanding of visibility and influence that goes beyond one-off operations. Rather than chasing short-term impact, BCF appears focused on maintaining relevance, reinforcing its ideological stance, and keeping its name in circulation, even when concrete operational outcomes are difficult to verify.
Editorial Note
Investigations into cyber and online activist groups are rarely definitive. Actors often obscure intent through fragmented identities, shifting platforms, and evolving narratives. This case underscores how StealthMole’s historical indexing and cross-platform correlation capabilities help navigate that uncertainty, allowing analysts to identify coordinated behavior without overstating attribution or intent.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Featured, Hacktivist Group

.svg)
.svg)
.svg)