SAPPORO88: Inside an Indonesian-Focused Illegal Gambling Operation
Illegal online gambling operations targeting Indonesia have increasingly shifted their operational footprint outside the country, relying on foreign infrastructure while maintaining deep financial and communication ties to Indonesian users. These operations often blend surface-web platforms, encrypted messaging services, and local banking channels to maintain scale while reducing direct exposure to Indonesian law enforcement.
This report examines one such operation, branded as SAPPORO88, through forensic artifacts recovered from StealthMole’s Compromised Data Set (CDS). Rather than relying on open-source reporting or takedown announcements, the investigation is grounded in direct host-level evidence collected from an infected machine actively used to manage the gambling service.
The analysis focuses on a single operator environment observed through infostealer telemetry, desktop screenshots, browser data, messaging sessions, and local files. These artifacts collectively document day-to-day operational activity, including platform administration, financial management, and customer support functions.
The objective of this report is to reconstruct how SAPPORO88 was operated, identify the infrastructure and workflows involved, and assess the level of attribution that can be made based on compromised host evidence, while clearly distinguishing confirmed findings from informed speculation.
Incident Trigger and Initial Investigation
The investigation was initiated through StealthMole’s CDS detection, which flagged an IP address associated with suspicious behavioral indicators commonly linked to online gambling operators. The detection criteria included repeated access to websites containing the keyword “casino”, concurrent execution of multiple Telegram instances, and active sessions with Indonesian web-based banking services.
The IP address identified was 1**.*1.1*4.***4, which StealthMole geolocation data estimates to be located in Cambodia, with attribution to CAMINTEL, National Telecommunication Provider, Phnom Penh. This IP served as the primary analysis target for the case.
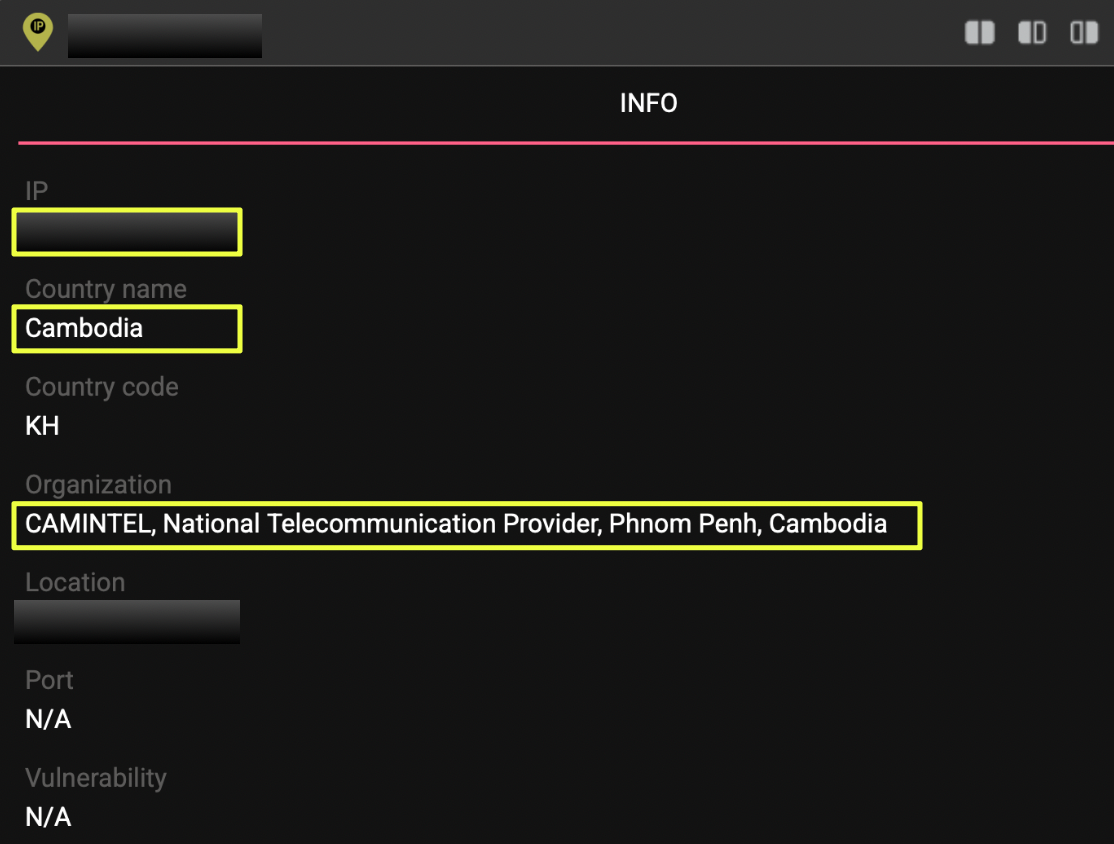
CDS data linked to this IP showed 604 results originated from infostealer malware, which captured system artifacts at the moment of compromise. These artifacts included browser sessions, screenshots, autofill data, messaging application sessions, and local files. Importantly, the captured screenshots provided direct visual confirmation of the user’s activities rather than inferred behavior.
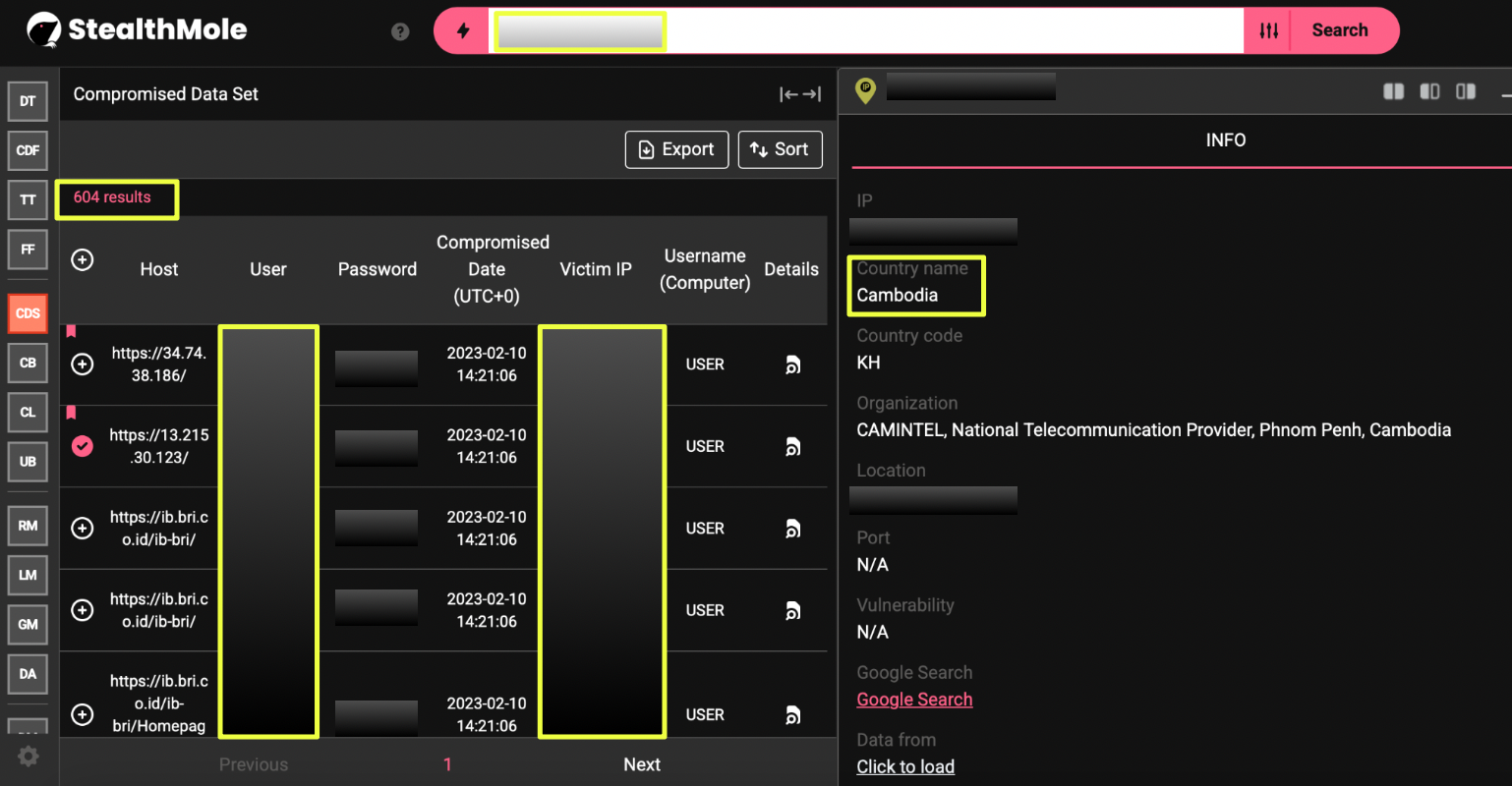
At the time of compromise, the machine was actively in use, allowing the investigation to pivot from abstract indicators to concrete operational evidence of an illegal gambling workflow.
Operator Environment and Platform Administration
Desktop screenshots captured by the infostealer revealed that the operator was using a dual-monitor workstation, suggesting a structured and sustained operational setup rather than casual or opportunistic activity.
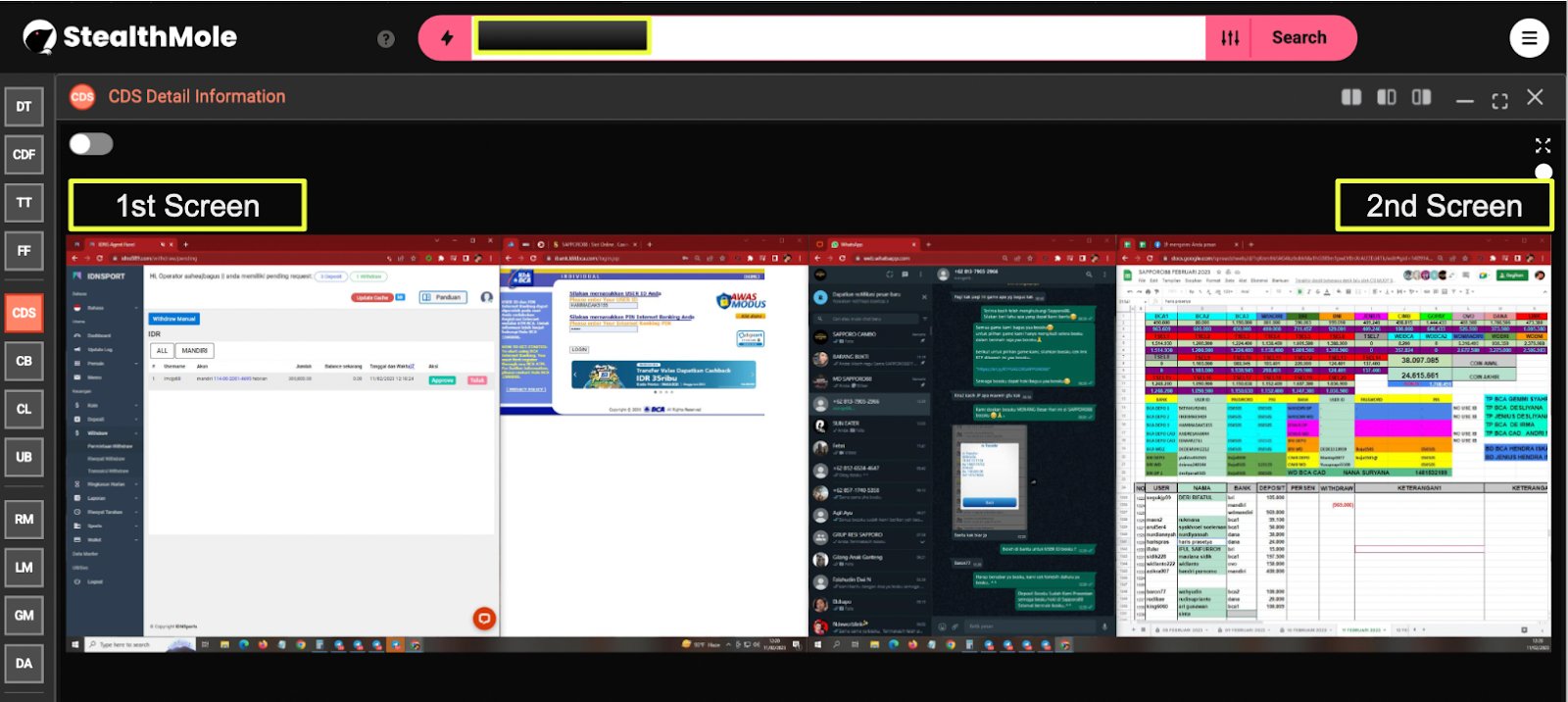
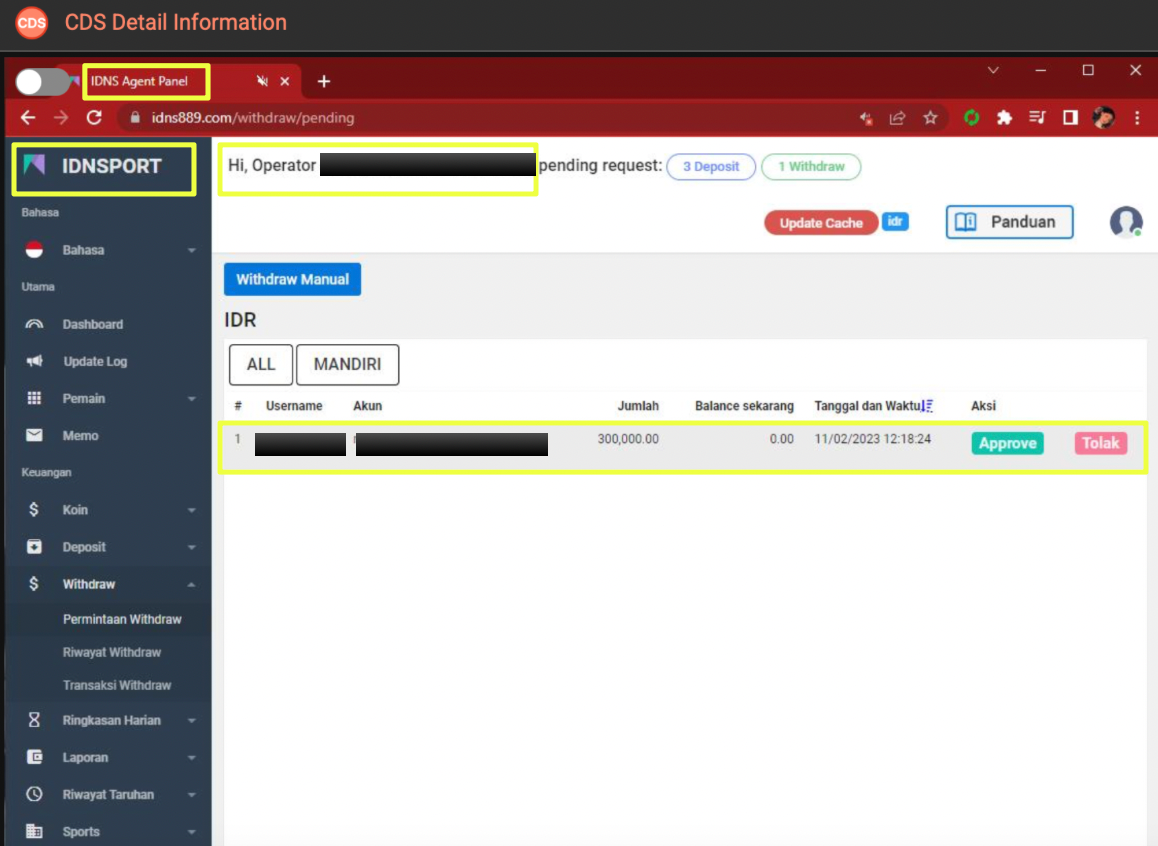
On the first screen, the operator was logged into idns889.com, identified in the presentation as a white-label service for IDN Poker. The interface displayed an “Operator” status banner, indicating administrative-level access. This confirms that the user was not a player or affiliate, but someone with direct control over platform configuration and management functions.
Simultaneously, multiple browser tabs were open referencing “SAPPORO88 : Slot Online, Casino”, reinforcing that SAPPORO88 was the brand being actively managed within this environment. The administrative session, combined with the visible branding, provides strong evidence that this machine was used to operate, not merely access, the gambling service.
This screen alone establishes a clear link between the compromised host and backend control of an illegal gambling platform targeting Indonesian users.
Financial and Banking Activity
The second monitor captured in the CDS screenshots showed active engagement with Indonesian online banking services, most notably KlikBCA. A login attempt was observed using the username “H**********5”, indicating direct interaction with Indonesian financial infrastructure.
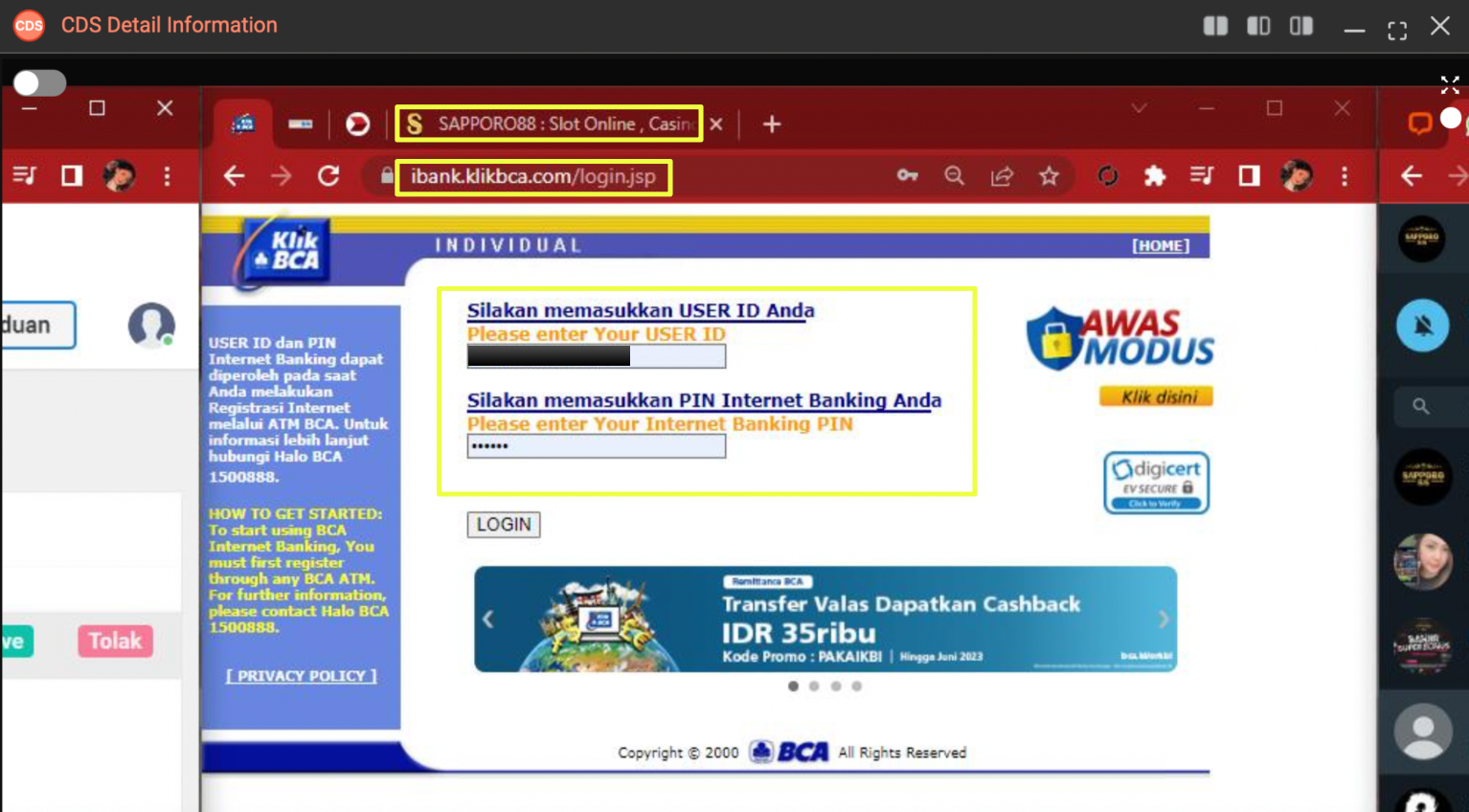
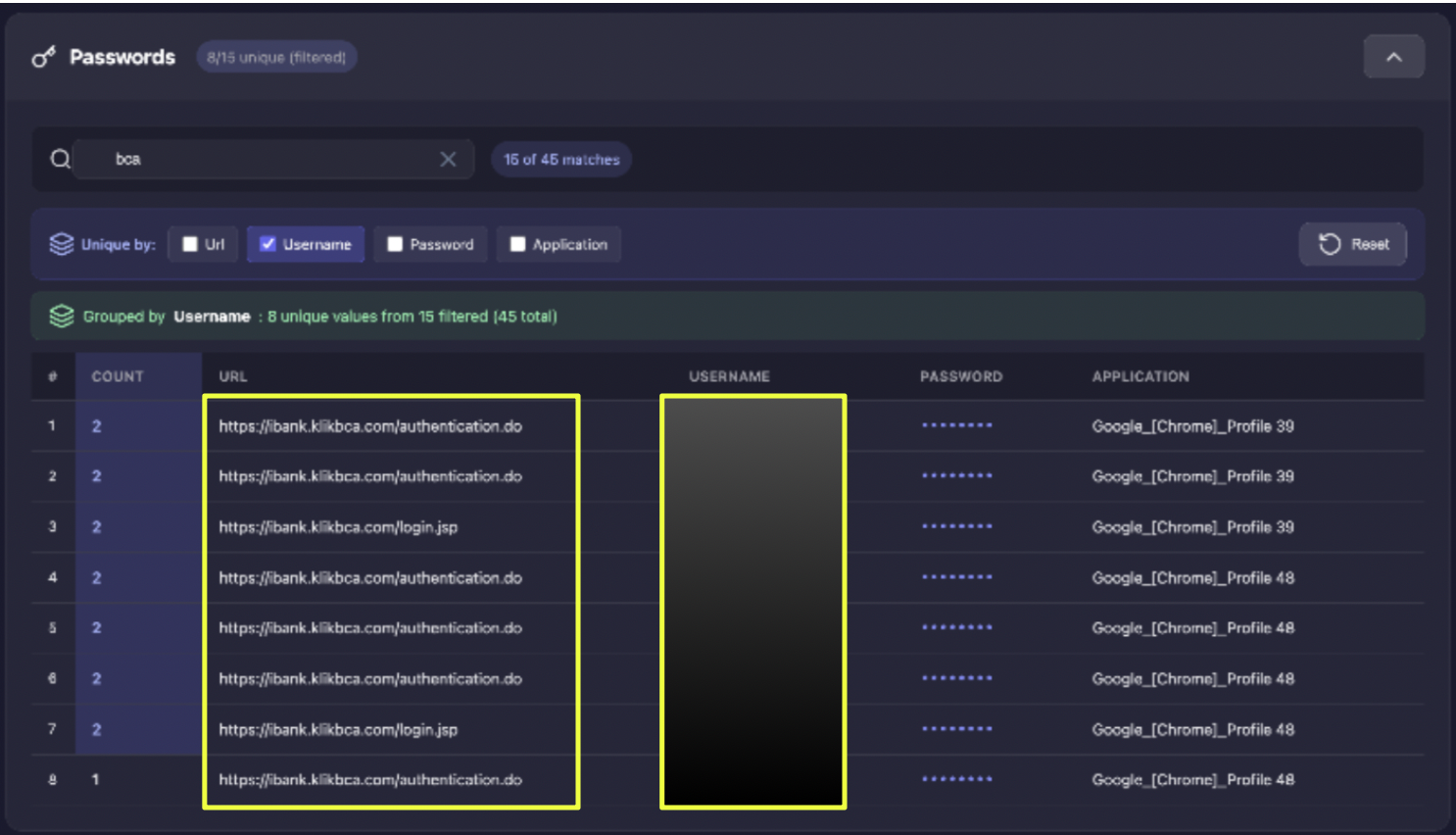
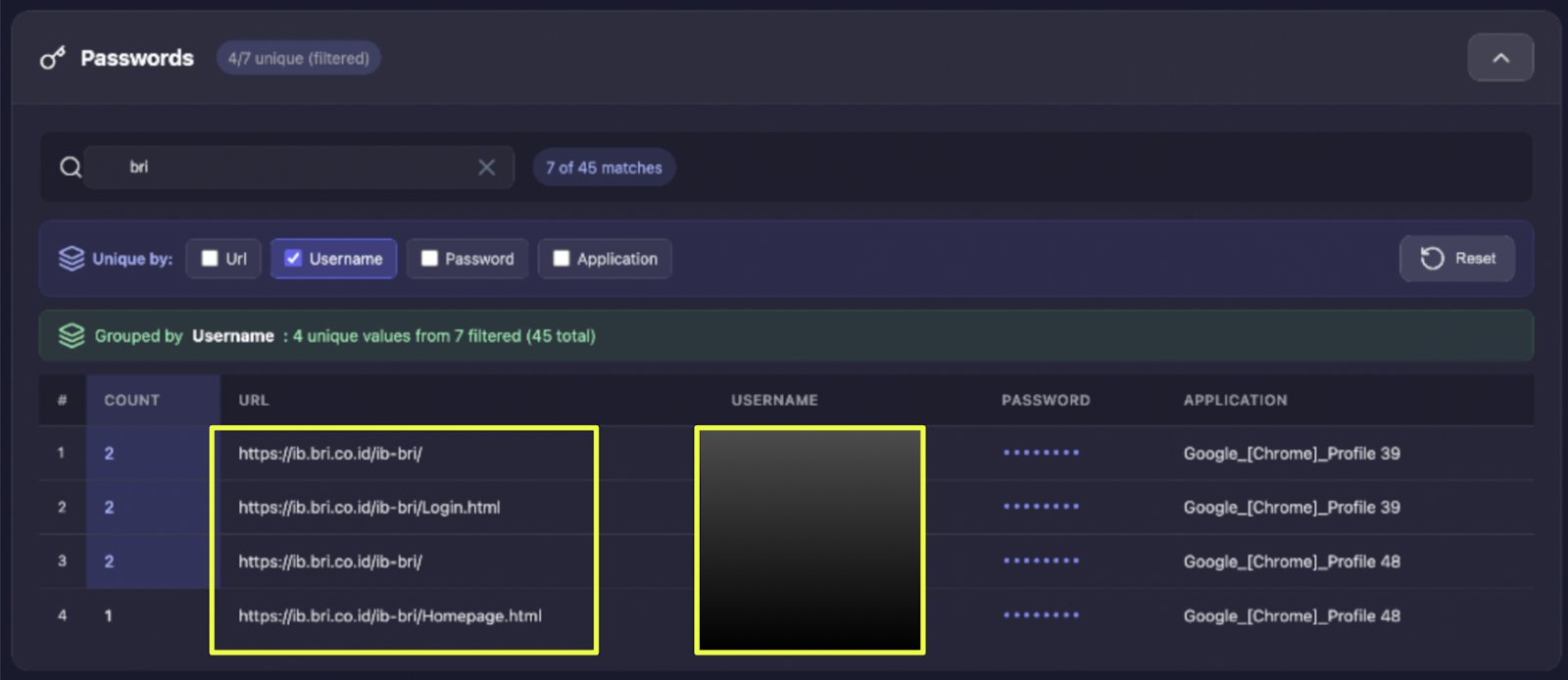
Further analysis of browser autofill data expanded this finding significantly. In total, credentials for 8 distinct KlikBCA accounts were recovered, along with 4 additional Bank BRI accounts. These accounts were not limited to a single session but were stored persistently in the browser, indicating repeated use over time.
In parallel, Excel files were visible on the desktop, including a ledger titled “SAPPORO88 FEBRUARI 2023”. This file functioned as a daily transaction log, tracking deposits and withdrawals. Critically, the spreadsheet stored user IDs, passwords, and PINs in plain text, exposing customer PII and suggesting minimal internal security controls.
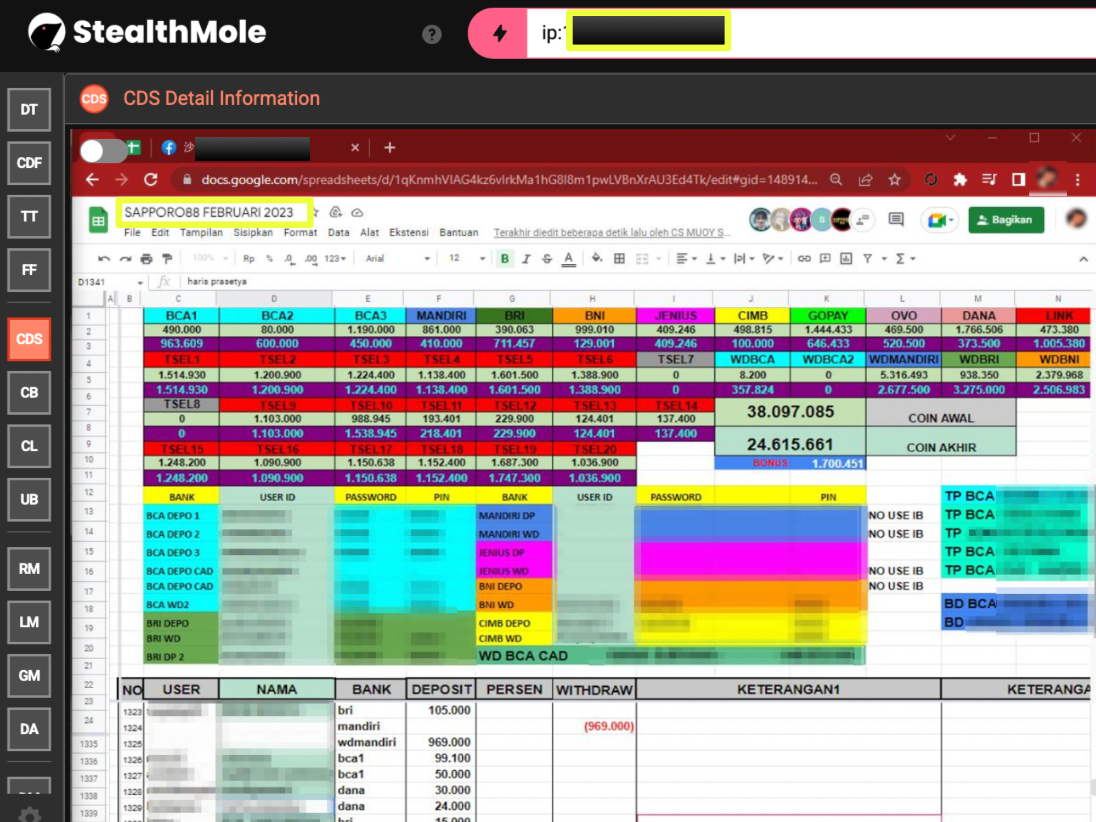
The banks referenced within the ledger included BCA, Mandiri, BNI, and BRI, all major Indonesian financial institutions. Taken together, these findings strongly suggest that the operator relied on multiple bank accounts, potentially mule or operational accounts, to manage cash flow for the gambling service.
Customer Support and Communication Channels
Beyond platform and financial management, CDS screenshots also captured the operator actively handling customer communications. WhatsApp Web was open on one of the screens, with visible chat logs involving Indonesian users. The presence of +62 country codes across contacts confirms that the primary customer base was located in Indonesia.
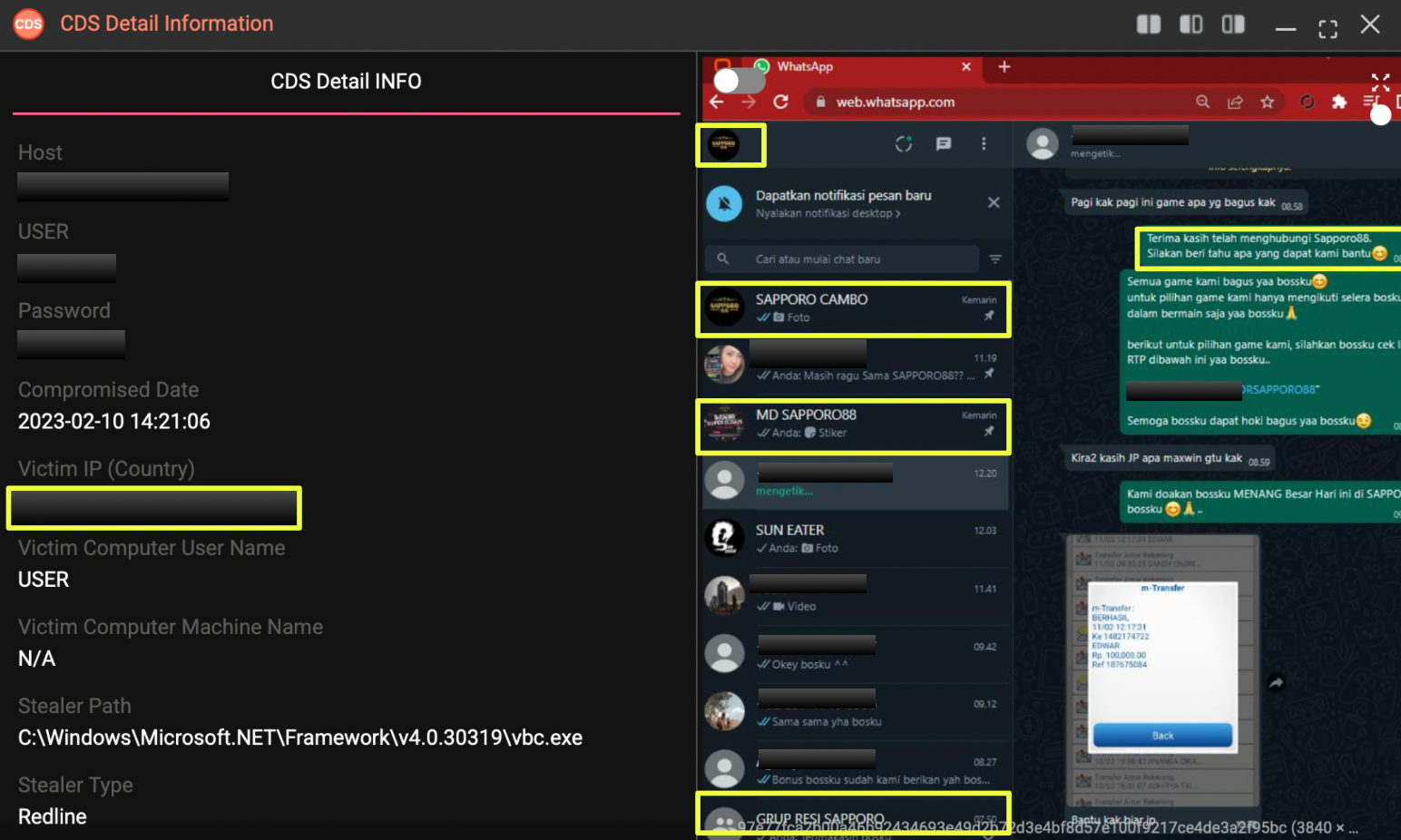
Several chat groups explicitly referenced “SAPPORO88”, and one group name, “SAPPORO CAMBO”, is particularly notable. This naming convention aligns with the Cambodia-based IP location and suggests internal acknowledgment of the operation’s geographic base.
The chats showed customers submitting proof of transfer and seeking assistance with deposits and withdrawals, demonstrating that the operator was directly involved in frontline support rather than delegating these tasks entirely.
Moreover, the taskbar revealed 4 active Telegram processes running simultaneously. CDS session data allowed further extraction and analysis of these Telegram accounts, providing a deeper view into the operator’s communication infrastructure.
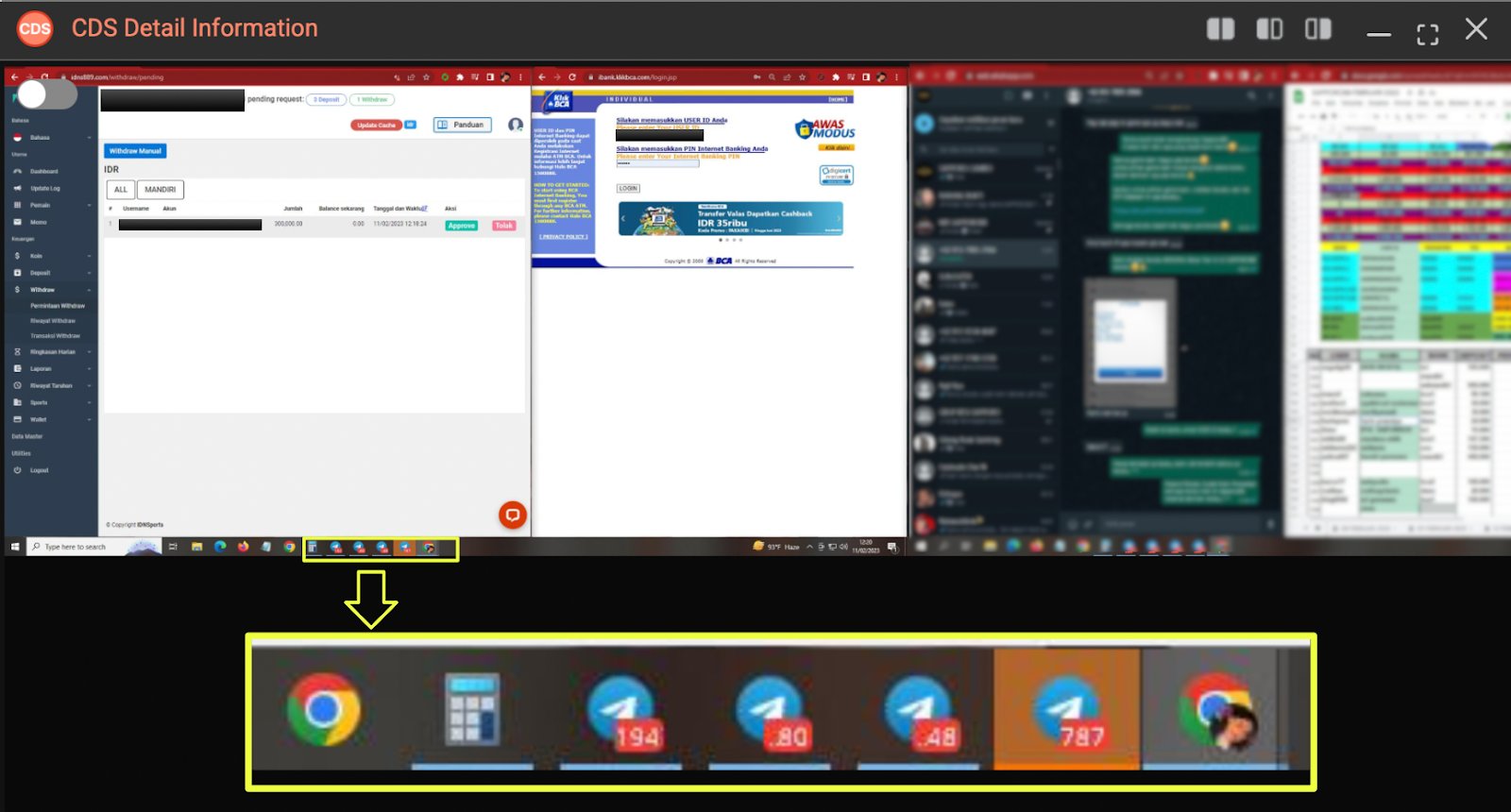
In addition to WhatsApp and Telegram, the compromised host also showed an active Facebook account session during operational activity. CDS screenshots captured the user logged into Facebook while simultaneously accessing internal financial records stored in a Google Sheets document titled “SAPPORO88 FEBRUARI 2023”.
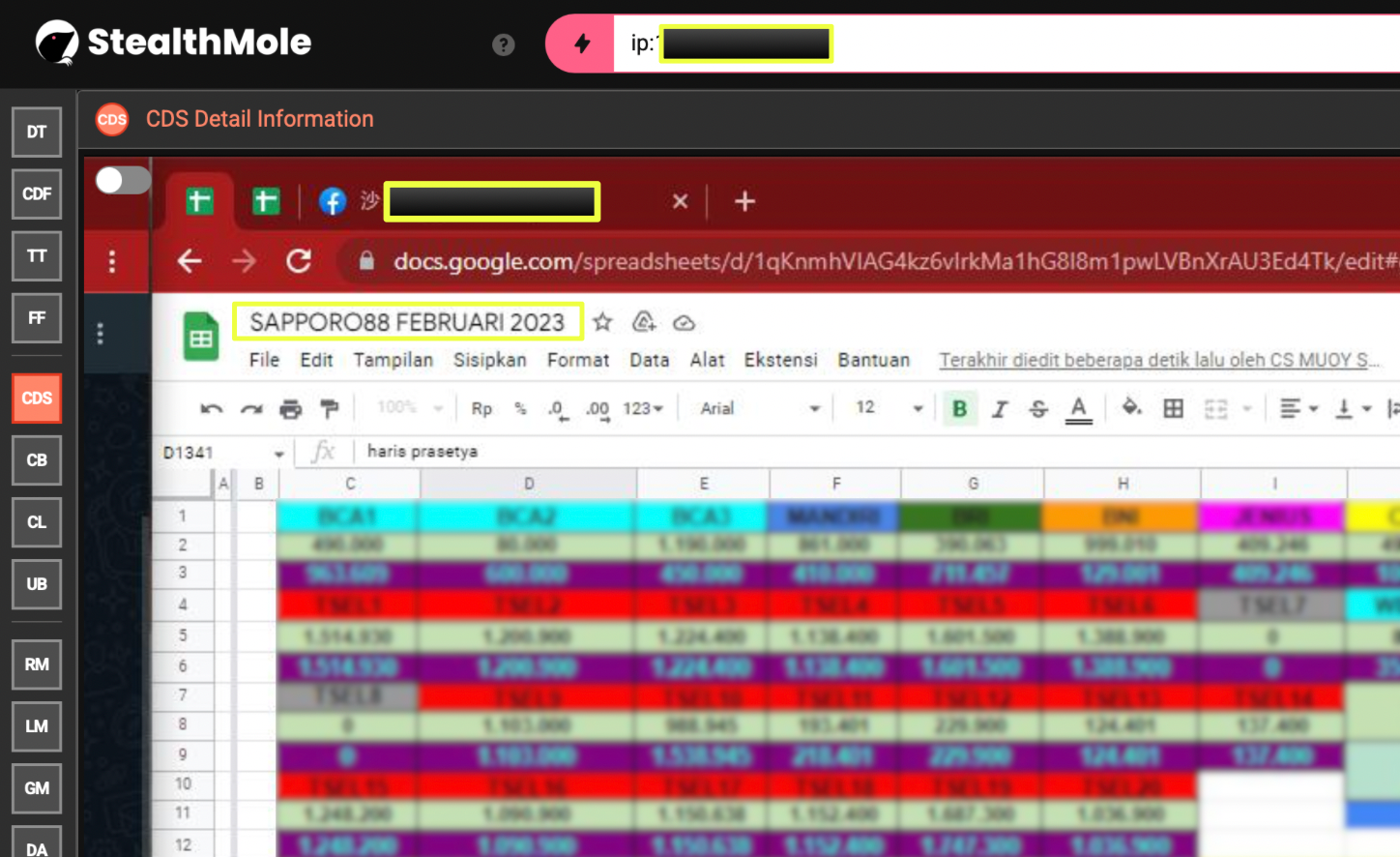
While the available data does not confirm how this Facebook account was used, its presence within the same operational workspace suggests it may have supported auxiliary communication, account management, or user interaction functions alongside other messaging platforms. No direct attribution or promotional activity was observed within the captured artifacts.
Telegram Account Forensics and Identity Correlation
Analysis of recovered Telegram session files identified 25 distinct Telegram accounts associated with the compromised machine. Through cross-referencing with other datasets, 24 of these accounts were successfully resolved to usernames.

Among the identified accounts was “SAPPORO 88”, which was confirmed to have been accessed from this same PC. This finding is significant because it directly ties the Telegram identity used to represent the gambling service to the physical operator environment observed in the screenshots.
The simultaneous use of multiple Telegram instances suggests deliberate segmentation of communication channels, likely used to manage customer inquiries, affiliates, payment coordination, or internal operations in parallel.
This Telegram linkage strengthens attribution by connecting branding, communication, and operational control to a single user environment rather than treating them as separate or loosely affiliated components.
User Files and Operational Scripts
The CDS collection also included local user files extracted from the machine. While many appeared related to Facebook account management, one file stood out: NOTE COUNTER JUSUF.txt, a 6.9 KB plain-text document.
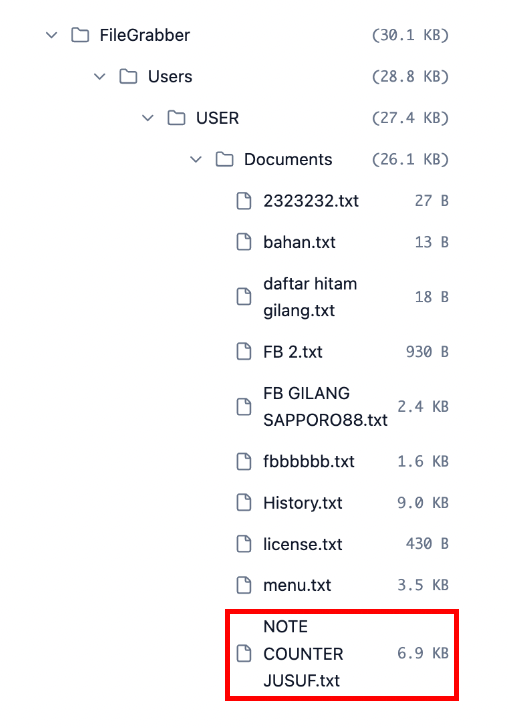
Manual analysis revealed that this file functioned as a customer support script library. It contained pre-written responses designed for copy-paste use when handling repetitive customer issues, such as deposit delays or withdrawal problems. The scripts included step-by-step guidance tailored specifically to Indonesian banking workflows involving Mandiri, BRI, and BCA.
Notably, the internal structure of the file revealed a sharp contrast between external politeness and internal sentiment. While customer-facing messages addressed users respectfully as “bosku”, internal section headers used explicit derogatory language to categorize complaint types. This provides behavioral insight into how the operator viewed customers while maintaining a polished external persona.
The file also listed betting value tables for major game providers such as PRAGMATIC and PG SOFT, indicating that the operator was deeply familiar with the technical and financial mechanics of the gambling platform.
Additional CDS Correlation: IP-Level User Artifacts
Further analysis of the same IP address (1**.*1.**4.**4) within StealthMole’s CDS revealed additional compromised data records. These records referenced a user with the computer username “PC”, along with email and password artifacts containing the string “bigcoin88”.
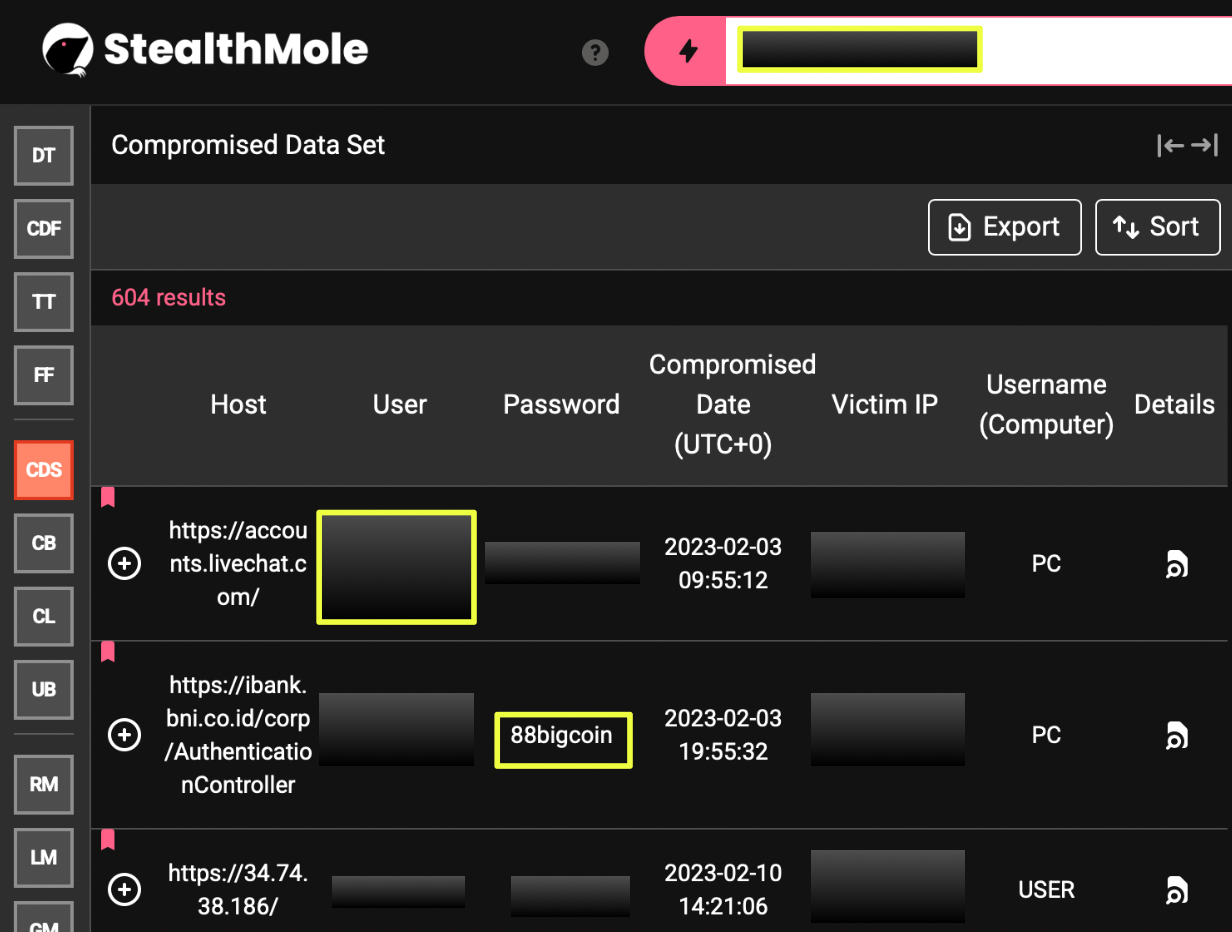
These artifacts appeared in association with logins to services such as accounts.livechat.com and ibank.bni.co.id, accessed from the same IP address. While no direct evidence confirms that this “bigcoin88” reference belongs to the SAPPORO88 operator, the naming similarity and shared IP environment warrant cautious consideration.
At this stage, this linkage remains speculative. The data suggests a potential overlap or reuse of identifiers within the same operational infrastructure, but it is not sufficient on its own to confirm identity consolidation.
Conclusion
StealthMole’s analysis confirms that the compromised host was actively used to operate the SAPPORO88 illegal online gambling service targeting Indonesian users. Evidence spans platform administration, financial account management, customer support communications, and internal operational documentation.
The operator demonstrated a structured workflow supported by a dual-monitor setup, multiple banking credentials, segmented messaging identities, and scripted customer interactions. The geographic footprint, inferred through IP data and internal naming conventions, places the operational base in Cambodia while maintaining strong financial and communication ties to Indonesia.
While additional CDS artifacts introduce speculative links, such as the “bigcoin88” identifier, core attribution to SAPPORO88 management is firmly supported by direct host-level evidence rather than circumstantial indicators.
This case illustrates how infostealer-derived data can expose the internal mechanics of illicit online services with a level of clarity rarely achievable through surface-level monitoring alone.
Editorial Note
Attribution in cyber and dark-web investigations is rarely absolute. Operators reuse infrastructure, identifiers, and environments in ways that blur clear boundaries between individuals and services. This report reflects those limitations by clearly separating confirmed evidence from informed speculation.
At the same time, it demonstrates how StealthMole’s CDS capabilities allow investigators to move beyond abstract signals and observe illicit operations as they function in real time, providing grounded, defensible intelligence in an inherently uncertain space.
Labels: Featured; Gambling

.svg)
.svg)
.svg)