HeLL Forum: A Decade of Hidden Infrastructure
HeLL Forum has long occupied a unique corner of the dark web: a place where hackers, carders, and exploit vendors converged under one persistent brand. Though repeatedly declared defunct, its name continues to resurface through shifting onion links, new contact aliases, and recycled templates that mirror its early versions.
The forum’s promise has always been the same: privacy, exclusivity, and profit. Yet its ability to repeatedly reappear, often months after vanishing, hints at something more structured than a simple clone network.
This investigation traces the most recent resurfacing of HeLL, beginning with a single domain indexed on a dark web repository and expanding into a pattern of connected mirrors, re-emerging operators, and payment infrastructures that span several years. What starts as a single .onion link evolves into a web of persistence: one that refuses to fade, no matter how many times it burns.
Background
First emerging in the early 2010s, HeLL Forum quickly built a reputation as one of the most exclusive dark web communities dedicated to hacking, fraud, and exploit trading. Operating primarily as an invite-only space, it attracted cybercriminals seeking vetted markets for zero-day vulnerabilities, malware, and stolen credentials.
At its height, HeLL distinguished itself through strict vetting systems and escrow services that were rare among dark web forums of its era. The platform’s administrator, known by the handle Ping, became synonymous with its brand, maintaining a controlled membership and a reputation for reliability within the underground ecosystem.
In mid-2015, HeLL reportedly shut down after Ping’s disappearance, prompting various clones and impersonators to surface. Over the following years, however, the brand itself refused to fade. Its design templates, slogans (#1 Hacking Forum, No Scams, No Bullshit), and encrypted membership models began reappearing across newer onion domains, each claiming to be the true successor.
These resurfacing instances suggested not just nostalgia or opportunistic imitation but a continuity of infrastructure and identity, pointing to either a persistent operator network or deliberate reactivation by its former members.
It’s against this long, fractured history that StealthMole’s investigation into the modern HeLL infrastructure (2022–2025) begins, revealing how one of the dark web’s oldest brands continues to evolve under new guises.
Incident Trigger and Initial Investigation
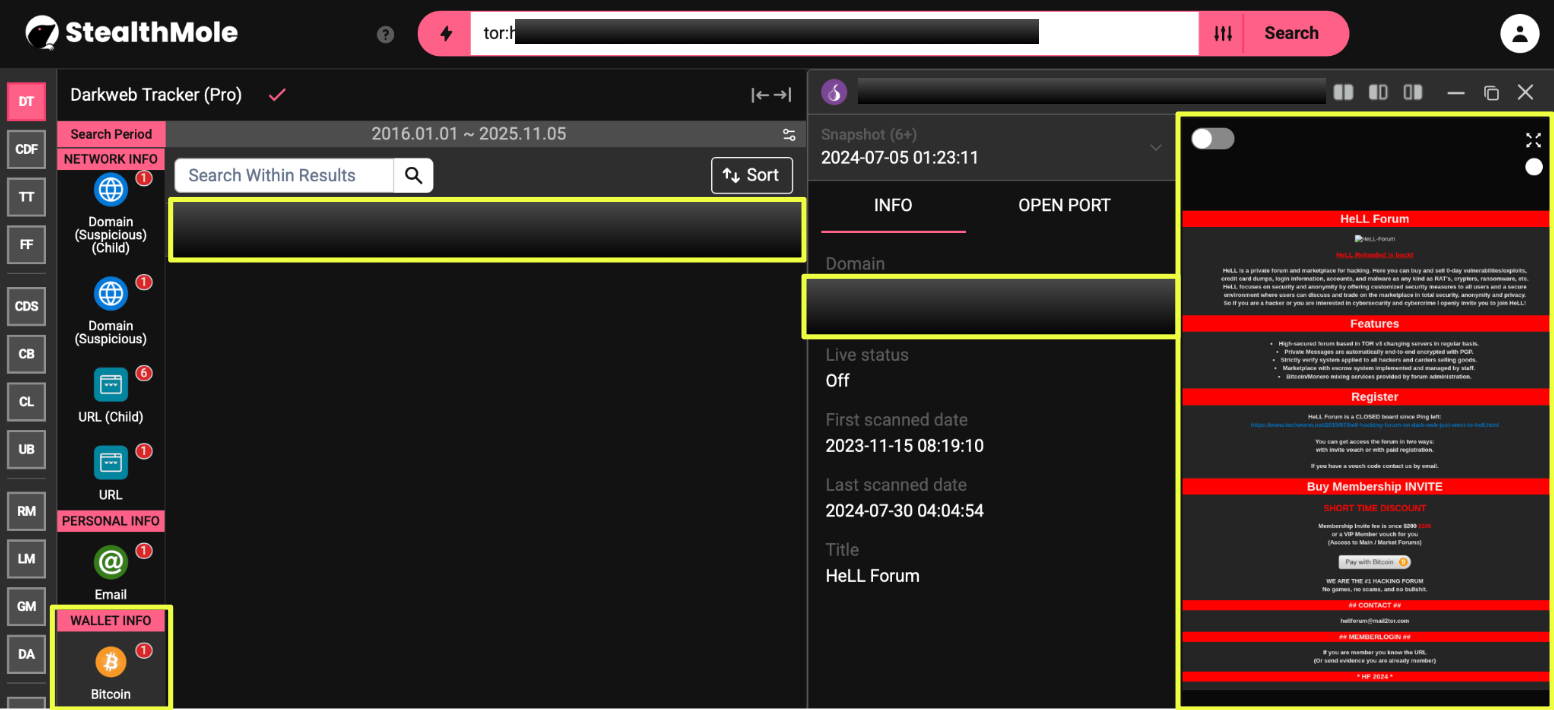
The investigation began with the discovery of an onion domain indexed in a dark web repository monitored through StealthMole’s Darkweb Tracker.
- hell***********************************************qd.onion
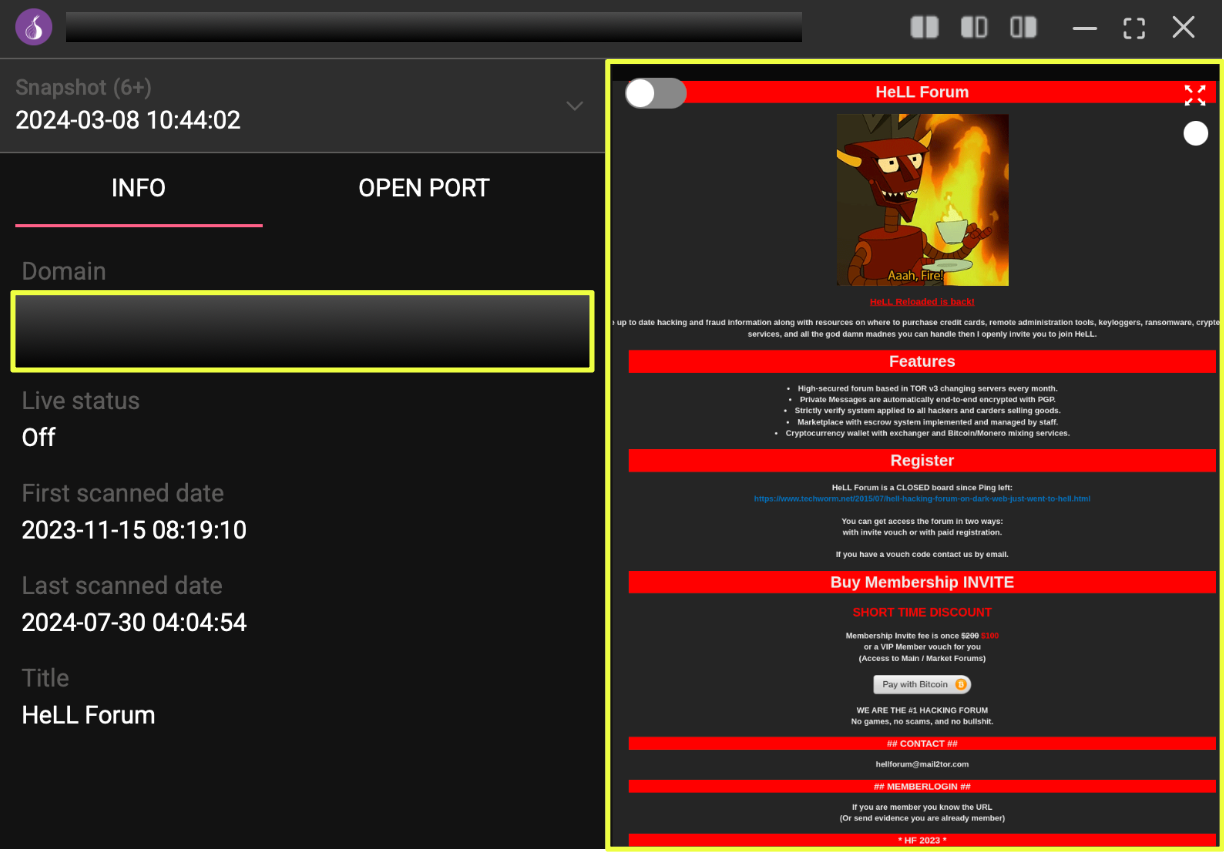
At first glance, the domain appeared dormant. But archival captures revealed that it had remained active from at least November 2023 until July 2024, carrying familiar branding and structural patterns tied to previous HeLL iterations.
The homepage explicitly referenced the forum’s closed status:
“Since Ping left, HeLL Forum is now a closed board.”
This phrasing, directly invoking the forum’s original administrator, was the first clear indicator that this wasn’t a random impersonator. The site also listed a Tor-based contact, hel*******@mail2tor.com, aligning with communication patterns used by earlier verified versions of HeLL Forum.
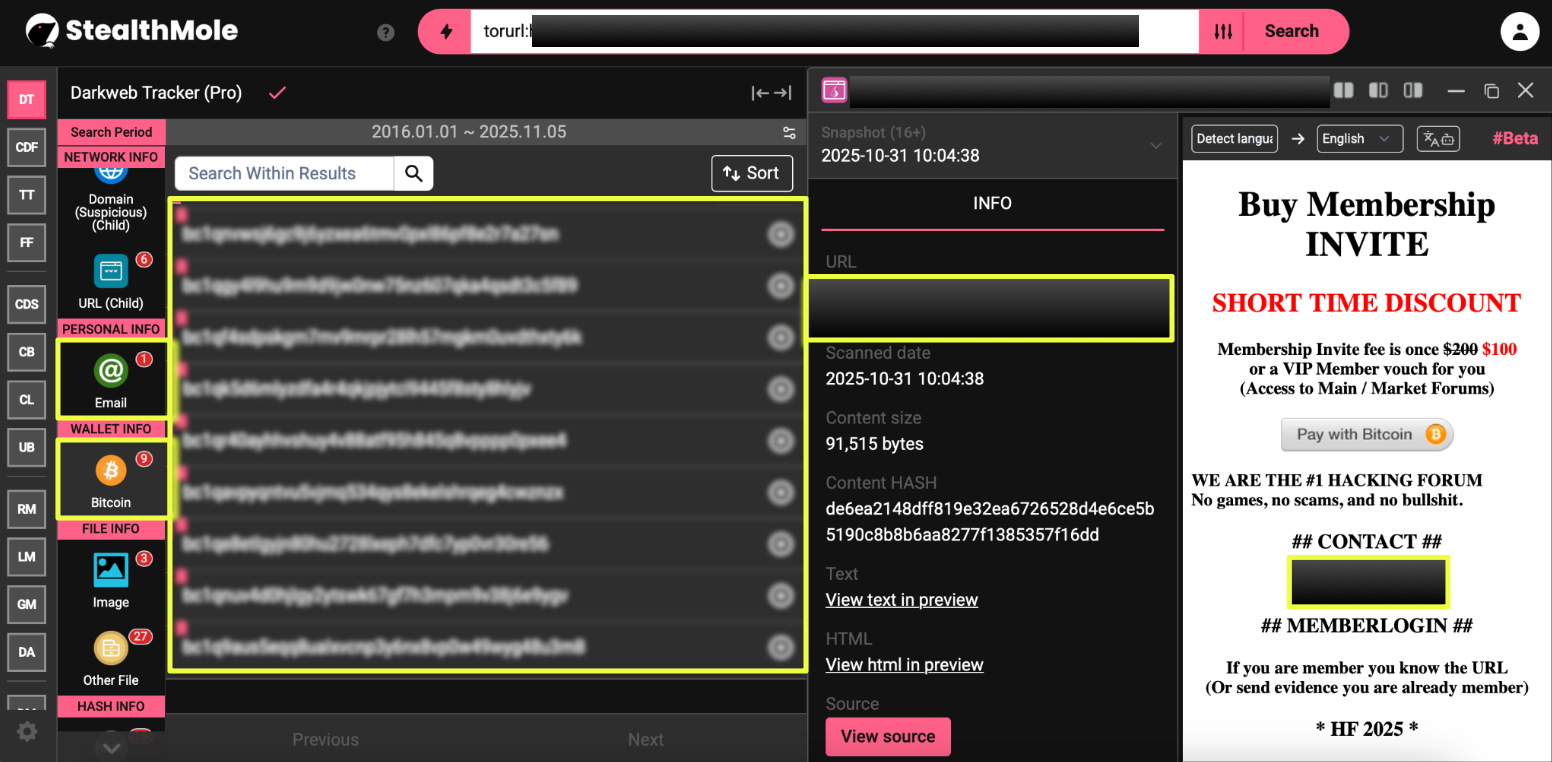
Further analysis through StealthMole surfaced a Bitcoin address embedded within the domain’s page structure. While the address was not linked to any other active marketplaces or wallets, its presence marked the reintroduction of HeLL’s classic paid membership model.
- bc1*******************************0
At this stage, the finding was treated as a potential isolated revival. However, extended crawling within StealthMole’s darkweb tracker began revealing a pattern of recurring HeLL-related domains emerging throughout 2025, many sharing identical page structures, replicated language, and variations of the same contact aliases.
This discovery marked the turning point of the case: HeLL wasn’t reappearing as a single forum, but as an entire ecosystem of mirrored infrastructures, all maintaining continuity in communication and design. From this point, the investigation shifted toward mapping each instance and identifying their shared operators and wallets to uncover how the network persisted for over the last three years.
Infrastructure Evolution (2022–2025)
StealthMole’s dark web tracking revealed that HeLL Forum did not operate as a single re-emergent site but as a network of evolving mirrors, each preserving the forum’s branding, structure, and operational patterns.
From 2022 through 2025, at least 14 distinct onion domains were observed, showing continuity through shared contact addresses, similar payment flows, and recycled interface templates.
1. http://hell2********************************************qd.onion/
Active: 15 April 2022 – 18 September 2025
Emails: he****@e*****t.im, hel******@el****e.in, hel******@mail2tor.com, he****@mail2tor.com
Notes: The earliest confirmed HeLL mirror in this phase. Its long lifespan and four distinct contact channels mark it as a backbone node for later re-deployments.
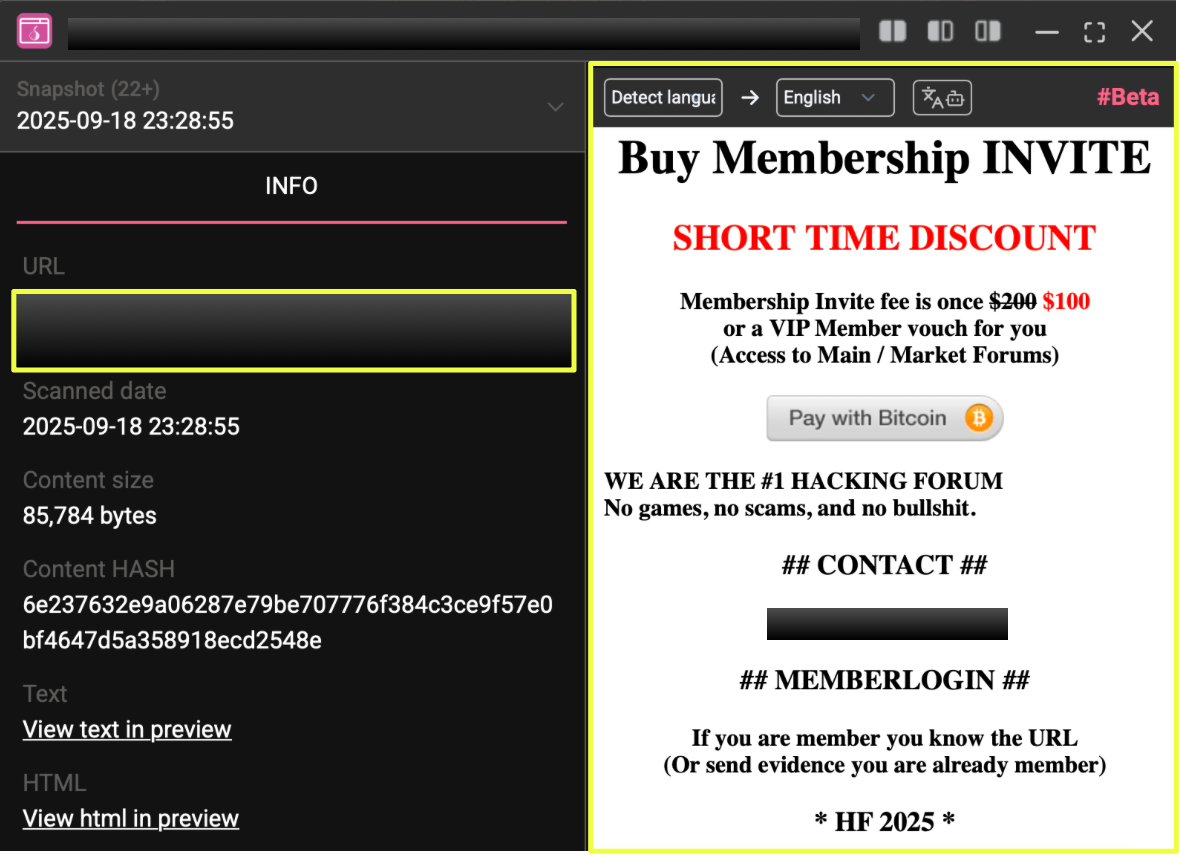
2. http://hel*************************************************qd.onion/
Active: November 2023 – July 2024
Email: hel*******@mail2tor.com
BTC: bc1*********************************0
Notes: Discovered via StealthMole’s dark web repository. Displayed the message “Since Ping left, HeLL Forum is now a private board.” Confirmed transition toward invite-only membership and BTC-based payments.
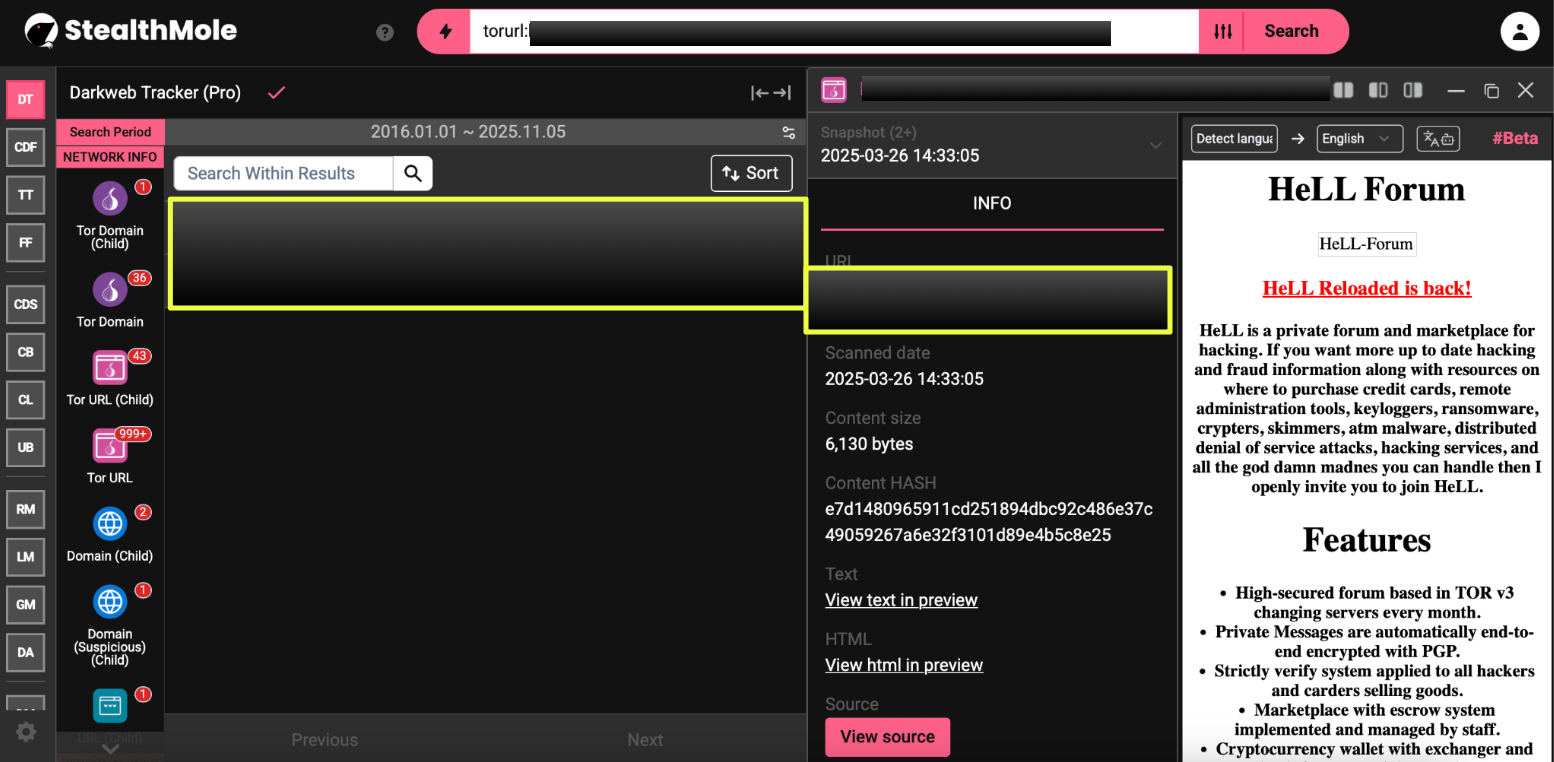
3. http://jtx********************************************ad.onion/
Active: 16 March 2025
Emails: jt******@ma****tor.com, Gl**********b@proton.me
Notes: First 2025 variant, introducing a dual-channel contact model, internal Tor mailbox plus ProtonMail for external communication.
4. http://lxa********************************************id.onion/
Active: 27 March 2025
Emails: he****@mail2tor.com, lx******@mailxtor.com
Notes: Continuation of the mail2tor + mailxtor pairing. Likely a secondary mirror to maintain accessibility during downtime.
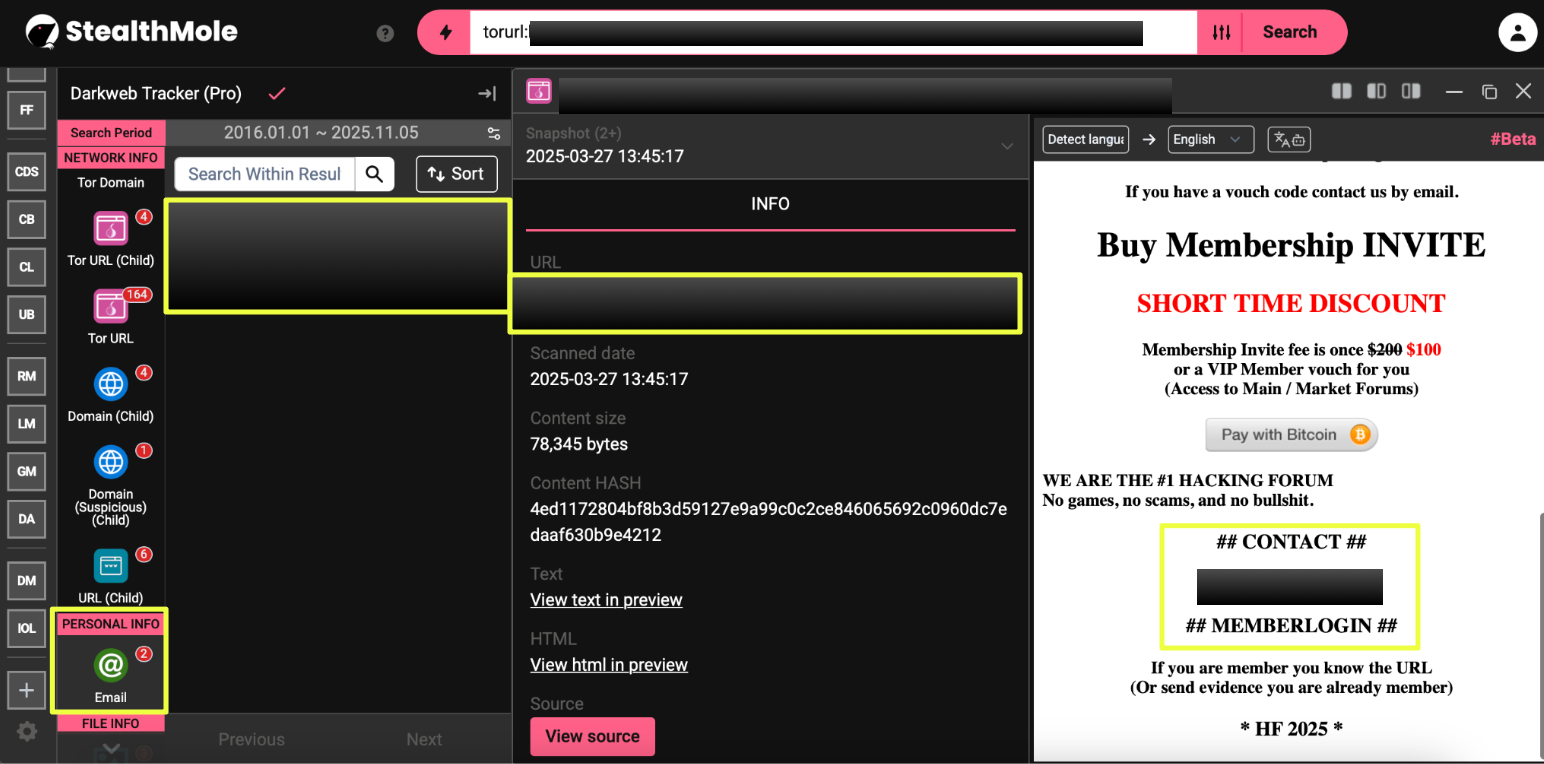
5. http://tmi*********************************************6yd.onion/
Active: 27 March 2025
Emails: A****@mail2tor.com, he****@mail2tor.com, tm****@mailxtor.com
Notes: Marks the first instance of multiple administrative aliases appearing simultaneously, suggesting a small operator group rather than a single administrator.
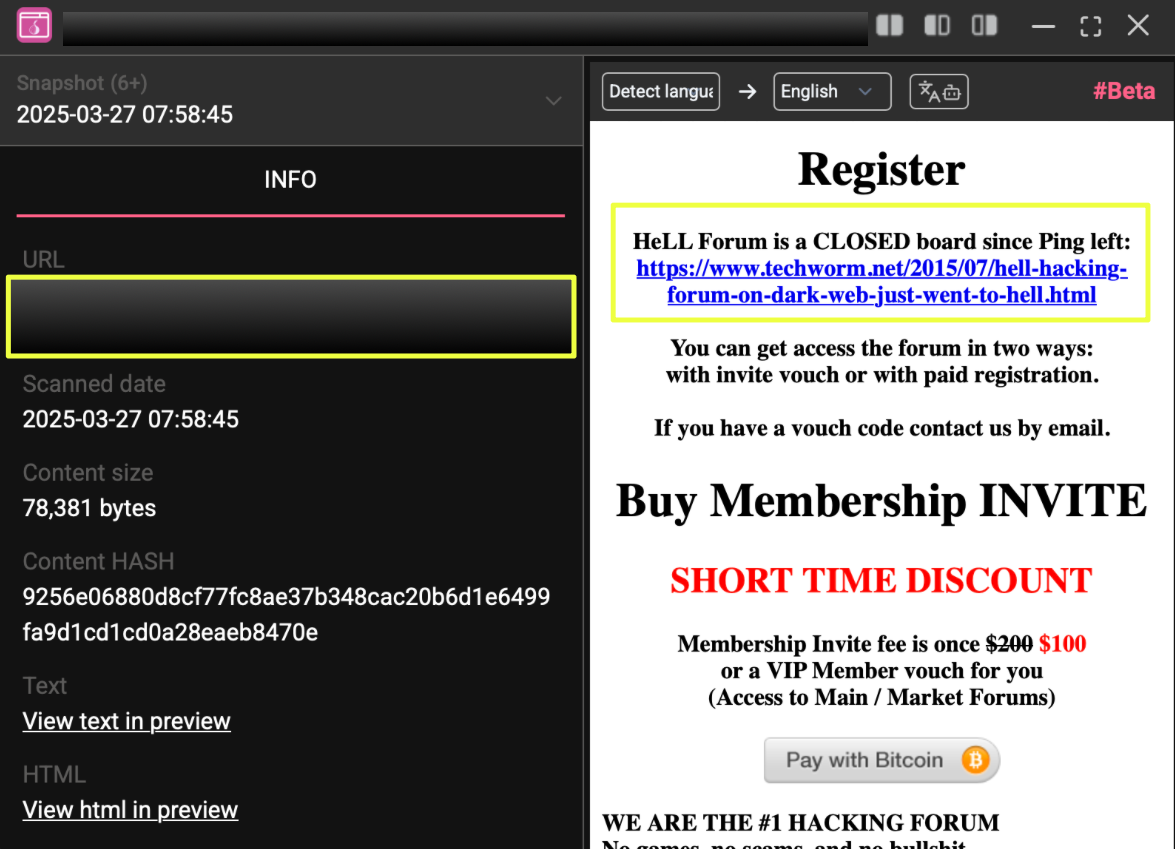
6. http://hellf**********************************************id.onion/
Active: 16 June 2025
Email: hel*****@bi*******************************************id.onion
Notes: Introduced internal onion-based email for communication and a Mycelium Gear BTC payment widget, the start of HeLL’s self-contained ecosystem phase.
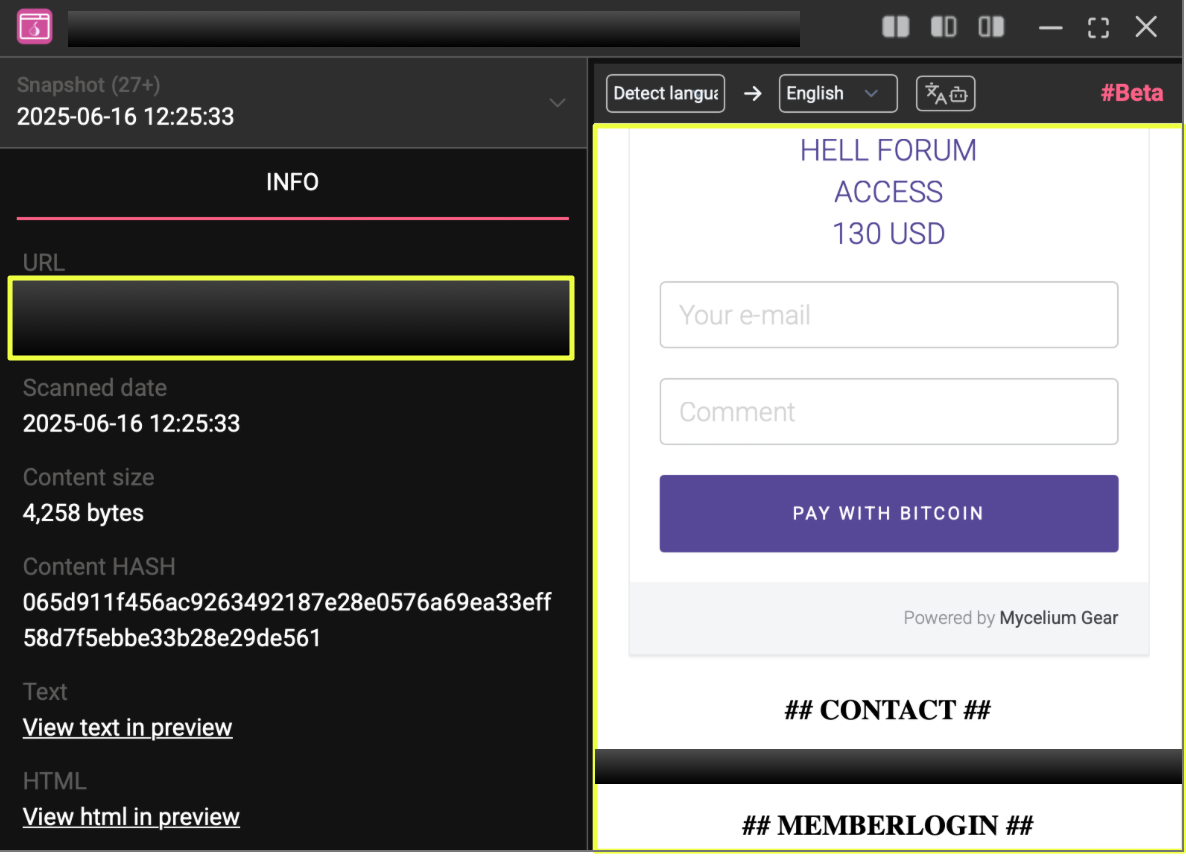
7. http://qjs************************************************ad.onion/
Active: 26 July 2025
Email: hel********@mail2tor.com
BTC: bc1******************************************w
Notes: Another mirror linking back to classic Mail2Tor contact; likely part of the July replication cluster.
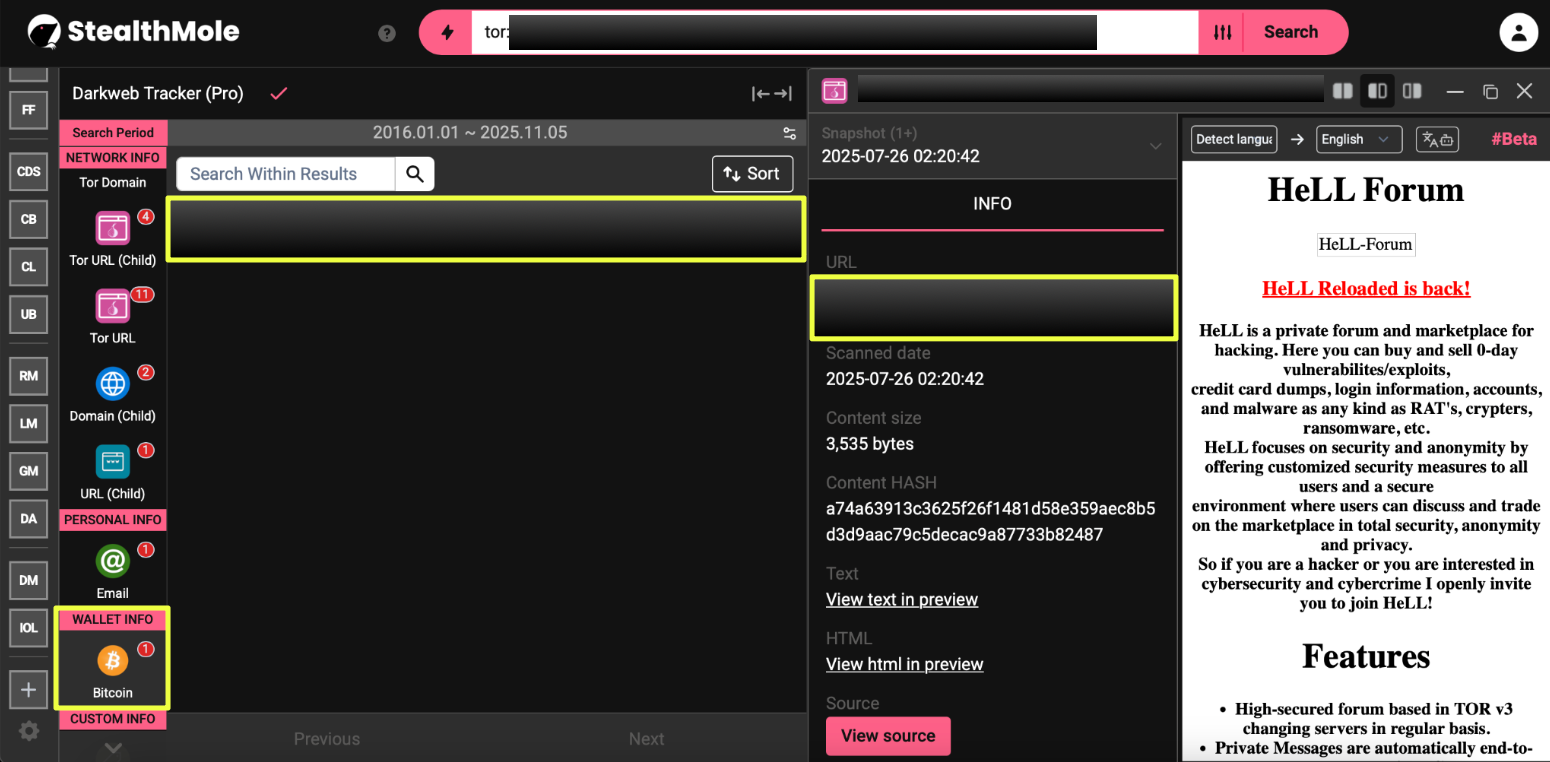
8. http://hell**********************************************yd.onion/
Active: 18 July 2025 – 7 September 2025
Emails:
- Gl************@proton.me
- Gl**************@dnmx.su
- Gl**************@dnmx.cc
- da**************@blah.im
- pla************@tuta.biz
- ha*************@tuta.biz
- ha*************@tuta.biz
- sh*************@tuta.biz
- Hi************@skiff.com
- be**************@cock.li
- ha***********@keemail.me
- sa*********@tutanota.com
- hi************t@tuta.com
- bl*************@tuta.com
- 247***********@proton.me
- dw***********@keemail.me
BTCs:
- 3QT**************************************Y
- Bc1**************************************q
- Bc1**************************************8
Notes: One of the densest mirrors, hosting multiple contact points and older wallet addresses dating back to 2019, indicating operator reuse.
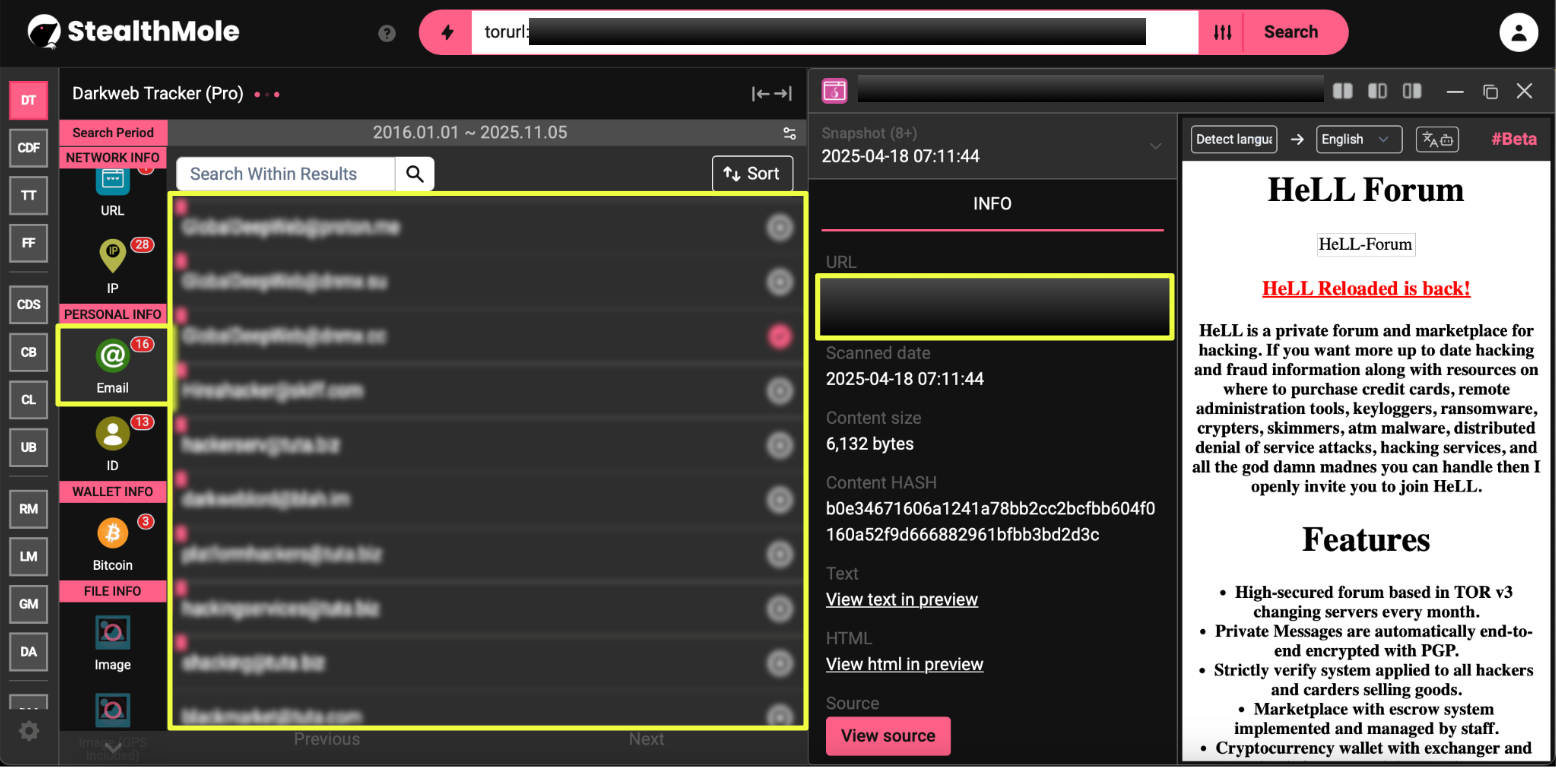
9. http://helll***********************************************id.onion/
Active: 1 March 2025 – 23 September 2025
BTCs:
- Bc1q*************************************w
- Bc1qm************************************t
Emails: Seven listed, one repeating from the previous mirror.
Notes: Exhibited repeated contact reuse and payment address rotation, strengthening links between the March and July clusters.
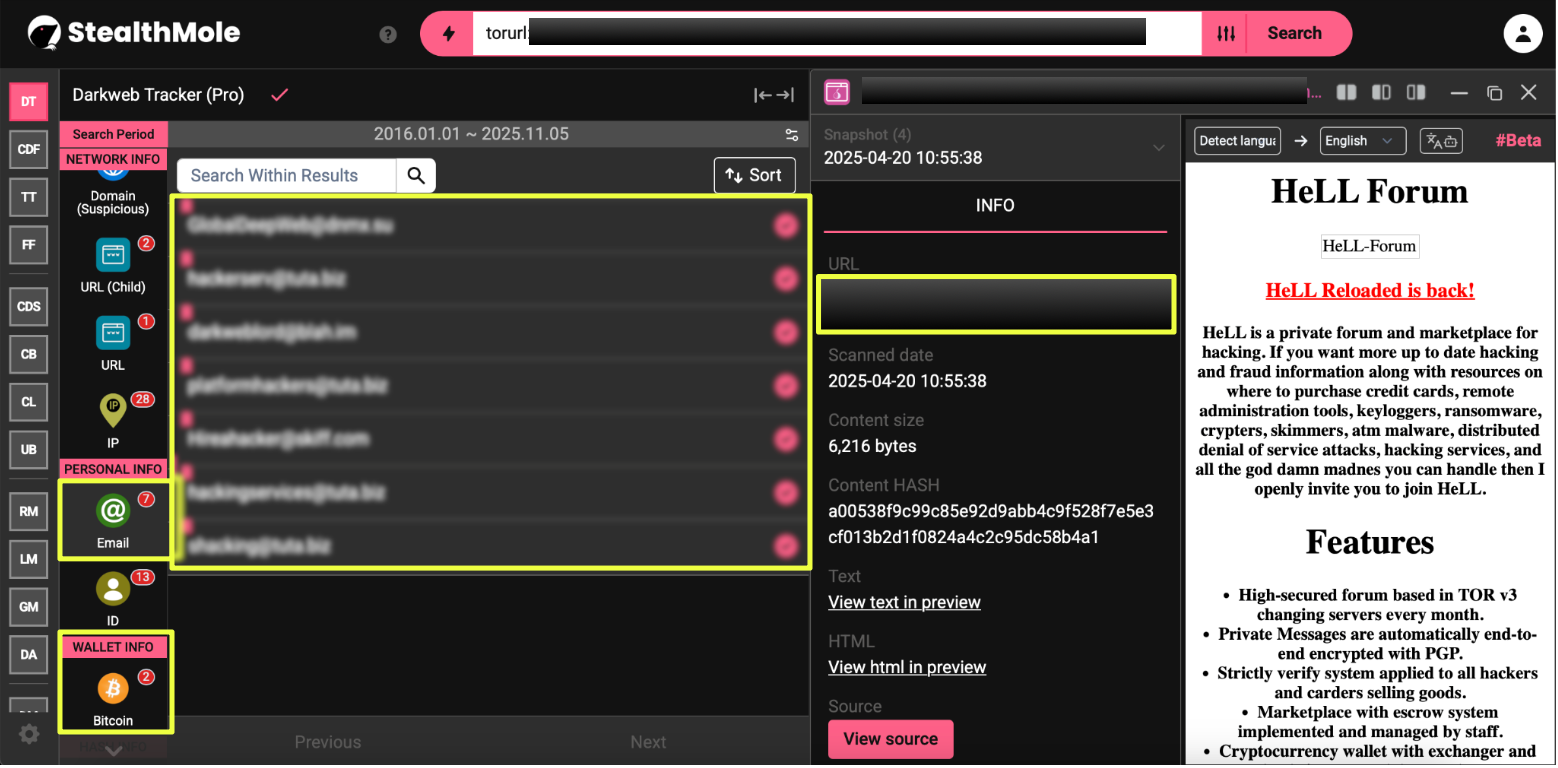
10. http://hellf********************************************5id.onion/
Active: 2 March 2025 – 23 September 2025
Email: hellf****@bipz*****************************************iid.onion
Notes: Persistent version of the earlier bipzap instance, six-month uptime and stable backend hosting confirmed continuity.
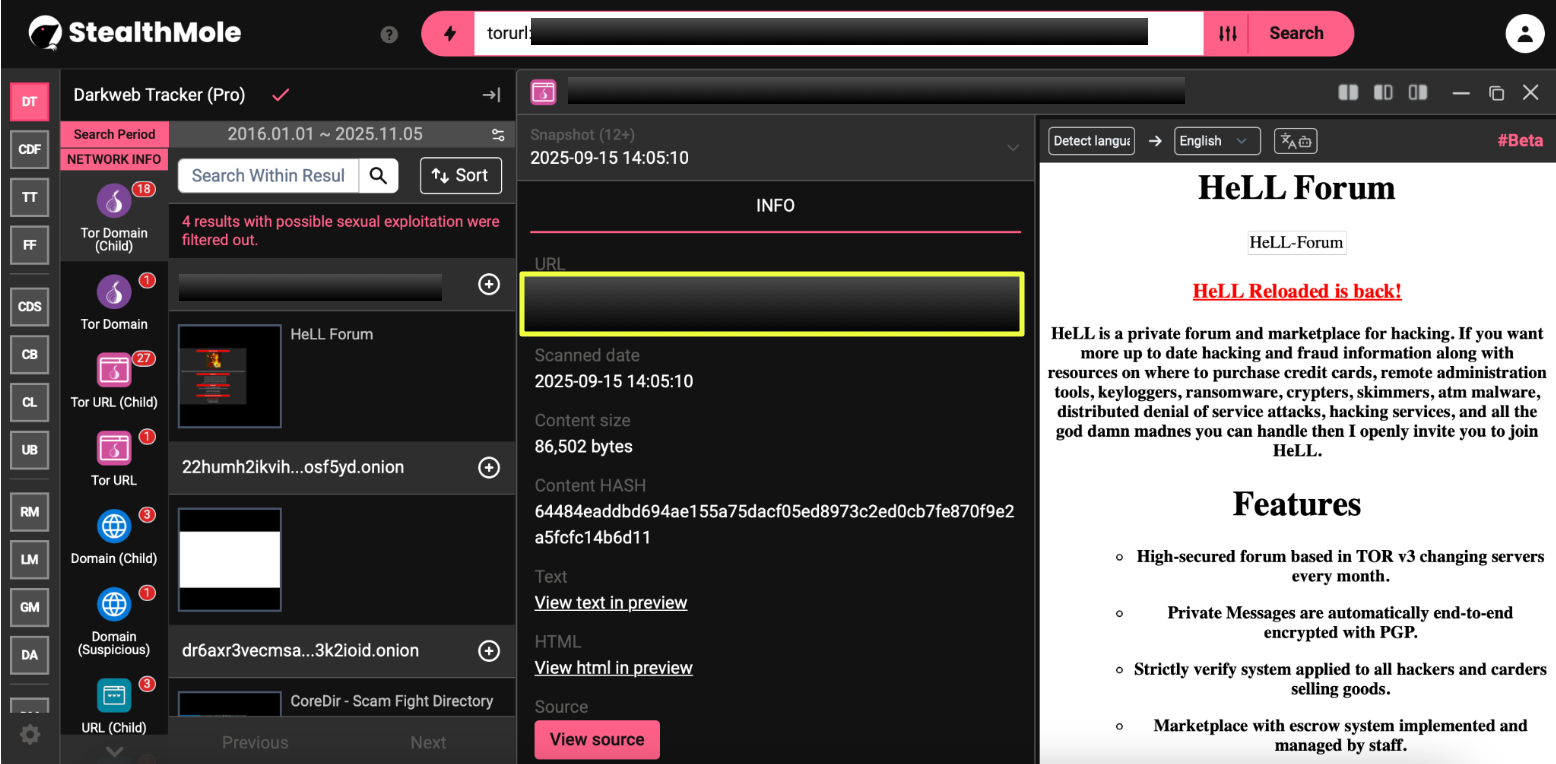
11. http://hellfo********************************************sqd.onion/
Active: 21 February 2025 – 26 September 2025
Email: hel******@bi****p.com
Notes: Clearnet variant linked to the bipzap ecosystem; indicates the use of external relay domains for off-Tor communication.
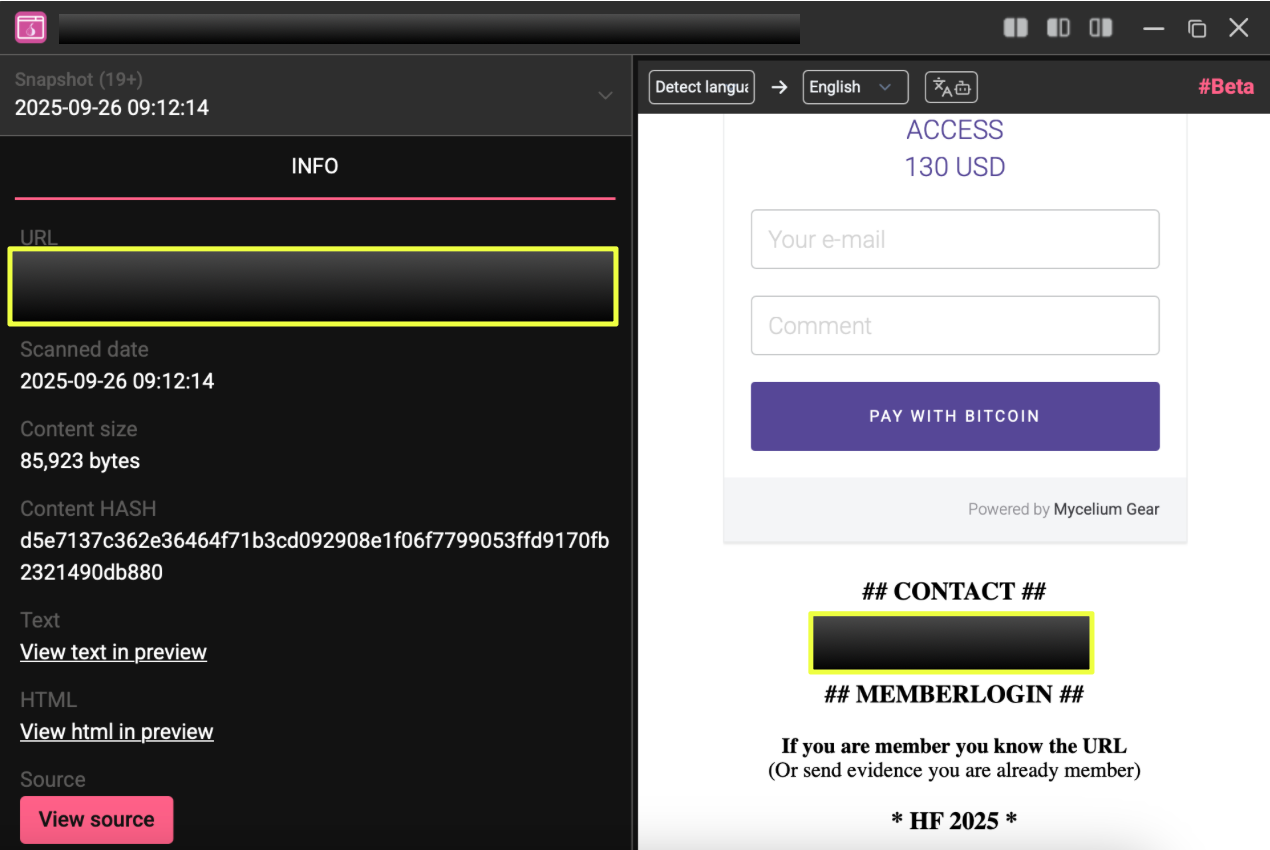
12. http://hell2k********************************************gyd.onion/
Active: 21 February 2025 – 26 September 2025
Emails: he****@ex*****t.im, hel***@mail2tor.com
Notes: Returns to the dual-contact format first seen in early HeLL mirrors, suggesting the persistence of legacy administrator routines.
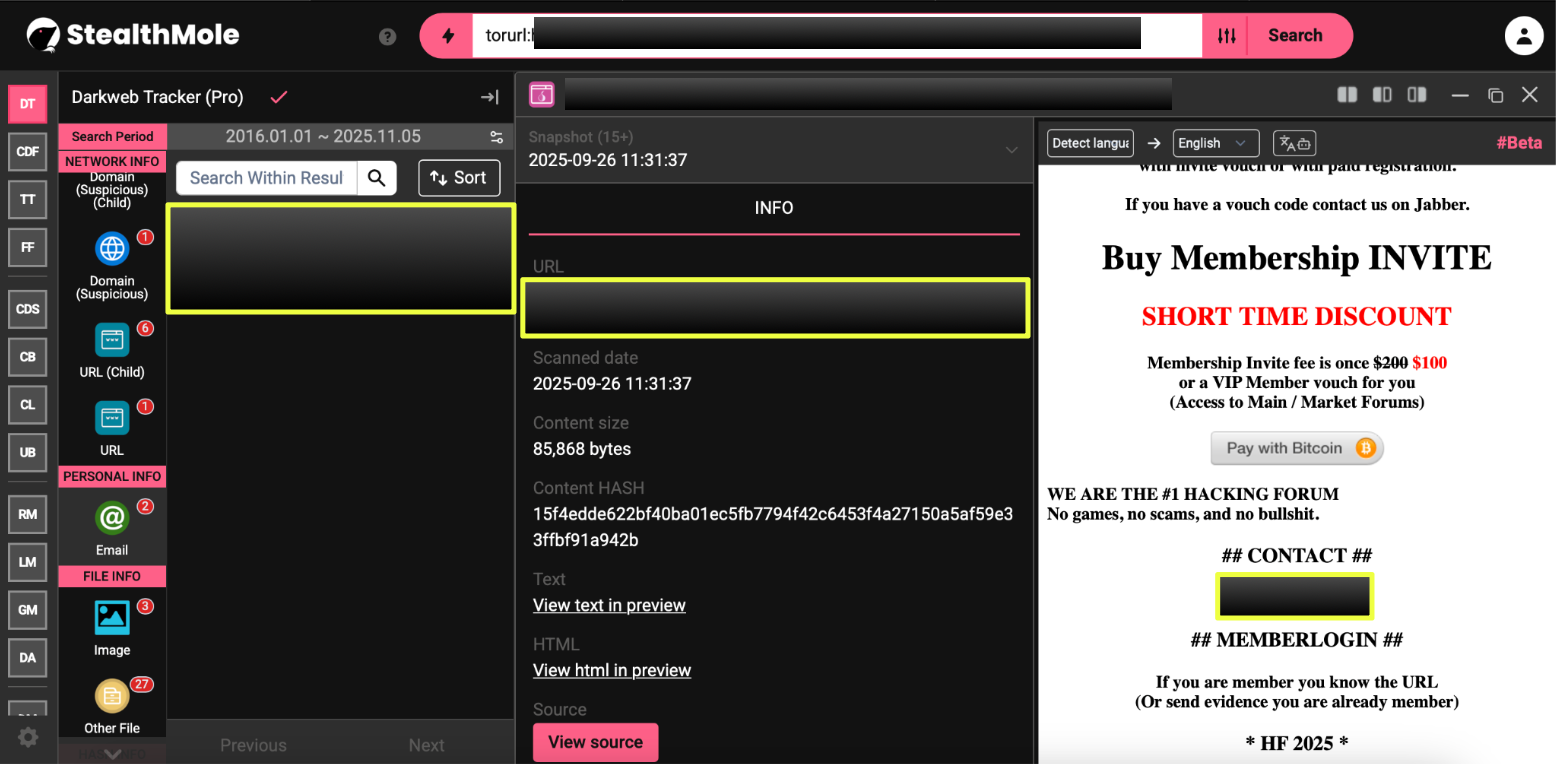
13. http://hell*********************************************qid.onion/
Active: 11 April 2025 – 30 September 2025
Emails: he****@exploit.im, he****@mail2tor.com
Notes: Transitional instance between the exploit.im and mail2tor infrastructure clusters, near-identical structure to Mirror 12.
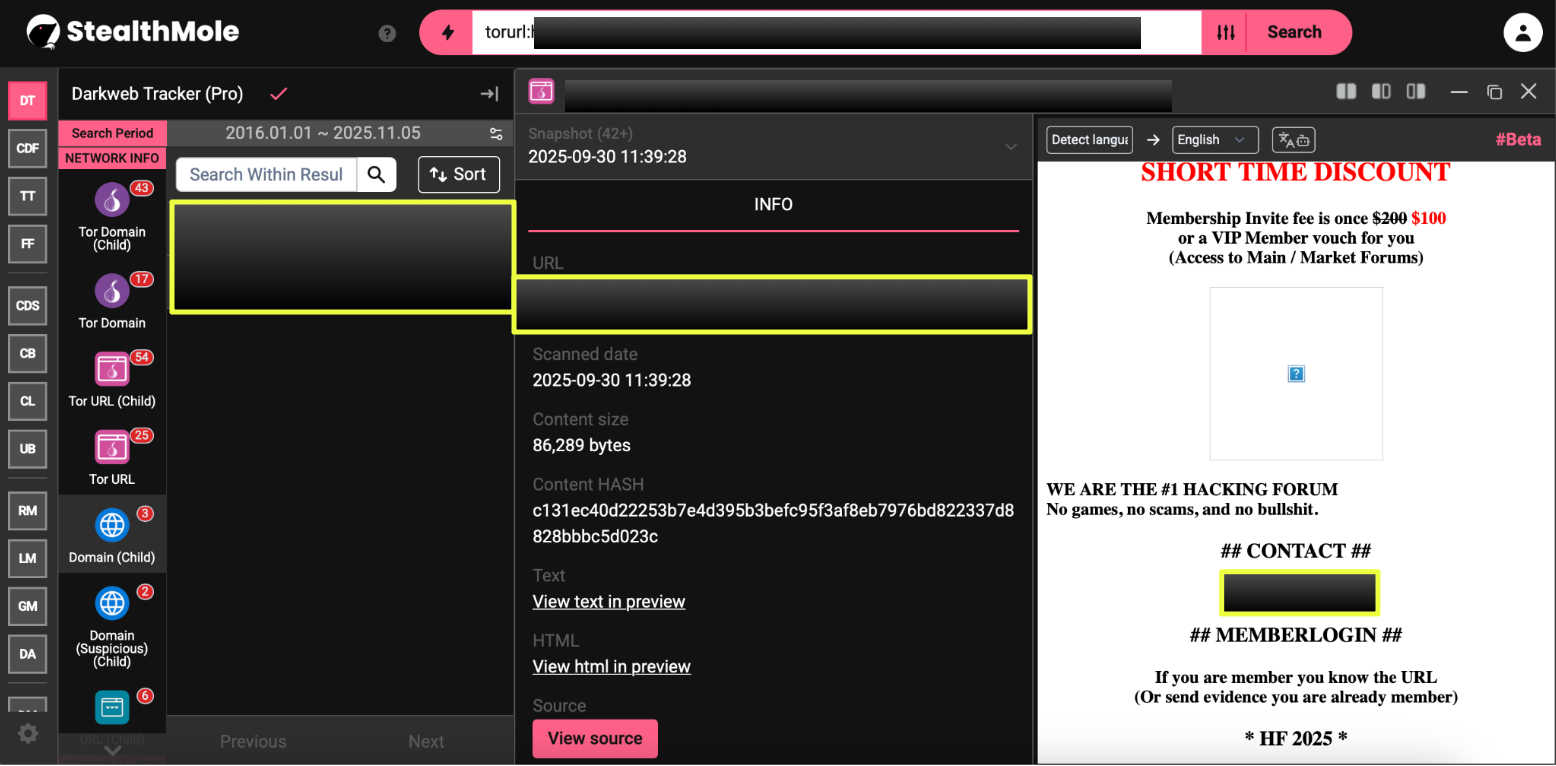
14. http://hellf*********************************************yd.onion/
Active: 23 September 2025 – 17 October 2025
BTCs:
- Bc1*************************************sn
- Bc1************************************5vs
Notes: Late-phase deployment, short operational window; continued use of unique payment addresses suggests per-user wallet rotation.
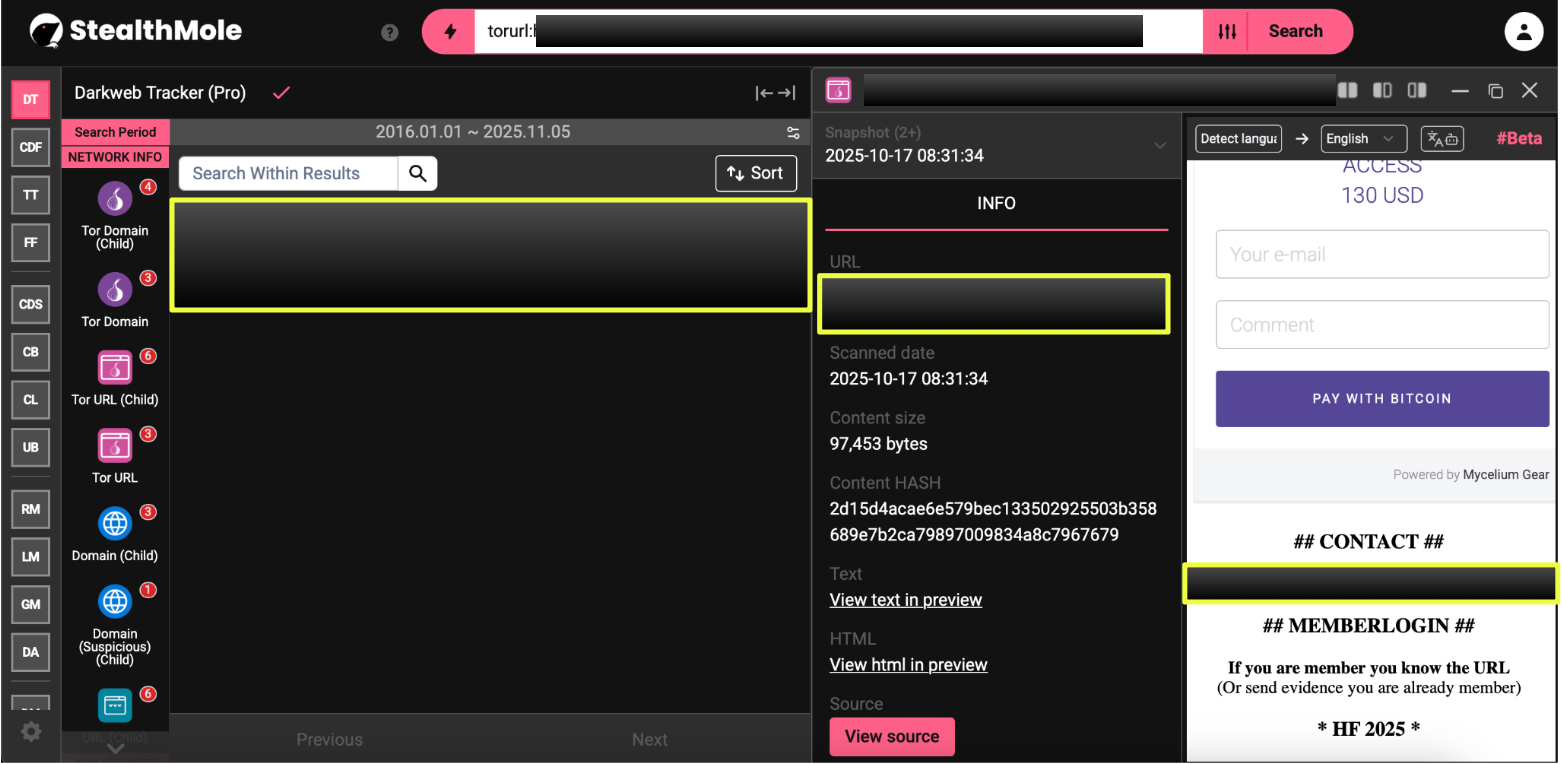
15. http://hell2********************************************dyd.onion/
Active: 17 October 2025 – 31 October 2025
Email: he****@ex******t.im
BTCs:
- Bc1************************************7sn
- Bc1************************************f89
- Bc1************************************y6k
- Bc1************************************yjv
- C1q*************************************e4
- Bc1*************************************zx
- Bc1*************************************56
- Bc1*************************************gv
- Bc1*************************************m8
Notes: Most recent live instance. Reflects an escalation in wallet segmentation, potentially tied to automated onboarding or escrow modules.
Communication Infrastructure
HeLL Forum’s communication ecosystem operated on a layered model designed for resilience and anonymity. Across its iterations, administrators relied on encrypted email platforms such as Mail2Tor, Elude, and later BipZap, with consistent naming conventions like hell@ and hellforum@ across mirrors. This uniformity points to a centralized deployment process rather than random replication.
By early 2025, the communication network expanded beyond Tor-based services, incorporating clearnet-encrypted mail providers like Exploit.im, ProtonMail, and DNMX. This hybrid approach enabled broader accessibility while preserving privacy, a deliberate evolution that balanced user onboarding with operational security.
The recurring “GlobalDeepWeb” handle family (@proton.me, @dnmx.su, @dnmx.cc) emerged as a key administrative cluster, appearing across multiple domains and acting as liaison points between users and forum operators. Their persistence across unrelated mirrors suggests a structured hierarchy, possibly coordinating membership verification and vendor management.
By mid-2025, HeLL’s communication infrastructure had matured into a dual-channel system: Tor-based mail for internal coordination and encrypted clearnet channels for outreach. This blend of accessibility and secrecy ensured continuity across takedowns and reinforced the forum’s long-standing reputation for controlled, invite-only operations.
Cryptocurrency Infrastructure
HeLL Forum’s payment system shows a clear progression toward complexity and anonymity over time. Early mirrors relied on single Bitcoin addresses embedded directly into their homepages, while later versions incorporated multiple wallets and merchant-style payment modules. This transition reflects a deliberate shift toward a compartmentalized financial model, reducing visibility into overall fund movement and limiting traceability.
Across 2025, several mirrors displayed rotating Bech32 addresses, each linked to distinct operational phases. One of the addresses was notable for showing transaction activity dating back to 2019. The reuse of an older, active wallet within newer infrastructure demonstrates continuity between earlier and current operators, supporting the theory of a consistent administrative lineage rather than independent replication.
- 3QT******************************DY
In later mirrors, including the October 2025 domain, the number of displayed wallets increased significantly with nine separate Bitcoin addresses embedded within the same page. This escalation in address segmentation likely serves both operational and security purposes: managing separate payment channels for membership tiers, and fragmenting on-chain visibility across multiple wallets.
- hell2********************************************dyd.onion
Collectively, these findings indicate that HeLL’s cryptocurrency infrastructure has evolved into a multi-wallet, rotating model rooted in earlier financial activity. Rather than isolating funds through random addresses, the operators appear to maintain continuity through a small number of legacy wallets, effectively blending old and new infrastructure to preserve credibility while complicating forensic tracking.
Assessment
The investigation into HeLL Forum’s infrastructure reveals a clear pattern of persistence, adaptation, and controlled decentralization. Across multiple years and at least fifteen confirmed .onion domains, the marketplace has maintained its operational identity, not through a single domain, but through a repeating blueprint of design, communication, and payment behavior. This consistency suggests a deliberate survival strategy, allowing the operators to preserve brand credibility even when individual mirrors are taken down or deindexed.
The continuous reuse of contact handles, particularly he***@ex****t.im, he****@ma******r.com, and the broader “GlobalDeepWeb” email cluster, indicates a central administrative link behind the forum’s many incarnations. Rather than isolated copycats, these domains appear to function as controlled mirrors or managed re-deployments, each carrying forward verified points of contact and the same membership structure. This continuity strengthens the likelihood that HeLL Forum remains under the control of one or more long-standing administrators who oversee both its public presence and its transactional backend.
The forum’s payment ecosystem also demonstrates a high level of operational discipline. While early instances relied on single Bitcoin wallets, recent iterations show a notable shift toward fragmented payment infrastructure, with up to nine distinct wallet addresses displayed simultaneously. This diversification reflects an increased focus on obfuscation and transaction isolation, likely to counter blockchain analysis and traceability. The recurring presence of Mycelium Gear-based payment modules across multiple domains further suggests a shared merchant backend or an automated script generating unique wallet addresses per transaction.
Equally significant is the reuse of the same HTML structure and “HF 2025” branding across nearly all observed mirrors. Identical templates, content hashes, and wording patterns, including the standard “Buy Membership Invite” and “No games, no scams, and no bullshit” lines, reinforce that each domain was generated from a standardized deployment kit rather than manually built. This kind of template-driven propagation is typical of well-organized underground operations that maintain centralized version control while allowing flexibility in hosting and deployment.
The overlapping lifespans of multiple mirrors, sometimes active concurrently for months, reveal an infrastructure model based on redundancy rather than replacement. Such overlap ensures that even if one instance is disrupted or reported, others continue to function seamlessly. This distributed continuity effectively guarantees the forum’s resilience, a tactic commonly used by persistent cybercriminal marketplaces aiming to avoid complete takedown through single points of failure.
Taken together, the mirrored domains, wallet rotation patterns, and repeated communication channels confirm that HeLL Forum is not a relic of its 2015 legacy, but an actively maintained ecosystem adapting to modern dark web norms. The evidence indicates a structured administrative hierarchy operating through automation and consistent branding, designed to maintain both user trust and operational anonymity. Its evolution from static forums to dynamic, multi-wallet commerce nodes underscores HeLL’s ongoing relevance as one of the longest-surviving cybercrime communities to persist through multiple shutdown waves.
Conclusion
The story of HeLL Forum is one of endurance and transformation. Across years of shutdowns, migrations, and reappearances, it has managed to preserve a single identity that continues to command recognition in dark web communities. What once functioned as a simple forum has gradually evolved into a self-replicating ecosystem: decentralized, encrypted, and engineered for continuity.
Rather than disappearing, HeLL has adapted to its environment. Each new domain, wallet, and contact address represents not a replacement but a recalibration, evidence of a system designed to outlast attention, disruptions, and even its own administrators. The re-emergence of old wallet addresses and communication patterns within newer infrastructure suggests a lineage of control stretching back years, reflecting a model of organized persistence rarely seen in dark web operations.
Beyond its technical sophistication, HeLL’s continued survival demonstrates a deeper trend: that reputation, once established in the underground economy, becomes a kind of currency of its own. For its members and vendors, the name “HeLL” carries trust, a guarantee of authenticity that allows its operators to reappear under new domains and instantly regain legitimacy.
What this investigation ultimately reveals is not just the structure of a cybercriminal forum, but the blueprint of long-term brand survival on the dark web. HeLL Forum stands as a reminder that in the underground, permanence is not achieved through stability, but through reinvention: one mirror, one wallet, and one name at a time.
Editorial Note
While every effort has been made to ensure the accuracy of this report, it is important to acknowledge that attribution in cyber investigations can never be guaranteed with complete certainty. The connections drawn are based on available open-source intelligence and StealthMole platform data. However, attribution remains probabilistic and subject to change as new information emerges.
The primary goal of this report is not just attribution, but to showcase how StealthMole’s platform enables comprehensive, efficient, and intuitive profiling of threat actors through integrated tools such as Dark Web & Telegram Trackers, ULP Binder, the Compromised Data Set and others. These tools allow even independent researchers to connect dots across aliases, infrastructure, and behavioral patterns, transforming fragmented data into actionable intelligence.
Labels: Darkweb Marketplace

.svg)
.svg)
.svg)