From Dark Web Pages to Blockchain Trails: The Red Room Case
“Red Rooms” are among the most persistent and controversial narratives associated with the dark web. Often described as private, pay-to-watch environments offering extreme or illicit content, they exist at the intersection of myth, exploitation, and deliberate obfuscation. While many alleged Red Rooms turn out to be scams or short-lived hoaxes, a smaller subset demonstrates characteristics of structured operations rather than opportunistic fraud.
What makes Red Rooms difficult to analyze is not just their content, but their design. These platforms are typically transient, frequently changing domains, interfaces, and access mechanisms. Instead of relying on recognizable branding or long-term infrastructure, they emphasize disposable web presence while shifting operational elements elsewhere. Payments, rather than pages, often become the most stable component of these systems.
Cryptocurrency plays a central role in this model. Fixed payment demands, one-time addresses, and time-limited access windows are commonly used to control entry while minimizing exposure. To an untrained observer, these transactions appear isolated and insignificant. In reality, they can serve as markers of coordination, reuse, and operational discipline when examined over time.
Understanding Red Rooms therefore requires moving beyond screenshots and surface-level claims. It demands correlating dark web artifacts with financial behavior, tracking how access is monetized, and identifying which components persist even as the visible infrastructure disappears. This report approaches Red Rooms not as a single site or story, but as an operational pattern, one that can only be understood by analyzing both where these services appear and how money flows through them.
Incident Trigger and Initial Discovery
This investigation did not begin with a single confirmed event or publicized incident. Instead, it emerged during routine dark web monitoring, where references to a Red Room–style platform surfaced alongside unrelated activity. What initially stood out was not the content itself, but the persistence of certain access instructions and payment references across otherwise unstable infrastructure.
- http://redroomfing27toi.onion/
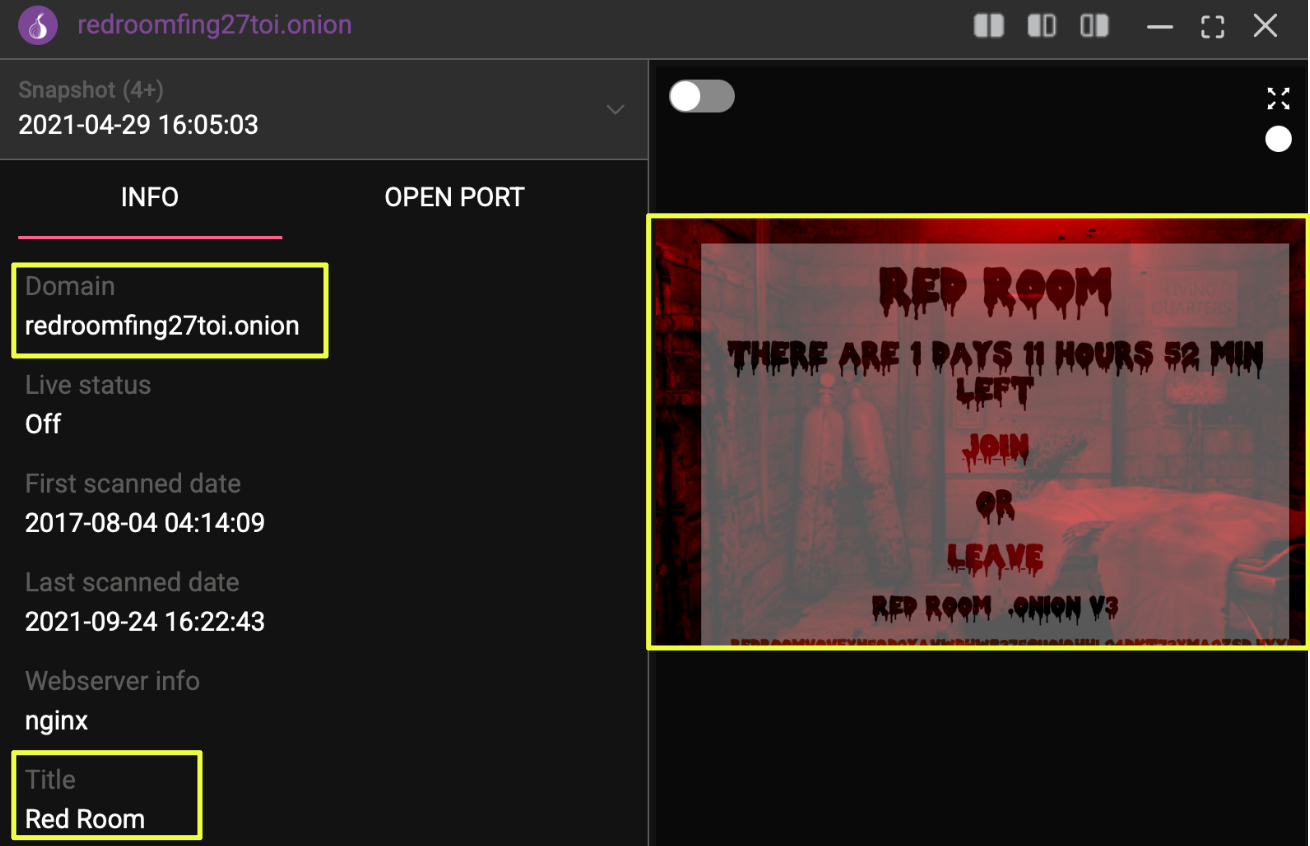
Using StealthMole’s dark web tracker, historical snapshots of multiple onion services were reviewed. While the sites differed in domain names and visual presentation, recurring structural elements began to appear, particularly around registration flows, access tiers, and payment instructions. Rather than treating each page as an isolated artifact, the investigation focused on how these fragments related to one another over time.
As this review expanded, additional onion domains surfaced through StealthMole queries. Some were no longer accessible, others displayed maintenance notices or alternate homepage layouts. Despite these differences, StealthMole’s historical indexing showed that several of these domains shared identical interface structures and navigation logic. This suggested that the visible web presence was being rotated deliberately, while core design elements remained unchanged.
- redroom**********************************************yid.onion
- Tnpmxdvvoxp5ysrmazhhh2ra4fujx3sxa3cc2kbizvtz6eaywcvy36id.onion
- 3xpx7iu7vqbiwuhbiee2orwp6e4fobgdg6zcikp6btigmlpgqdi5blid.onion
- mqmn3rz5f7bb5oit.onion
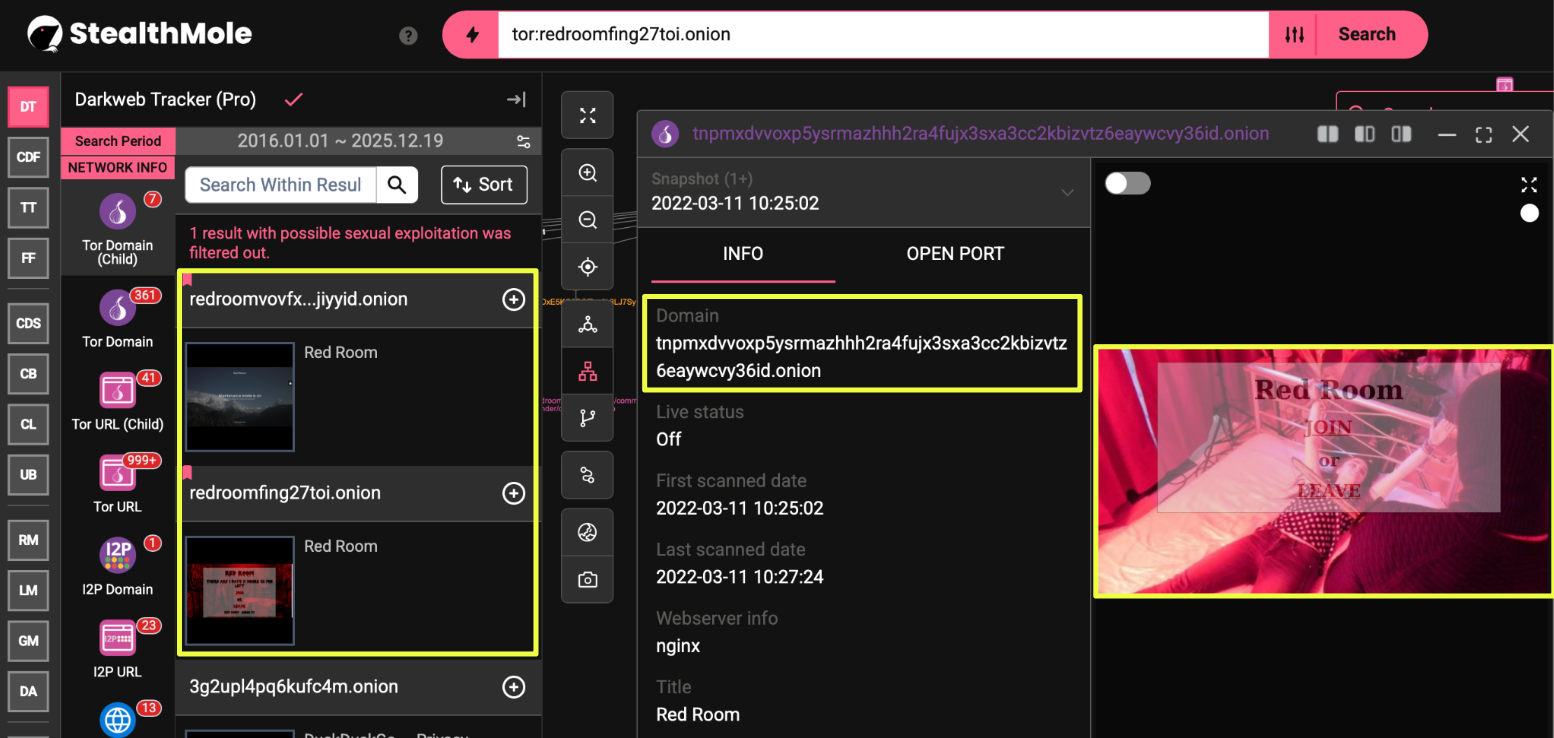
Across these site variants, payment-related components appeared consistently. Bitcoin wallet addresses were embedded directly within registration pages, access instructions, and references to specific roles or events. In some instances, exact payment amounts were specified, while in others the addresses appeared as part of backend or administrative flows.
Payment Layer Identification
With the web-facing infrastructure mapped, the investigation shifted toward the payment layer exposed across the identified Red Room domains. Rather than treating cryptocurrency references as secondary details, they were examined as core components of how access to these platforms was structured and controlled.
Bitcoin wallet addresses were not presented uniformly across the sites. Some appeared within user-facing registration and access pages, accompanied by specific instructions and payment amounts. Others surfaced in sections that suggested administrative functions, event-related access, or backend operations. Each wallet was cataloged based on the exact context in which it appeared, distinguishing between addresses intended for user payments and those likely serving internal or transitional roles.
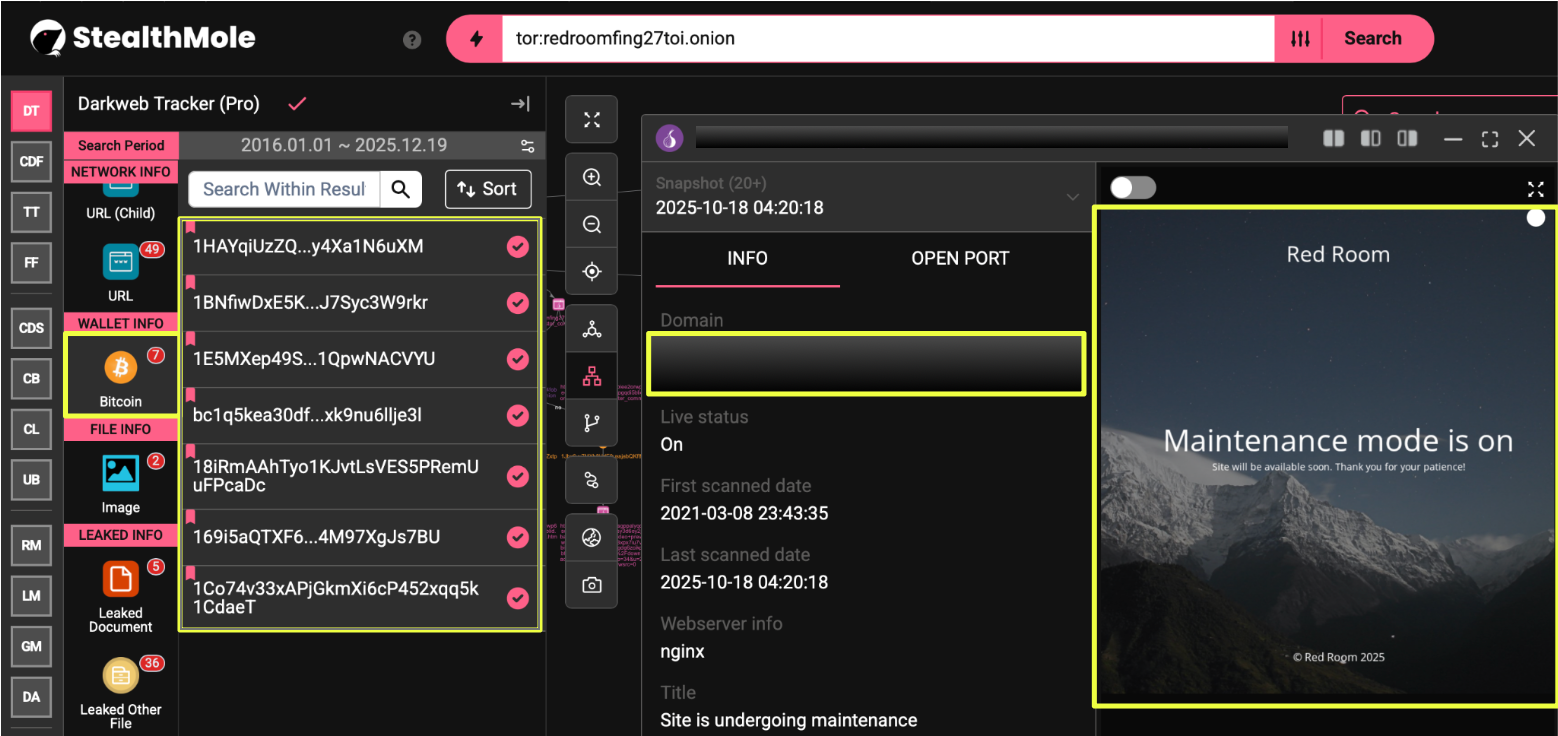
A notable observation during this phase was that not all wallets exposed through the infrastructure were actively used. Several addresses showed no observable transaction history, while others recorded only minimal activity. Rather than discounting these findings, the investigation treated wallet inactivity as a potential indicator of role separation, contingency planning, or phased deployment within the broader payment architecture.
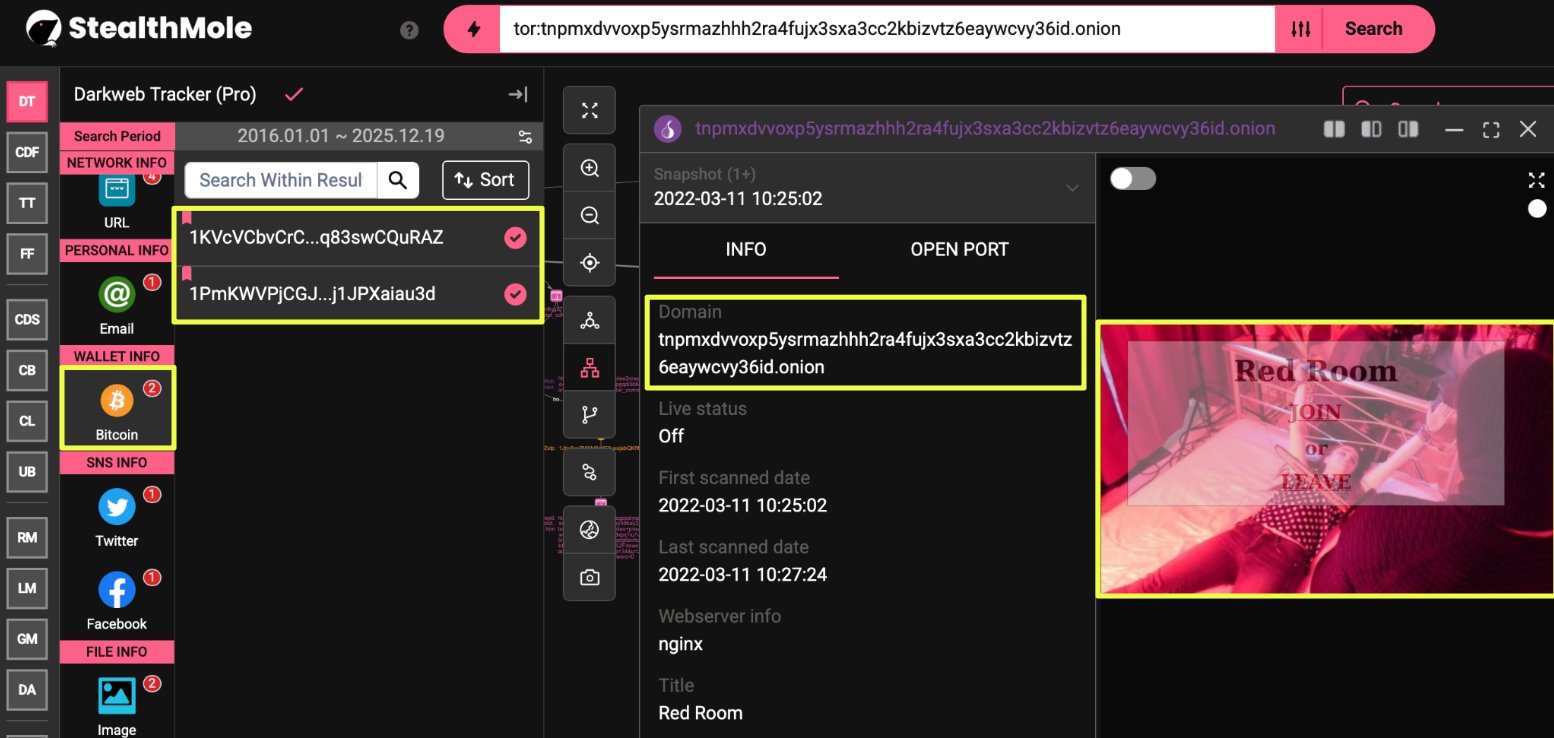
At the same time, a smaller subset of wallets displayed consistent transaction behavior over defined periods. These wallets were associated with precise payment instructions and appeared repeatedly across site variants, suggesting they functioned as primary collection points rather than experimental or disposable addresses. The contrast between active, minimally active, and inactive wallets provided early insight into how financial responsibilities may have been distributed within the Red Room ecosystem.
Wallet Identification and Role Differentiation
Once the payment layer had been established across the identified Red Room domains, the investigation moved toward isolating and classifying the Bitcoin wallets exposed through that infrastructure. Rather than assuming uniform purpose, each address was examined in relation to where it appeared, how it was referenced, and whether it demonstrated observable on-chain activity.
The most prominent wallet identified during this phase:
- 1Co74v33xAPjGkmXi6cP452xqq5k1CdaeT
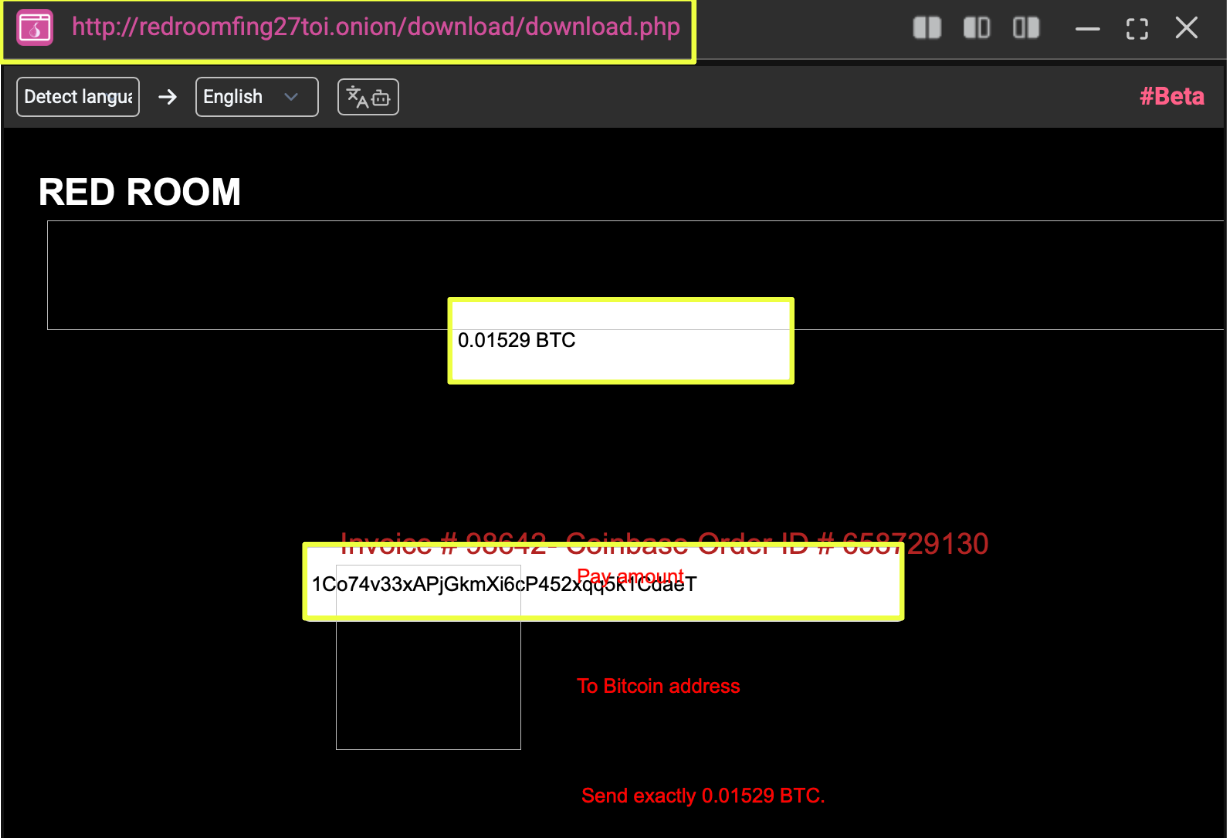
This address appeared directly within user-facing payment instructions and was consistently paired with an exact payment requirement. Its repeated presence across access-related pages distinguished it from other wallets that appeared in less explicit or more fragmented contexts.
In contrast, several wallets surfaced through Red Room–linked pages but showed no observable transaction history on the blockchain. These included:
- 18iRmAAhTyo1KJvtLsVES5PRemUuFPcaDc
- 169i5aQTXF6ccUj1FQNDPgv4M97XgJs7BU
- 1Jbx6vy7MXh8HdE9ussjabQKf8TjhvH2tR
- Bc1q5kea30df7pgnhesvz8saw8s7efxk9nu6llje3l
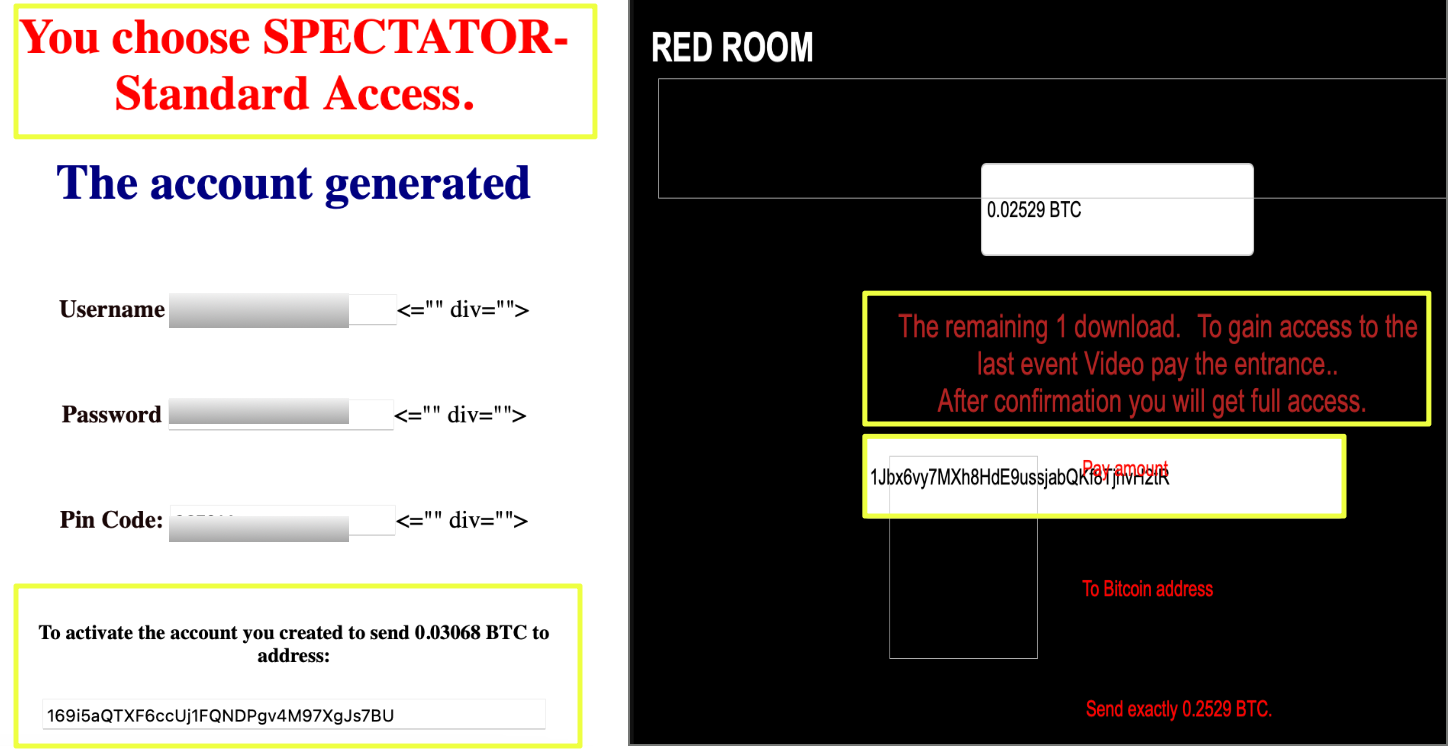
Despite their inactivity, their inclusion within Red Room infrastructure suggested they were generated intentionally, potentially as contingency addresses, placeholders, or components of planned but unused payment flows.
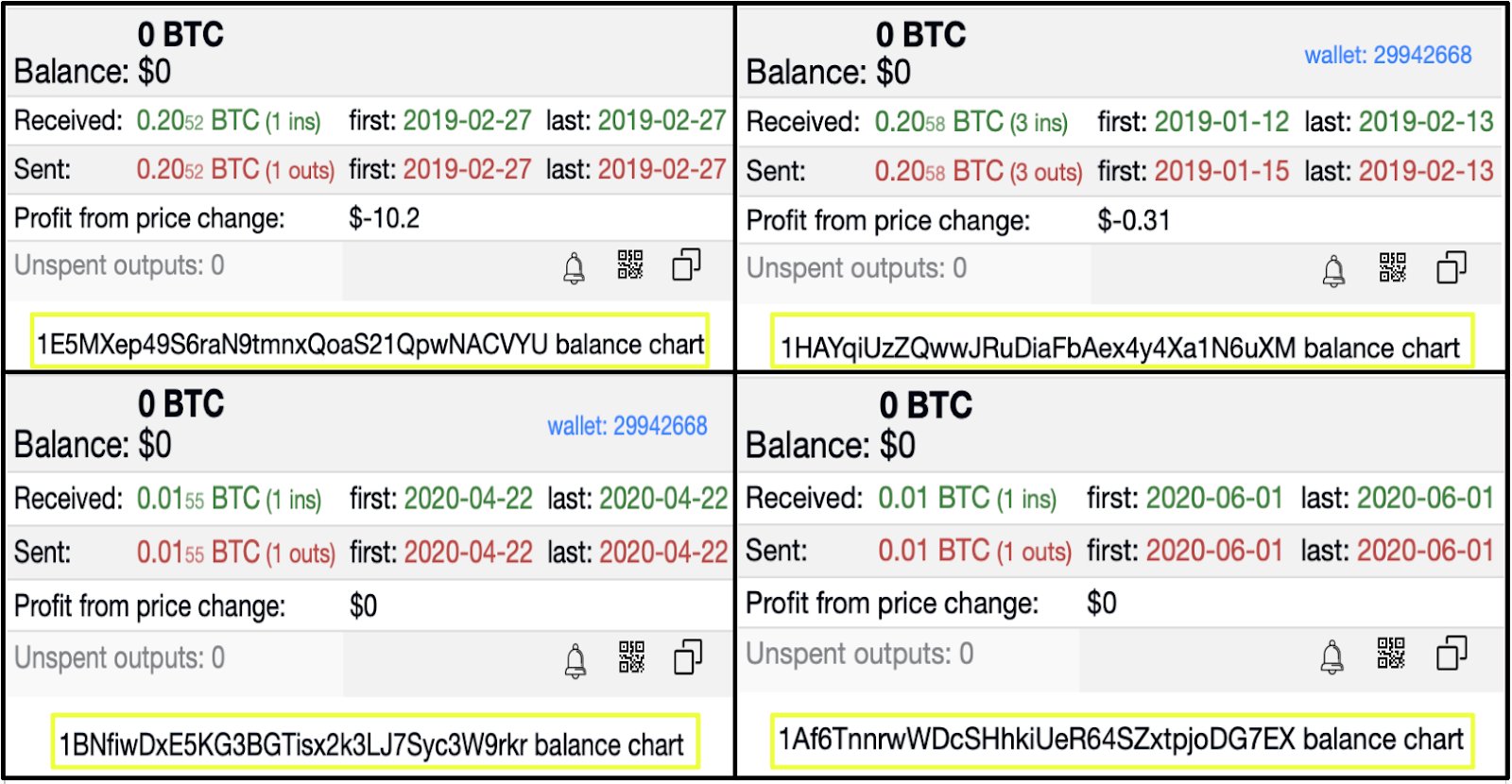
Other wallets displayed limited on-chain activity, typically consisting of one or two transactions. These addresses did not exhibit the repeated, structured payment patterns associated with user-facing monetization but nonetheless formed part of the broader financial footprint exposed by the sites. Their behavior was consistent with short-lived or purpose-specific roles, such as internal transfers or transitional routing.
- 1E5MXep49S6raN9tmnxQoaS21QpwNACVYU
- 1BNfiwDxE5KG3BGTisx2k3LJ7Syc3W9rkr
- 1HAYqiUzZQwwJRuDiaFbAex4y4Xa1N6uXM
- 13TiXQsjYPiq7rfeqiGGJD9on8Kp7HZdm3
- 1Af6TnnrwWDcSHhkiUeR64SZxtpjoDG7EX
- 1PmKWVPjCGJoW2tuvVs5tnnj1JPXaiau3d
One wallet stood apart in both longevity and activity:
- 1KVcVCbvCrC9VfBJ2PVan2yq83swCQuRAZ
Unlike the previously identified addresses, this wallet remained active well beyond the timeframe observed for the primary payment wallet and recorded sustained transaction activity over multiple years. Its appearance across different Red Room–linked contexts, combined with its extended operational lifespan, indicated a role distinct from single-use or event-specific payment collection.
Blockchain Analysis and Financial Correlation
With the Red Room–linked wallets identified through StealthMole, the investigation moved beyond exposure mapping and into transaction-level analysis. While StealthMole established where these wallets appeared and how they were presented within dark web infrastructure, understanding what actually happened after payments were made required visibility into on-chain behavior. This is where deeper blockchain analysis became essential.
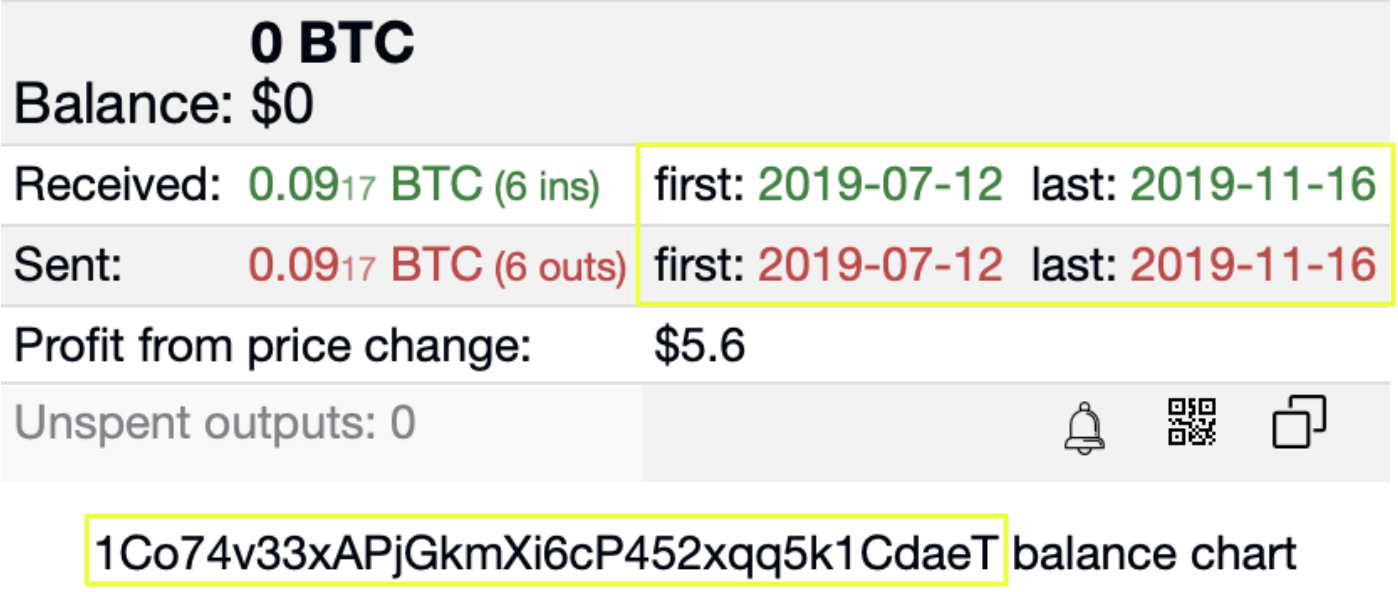
The first wallet examined using Sentinel Protocol was 1Co74v33xAPjGkmXi6cP452xqq5k1CdaeT, which had been consistently presented on Red Room pages as a payment destination. Sentinel analysis showed that this wallet was active for a clearly defined period, with transactions occurring between 12 July 2019 and 16 November 2019, after which no further activity was observed. This bounded activity window aligned closely with the operational lifespan inferred from the associated Red Room infrastructure.
Rather than receiving funds from a large number of unrelated addresses, Sentinel revealed that this wallet received Bitcoin primarily from two upstream source wallets:
- 1EyAFt7JTegJmg1CzUzABA7WfCCABzDxoQ
- 34EFZUCZWo8cwbJ6VjMFihwc88x9oWd4yn
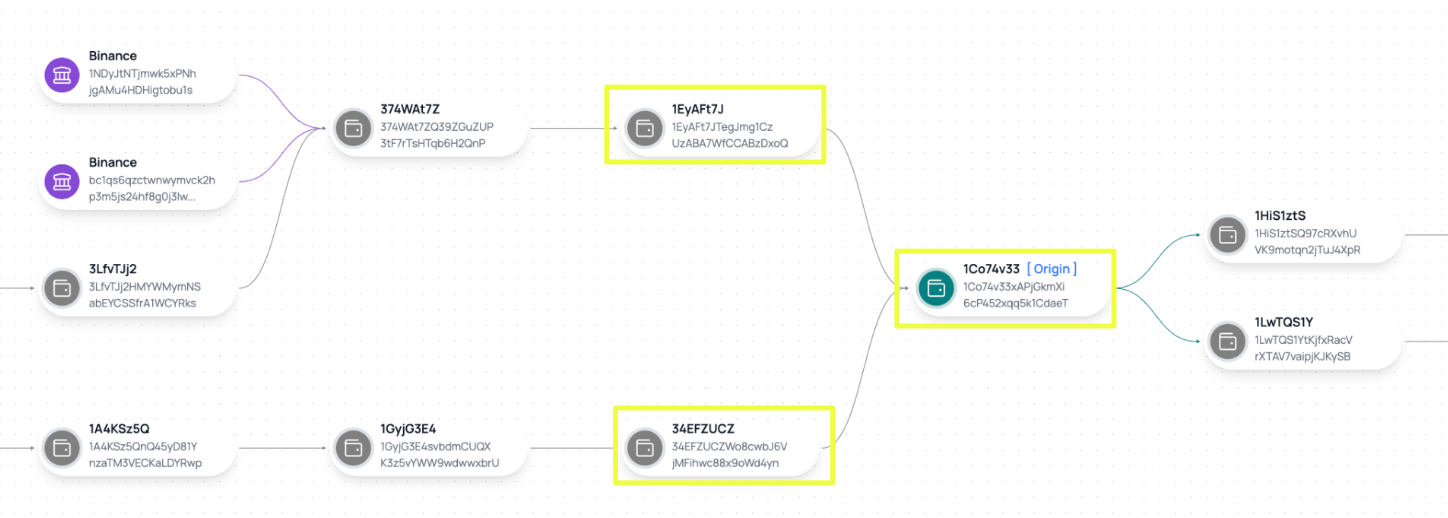
These wallets functioned as intermediaries, aggregating funds before forwarding them to the Red Room payment wallet. This structure indicated deliberate separation between end-user payments and the exposed payment address, rather than direct peer-to-peer transfers from customers.
A key challenge addressed during this phase was Bitcoin’s UTXO (Unspent Transaction Output) model, which can make single payments appear fragmented when viewed superficially. Sentinel made it possible to correctly group multiple outputs belonging to the same transaction hash. This revealed that what initially appeared as multiple small transfers were, in fact, single payments split at the protocol level. Proper aggregation confirmed that inbound payments repeatedly matched the exact amount specified on Red Room payment pages: 0.01529 BTC.
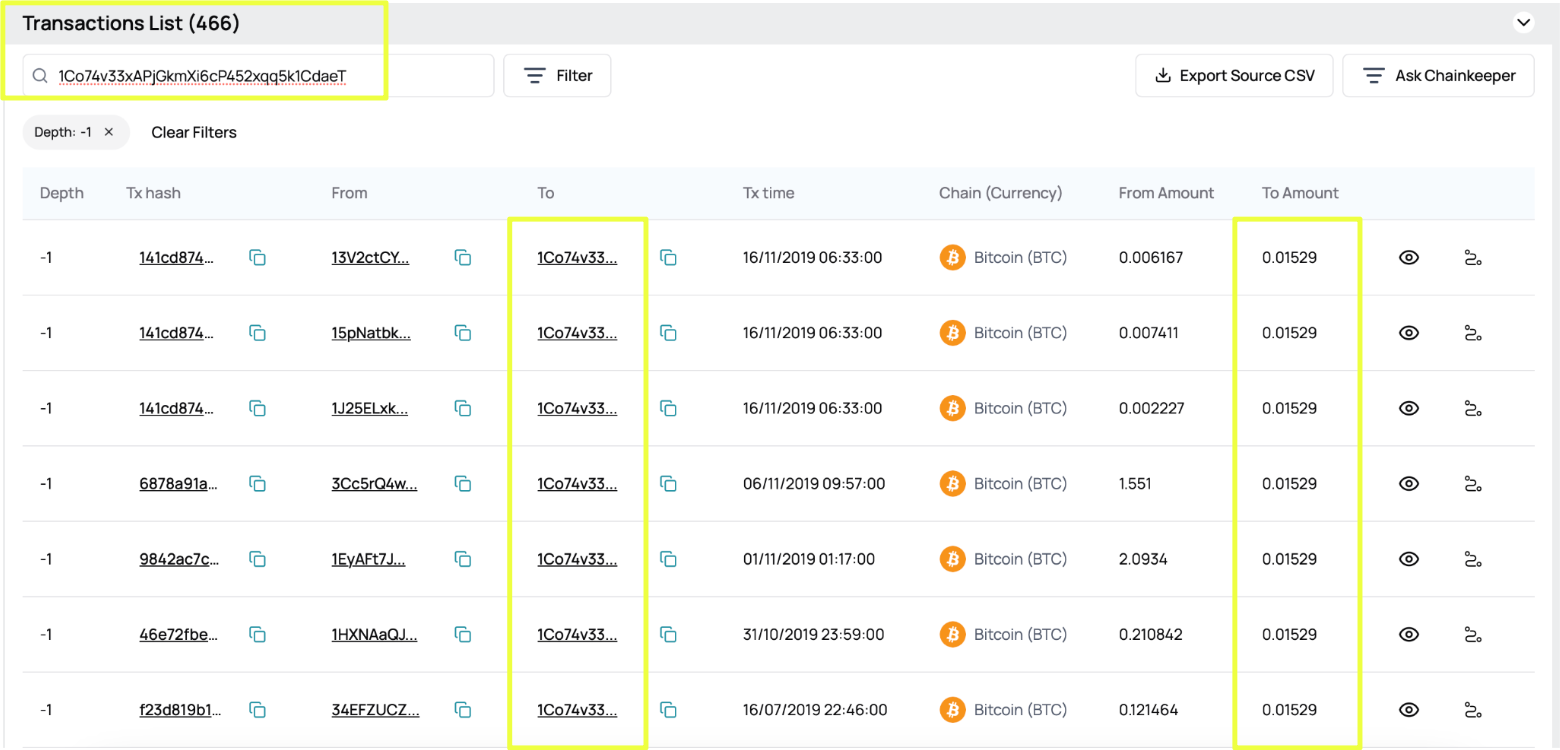
Sentinel analysis further showed that the wallet did not retain funds for extended periods. Bitcoin received by 1Co74v33xAPjGkmXi6cP452xqq5k1CdaeT was forwarded onward in structured transactions, often moving through intermediate addresses before exiting toward exchange-linked infrastructure. This behavior was consistent with a collection wallet designed for short-term receipt rather than long-term storage.
Importantly, Sentinel annotations identified one downstream address, 15cU6gZRLWU3WjpynW6zTusb3oa4H8q5ce, as having prior associations with darknet-related activity. Funds passing through this address were subsequently routed toward centralized exchanges, including Binance-linked wallets. This sequence established a complete financial path from user payment, through intermediary handling, and into exchange cash-out points.
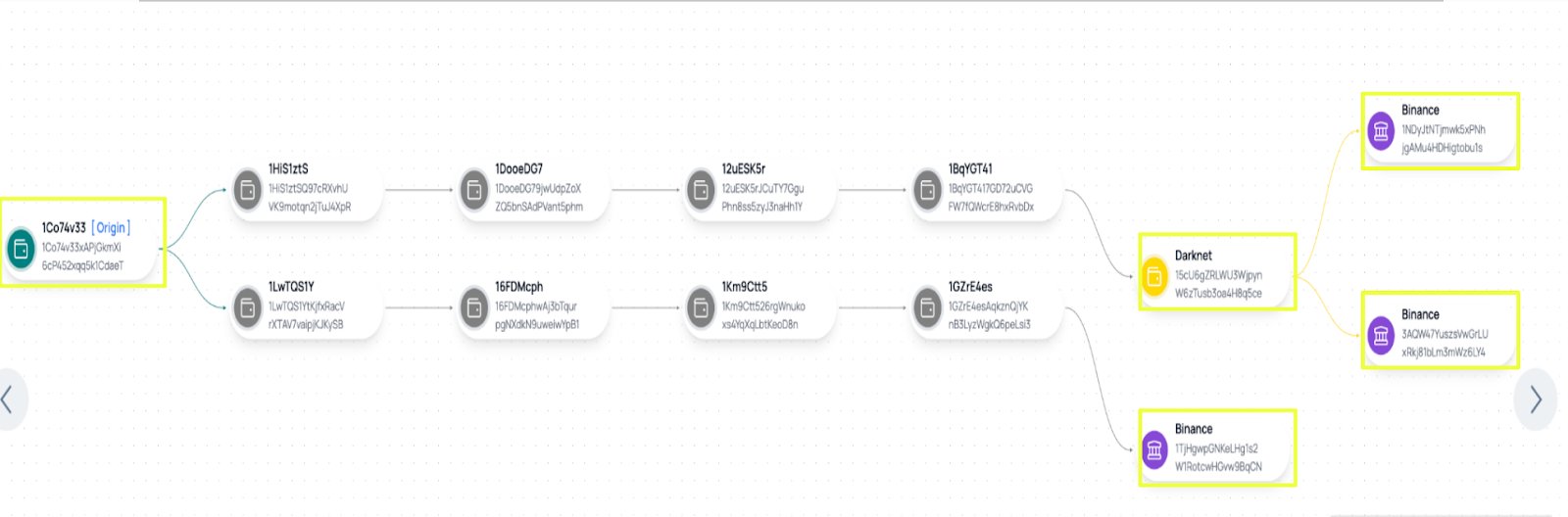
Interestingly, when this downstream address was further investigated using StealthMole, it surfaced in an external web thread that included an image of an individual alongside references to infrastructure associated with a Keybase staging server. A reverse image search of the same image led to a Facebook profile under the name А****й М****н, as well as activity on a review-based platform (lovenik.ru) using the username N**m. Related infrastructure also referenced the handle m3*****n, or the name M***k, on Keybase.
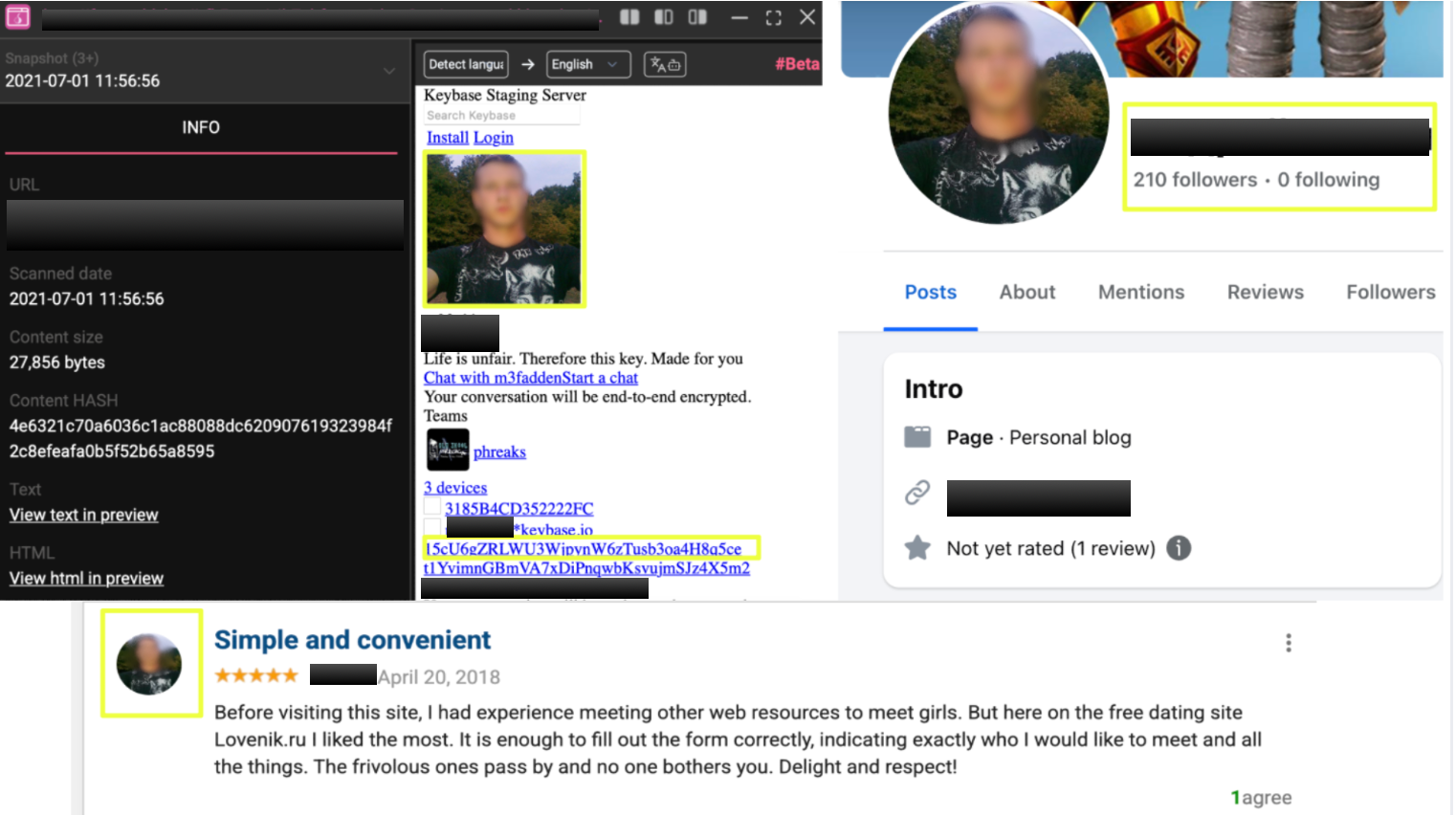
While these overlaps are not sufficient for attribution and may reflect coincidence, reuse, or deliberate misdirection, they illustrate how wallets linked to darknet financial flows can intersect with identifiable surface-web artifacts, providing additional context without establishing identity.
Taken together, Sentinel’s analysis of 1Co74v33xAPjGkmXi6cP452xqq5k1CdaeT transformed static wallet references into a coherent financial narrative. It confirmed that payments advertised on Red Room pages were received as instructed, processed through a controlled transaction flow, and ultimately liquidated through regulated exchange infrastructure.
Extended Wallet Activity and Long-Term Payment Handling
Following the analysis of the primary Red Room payment wallet, attention shifted to a second address that displayed markedly different behavior:
- 1KVcVCbvCrC9VfBJ2PVan2yq83swCQuRAZ
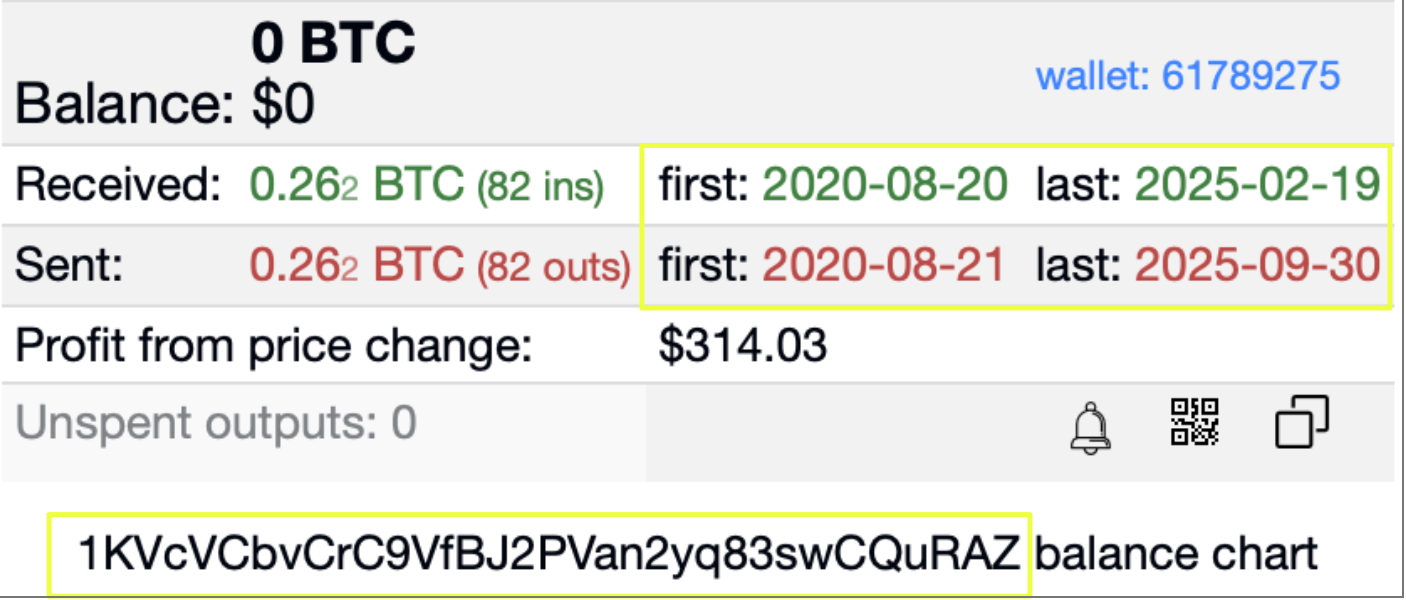
Unlike the earlier wallet, which operated within a limited timeframe, Sentinel showed that this address remained active over a much longer period, with transactions observed from August 2020 through at least September 2025. This extended lifespan immediately suggested a role beyond short-term or event-specific payment collection.
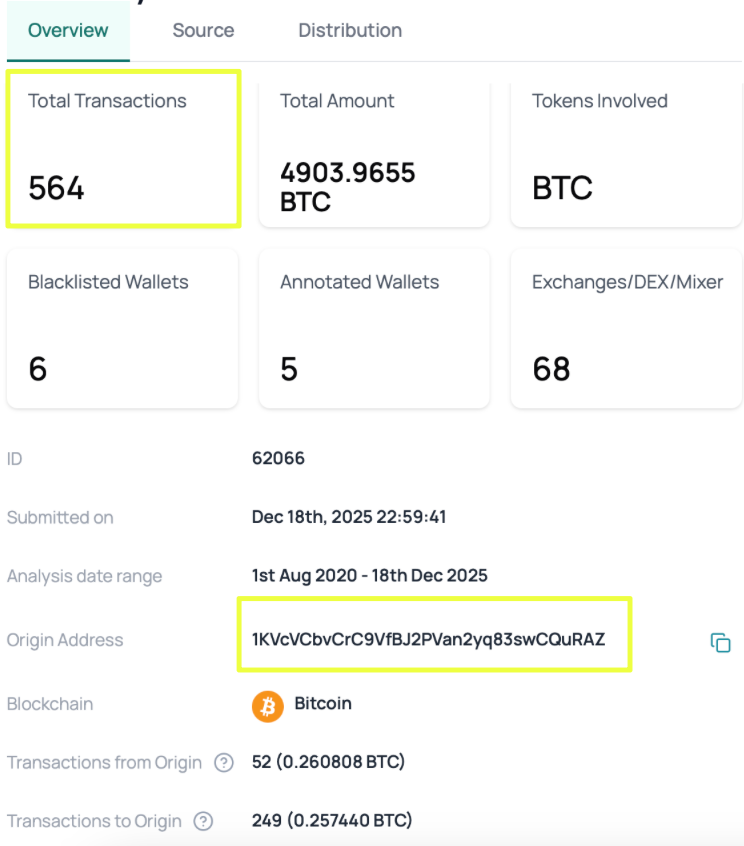
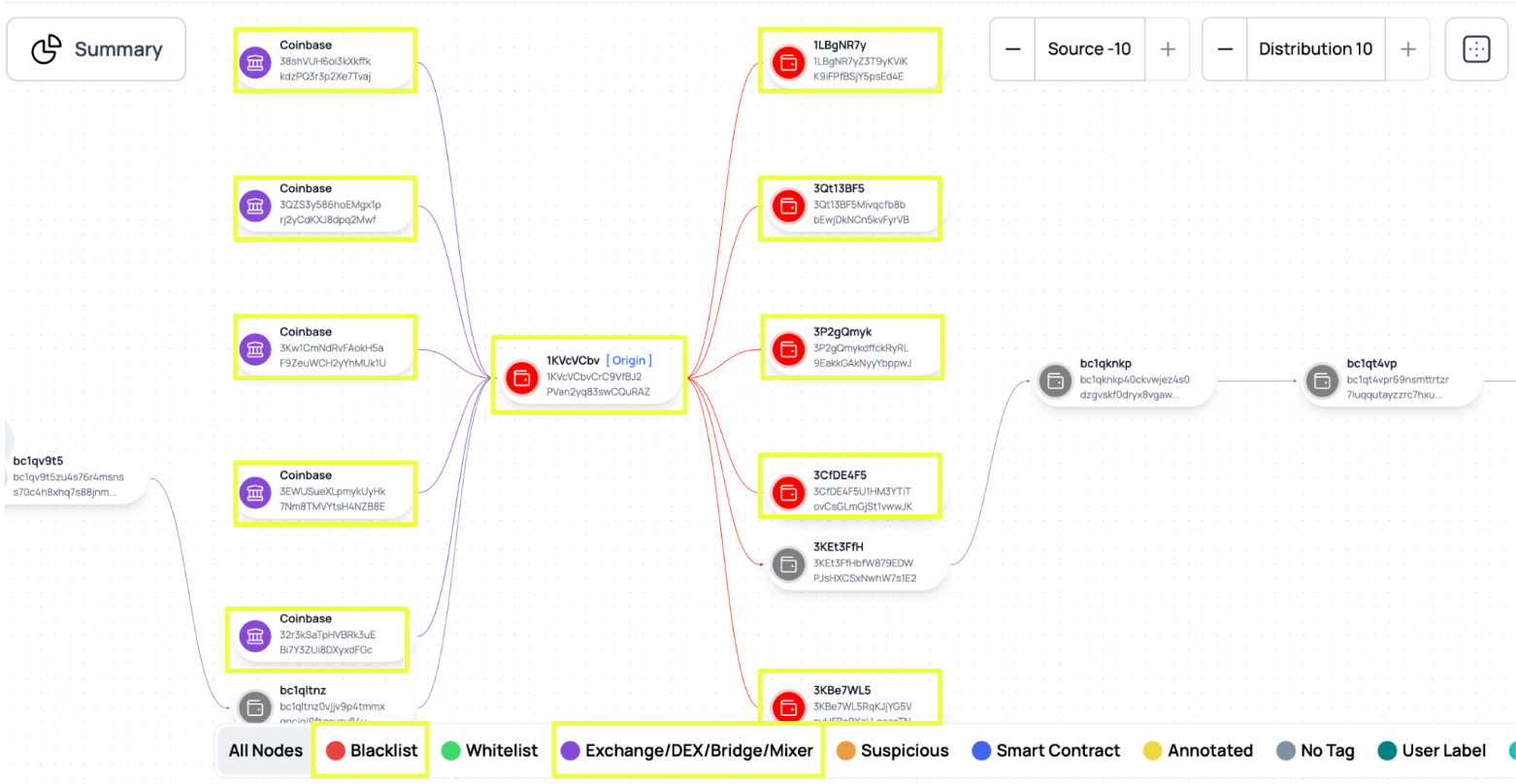
Sentinel’s transaction history revealed that this wallet received funds from a wide range of external sources rather than a small number of upstream aggregators. Notably, several inbound transactions originated from wallets associated with centralized exchanges, including Coinbase-linked addresses. These payments were not isolated incidents but occurred repeatedly over time, indicating that users were sending funds directly from regulated wallets rather than through intermediary mixing or aggregation wallets.
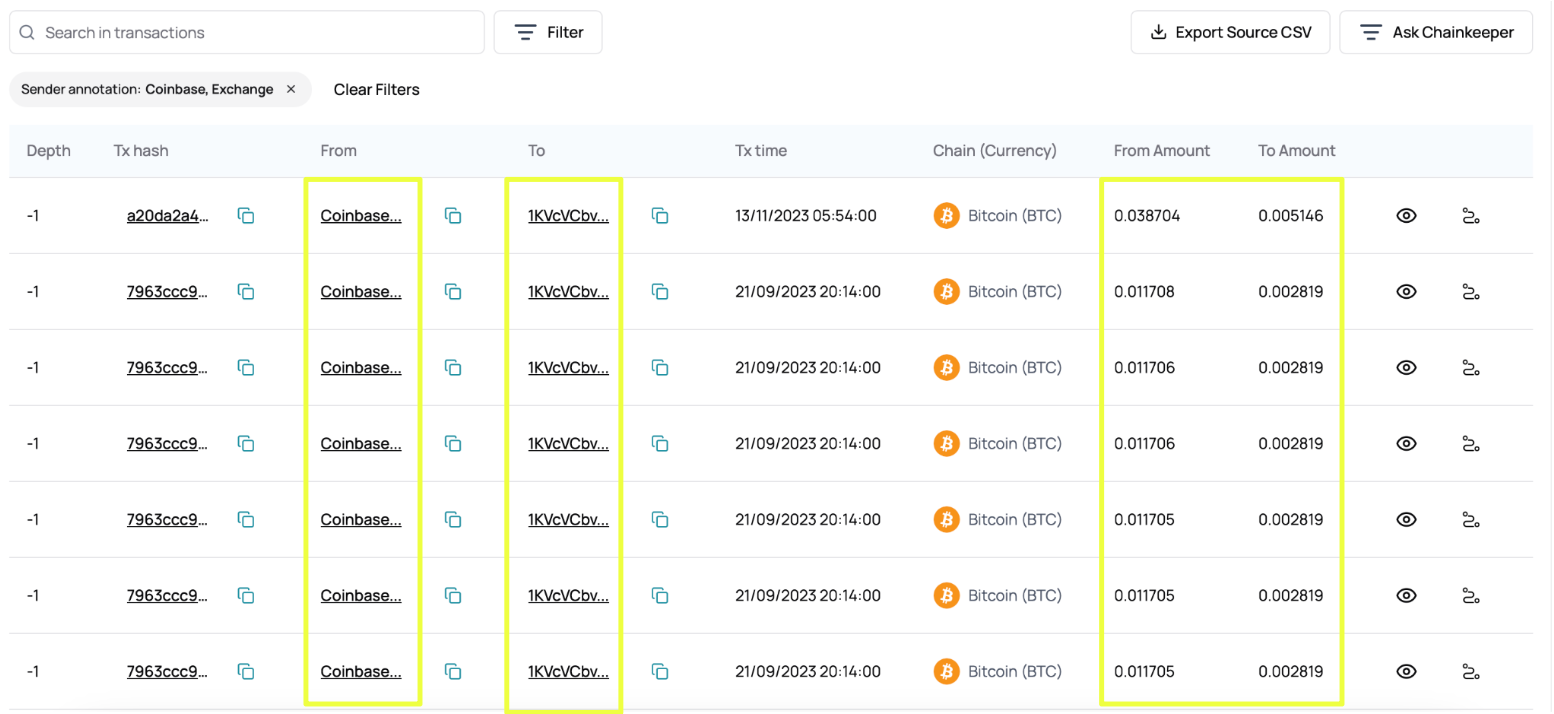
Unlike the fixed-price behavior observed for 1Co74v33xAPjGkmXi6cP452xqq5k1CdaeT, payments into 1KVcVCbvCrC9VfBJ2PVan2yq83swCQuRAZ showed minor variation in Bitcoin amounts. Sentinel’s transaction breakdown revealed clusters of near-identical values, such as 0.011705 BTC, 0.011706 BTC, and 0.011708 BTC, alongside occasional higher payments, including 0.038704 BTC. When viewed in isolation, these differences might appear inconsistent. When examined collectively, however, they aligned with users purchasing Bitcoin on exchanges at slightly different market prices and fee conditions.
Sentinel also identified that this wallet had been flagged within its intelligence framework, alongside several downstream recipient addresses. Funds entering 1KVcVCbvCrC9VfBJ2PVan2yq83swCQuRAZ were subsequently forwarded to other wallets, some of which were already associated with high-risk or darknet-linked activity. This behavior was consistent with a collection-and-distribution role rather than a terminal payment endpoint.
Importantly, this wallet appeared across Red Room–linked infrastructure in multiple contexts, including pages that referenced payment requirements different from those observed in earlier operational phases. The combination of long-term activity, exchange-sourced payments, and downstream redistribution indicates that 1KVcVCbvCrC9VfBJ2PVan2yq83swCQuRAZ functioned as a more persistent payment handler within the broader Red Room ecosystem, distinct from the short-lived, fixed-price wallet used in 2019.
Contact Points and Administrative References
In addition to payment instructions, the investigation also identified direct contact information associated with Red Room–linked discussions. Within an external thread referencing a purported Red Room event, users claiming administrative roles shared email addresses as points of contact for access, coordination, or further communication. These addresses were presented as official channels rather than user-generated speculation, suggesting an attempt to establish legitimacy and continuity beyond the dark web pages themselves.
- C.2*****************2@tutanota.com
- C.2.***************N2@tutanota.com
- C2A*****************2@tutanota.com
- og**********w@secmail.pro
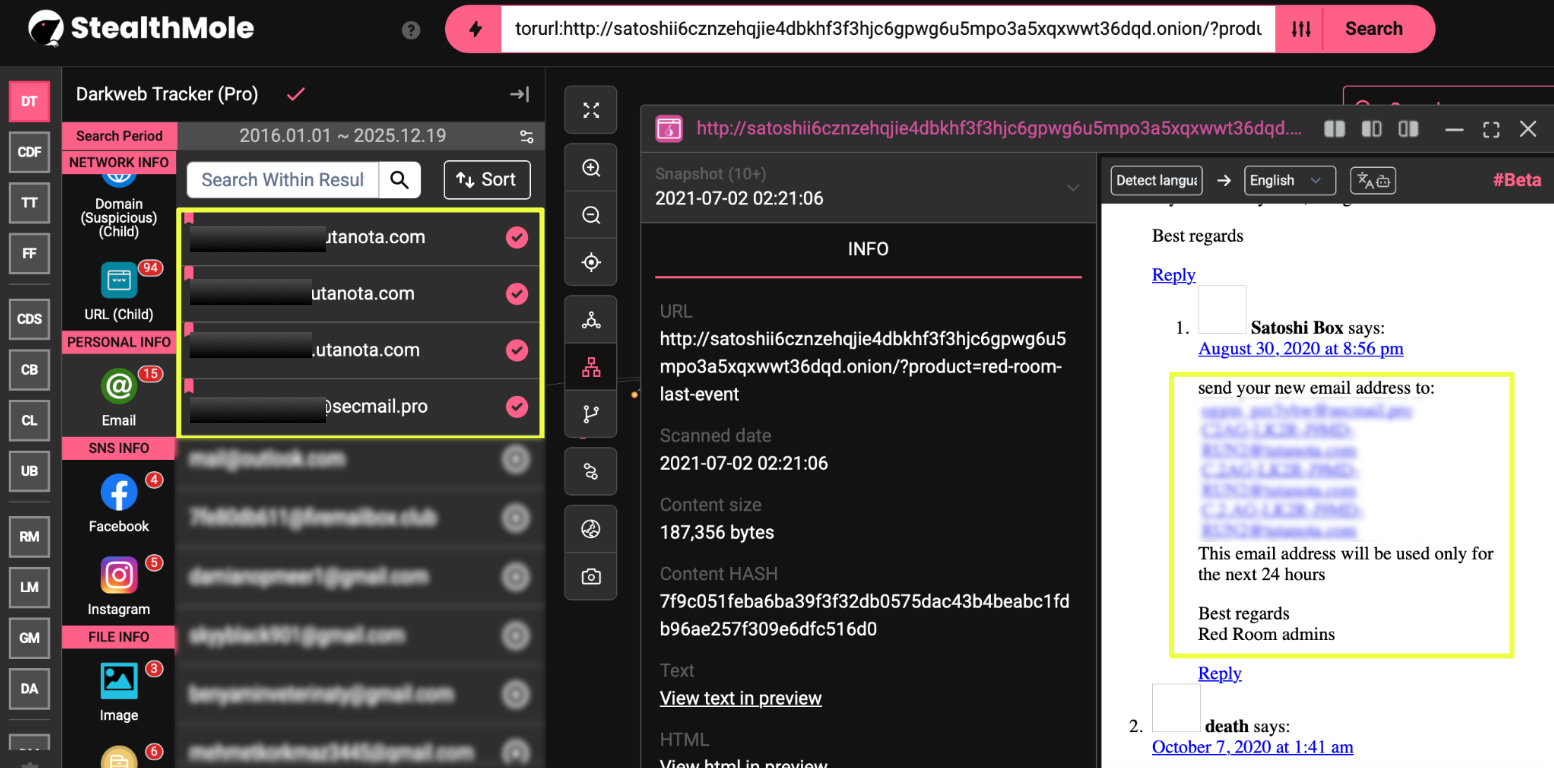
While the presence of email contact points does not confirm the identities of those operating the platform, it does indicate that communication related to Red Room activity was not confined exclusively to Tor-based infrastructure. The use of external email services introduces an additional operational surface that can persist even as domains change or sites go offline. As with other elements documented in this report, these contact references were treated as contextual artifacts rather than definitive proof, but they contribute to a broader picture of how access, coordination, and user interaction were facilitated across multiple layers.
Assessment
Taken together, the findings suggest that the Red Room–linked infrastructure examined in this report was not limited to isolated or purely speculative activity. While the web-facing components were intentionally short-lived, the payment mechanisms exposed through them showed repeat use, structured handling, and consistency across defined timeframes. This contrast indicates that the instability of the visible sites was likely a design choice rather than a sign of disorganization.
Analysis of the associated Bitcoin wallets revealed clear differences in how payment infrastructure was used. Some wallets aligned with specific operational windows, while others remained active for longer periods and received funds from a broader range of sources. Payment amounts observed on-chain consistently reflected the access requirements shown on Red Room pages, even when the exact Bitcoin values varied slightly due to market conditions or transaction structure.
Equally important is what did not emerge from the analysis. Several wallets exposed through Red Room pages showed little or no transaction activity, and others appeared only briefly. This uneven usage reinforces the importance of distinguishing between infrastructure that is publicly exposed and infrastructure that is actually operational.
Conclusion
This investigation demonstrates how Red Room–linked activity can persist despite deliberately unstable and short-lived web infrastructure. While domains and pages changed frequently, the operational elements underpinning access, particularly payment mechanisms, showed continuity that could be observed and evaluated over time. Examining these elements provided insight that would not have been apparent through site-level analysis alone.
The case also reinforces the importance of separating exposed infrastructure from functional infrastructure. Not every wallet, domain, or reference surfaced during the investigation played an active role. Meaningful conclusions were possible only by correlating where elements appeared with how they were actually used, allowing inactive or placeholder components to be distinguished from operational ones.
More broadly, this report illustrates how combining dark web monitoring with blockchain analysis enables a more reliable understanding of services designed to minimize their footprint. By aligning contextual exposure with verifiable financial behavior, it becomes possible to move beyond surface-level claims and assess operational patterns with greater confidence. As dark web platforms continue to rely on disposable infrastructure, this approach remains essential for identifying what persists when visibility is intentionally limited.
Editorial Note
While every effort has been made to ensure the accuracy of this report, it is important to acknowledge that attribution in cyber investigations can never be guaranteed with complete certainty. The connections drawn are based on available open-source intelligence along with StealthMole and Sentinel Protocol platform data. However, attribution remains probabilistic and subject to change as new information emerges.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com

.svg)
.svg)
.svg)