Inside 0Day Today: Infrastructure, Mirrors, and Exposure Patterns
The platform 0day.today occupies a persistent space within the online exploit ecosystem. For years, it has circulated through cybersecurity discussions, darkweb resource lists, and archived exploit catalogs, often referenced, rarely explained, and almost never examined in a structured way. This report takes a step back from assumptions, focusing instead on what can actually be observed about the platform through StealthMole. Rather than treating 0day.today as a marketplace, we approached it as an open question: What does this platform look like when analyzed across the surface, deep, and dark web using real, captured evidence?
The goal of this investigation is not to validate the authenticity of any exploit claims but to understand the platform’s visible footprint: how it presents itself, where it appears, and what kinds of digital traces emerge when its domains, mirrors, and identifiers are examined. Using StealthMole, the platform was observed across multiple contexts, including its web-facing structure, associated mirrors, user-facing touchpoints, and external references scattered across community spaces. Each dataset provided a different perspective, and together they form a more complete picture of how 0day.today functions within the wider ecosystem.
This report organizes those findings into a clear analytical narrative. Subsequent sections walk through the discovery path, highlight the platform’s observable infrastructure, and outline the various signals connected to it across multiple data sources. By approaching 0day.today in this evidence-first manner, the analysis aims to give readers a grounded understanding of the platform’s presence, setting the stage for deeper insights in the sections that follow.
Incident Trigger & Initial Investigation
The investigation began with a broad inquiry into how “private exploit” offerings surface across dark web, particularly those that position themselves as repositories or distribution points for unpatched vulnerabilities. The goal at this stage was simply to observe which platforms or services appeared repeatedly when actors discussed obtaining exploit code outside formal disclosure channels. During this sweep, StealthMole’s Darkweb Tracker surfaced a Tor-hosted address, identifying itself as a gateway to a platform called 0day.today. The appearance of this domain was notable because it emerged organically through dark web indexing rather than from deliberate targeting, prompting a closer look at what the service actually represented.
- sq542*************************************************3id.onion
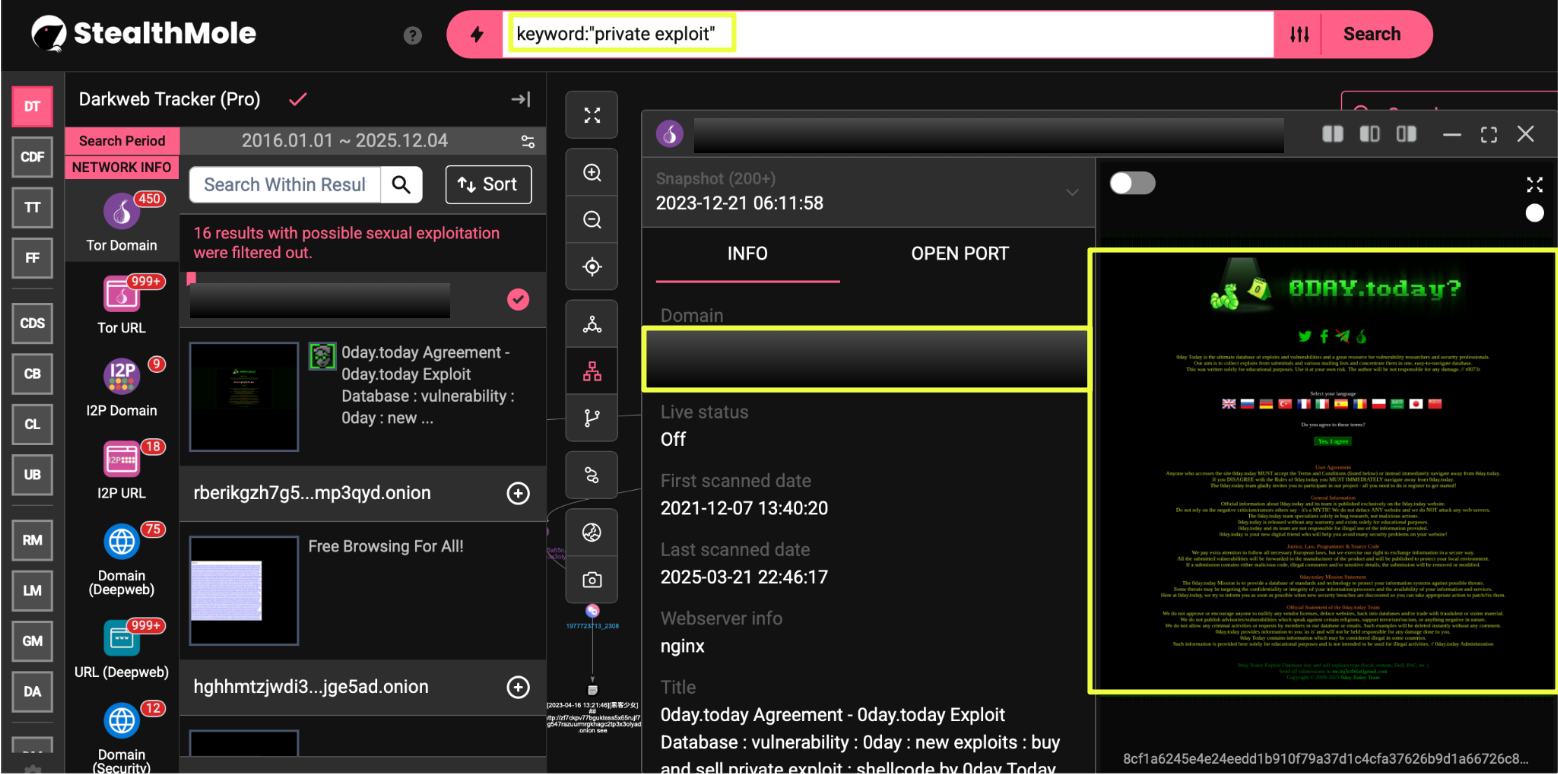
The initial task was to understand the nature of the onion site itself: whether it functioned as an active service, a mirror of a known platform, or a static artifact left behind from a previous operational period. Using StealthMole, the domain was queried to capture its landing structure, visible content, and any immediate patterns observable from the pages accessible through the onion service. At this stage, the objective remained intentionally broad: to determine how the platform presents itself within the Tor environment and whether it is part of a larger ecosystem.
As the onion link was explored, additional related paths surfaced through StealthMole, revealing that the platform did not exist solely as a single darkweb instance. Instead, several additional domains and language-specific entry points began to appear, suggesting a distributed or mirrored layout rather than a standalone service. These early findings set the direction for the rest of the investigation, indicating that what initially appeared as a single Tor resource might represent a wider footprint spanning multiple access points.
Infrastructure Mapping
Once the presence of the onion domain was established, the next step was to understand how this resource fit into the broader structure of the platform it referenced. Using StealthMole, the onion link was expanded outward to identify any additional mirrors, language variants, or structural patterns associated with the platform. This process quickly revealed that the service was not confined to a single entry point; instead, it appeared as a distributed network of URLs that consistently mirrored the same presentation, layout, and messaging.
- sq542***************************************************3id.onion
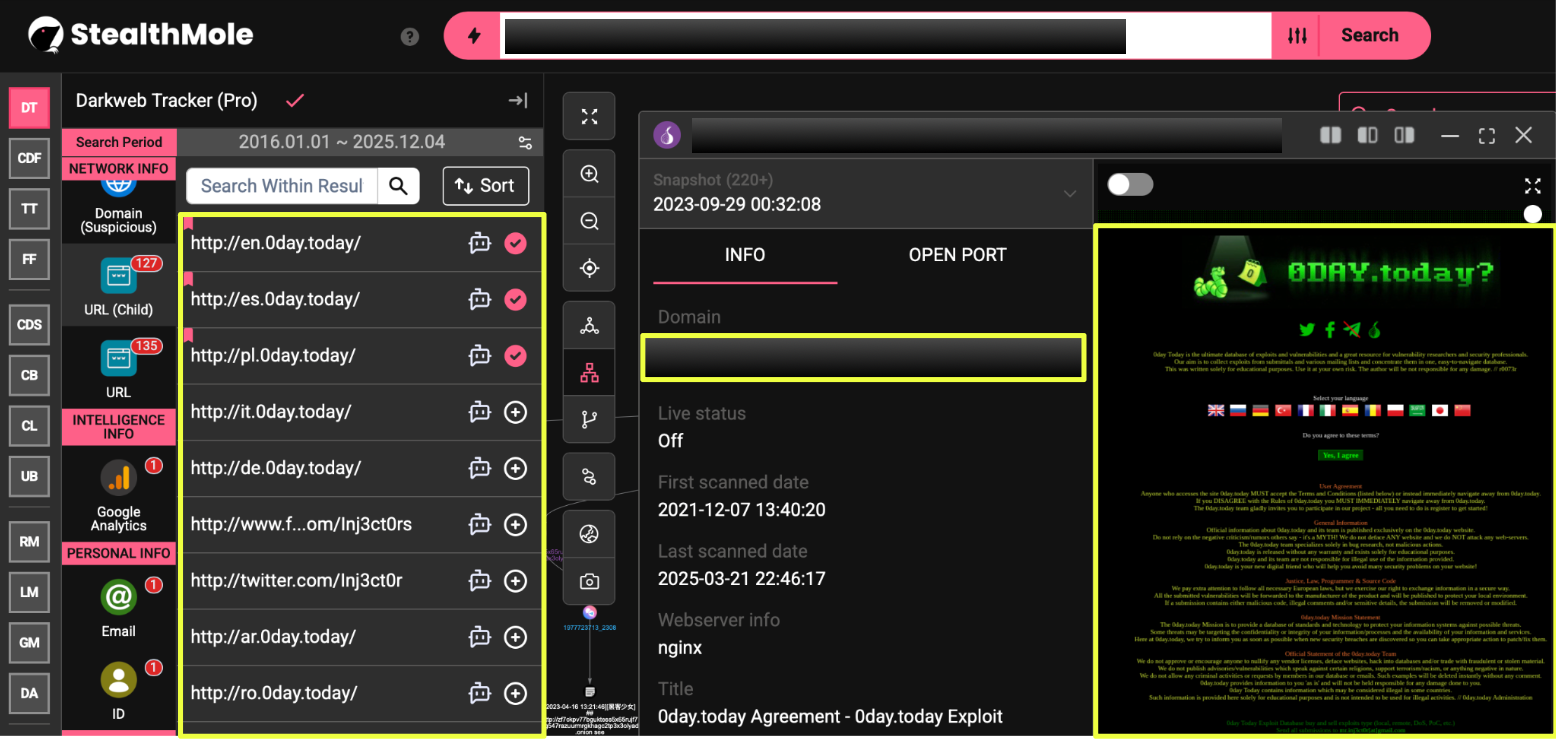
Multiple language-specific subdomains emerged during this phase, including:
- http://en.0day.today
- http://es.0day.today
- http://pl.0day.today
- http://fr.0day.today
- http://it.0day.today
- http://ru.0day.today
- http://tr.0day.today
- http://ro.0day.today
- http://cn.0day.today
- http://de.0day.today
- http://jp.0day.today.
Despite their regional labels, each instance displayed nearly identical content and messaging, suggesting that the platform relies on a template-based mirroring structure rather than localized or independently maintained deployments. The website showed consistent HTML size, visual design, and disclaimers across these domains, reinforcing the impression of a single platform replicated across multiple language fronts.
Alongside the clearweb subdomains, additional Tor-based mirrors also surfaced during the mapping phase. These domains displayed the same structural characteristics and branding.
- Zf7c*************************************************yad.onion
- Cura*************************************************cyd.onion
- Mvf****************o.onion
- Mv****************g3.onion
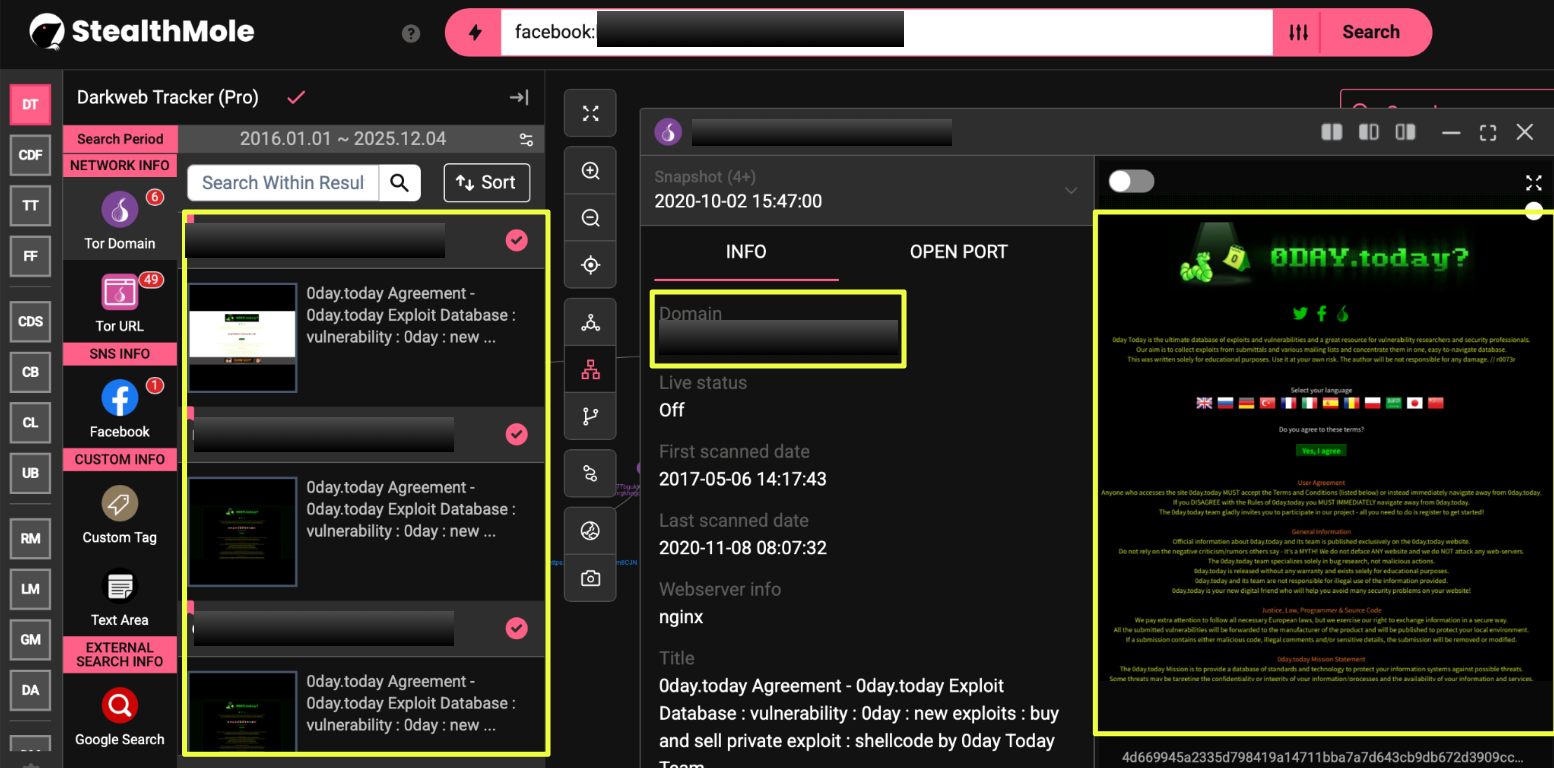
Some of these onion links were also referenced in external community spaces, such as Telegram channels and Pastebin posts, indicating that the mirrors were known among users even if no official communication confirmed their provenance.
The consistency across both clearweb and darkweb versions suggested that 0day.today functions through a wide but shallow distribution model: a single platform presented through numerous access points with minimal differentiation between them. This structure provided a foundation for the subsequent analysis, enabling the investigation to move from identifying where the platform is hosted to examining how it is referenced, used, and exposed across various datasets.
Platform Identity and Public-Facing Elements
As the platform’s distributed infrastructure became clearer, the investigation turned toward cataloging the elements that 0day.today publicly associates with its identity. These artifacts were identified through StealthMole, where recurring contact points, messaging handles, and social media links appeared consistently throughout the platform’s structure.
Multiple mirrored instances prominently listed mr.in******r@gmail.com as the contact point for submissions or proposals, while additional identifiers such as 1*****y@jabber.org and a*****@0day.today appeared across various pages linked to the site. These addresses were consistently embedded in the platform’s layout, indicating that they form part of the legacy communication channels tied to the 0day.today ecosystem.
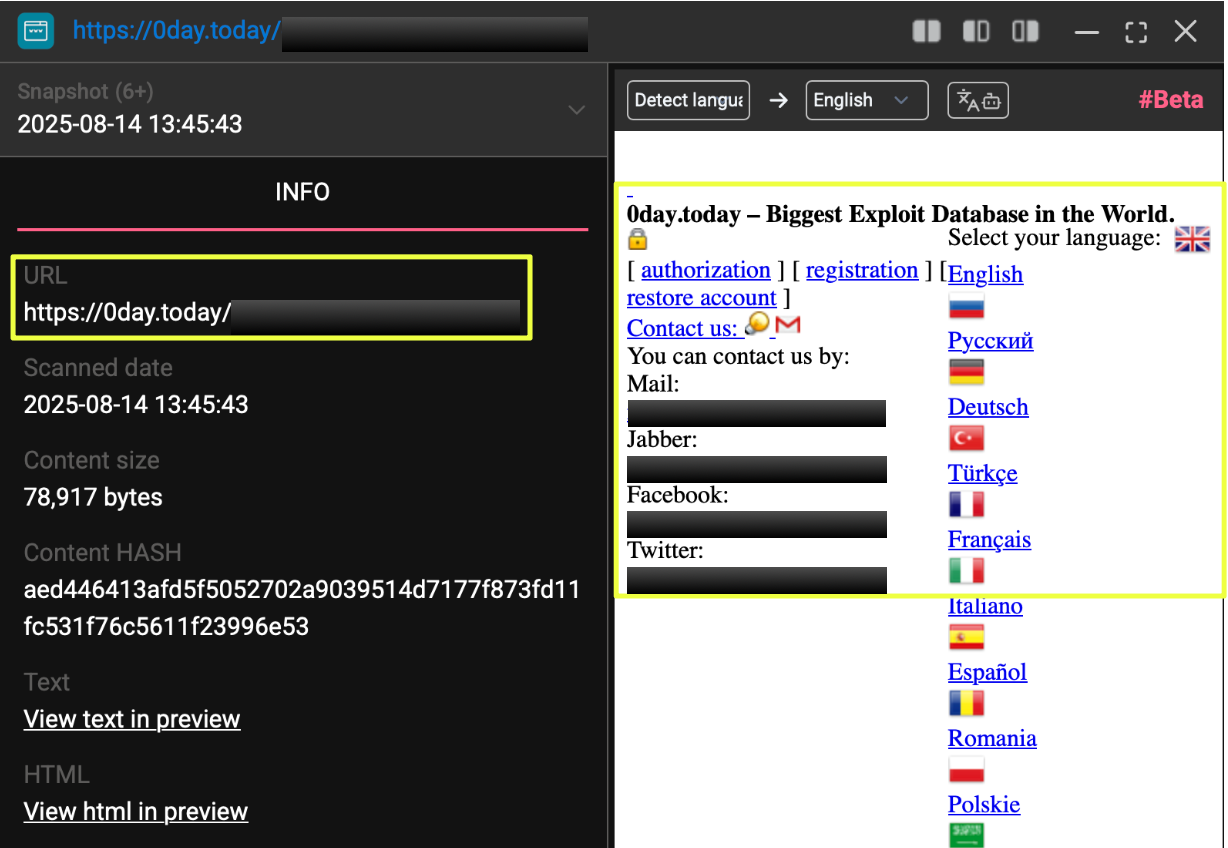
Social media references, including facebook.com/I******rs and twitter.com/I******r, also appeared across several variants of the platform. Their repeated inclusion suggests that these profiles were intentionally aligned with the site’s public-facing identity, forming part of the broader Inj3ct0r/1******y branding visible in other mirrored pages.
An important detail emerged in parallel: several mirrored versions of the site included a clear statement that the platform does not maintain any presence on Telegram or other messenger services. This message was positioned prominently on certain landing pages, cautioning users about unofficial accounts impersonating the platform. While the platform distances itself from Telegram activity, this disclaimer also helped contextualize later findings where external actors referenced 0day.today independently of any official communication.
External References and Community Mentions
As the investigation broadened beyond the platform’s own hosted pages, we focused on how 0day.today appears in the wider ecosystem where users informally share, recommend, or archive exploit-related resources. Rather than looking for official communication from the platform, which it explicitly states it does not provide through Telegram or other messengers, this stage focused on understanding how its domains and mirrors circulate organically through user-driven spaces. StealthMole’s telegram tracking capabilities allowed these references to be traced across Telegram channels, paste sites, and darkweb, offering a view of the platform’s presence outside its self-maintained infrastructure.
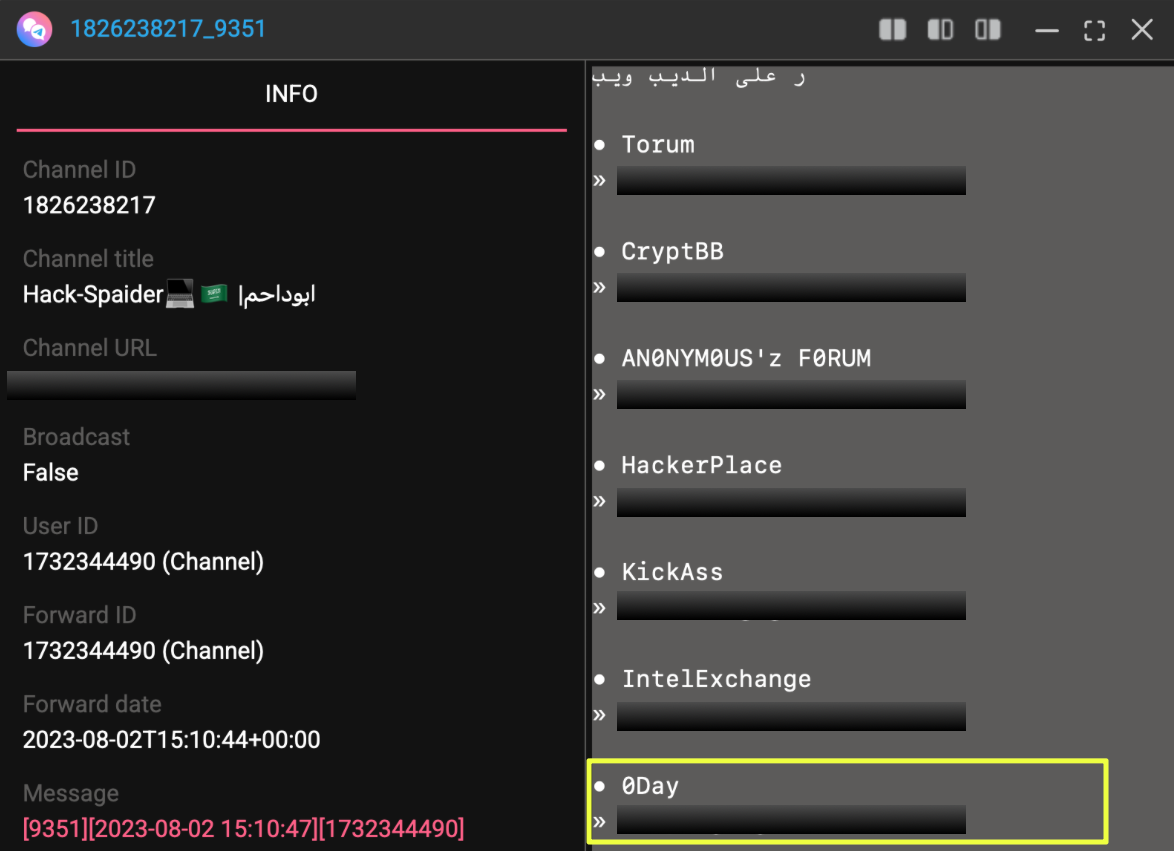
It was found that several 0day.today mirrors are referenced across a range of Telegram channels, often as part of broader lists of dark web sites or exploit-oriented resources. For example, the onion address mvf**********ho.onion appeared in dozens of channel messages, typically alongside other well-known forums and marketplaces. These mentions were not framed as official announcements but as community-compiled lists, forwarded posts, or general resource compilations shared among users. Similarly, mirrors (see below) surfaced in Telegram references and external indexing sites, reinforcing that these variants circulate independently of any operator-controlled outreach.
- zf7c*************************************************yad.onion
- cura*************************************************cyd.onion
Additional references appeared on paste-sharing platforms, where StealthMole captured instances of mirror URLs included within broader collections of .onion links. These entries mirrored the structure seen in Telegram posts, informal lists curated by users rather than platform operators. Indexing services such as OnionTree also catalogued several mirrors, at times flagging them with cautionary notes, adding contextual information without altering the observable footprint.
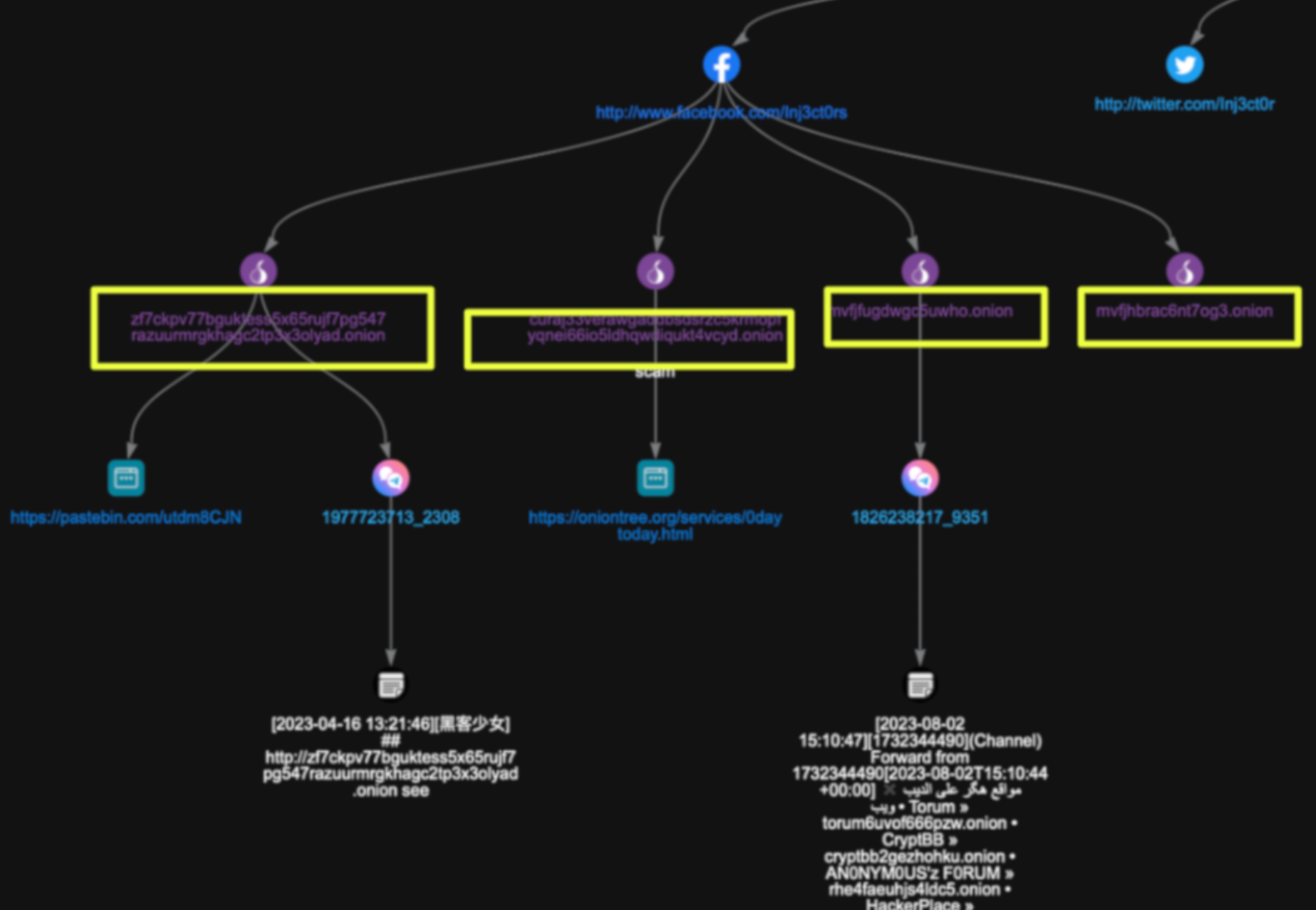
Overall, these community mentions highlighted how 0day.today spreads through ecosystems shaped primarily by user activity. Despite the platform’s explicit statement that it does not maintain a presence on Telegram or messenger applications, its mirrors and subdomains emerge frequently across crowdsourced posts, resource lists, and archival references. These patterns offered additional avenues for analysis as the investigation progressed toward examining how the platform and its identifiers intersect with broader exposure datasets.
Compromised Credentials
To understand how 0day.today interacts with the broader data breach landscape, the platform’s domains and publicly associated identifiers were examined using StealthMole’s credential exposure tools. This phase aimed to determine whether the platform itself, its mirrors, or its declared contact points appeared in compromised credential collections, breach compilations, or historical leak datasets.
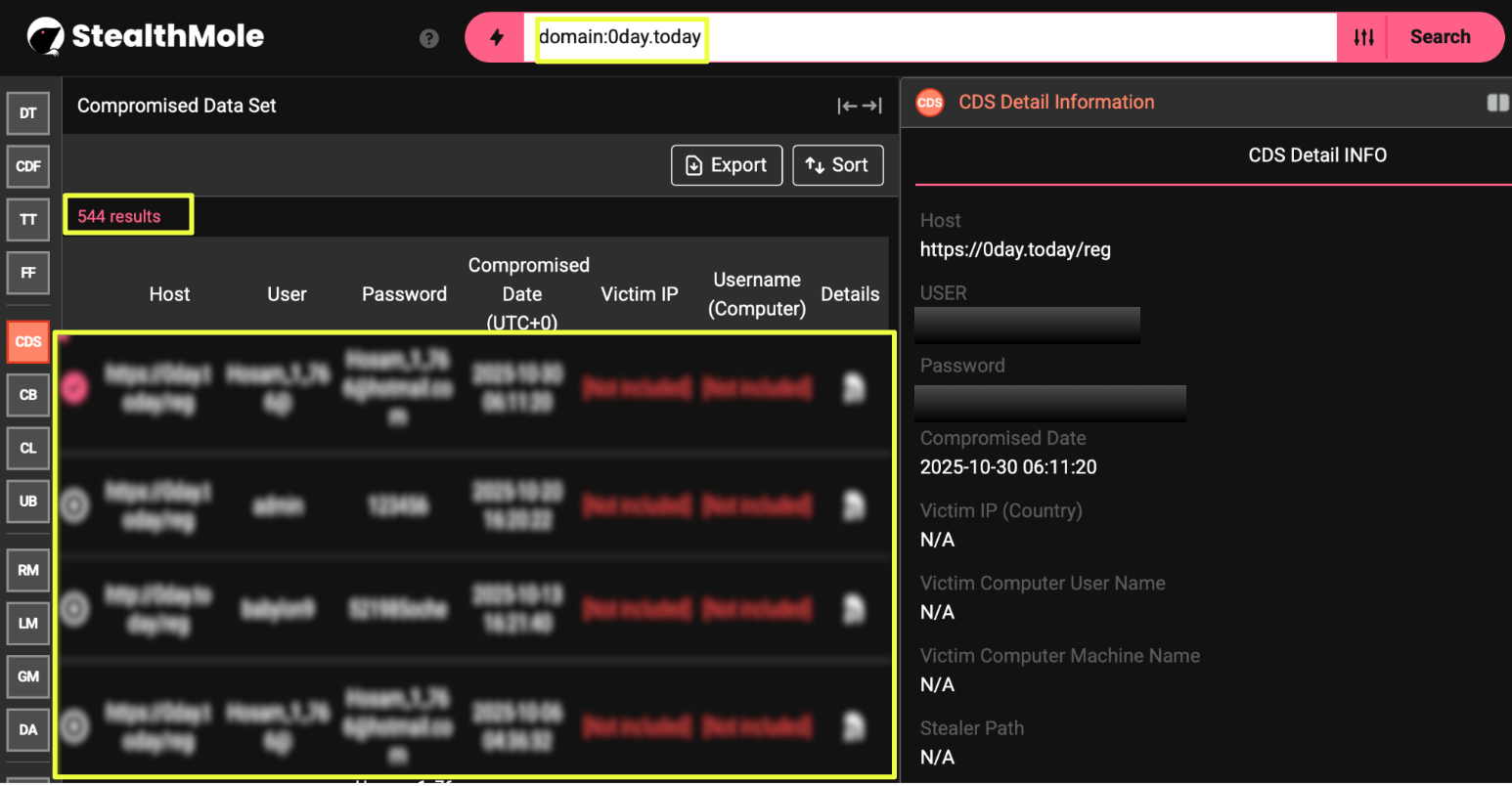
Running the primary domain 0day.today and its variants through StealthMole’s Compromised Data Set (CDS) revealed a significant number of entries linked to the site’s registration or login paths. Across CDS, more than five hundred results appeared for URLs such as https://0day.today, https://0day.today/reg, and their language-specific equivalents. These records reflected user credentials exposed through external breach events, indicating that individuals who created accounts on the platform later had their information captured in unrelated compromises. Additional entries surfaced through the ULP Binder, which produced several hundred more results tied to the same set of domains, further illustrating that the platform’s user base appears frequently within leaked datasets.
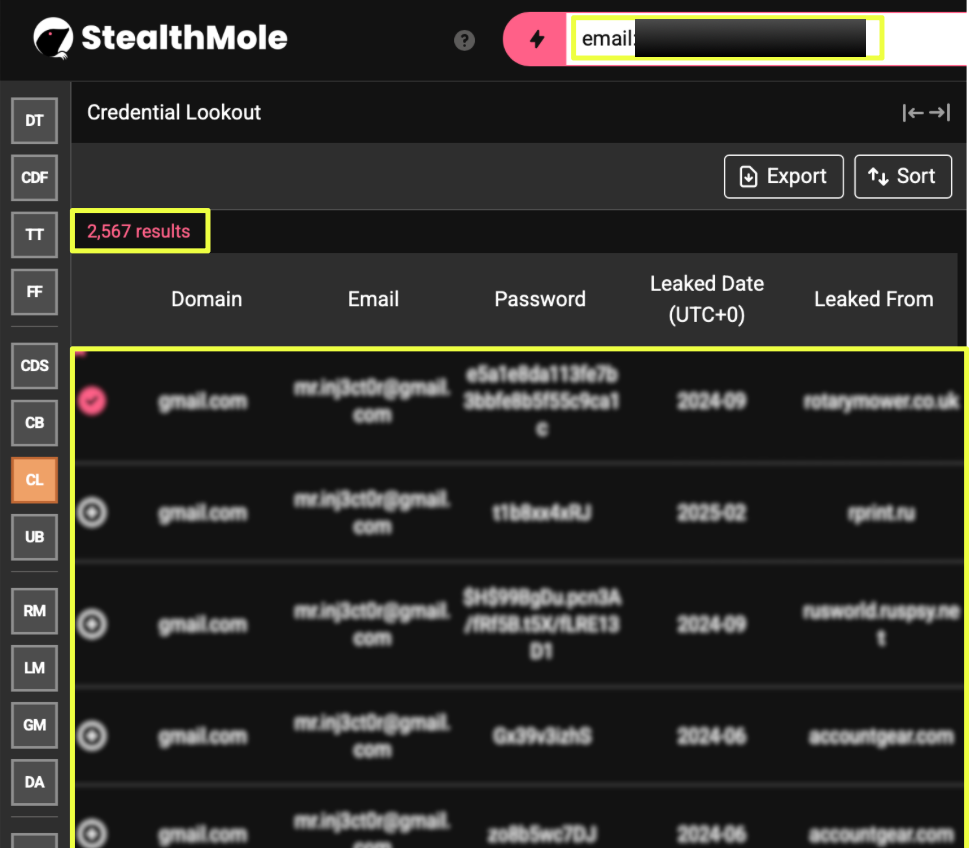
The platform’s publicly stated contact email, mr.in********r@gmail.com, was examined separately due to its repeated presence across multiple mirrored versions of the site. When queried through StealthMole’s Combo Binder and Credential Lookout, the address returned several thousand compromised entries spanning numerous unrelated third-party websites. These records reflected wide reuse of the email across different services and time periods, positioning it as a consistent point of exposure within historical breach data.
Assessment
The investigation ultimately positioned 0day.today as a legacy platform whose present-day footprint is fragmented across inconsistent infrastructure, outdated operator channels, and repurposed web content. What emerged through StealthMole was not the profile of an active exploit marketplace competing in today’s cybercrime economy, but rather a platform that continues to persist in traces: technically reachable, frequently referenced, and still indexed, despite showing no signs of ongoing maintenance or operational coherence.
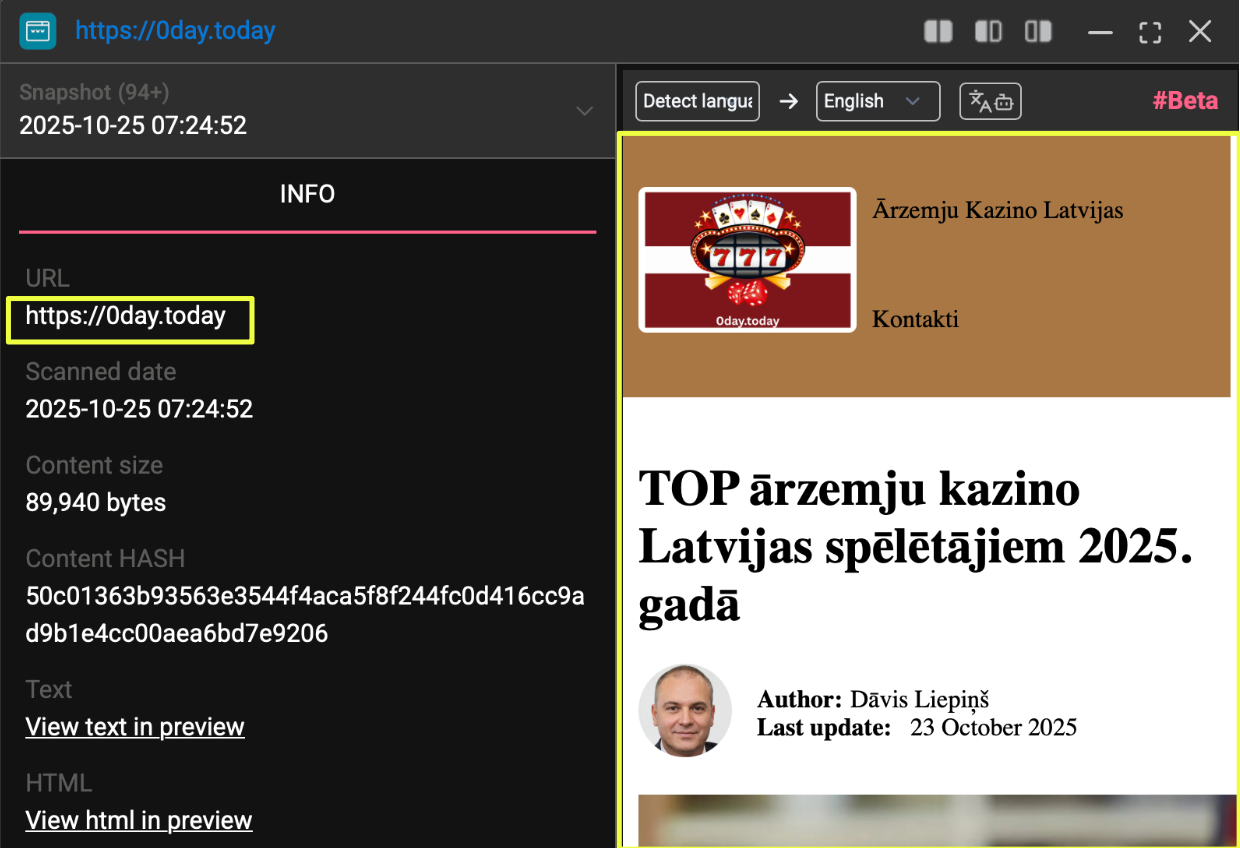
One of the clearest indicators of this fragmentation was the behaviour of the primary web domain. When accessed directly, https://0day.today resolved to a Latvian-language gambling website, an entirely unrelated commercial service that appeared to occupy the front-facing landing page. However, when navigating to internal historical paths such as https://0day.today/local#popup_welcome_div, the platform’s original interface reappeared: the signature green-themed Inj3ct0r layout, legacy exploit listings, references to “1337day Gold,” and familiar static elements that had been characteristic of the site for more than a decade. This coexistence of two unrelated web layers strongly suggests that while portions of the original backend remain online, the domain’s top-level index has been replaced, hijacked, or otherwise overwritten.

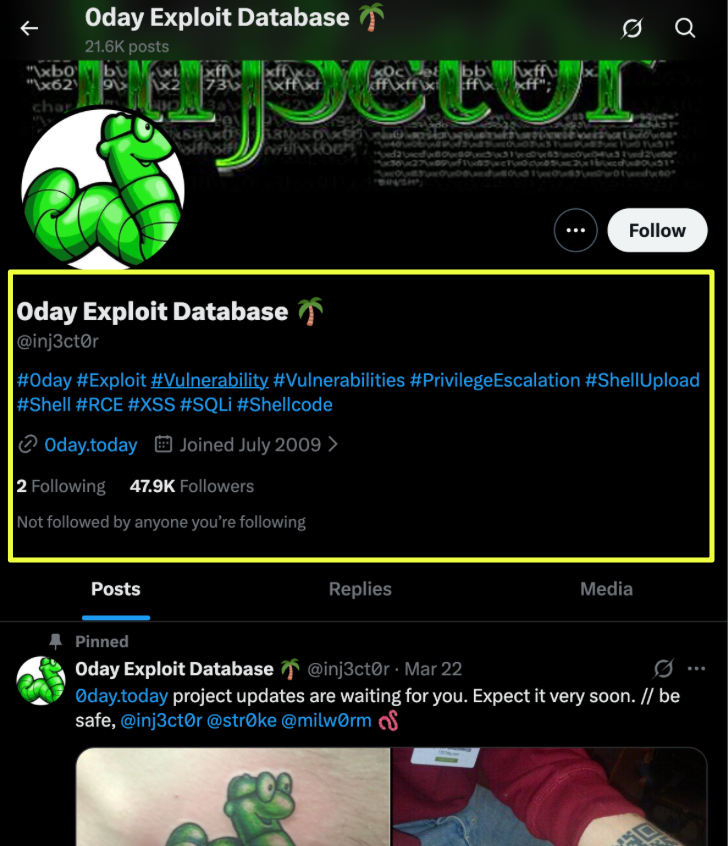
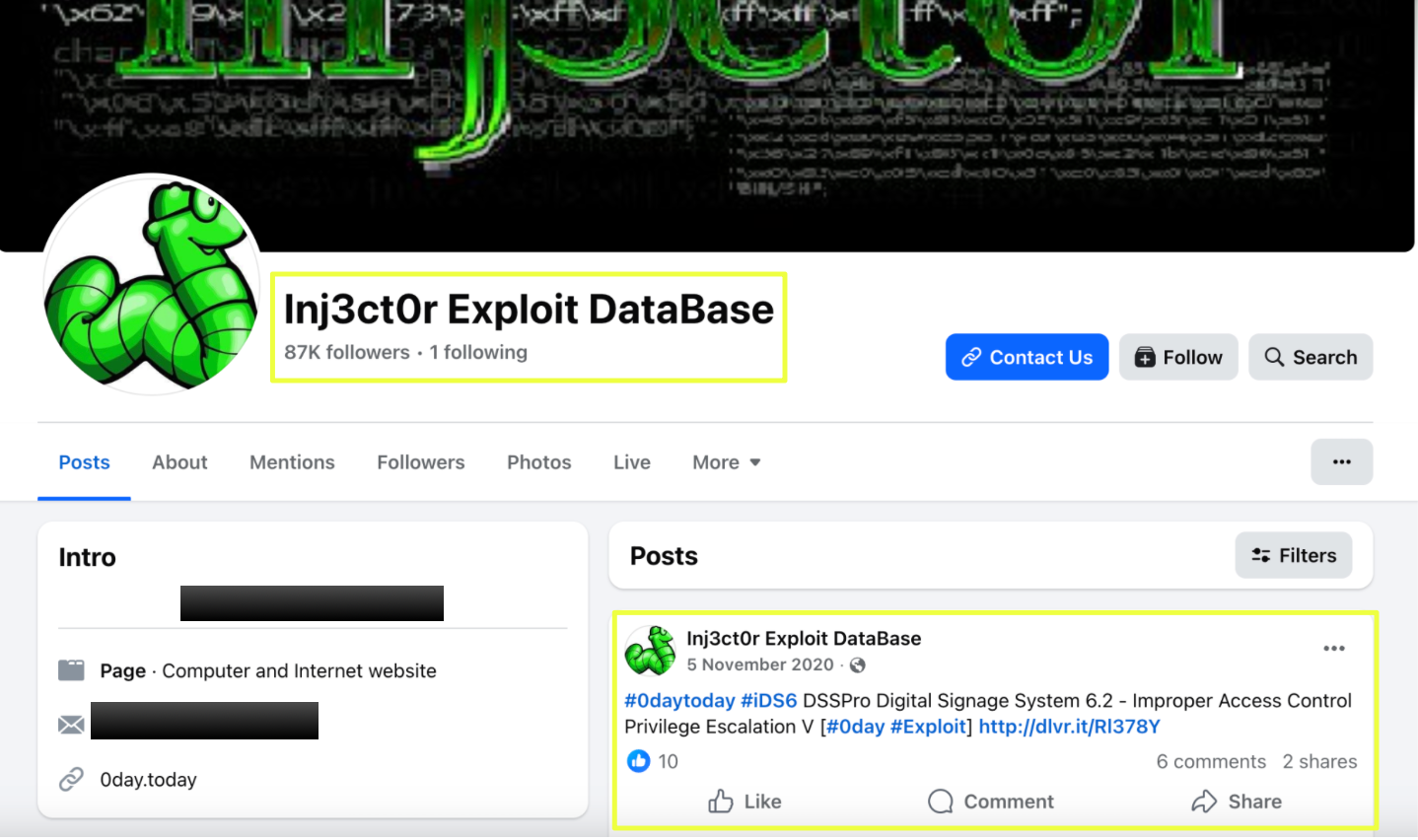
External accounts tied to 0day.today show a similar pattern of dormancy rather than deletion. Both the Twitter profile (@inj3ct0r) and the Facebook page (Inj3ct0r Exploit Database) remain publicly accessible, continue to list mr.inj*******r@gmail.com as a contact point, and retain branding consistent with the original platform. Yet activity on these channels effectively stopped years ago: the last Facebook post dates to 2020, and the Twitter account’s final message in March 2022 featured non-operational content rather than platform updates. User comments on Facebook further imply service disruption, with at least one complaint indicating payment was taken without deliverables. These signals align with the overall picture of an abandoned or minimally maintained service rather than an active exploit marketplace.
StealthMole’s exposure datasets reinforce this interpretation. Queries for 0day.today resulted in 544 records in the Compromised Data Set and 508 records in the ULP Binder, primarily reflecting leaked user credentials associated with registration or login endpoints such as https://0day.today/reg and /auth. Additionally, the email mr.inj3ct0r@gmail.com, repeatedly cited across legacy platform pages and operator profiles, appeared in thousands of leaked entries, 4,757 in Combo Binder and 2,567 in Credential Lookout. The scale of these exposures suggest that accounts linked to the historical platform’s operator have been widely compromised, further diminishing the likelihood of a functioning administrative presence.
0day.today continues to circulate in community spaces where exploit-related content is discussed. The platform’s TOR mirror mvfjfugdwgc5uwho.onion was referenced in dozens of Telegram messages, usually embedded in broad lists of dark web resources rather than in announcements of active services. Mirrors appear on indexing services like OnionTree, sometimes accompanied by cautionary notes flagging scam reports. These references reflect persistence through inertia, the platform survives in collective memory and archival lists, even if its operational status no longer matches its historical reputation.
- curaj33verawgaddbsdsrzc5krmopfyqnei66io5ldhqwdiqukt4vcyd.onion
Taken together, the evidence points to a platform that is no longer operational in any consistent or reliable sense, yet remains partially online due to remnants of its original infrastructure and the enduring circulation of its identifiers. The hybrid state, abandoned accounts, leaked credentials, an overwritten homepage, and surviving internal pages, suggests that 0day.today’s legacy footprint is being passively preserved by various web layers rather than actively maintained by its former operators. Subsequent sections build on this assessment, mapping how these observed signals intersect and what they collectively imply about the platform’s current standing in the exploit ecosystem.
Conclusion
The fragmented state of 0day.today offered a reminder of how difficult it can be to interpret legacy infrastructure in the cybersecurity ecosystem. What appeared at first glance to be a single platform instead revealed multiple layers of historical residue: surviving mirrors, dormant branding, abandoned operator accounts, and a main domain that no longer reflects its original purpose. Rather than pointing to an active marketplace or coordinated threat operation, the investigation ultimately highlighted how long a service’s digital footprint can continue to surface even when its core function has deteriorated or disappeared entirely.
By tracing these remnants through StealthMole, the investigation demonstrated the value of evidence-driven mapping in situations where narratives, assumptions, and community memory can easily overshadow verifiable facts. Each dataset, Telegram references, onion mirrors, old submissions, leaked credentials, contributed a different angle, not to reconstruct a thriving ecosystem but to understand how the platform continues to echo across the surface, deep, and dark web long after its period of relevance.
In that sense, the significance of this case lies less in the operational status of 0day.today and more in the methodology used to untangle it. Platforms with long histories often leave behind sprawling, inconsistent trails, and distinguishing between what is active, what is abandoned, and what is simply repurposed requires a structured, cross-source approach.
Editorial Note
Investigations into legacy cyber platforms rarely yield clean narratives, and 0day.today was no exception. Instead of a definitive answer about what the platform “is,” the process revealed how complex and uneven the digital remains of long-running services can be. This report reflects an evidence-first approach, acknowledging that visibility across surface, deep, and dark web sources is always partial and inherently shaped by what still exists, what has decayed, and what communities continue to circulate. While the findings map the observable footprint of 0day.today as it stands today, they should be understood as a snapshot rather than a final judgment: an illustration of how open-source intelligence can clarify, but not always conclusively resolve, the shifting identities of platforms with long and tangled histories.
To access the unmasked report or full details, please reach out to us separately.
Contact us: support@stealthmole.com

.svg)
.svg)
.svg)