Beyond Defacements: Expanding Digital Ecosystem of LulzSec Black
 |
The name LulzSec carries weight in cybersecurity circles. The original group, active in 2011, became infamous for high-profile breaches, media spectacle, and a brand of chaotic, attention-driven hacking. But more than a decade later, a new entity using a similar name has surfaced and despite the branding overlap, its motivations and operational behavior tell a very different story.
LulzSec Black is not a revival of the original collective. It does not operate in the same context, nor does it pursue the same type of targets. Instead, it presents itself as an ideologically aligned hacktivist group, blending cyber intrusions, defacements, and data leak claims with overt political messaging. Its branding heavily incorporates pro-Palestinian symbolism, religious references, and rhetoric positioning cyber activity as part of a broader resistance narrative.
At first glance, the group appears to be another defacement-focused actor riding geopolitical tensions for visibility. However, a deeper look reveals something more structured. Across dark web forums, Telegram channels, bot infrastructures, and even mainstream social media platforms, LulzSec Black has developed a multi-layered digital presence. Their activity extends beyond website defacements into data sales, tool distribution, cross-channel amplification, and coordinated messaging campaigns.
One recurring pattern stands out early in the investigation: a consistent focus on Indian entities, alongside messaging targeting Israel. Whether ideological alignment, opportunistic targeting, or both, this trend becomes increasingly difficult to ignore as their footprint expands across platforms.
This report maps that footprint, from dark forum postings and defacement archives to Telegram ecosystems and monetization attempts, to understand how LulzSec Black operates, communicates, and sustains its presence online.
Incident Trigger and Initial Investigation
The investigation began with a straightforward query inside StealthMole’s Dark Web Tracker using the keyword “LulzSec Black.” The initial search returned multiple indexed posts from DarkForums, immediately indicating that the actor was active on at least one established underground discussion platform.
One of the relevant findings was a July 2025 thread posted by the user “lulzsecblack” on:
- https://darkforums.**/Thread-Document-Hacked-Company-M*-F*S-INDIA
In this post, the actor claimed to have breached M** F****s India, describing the company as an engineering and medical systems manufacturer. The thread included two publicly accessible file-sharing links:
- https://gofile.io/d/d****f
- https://gofile.io/d/t****b
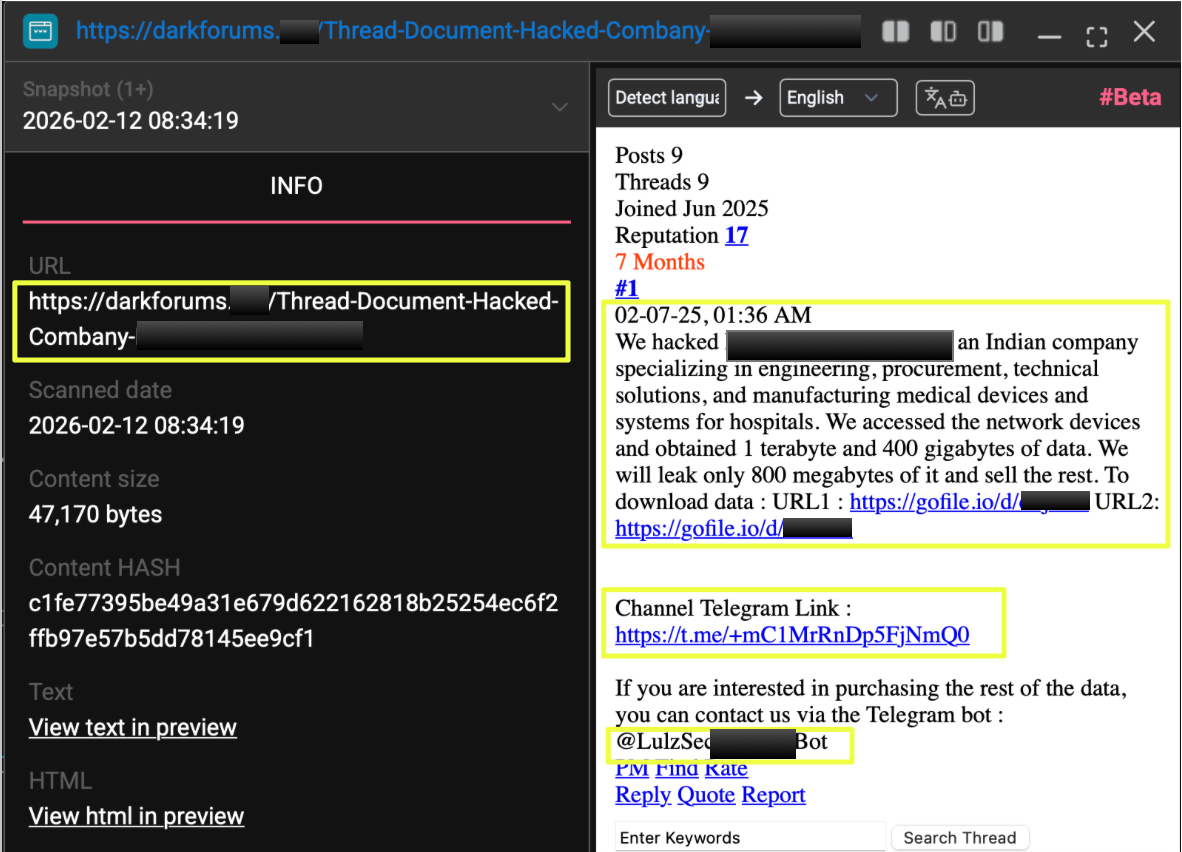 |
The post stated that approximately 1.4 TB of data had been exfiltrated, with a small portion released and the remainder offered for sale. The author also embedded a Telegram channel link:
- https://t.me/+mC1MrRnDp5FjNmQ0
And a contact bot:
- @LulzSec*****Bot
This combination of public leak samples, private sale channel, and automated bot contact indicated a structured monetization pathway rather than a purely ideological disclosure.
Further review of the same DarkForums user profile revealed an additional thread:
- https://darkforums.**/Thread-Document-Indian-Nuclear-Reactors-and-Chemicals-Company-hacked-C*******r
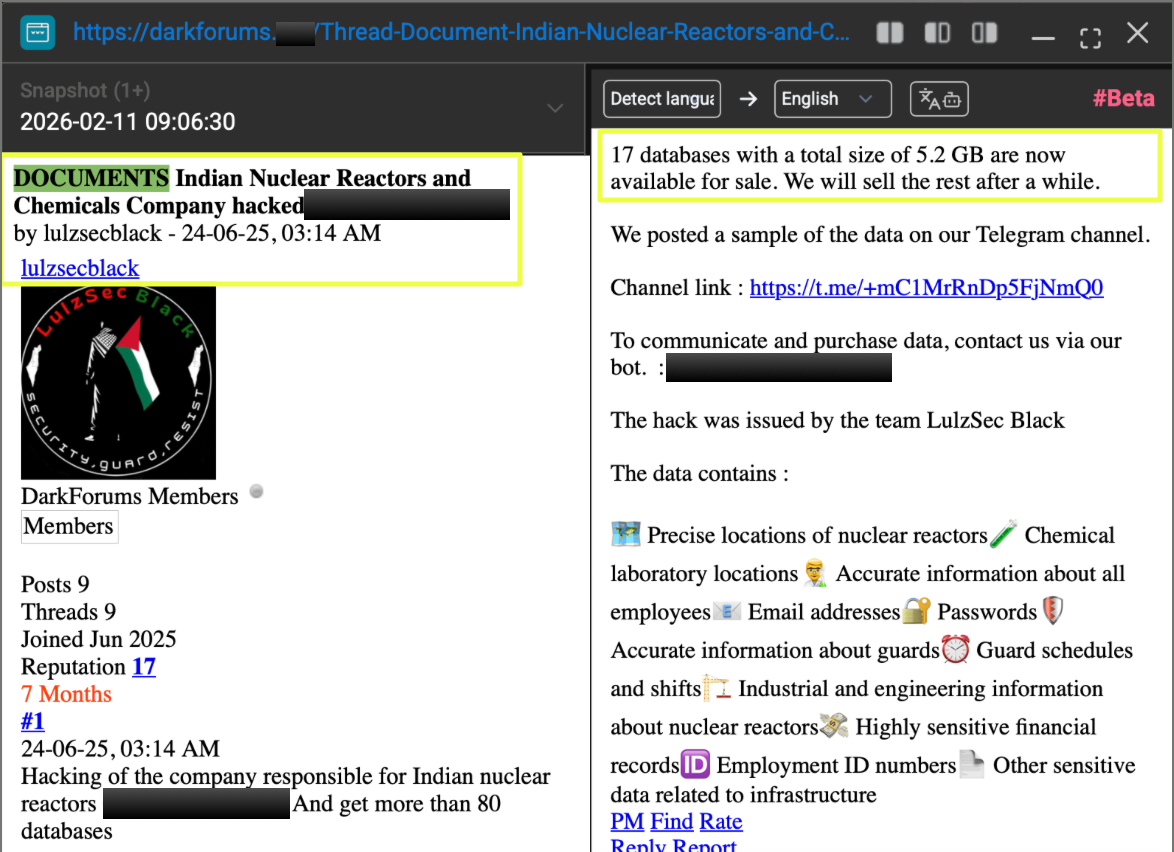 |
In this case, the group claimed to have accessed databases related to an Indian nuclear and chemicals entity. Unlike the MAP Filters incident, no direct download links were provided. Instead, access to the data required purchase via Telegram bot contact, suggesting tiered exposure tactics, partial public proof in some cases, controlled access in others.
During this stage of the investigation, a second DarkForums domain surfaced:
- https://darkforums.st/User-lulzsecblack
The presence of the same username across domains, consistent branding imagery, and identical Telegram contact details strengthened attribution confidence.
At this point, two patterns became clear:
- India appeared repeatedly as a target of claimed intrusions.
- Each forum claims redirected traffic toward Telegram infrastructure.
This redirection became the next logical pivot in the investigation.
Telegram Infrastructure and Ecosystem Expansion
With multiple DarkForums posts redirecting users to Telegram, the investigation shifted to StealthMole’s Telegram Tracker to examine the channel linked in the breach announcements:
- https://t.me/+mC1MrRnDp5FjNmQ0
Although the channel was no longer publicly accessible at the time of investigation, StealthMole’s historical indexing capability enabled a reconstruction of its activity. Archived records showed multilingual messaging in Arabic, English, and Hebrew, along with repeated references to operations targeting Israel and India. The channel also circulated content from other militant-aligned Telegram channels, reinforcing its ideological positioning.
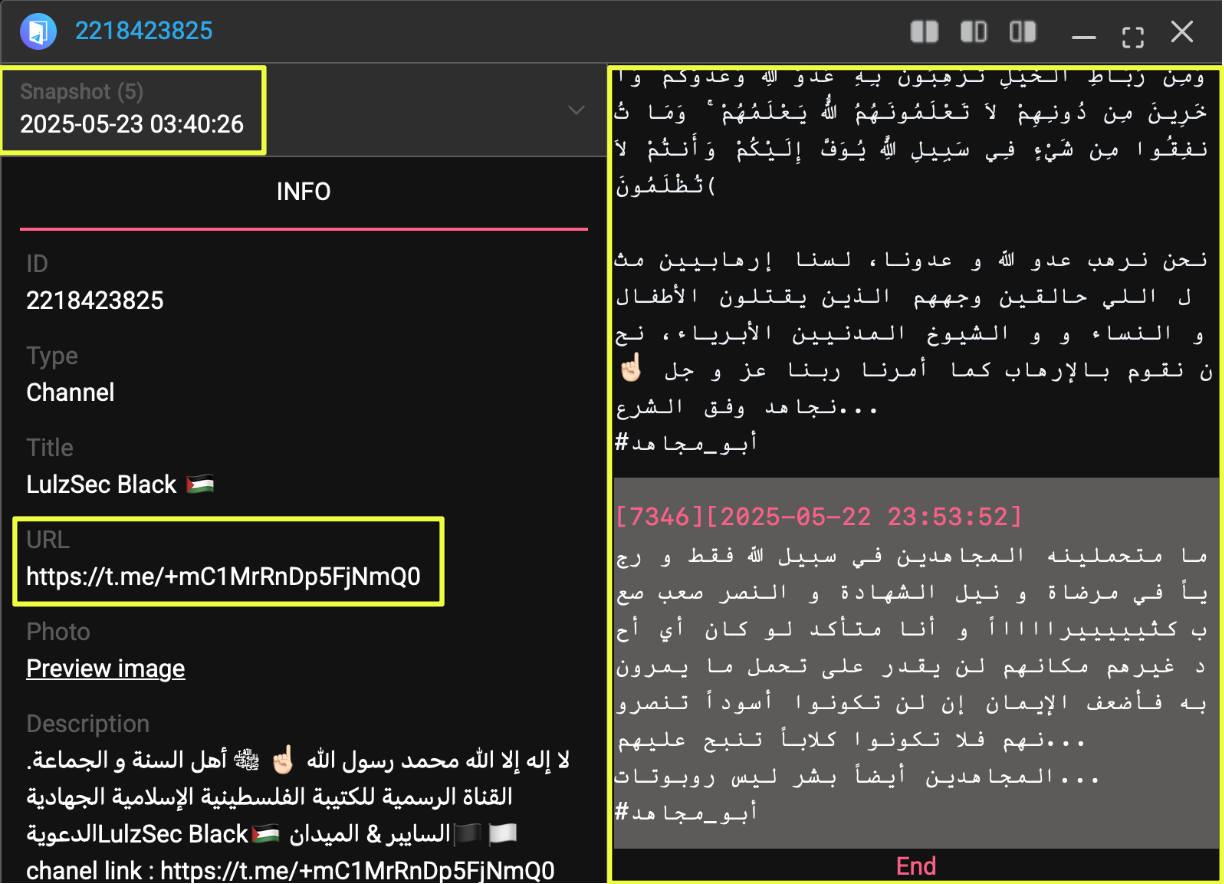 |
The last indexed message in this channel dated back to May 2025, suggesting either voluntary shutdown, administrative action, or migration to alternative infrastructure.
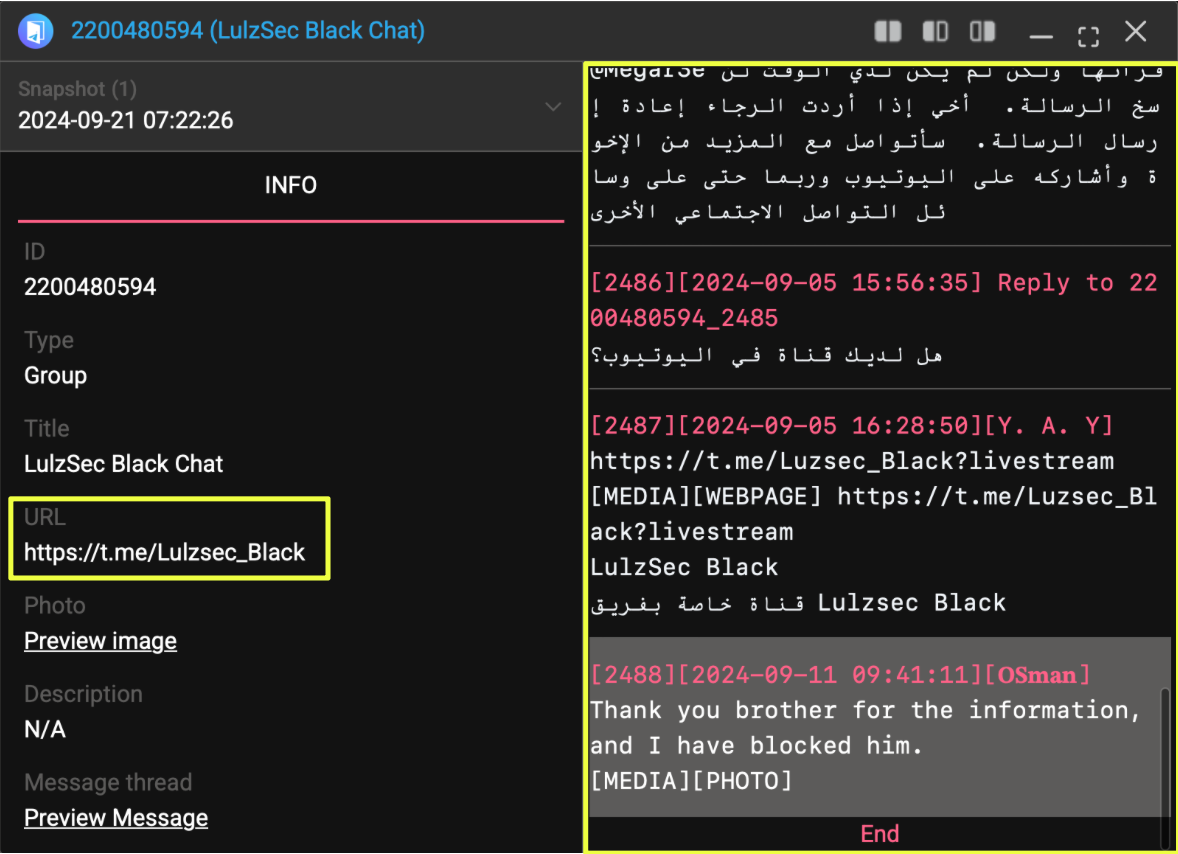
Further pivoting from this channel revealed additional Telegram nodes associated with the same branding:
- https://t.me/Luzsec_Black (chat channel)
- https://t.me/LulzSec_Black_Tools (tools distribution channel)
- @LulzSec*******Bot
- @lulzsecblack2_bot
- @ab*******d_co_bot
 |
The tools channel contained an Arabic-language announcement stating that, in response to requests from followers, the group had created and would distribute a dedicated DDoS attack tool through a specialized channel. This marked a notable shift from messaging and breach claims toward operational enablement.
The chat channel introduced another layer: community interaction. It included livestream references and forwarded operational updates, indicating attempts to build a participatory audience rather than maintain a one-way broadcast structure.
During Telegram pivoting, additional invite links surfaced, including:
- https://t.me/+5tOXpaGX8o8xNDc8
- https://t.me/+Z4TymJU-X4pkYTZk
- https://t.me/+ghJlzrgSBXs0OWFk
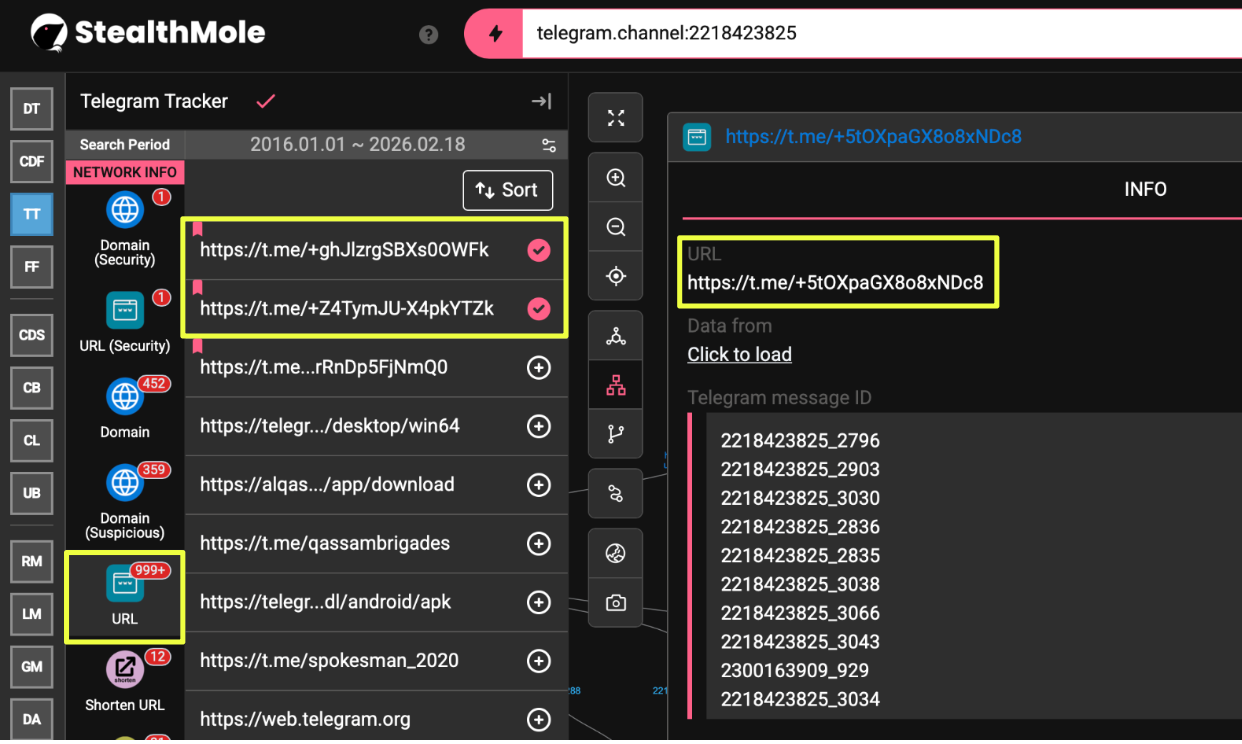 |
Several of these links had expired, but their repeated appearance across defacement archives and related Telegram channels suggested a pattern of infrastructure rotation, a common resilience tactic among hacktivist groups operating under platform enforcement pressure.
Parallel investigation identified an active Instagram account:
- https://www.instagram.com/lulz******k
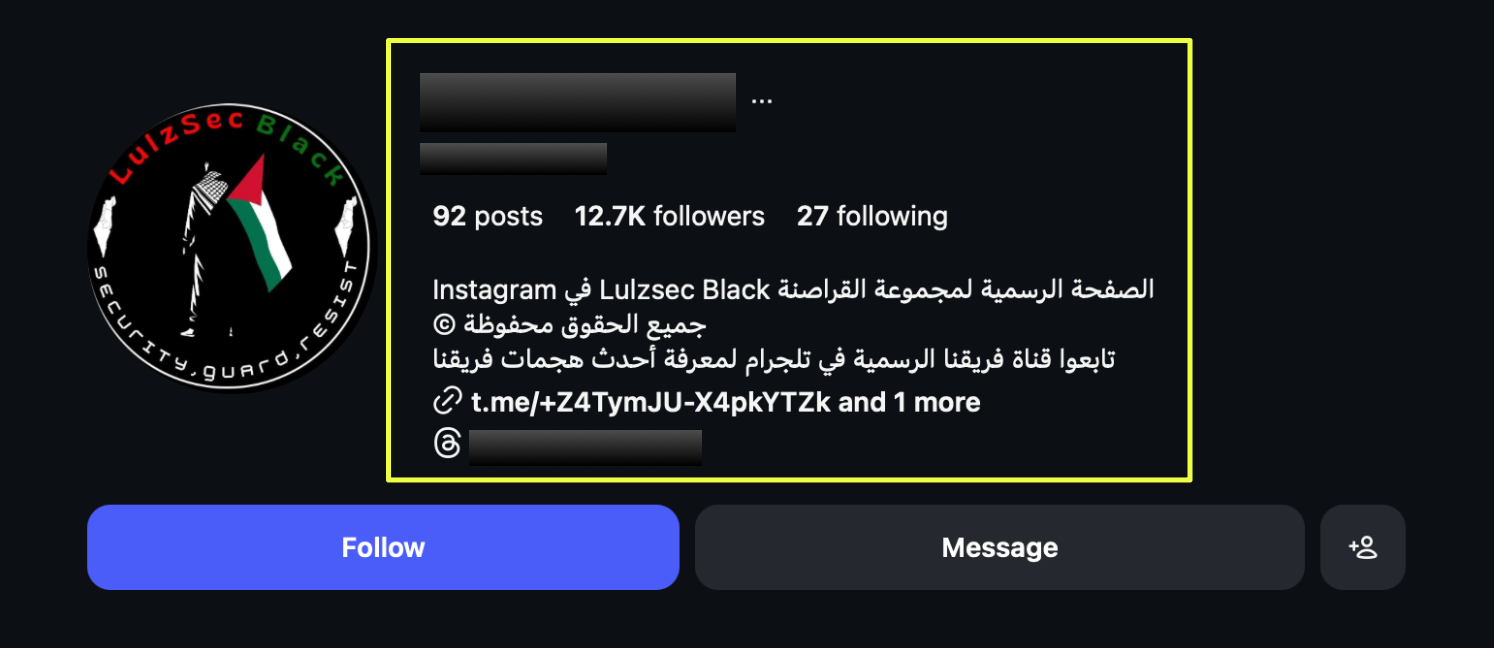 |
With approximately 12.7K followers, the account directed traffic toward Telegram channels, indicating a deliberate funnel from mainstream social media into encrypted communication environments.
- https://t.me/Lu********k
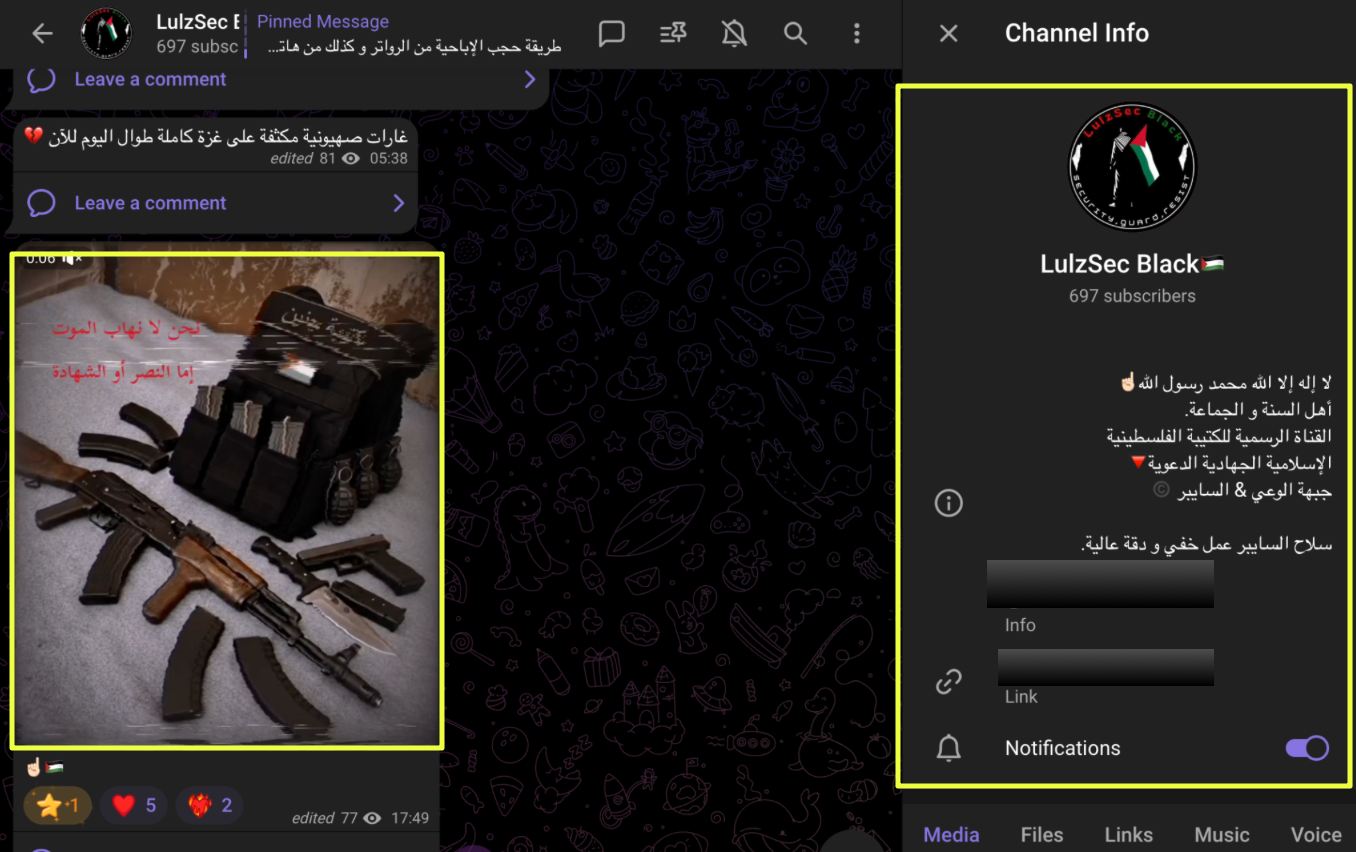 |
Taken together, the Telegram and social media mapping revealed that LulzSec Black’s operations were not confined to isolated breach announcements. Instead, they maintained a layered digital ecosystem consisting of broadcast channels, chat groups, bot-driven contact points, tool distribution hubs, and public-facing recruitment pathways.
At this stage of the investigation, the group’s structure appeared increasingly deliberate rather than sporadic.
Defacement Campaigns and Ideological Framing
While forum posts and Telegram channels revealed the group’s communication structure, defacement archives provided direct evidence of operational activity.
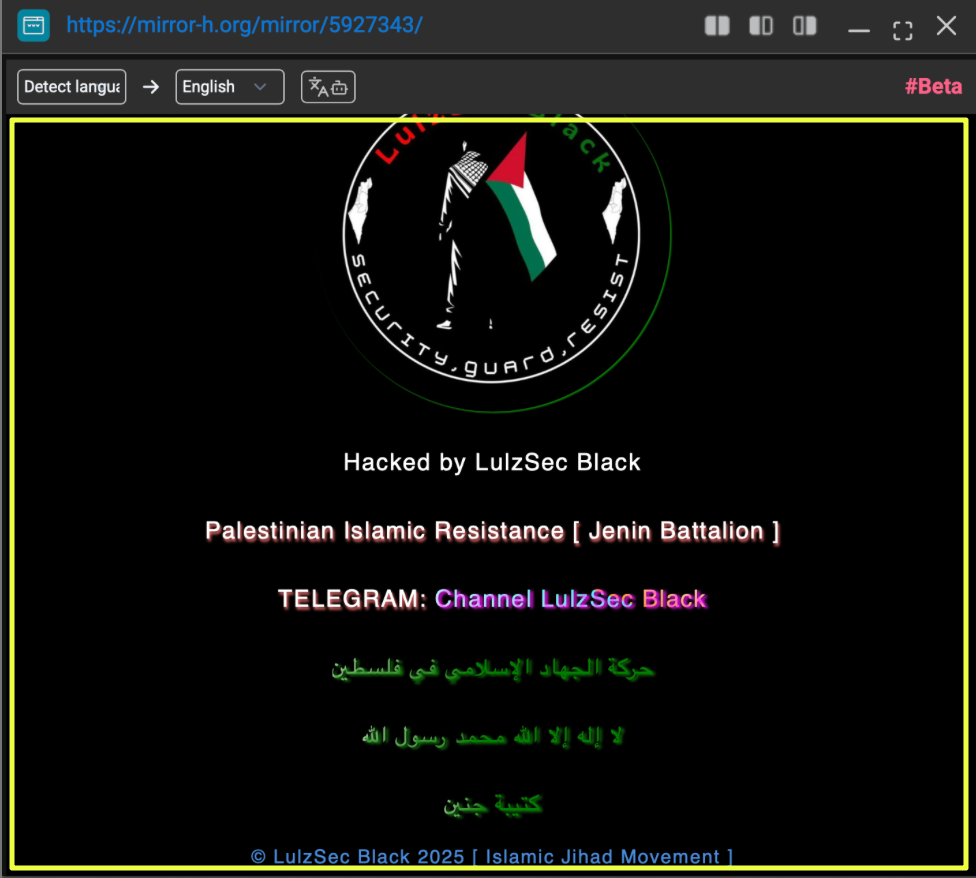
A review of entries on Mirror-H showed a defacement page attributed to “LulzSec Black.” The defaced page prominently displayed the group’s logo alongside pro-Palestinian imagery and explicit references to “Palestinian Islamic Resistance [ Jenin Battalion ].” The page also embedded Telegram links, reinforcing the pattern observed earlier, each operational act redirected attention back to their communication channels.
- https://mirror-h.org/mirror/5927343/
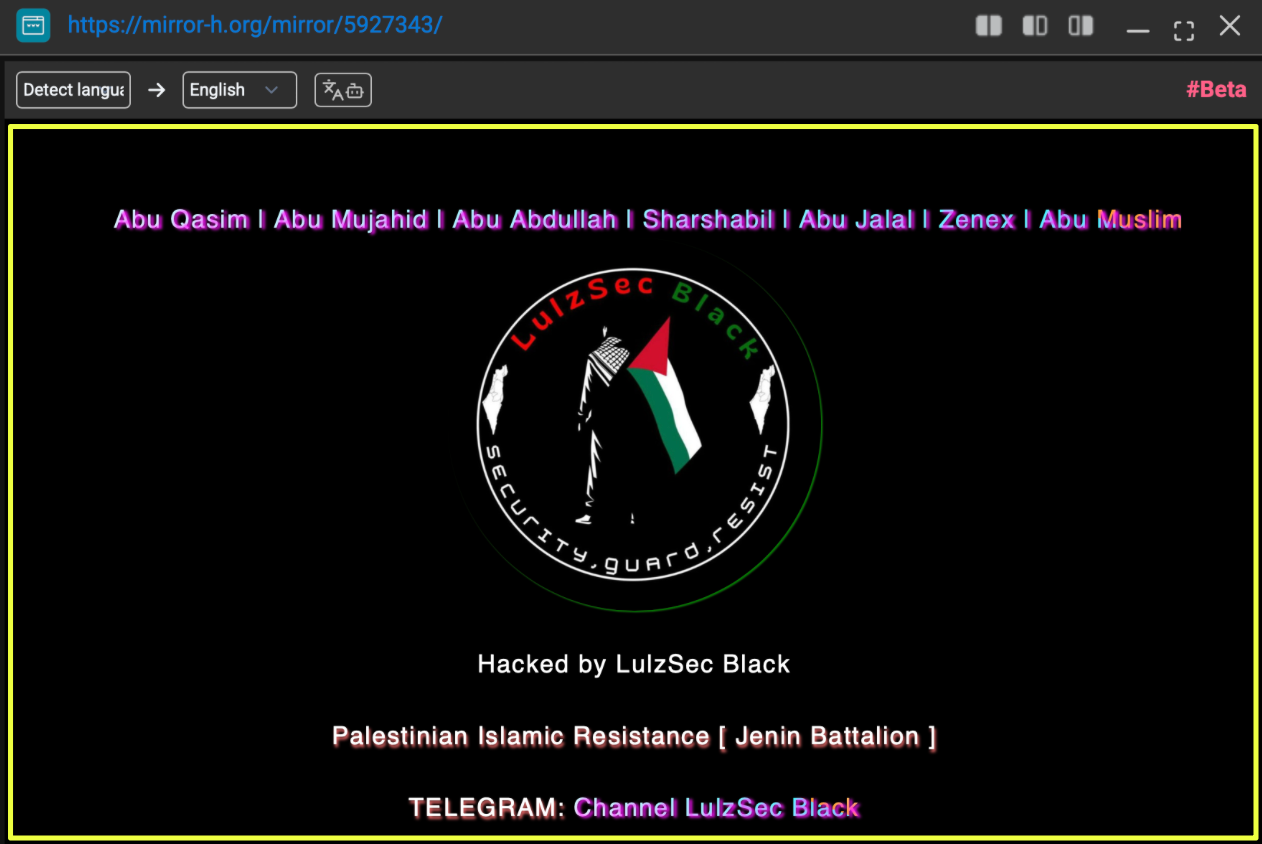 |
The messaging within the defacement was not neutral or generic. It incorporated religious declarations, resistance-oriented slogans, and references to militant-aligned narratives. The branding was consistent with what appeared across Telegram and DarkForums: identical logo styling, repeated bot contact references, and the same ideological framing.
This consistency is important. Many defacement actors rely on disposable branding or opportunistic messaging. In contrast, LulzSec Black demonstrated uniform visual identity and repeated narrative themes across platforms. The defacement was not an isolated technical act, it functioned as amplification.
Notably, Telegram invite links embedded in defacement pages were later observed being circulated across related Telegram channels. Although several of these links have since expired, their cross-appearance suggests centralized coordination rather than spontaneous or unaffiliated use of the group’s name.
- https://t.me/+5tOXpaGX8o8xNDc8
 |
The defacement activity also aligned with previously observed targeting patterns. Several claims and references pointed toward Indian entities, while broader messaging consistently positioned Israel as a rhetorical adversary. Whether all claimed breaches are independently verifiable remains outside the scope of this section; however, the messaging pattern itself is consistent and deliberate.
At this stage, LulzSec Black appears to use defacement as a signaling mechanism, a way to project ideological alignment, recruit attention, and funnel traffic into controlled communication spaces. It is less about the single compromised website and more about the narrative ecosystem built around it.
Monetization Strategy and the Hybrid Hacktivism Model
Although LulzSec Black presents itself as an ideologically driven cyber collective, activity on DarkForums introduces a parallel dimension: monetization.
The July 2025 post claiming a breach of M** F*****s India included publicly accessible sample data alongside two GoFile download links. The remaining data, reportedly totaling over a terabyte, was offered for sale via Telegram contact. In a separate DarkForums thread concerning an alleged breach of an Indian nuclear and chemicals entity, no public sample was provided at all, instead, interested parties were directed to purchase access directly through the Telegram bot.
This distinction is telling.
In one case, partial exposure appears designed to establish credibility. In the other, exclusivity appears designed to maximize sale value. Both methods follow a structured sales logic rather than a purely ideological disclosure model.
The repeated inclusion of Telegram bots, particularly @LulzSec*****Bot, reinforces this assessment. Bots reduce friction in communication, automate inquiries, and enable scalable interaction. The presence of a secondary bot (@lulzsecblack2_bot) suggests redundancy or operational continuity planning.
The tools channel further complicates the picture. The announcement of a custom-built DDoS tool for followers signals another potential revenue or influence pathway. Even if tools are distributed freely, they function as capability amplification, expanding operational reach through community participation.
Taken together, these elements suggest a hybrid operational identity:
- Ideological messaging and militant-aligned rhetoric
- Defacement activity for visibility and signaling
- Data breach claims targeting strategic entities
- Structured data sales via forum and bot infrastructure
- Tool distribution to followers
This model blends hacktivist narrative with financially motivated behavior. It does not fit neatly into a single category. The group appears to leverage geopolitical rhetoric while simultaneously operating within established cybercrime market dynamics.
The consistency of this pattern across multiple platforms indicates deliberate structuring rather than opportunistic posting. LulzSec Black does not simply claim attacks; it builds funnels: from defacement to Telegram, from forum posts to bots, from propaganda to monetization.
This hybrid positioning may explain the group’s sustained activity across 2024–2025 and its ability to maintain visibility even as individual channels are suspended or expire.
Conclusion
LulzSec Black presents itself under a familiar name, but its operational behavior reflects a distinctly modern structure. Unlike the original 2011 LulzSec collective, which thrived on spectacle and short-lived disruption, this iteration demonstrates sustained cross-platform coordination and layered digital presence.
The investigation traced a consistent pattern: DarkForums breach claims redirecting to Telegram channels; defacement pages embedding the same contact infrastructure; bot-driven communication pathways; tool distribution channels; and an active Instagram account funneling public audiences into encrypted spaces. Across these platforms, India repeatedly appeared in breach claims, while Israel featured prominently in ideological messaging. Whether opportunistic or strategically aligned, the targeting pattern is difficult to ignore.
More importantly, LulzSec Black does not operate as a purely ideological propaganda outlet nor as a conventional financially motivated breach actor. Instead, it blends both models. Defacements function as visibility signals. Forum posts serve as credibility markers. Telegram bots facilitate transactions. Tool distribution encourages participation. The ecosystem is interconnected.
What emerges is not a loose collection of online claims, but a structured digital footprint: one that evolves across domains, migrates when links expire, and maintains consistent branding throughout. Beyond defacements, the group has built a networked presence designed to sustain attention, coordinate messaging, and monetize access.
Editorial Note
Attribution in cyber investigations is rarely absolute. Online identities can fragment, migrate, or be imitated, and infrastructure often shifts in response to platform enforcement. This case demonstrates how systematic tracking, across dark web forums, defacement archives, Telegram ecosystems, and social media funnels, helps reduce uncertainty by focusing on repeated identifiers, behavioral consistency, and cross-platform linkage. The findings presented here reflect the observable digital footprint of LulzSec Black at the time of investigation, recognizing that cyber actors and narratives continue to evolve.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com
Labels: Featured, Hacktivist Group
.svg)
.svg)
.svg)