8Base Revisited: Tracing a Dormant Ransomware Operation
 |
8Base surfaced as a ransomware operation built around visibility. Victim disclosures were central to its strategy, with listings published across Tor-based leak sites and, at times, mirrored through surface-level infrastructure. Throughout 2023 and into early 2024, the group remained consistently present in ransomware reporting, maintaining a steady cadence of victim publications before abruptly going quiet.
That silence followed the seizure of its primary onion site by law enforcement. After the takedown, 8Base stopped appearing in new victim disclosures and gradually faded from public view, leading many to treat the operation as concluded. But ransomware groups rarely vanish cleanly, and disappearance alone is often a poor indicator of whether an operation has truly ended.
This investigation revisits 8Base with a different question in mind, not whether it was taken down, but what traces it left behind. By examining residual infrastructure, dormant communication channels, and technical artifacts preserved through StealthMole’s historical indexing, dark web tracking, and Telegram monitoring, the analysis reconstructs how the operation evolved over time. What emerges is not a clean shutdown, but a fragmented footprint that overlaps with other ransomware ecosystems, suggesting continuity beneath the surface even after the brand itself went quiet.
Incident Trigger and Initial Investigation
The decision to investigate 8Base came from its absence rather than its activity. By the time this case was initiated, the group had been offline for several months, and most public reporting treated it as a concluded ransomware operation. That assumption raised a simple question: was 8Base truly gone, or had it merely gone quiet?
Rather than looking for new victims or fresh extortion attempts, the investigation focused on what might still be accessible. Ransomware groups rarely disappear cleanly. Even after takedowns, traces often remain in the form of abandoned infrastructure, forgotten communication channels, or technical artifacts that outlive the brand itself. The goal was to map those remnants and assess whether anything of intelligence value still persisted.
The first step was to ground the investigation in confirmed activity. A review of 8Base within StealthMole’s ransomware monitoring tool showed that the group had recorded 459 victims between May 2023 and February 2025. This confirmed that 8Base was active far more recently than many assumed and provided a clear operational timeframe to work within.
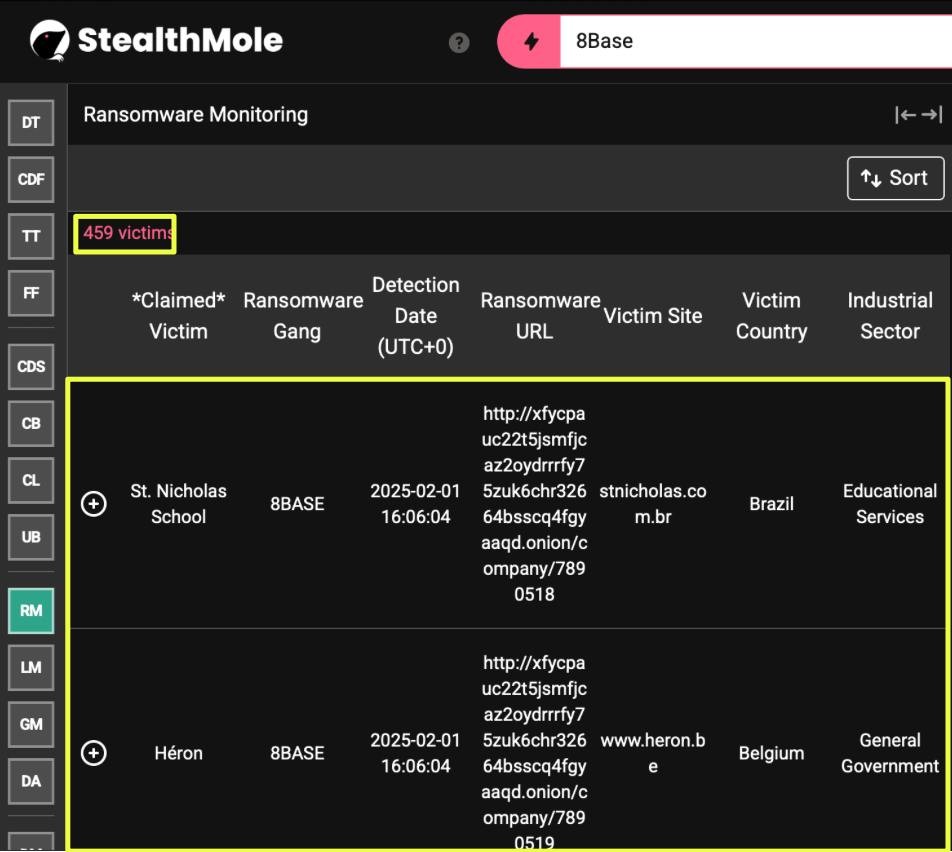 |
The final recorded victim, dated 1 February 2025, was St. Nicholas School in Brazil, which became the starting point for tracing 8Base’s infrastructure backward, following the same path an analyst would have followed while the group was still active.
Tracing the Primary Leak Site
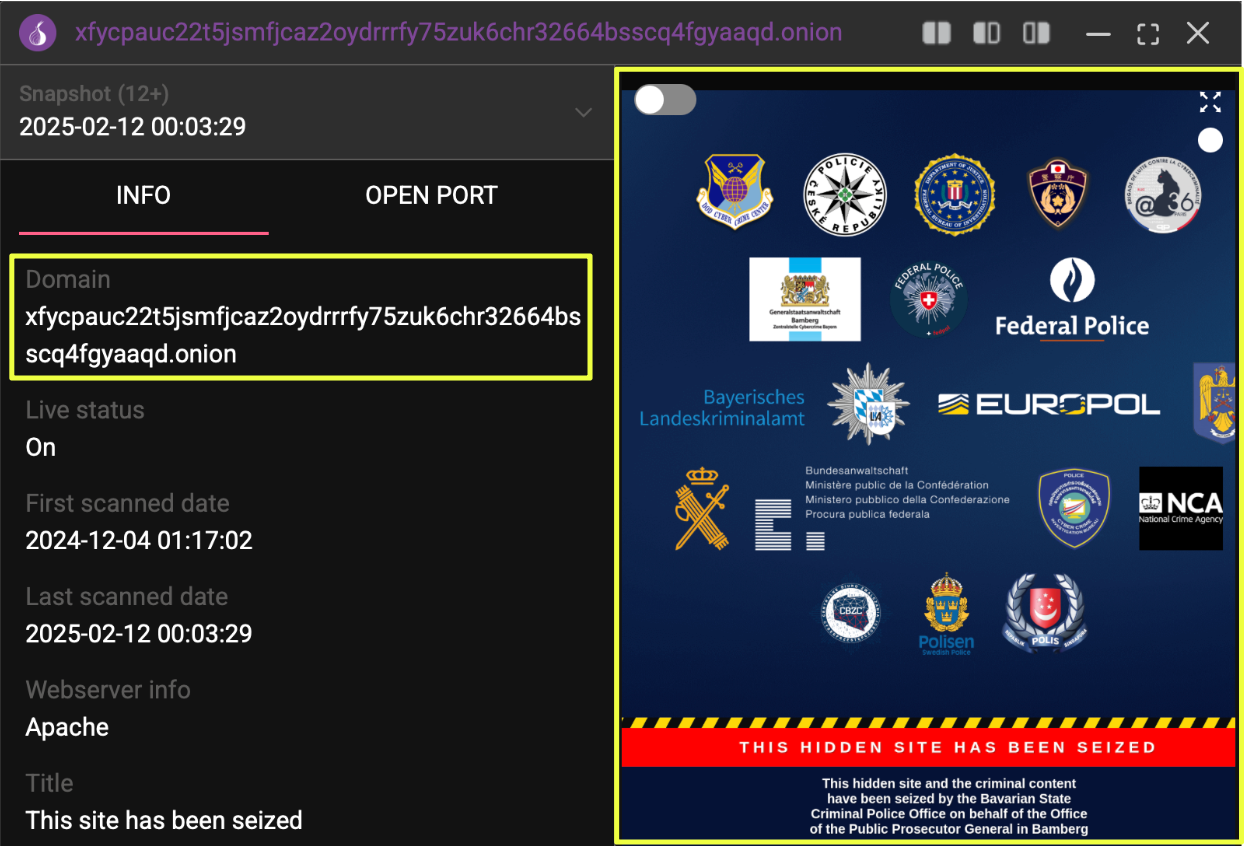
Following the final victim listing led directly to the ransomware leak site where the disclosure had been published. When accessed during the investigation, the site was still reachable over Tor but displayed a law enforcement seizure banner, confirming that authorities had taken control of the infrastructure rather than simply going offline.
- http://xfycpauc22t5jsmfjcaz2oydrrrfy75zuk6chr32664bsscq4fgyaaqd.onion/
 |
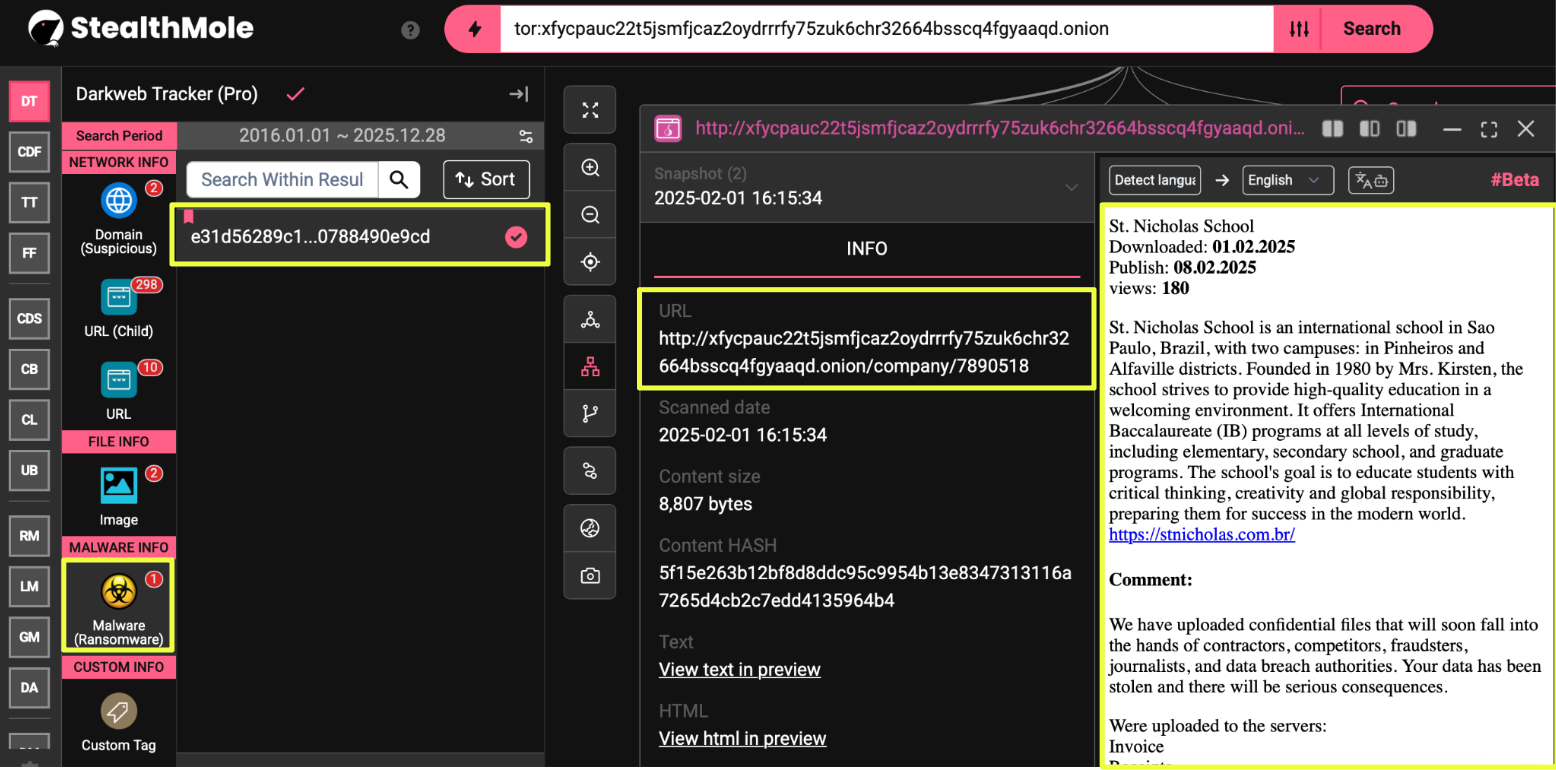
Using StealthMole’s historical indexing feature, it was possible to view how the site appeared prior to the seizure. Archived snapshots showed a fully functioning extortion portal, complete with victim pages, descriptive summaries, and publication timelines. This confirmed that the site was not a mirror or scraped archive, but a core component of 8Base’s operation.
When the site was analyzed further using StealthMole’s dark web tracker, a malware hash surfaced in connection with the infrastructure:
- e31d56289c1957053630383ff71959cba08521874410bd78e46680788490e9cd
 |
This discovery shifted the focus of the investigation. While domains can be seized and channels abandoned, malware hashes tend to persist, offering a longer-lasting signal than any single piece of infrastructure.
Telegram as the Remaining Communication Layer
With the primary infrastructure identified, attention turned to whether 8Base had maintained any communication presence beyond its seized site. The onion domain was searched across StealthMole’s Telegram tracker, which surfaced an invite-only chat channel that had circulated the same onion address shortly before the takedown:
- https://t.me/+GxHjaDP0bOphZjNh
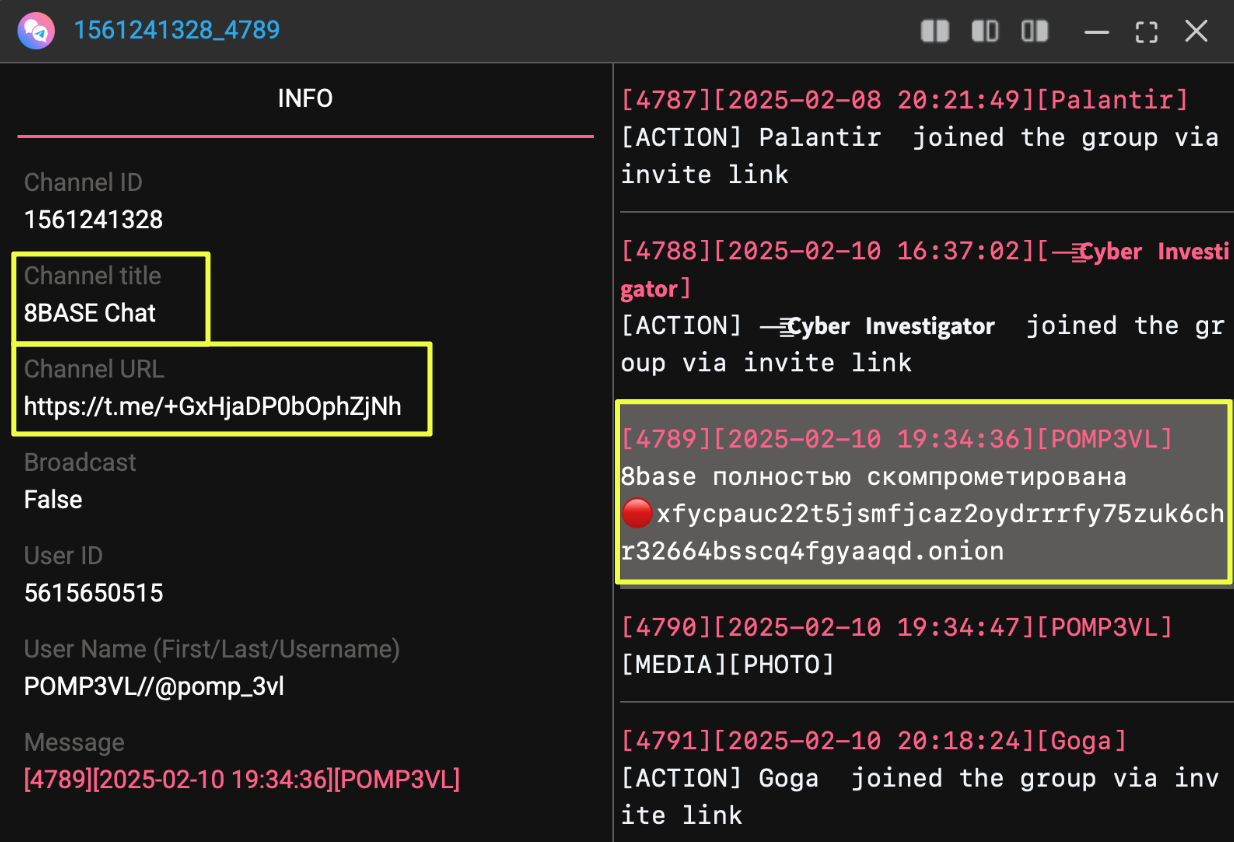 |
Although the channel is no longer accessible, historical messages provide context into how 8Base-linked infrastructure was being discussed in the period surrounding the takedown. One message explicitly stated that 8Base had been compromised and referenced the seized onion site. While the identity of the poster cannot be verified, the message reflects how the takedown was perceived within adjacent communities.
Further analysis revealed a second Telegram channel with a different purpose and structure:
- https://t.me/eightbase
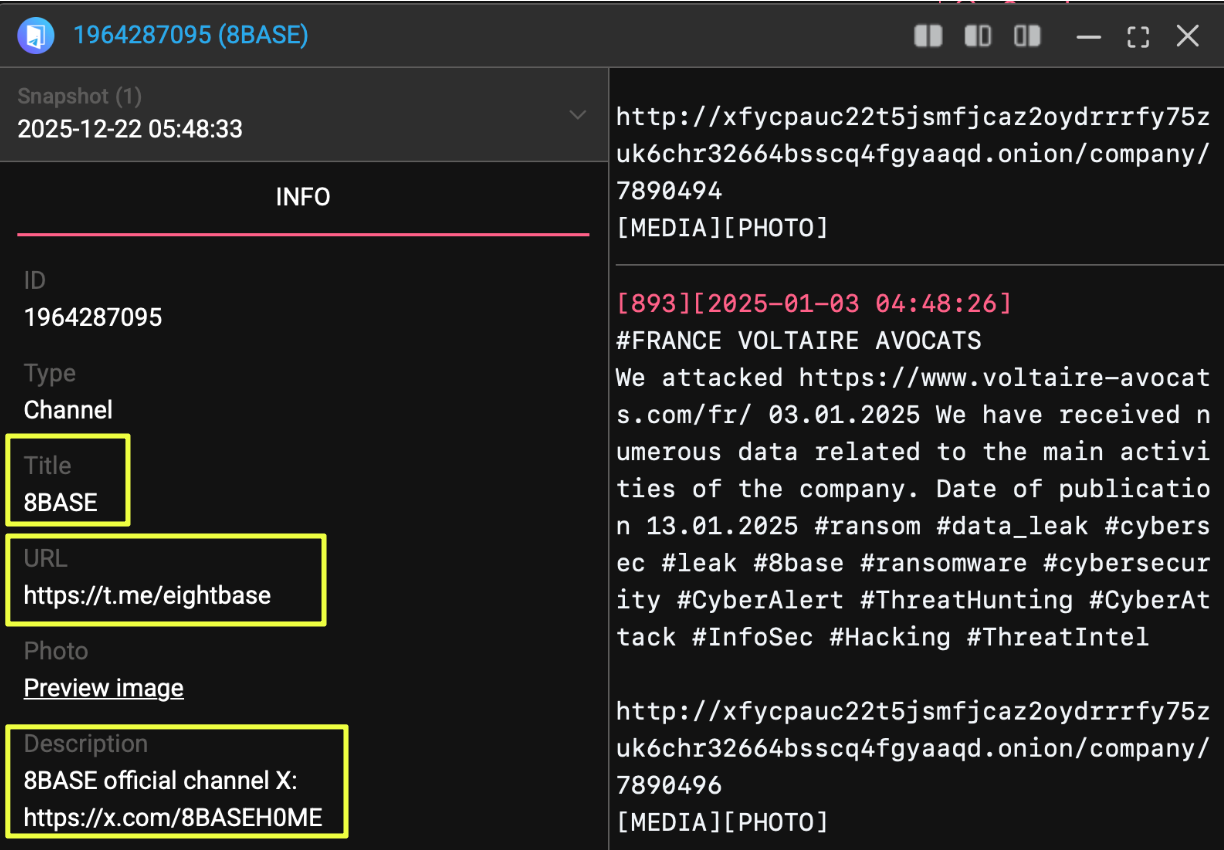 |
This channel described itself as the official 8Base channel and functioned as a broadcast outlet rather than an open chat. Unlike the invite-only channel, it remains online, though its administrators have been inactive for months. The contrast between these two channels suggests a layered communication strategy rather than a single point of contact.
Official Messaging, Social Media, and Infrastructure Changes
The official Telegram channel provided a clearer timeline of 8Base’s public-facing activity. Created in May 2023, it was used to post announcements, infrastructure updates, and links to external platforms. While activity has ceased, the historical messages remain accessible and offer insight into how the group managed disruption.
Within the channel, 8Base linked to its X account:
- https://x.com/8BASEHOME
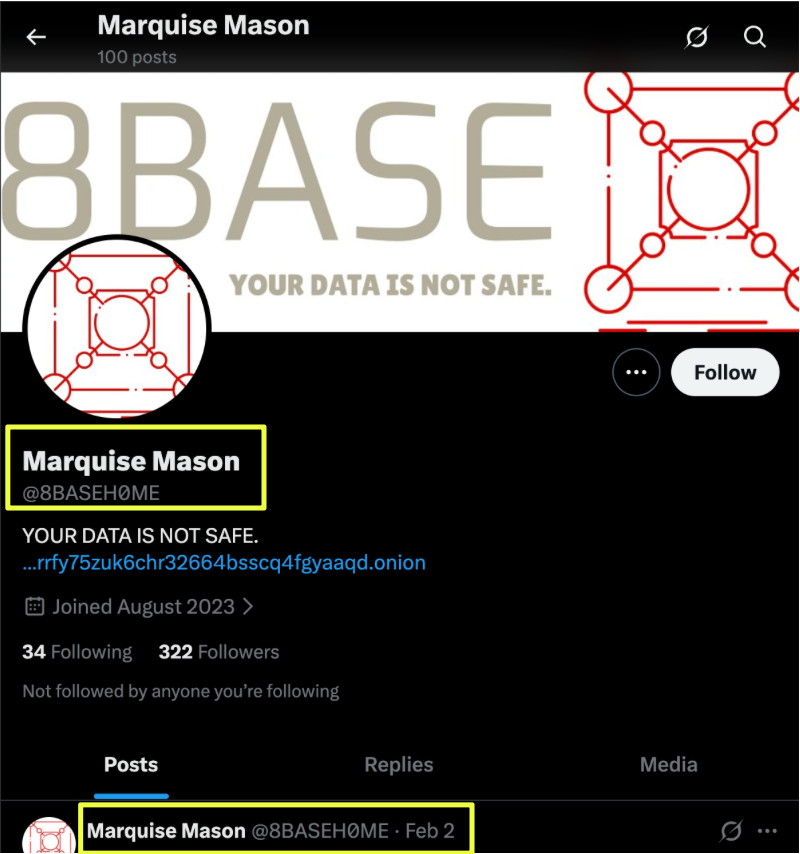 |
Messages from 2023 explained that a previous Twitter account had been suspended, prompting the creation of this replacement. The X account itself remains online but has shown no activity since 2 February 2025, closely aligning with the group’s disappearance elsewhere.
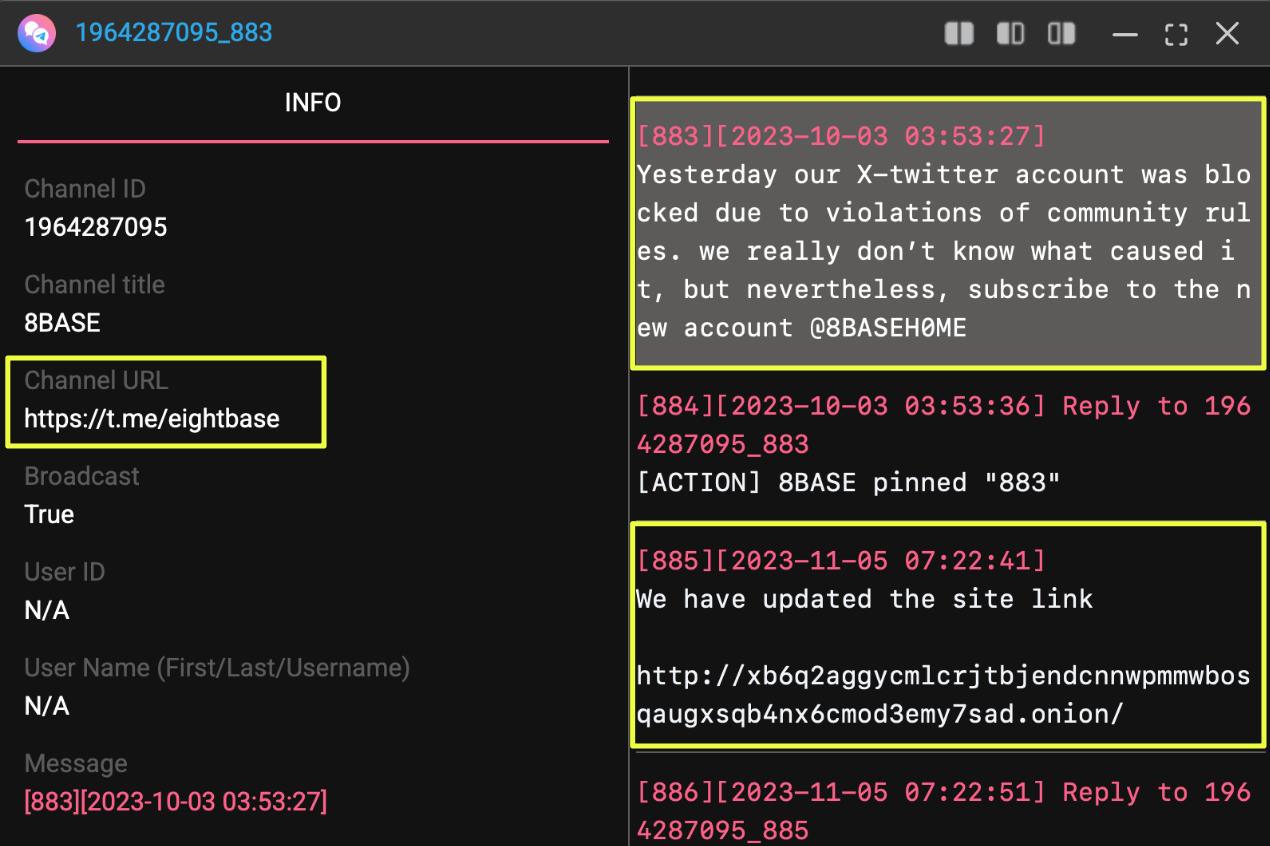 |
One Telegram post from late 2023 announced a change to the group’s website and shared a new onion address:
- xb6q2aggycmlcrjtbjendcnnwpmmwbosqaugxsqb4nx6cmod3emy7sad.onion
This was not the site later seized by law enforcement, indicating that 8Base had already begun rotating infrastructure well before any coordinated takedown.
Earlier Infrastructure and Surface-Level Presence
By the time the official Telegram channel was identified, it had already become clear that 8Base did not rely on a single piece of infrastructure throughout its lifetime. Further analysis of the channel revealed another onion domain linked to the group:
- basemmnnqwxevlymli5bs36o5ynti55xojzvn246spahniugwkff2pad.onion
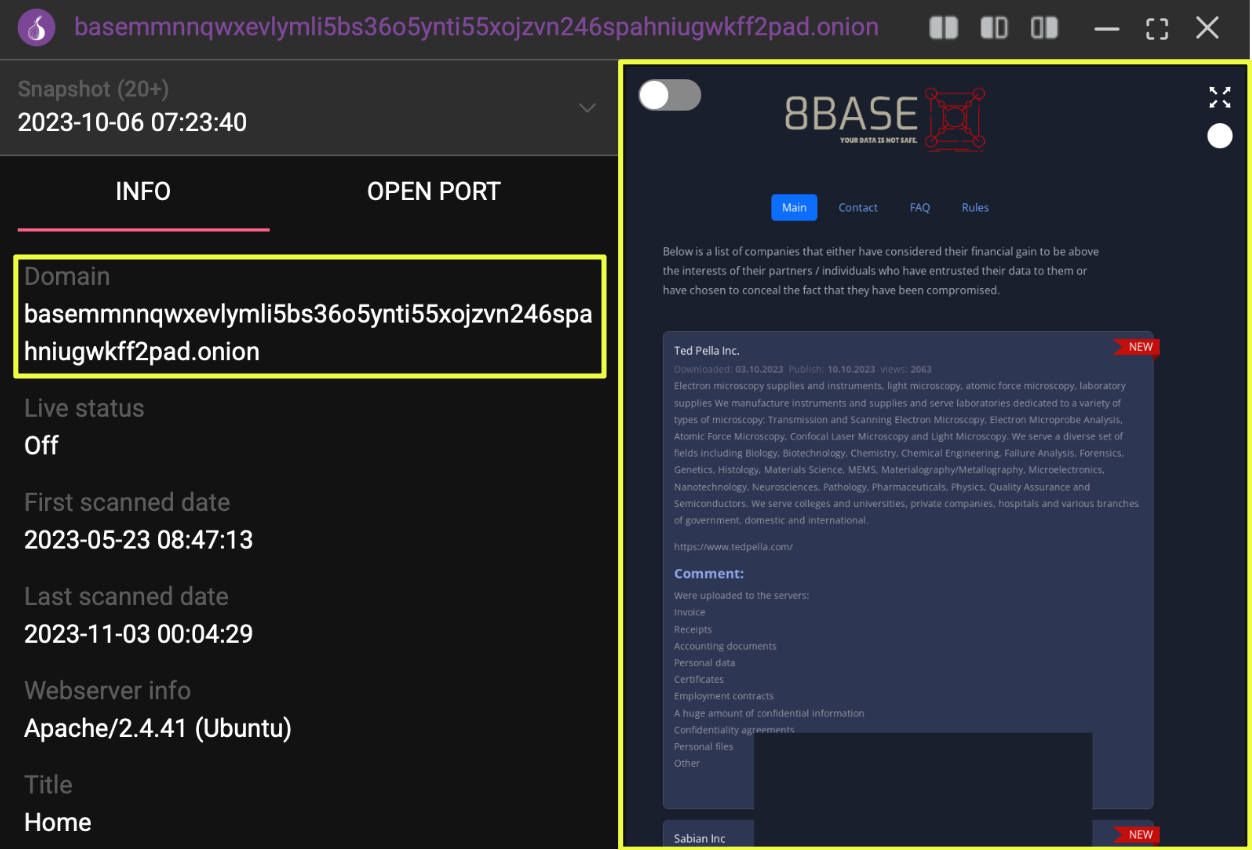 |
Unlike the site that was later seized by law enforcement, this domain was already offline by the time it appeared in StealthMole’s historical records. There was no seizure banner and no indication of intervention, suggesting it had been abandoned earlier as part of routine infrastructure churn rather than forced takedown. This places the domain as an earlier iteration rather than a successor.
This detail matters because it suggests that 8Base was already accustomed to rotating or discarding infrastructure well before external pressure became visible. Rather than reacting to disruption, the group appears to have operated with an expectation that sites would eventually fail, be blocked, or become liabilities. In that sense, the law enforcement seizure did not interrupt a stable system, it simply accelerated an already transient model.
The presence of a surface-level site reinforces this pattern. Telegram messages pointed to a publicly accessible IP address that hosted 8Base-branded content:
- http://92.118.36.204
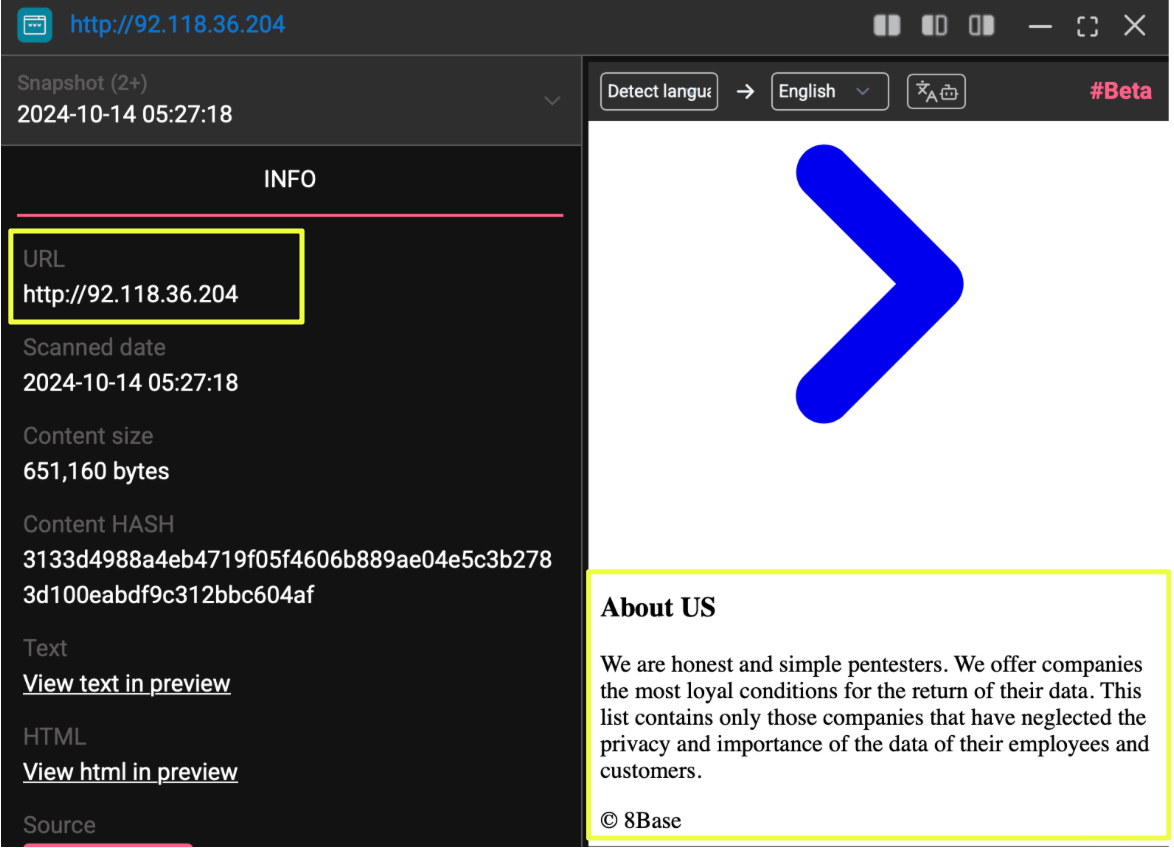 |
The decision to maintain a surface site alongside Tor infrastructure is notable. While riskier, it provides broader visibility, easier access for journalists or intermediaries, and redundancy if Tor services become unreliable. At the same time, it dramatically increases exposure to monitoring and attribution, which may explain why the site was eventually abandoned rather than defended.
Viewed together, these infrastructure layers suggest that 8Base treated domains as disposable assets rather than fixed anchors. Onion services came and went, surface infrastructure was briefly leveraged, and communication channels carried the continuity instead. This approach aligns more closely with ransomware-as-a-service ecosystems than with tightly controlled, single-group operations.
How 8Base Framed Its Own Operations
Insight into how 8Base claimed to operate came primarily from the FAQ page hosted on its surface-level site, accessible at:
- http://92.118.36.204/faq/44
While the site is no longer online, historical snapshots preserved by StealthMole provide a detailed view of how the group structured its extortion workflow and victim interactions. Unlike brief ransom notes or generic leak pages, the FAQ laid out a multi-stage process that attempted to formalize how victims were handled from initial compromise to potential disclosure.
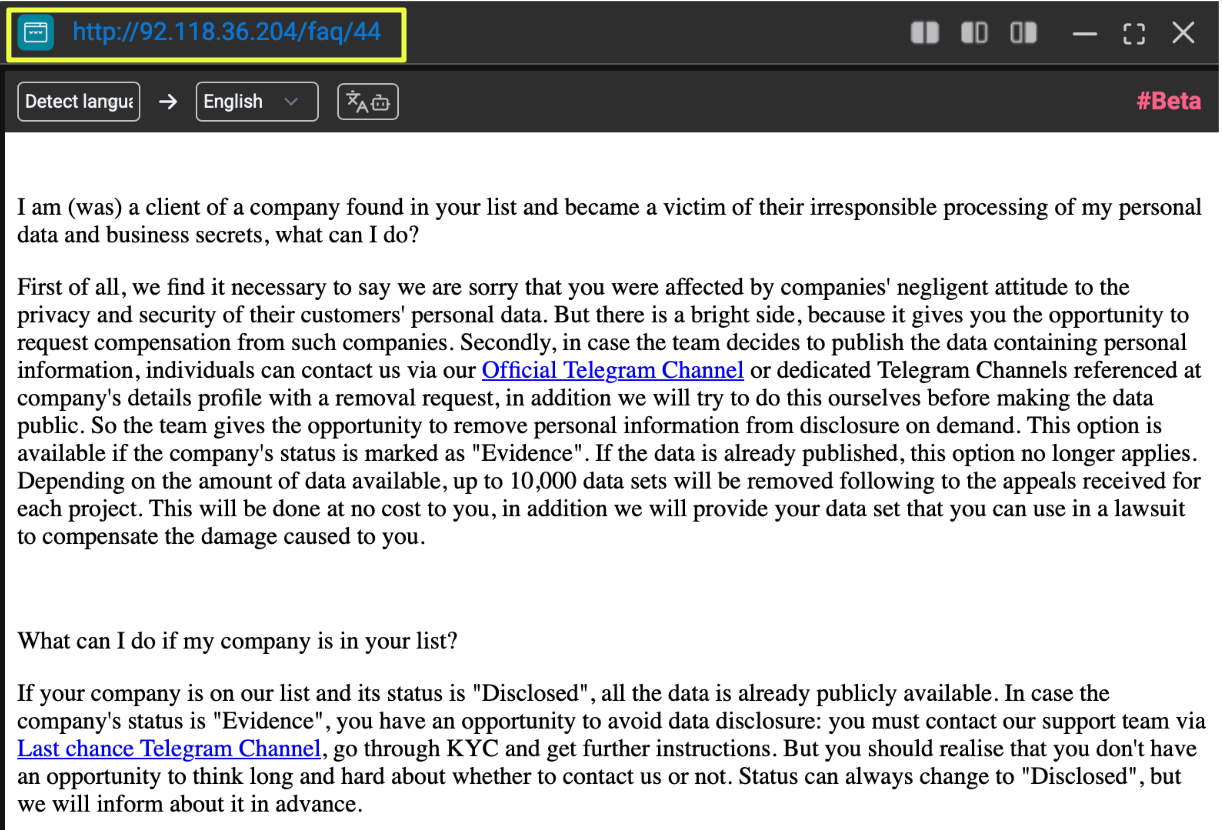 |
8Base divided victim cases into distinct stages. Newly compromised organizations were first placed in an “evidence” state, where limited proof of access or data theft was shown. This phase functioned as a pressure mechanism without immediate full disclosure. If negotiations failed or communication stopped, victims were moved to a “disclosed” state, where broader datasets were published publicly. This tiered approach mirrors common ransomware extortion models but shows deliberate staging rather than immediate escalation.
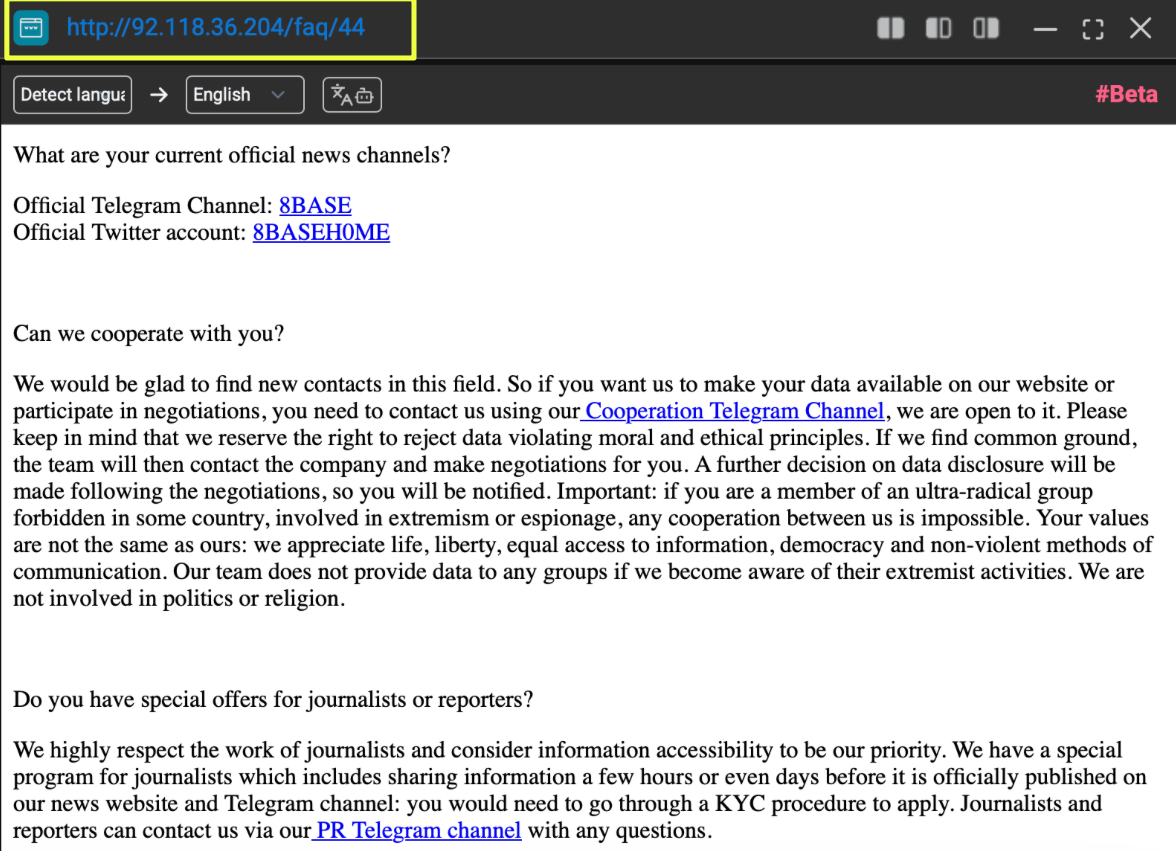
Negotiation was positioned as central to the operation. The FAQ emphasized Telegram as the primary channel for communication, directing victims to engage through designated Telegram accounts rather than email or web forms. It also described a “last chance” negotiation window, suggesting that victims retained the ability to engage even late in the process, though under increasing time pressure. This indicates that 8Base prioritized real-time, controllable communication channels that could be abandoned or replaced quickly if compromised.
 |
The group also described internal rules around what data would be published and what could potentially be withheld. While these claims cannot be verified, they outline how 8Base attempted to standardize decision-making across cases, rather than treating each victim as an ad hoc negotiation. The FAQ mentioned limits on the volume of personal data released and conditions under which partial removal might occur, suggesting an effort to balance pressure with perceived credibility.
Beyond victim negotiations, the FAQ also outlined how 8Base managed external communication. Journalists were encouraged to make contact through dedicated Telegram channels and were offered early access to data prior to public release. This reflects an understanding of media amplification as an extension of the extortion process, using publicity to increase pressure on victims rather than relying solely on private negotiation.
Malware Hashes and a Broader Ransomware Ecosystem
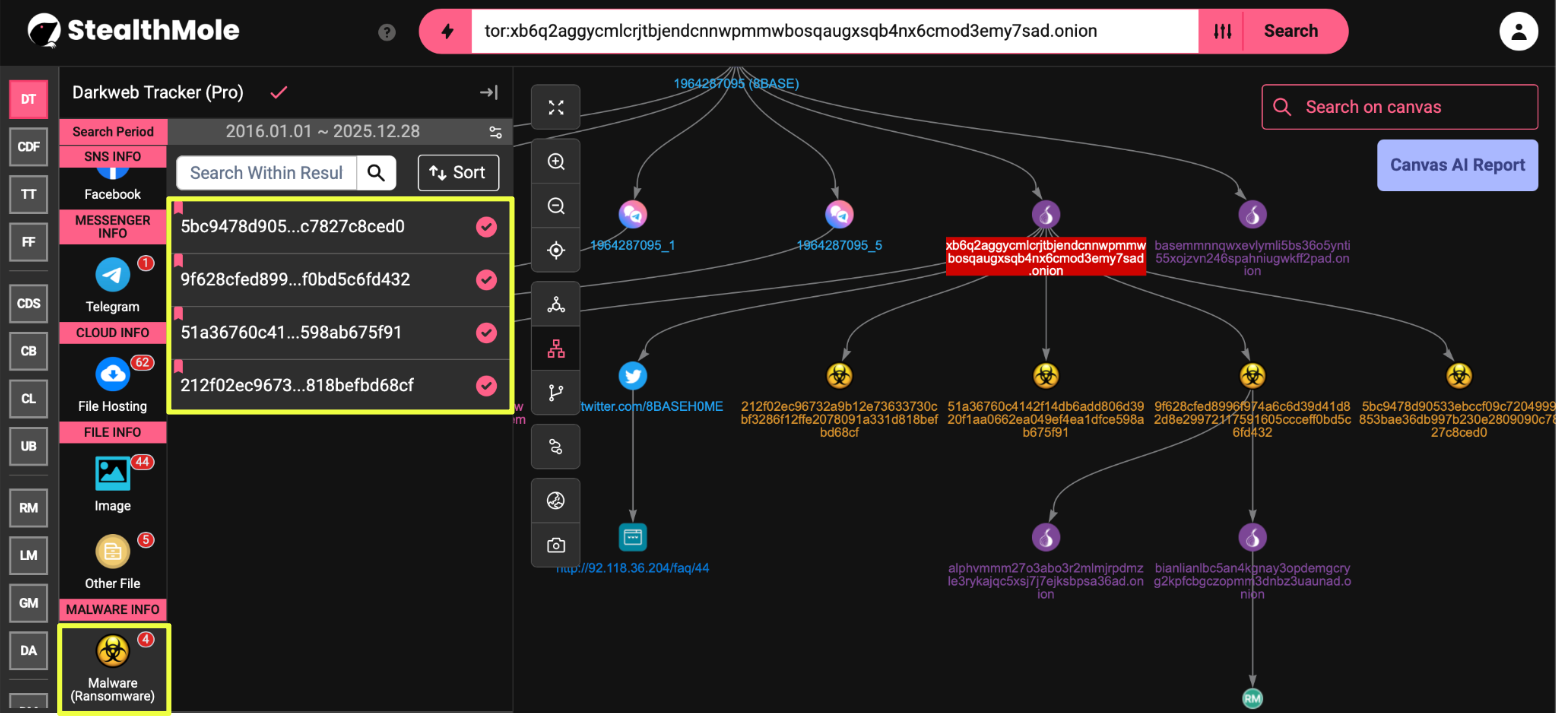
The most analytically significant findings emerged when one of the rotated onion domains xb6q2aggycmlcrjtbjendcnnwpmmwbosqaugxsqb4nx6cmod3emy7sad.onion was examined through StealthMole’s dark web tracker. This analysis surfaced four malware hashes associated with the infrastructure:
- 212f02ec96732a9b12e73633730cbf3286f12ffe2078091a331d818befbd68cf
- 51a36760c4142f14db6add806d3920f1aa0662ea049ef4ea1dfce598ab675f91
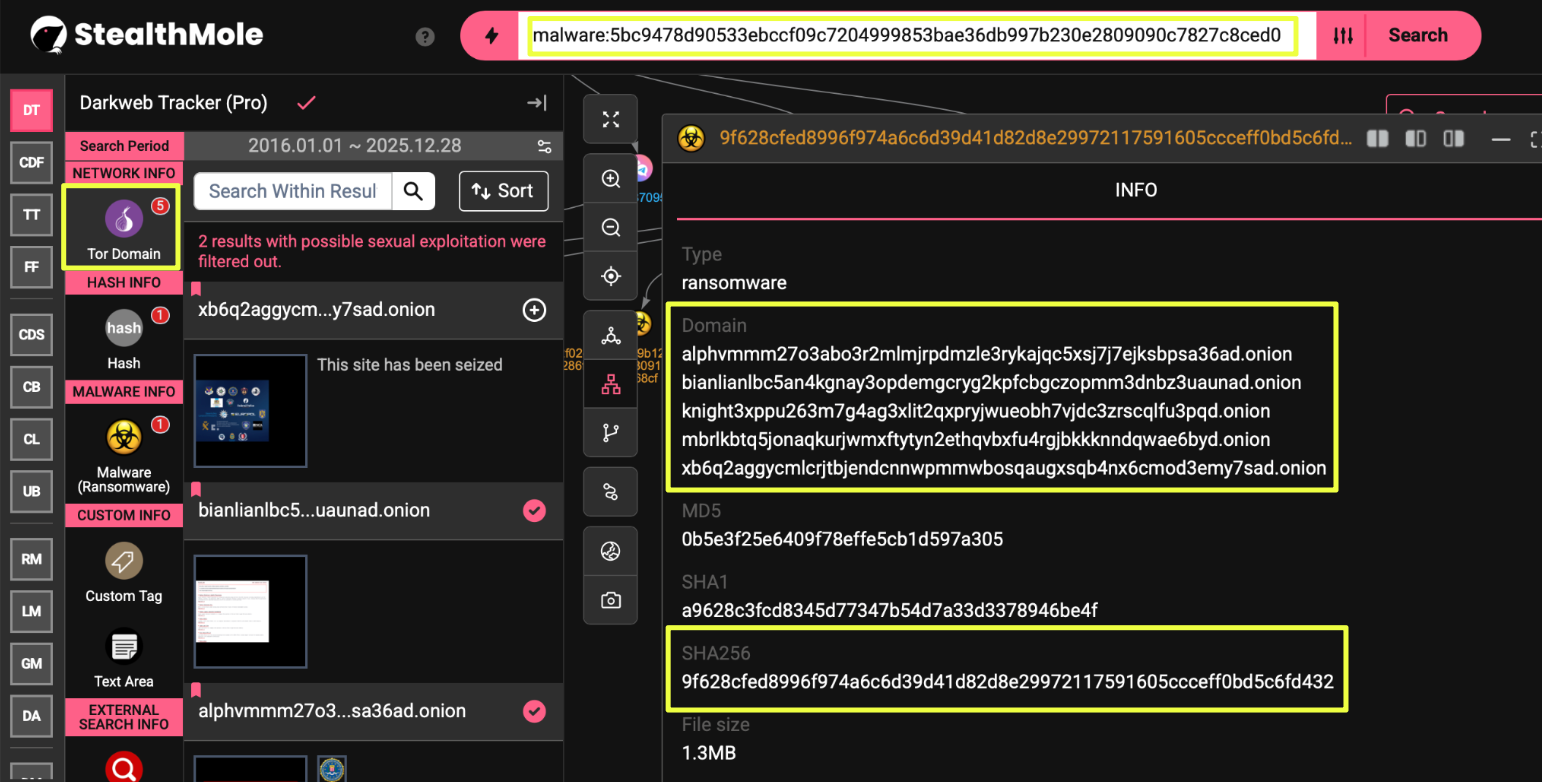
- 9f628cfed8996f974a6c6d39d41d82d8e29972117591605ccceff0bd5c6fd432
- 5bc9478d90533ebccf09c7204999853bae36db997b230e2809090c7827c8ced0
 |
At first glance, the presence of multiple hashes tied to a single onion site might suggest routine tooling updates or payload variations. However, the significance lies not in their quantity, but in their reuse beyond 8Base’s infrastructure.
Two of these hashes: 9f628cfed8996f974a6c6d39d41d82d8e29972117591605ccceff0bd5c6fd432 and 5bc9478d90533ebccf09c7204999853bae36db997b230e2809090c7827c8ced0 were also observed across onion sites associated with several other ransomware operations, including ALPHV, BianLian, Knight, and Play:
- Alphvmmm27o3abo3r2mlmjrpdmzle3rykajqc5xsj7j7ejksbpsa36ad.onion
- bianlianlbc5an4kgnay3opdemgcryg2kpfcbgczopmm3dnbz3uaunad.onion
- knight3xppu263m7g4ag3xlit2qxpryjwueobh7vjdc3zrscqlfu3pqd.onion
- mbrlkbtq5jonaqkurjwmxftytyn2ethqvbxfu4rgjbkkknndqwae6byd.onion
 |
A deeper look at the malware itself helps clarify this overlap. Strings extracted from the binary show that it was written in Go and includes a fully developed extortion workflow, not just encryption logic. Embedded messages reference data exfiltration, staged disclosure timelines, proof-of-compromise materials, and media pressure, elements that align closely with how large ransomware operations structure negotiations. This suggests the malware was designed to integrate directly with leak-site-driven extortion rather than function as a standalone locker.
More notably, the strings explicitly reference multiple ransomware leak sites and communication channels, including onion URLs associated with ALPHV, BianLian, Knight, Play, and 8Base itself. This indicates that the overlap was not accidental reuse or post-compromise contamination, but deliberate design. The malware appears to have been built with awareness of multiple branded operations, capable of operating within different extortion ecosystems depending on deployment. In other words, the same tooling could support multiple “groups” without requiring each to maintain its own bespoke malware.
This reframes how 8Base should be understood. Rather than operating as a fully independent ransomware group with unique infrastructure and tooling, 8Base fits more naturally into a shared-backend model. Under this structure, branding, victim portals, and Telegram channels form the visible layer, while malware development and infrastructure provisioning sit beneath it. When a brand becomes exposed or compromised, as 8Base eventually was, it can be retired without disrupting the underlying technical framework.
From an intelligence perspective, this is precisely why the malware hashes matter more than the seized domains. Onion sites can be rebuilt, Telegram channels can be renamed, and brands can be abandoned. Malware artifacts, especially when reused across multiple ecosystems, offer a far more stable signal. If these hashes or closely related variants surface again, they provide a direct line back to this cluster of activity, regardless of what name is attached to it next.
Conclusion
The takedown of 8Base’s primary leak site marked the end of its public operations, but it did not erase the group’s footprint. The investigation shows that infrastructure was already fluid before enforcement action, with multiple onion domains, a short-lived surface presence, and communication channels that gradually fell silent rather than being dismantled. What remains is a set of artifacts that reflect how the operation functioned, adapted, and ultimately fragmented.
The most significant insight comes from the malware artifacts linked to 8Base infrastructure. Hash overlap with several other ransomware operations suggests that 8Base was embedded within a shared ecosystem rather than operating in isolation. This points to common tooling or infrastructure dependencies that outlived the brand itself, offering a more durable signal than any single domain or channel.
Taken together, these findings position 8Base as a dormant operation rather than a resolved one. While the name may no longer appear in victim disclosures, the technical traces mapped in this investigation remain relevant. If related activity resurfaces under a different identity, those same remnants are likely to provide the first indication of continuity.
Editorial Note
Investigating ransomware groups after takedown often means working with fragments rather than conclusions. Infrastructure disappears unevenly, narratives fade, and attribution becomes less certain over time. This case illustrates how focusing on residual signals, rather than live activity, can still yield meaningful intelligence.
By using StealthMole to reconstruct infrastructure history, trace communication layers, and correlate technical artifacts, this investigation demonstrates how uncertainty can be navigated without overreach. In the case of 8Base, what remains offers more insight than what was taken down.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Featured, Ransomware

.svg)
.svg)
.svg)