WeTheNorth Marketplace: Credential Exposure in a Fragmented Ecosystem
WeTheNorth is a Canada-focused marketplace operating within the dark web economy, built around a deliberately regional identity. First appearing in 2021, the platform takes its name from the well-known Toronto Raptors slogan “We The North,” a branding choice that reinforces its domestic focus and cultural familiarity. As several established marketplaces disappeared through takedowns or exits, WeTheNorth positioned itself as a local alternative: quiet, controlled, and intentionally insulated.
The marketplace follows the standard operating model of modern dark web platforms. Escrow-based transactions, vendor reputation systems, and PGP-secured communications form the backbone of its operations, with cryptocurrency payments facilitating trade. Access is explicitly restricted to Canadian citizens and residents, a rule repeatedly emphasized across the platform and framed as a trust and security measure rather than a limitation.
This report maps how WeTheNorth exists across different layers of the web, where its presence is consistent, where it fractures, and where it starts to blur into something else entirely. By following those inconsistencies, the investigation reveals a pattern that is less about a single marketplace and more about how dark web brands evolve, replicate, and sometimes lose control of their own identity.
What emerges is not just a story about WeTheNorth, but about how dark web markets are increasingly surrounded by look-alikes, shadow infrastructure, and secondary actors and how users are often left navigating that landscape with far less certainty than they realize.
Incident Trigger & Initial Investigation
The investigation did not begin with a breach, a takedown, or a sudden surge in attention. Instead, it started quietly, during routine monitoring of active marketplaces that maintain a long-term presence within the dark web economy. Among those, WeTheNorth appeared largely unchanged at first glance: still active, still visible, and still operating under the same regional framing it had used for years.
- hn2paw**********************************************bid.onion
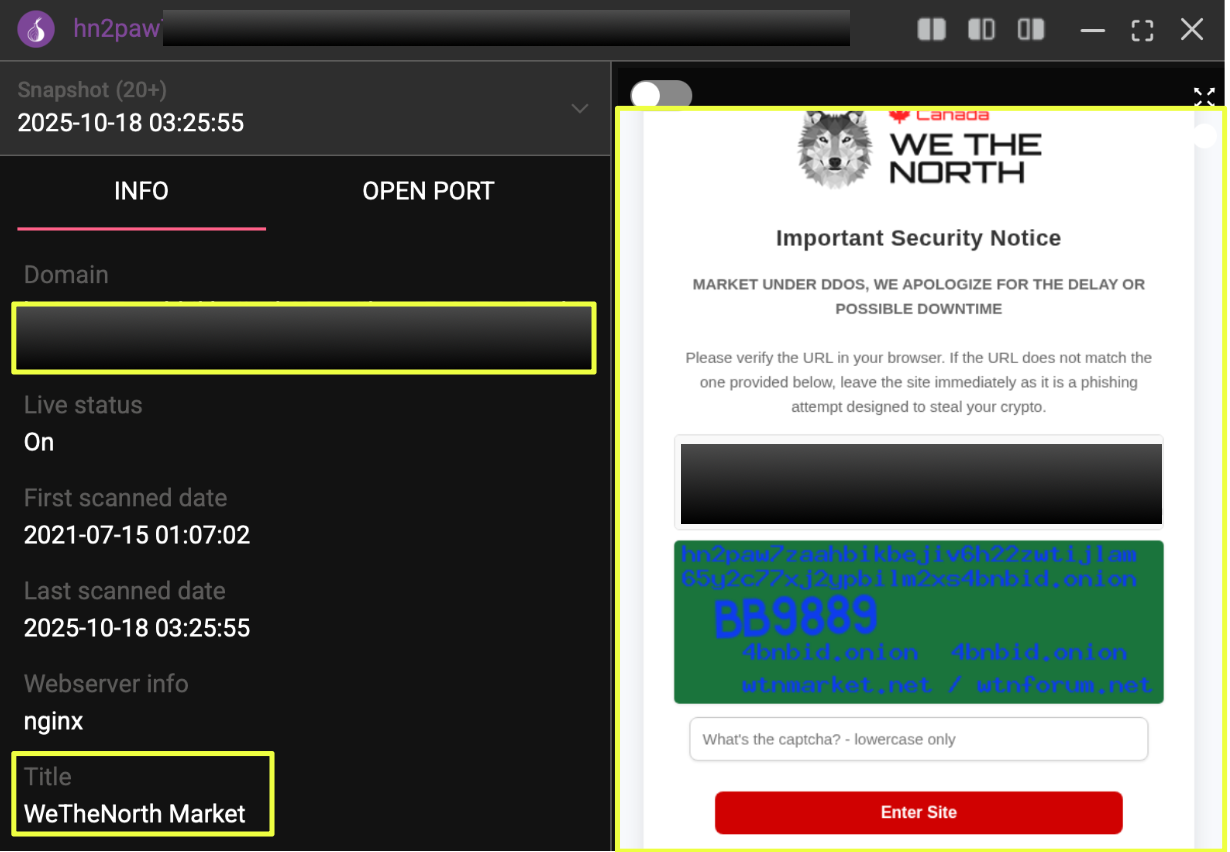
What drew attention was not the marketplace itself, but how it presented at the moment it was encountered. Rather than a standard landing page, the primary access point displayed a notice referencing service being under DDoS attack. Messages like these are common enough across darknet platforms to avoid immediate alarm, but in this case, the framing was deliberate. The site emphasized continuity and control, suggesting that access was being managed rather than lost.
Before expanding the scope of the inquiry, the initial focus remained narrow. The goal was simply to confirm whether the observed access point reflected a legitimate, long-standing service or a temporary stand-in. Historical visibility indicated persistence going back several years, aligning with WeTheNorth’s broader timeline and reducing the likelihood of a short-lived imitation.
At the same time, elements beneath the surface suggested the platform remained operational. Core access mechanisms were still present, and the marketplace’s defining characteristics: restricted access, emphasis on operational security, and clear boundary-setting around its user base, were reinforced rather than relaxed. Nothing at this stage pointed to disruption in the traditional sense.
It was only when references to the platform began appearing outside of this expected entry point that the investigation widened. What initially seemed like a momentary operational issue became a prompt to look more closely at how WeTheNorth was being represented, accessed, and reused across different environments and whether the boundaries it sought to enforce were holding as firmly as intended.
Operational Model and Platform Services
At its core, WeTheNorth operates as a full-service darknet marketplace built around a tightly controlled transactional environment. The platform follows a conventional but deliberate design philosophy, prioritizing predictability over scale and containment over openness. From the first entry, users are guided into a structured ecosystem where almost every interaction is mediated by the market itself.
The marketplace offers a wide range of listings across multiple categories, with the most prominent activity concentrated around drugs and chemicals. These listings are presented alongside clearly defined pricing in Canadian dollars, with cryptocurrency equivalents calculated at the point of purchase. The emphasis on CAD pricing reinforces the platform’s domestic orientation and distinguishes it from markets that default to USD or BTC-only models.
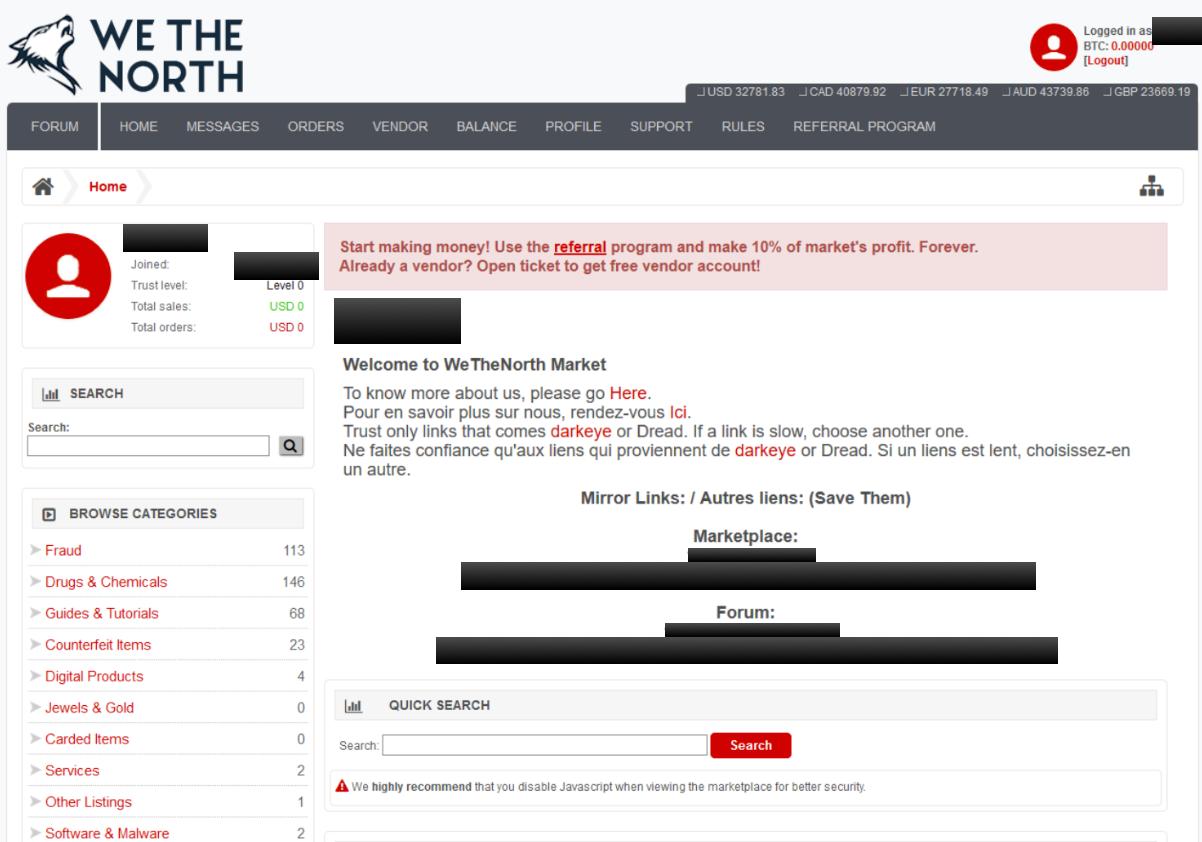
Beyond physical goods, WeTheNorth also supports digital offerings. Categories related to software, malware, and guides are visible within the platform, alongside sections dedicated to fraud-related services. In addition, a separate credit card autoshop operates within the same environment, allowing users to browse structured datasets filtered by province, city, and data completeness. This autoshop functions differently from the main marketplace, notably operating without escrow and placing responsibility on buyers to assess vendor credibility.
From a transactional standpoint, WeTheNorth relies on cryptocurrency payments to facilitate trade. Bitcoin and Monero are supported, aligning with common practices across contemporary darknet markets. Escrow services are central to the platform’s design and are positioned as a primary trust mechanism between buyers and vendors. Funds are held by the marketplace until orders are finalized, with automated finalization timelines applied differently to digital and physical goods.
Vendor participation is gated through a formal onboarding process. Sellers are required to activate vendor accounts by posting a bond, intended to deter low-effort scams and disposable identities. Once approved, vendors are subject to a detailed rule set governing listing accuracy, prohibited items, and communication practices. Enforcement is framed as strict and immediate, with repeated references to account suspension or permanent bans for violations.
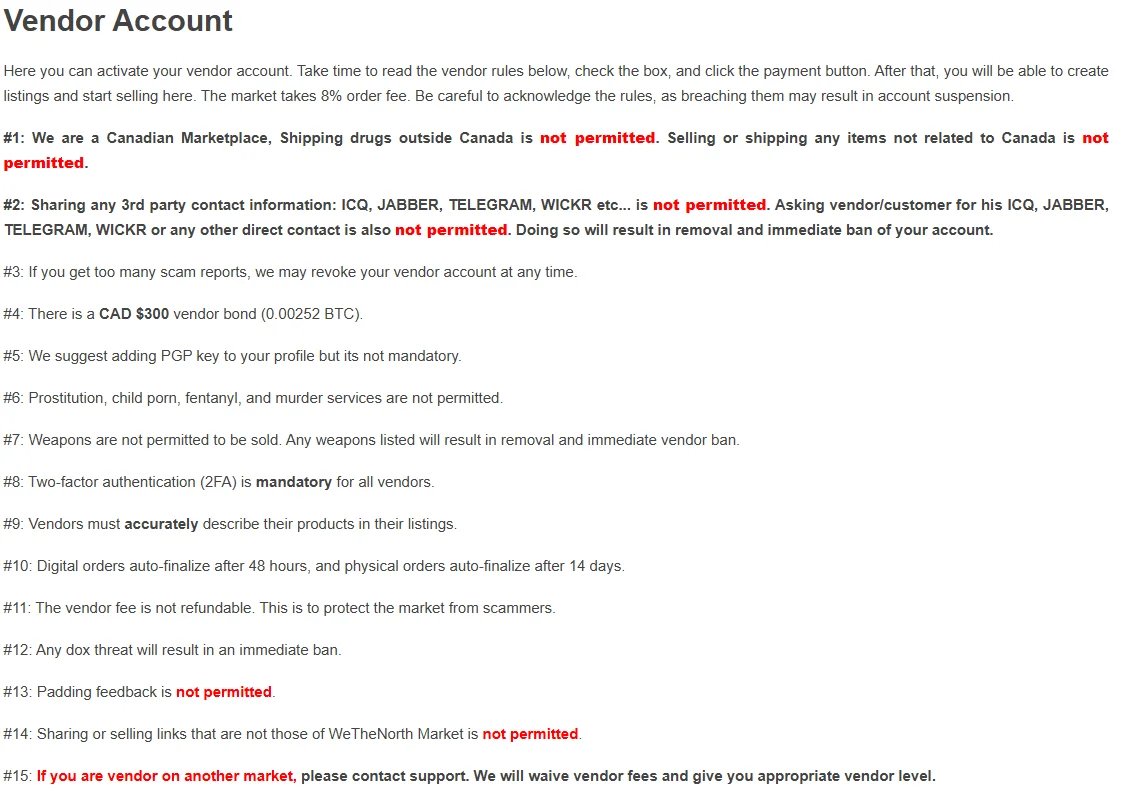
Security controls are embedded throughout the platform. PGP encryption is strongly encouraged for user communications, and two-factor authentication is mandatory for vendors. The marketplace repeatedly emphasizes its no-logs policy and positions anonymity as a foundational principle rather than an optional feature. Support services are available through an internal ticketing system, reinforcing the platform’s preference for keeping all interactions contained within its own infrastructure.
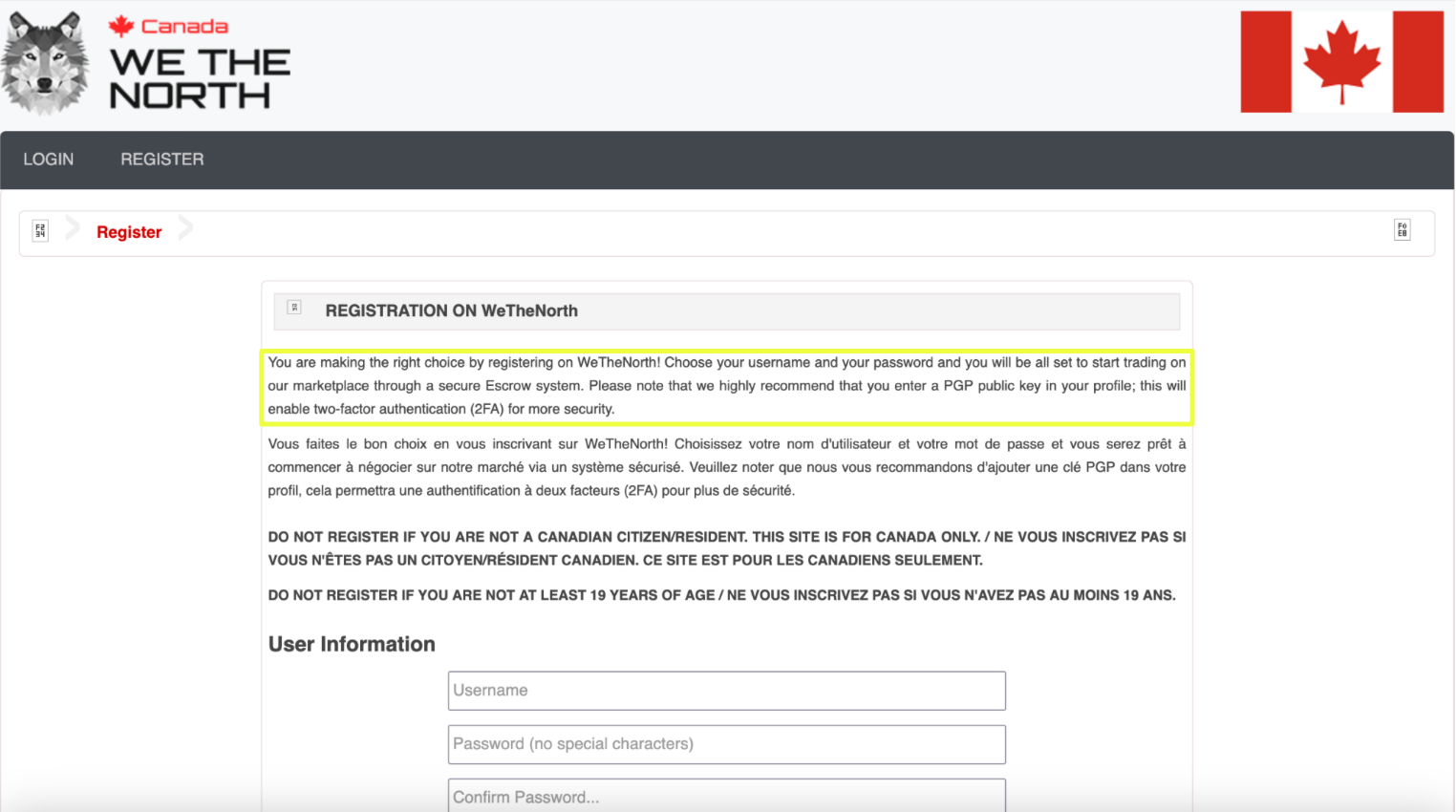
Taken together, these elements present WeTheNorth as a marketplace designed to appear disciplined, self-contained, and risk-aware. The services it offers, the rules it enforces, and the boundaries it draws all point toward a platform that values control over growth. At this stage, everything about the infrastructure suggests coherence, a market that knows what it wants to be and how it intends to operate.
Official Domains and Access Structure
The next step in the investigation was to understand how WeTheNorth presents itself beyond its primary marketplace interface. Rather than limiting its presence to a single Tor address, the platform maintains multiple publicly accessible domains that mirror the same content and structure.
At the time of observation, WeTheNorth explicitly referenced a total of four official access points: three on the surface web and one on the dark web.
The surface web domains included:
- w*****t.net
- w***.****et
- w*****m.net
Alongside these, a single Tor service was presented as the primary dark web access point:
- hn2paw7************************************************bid.onion
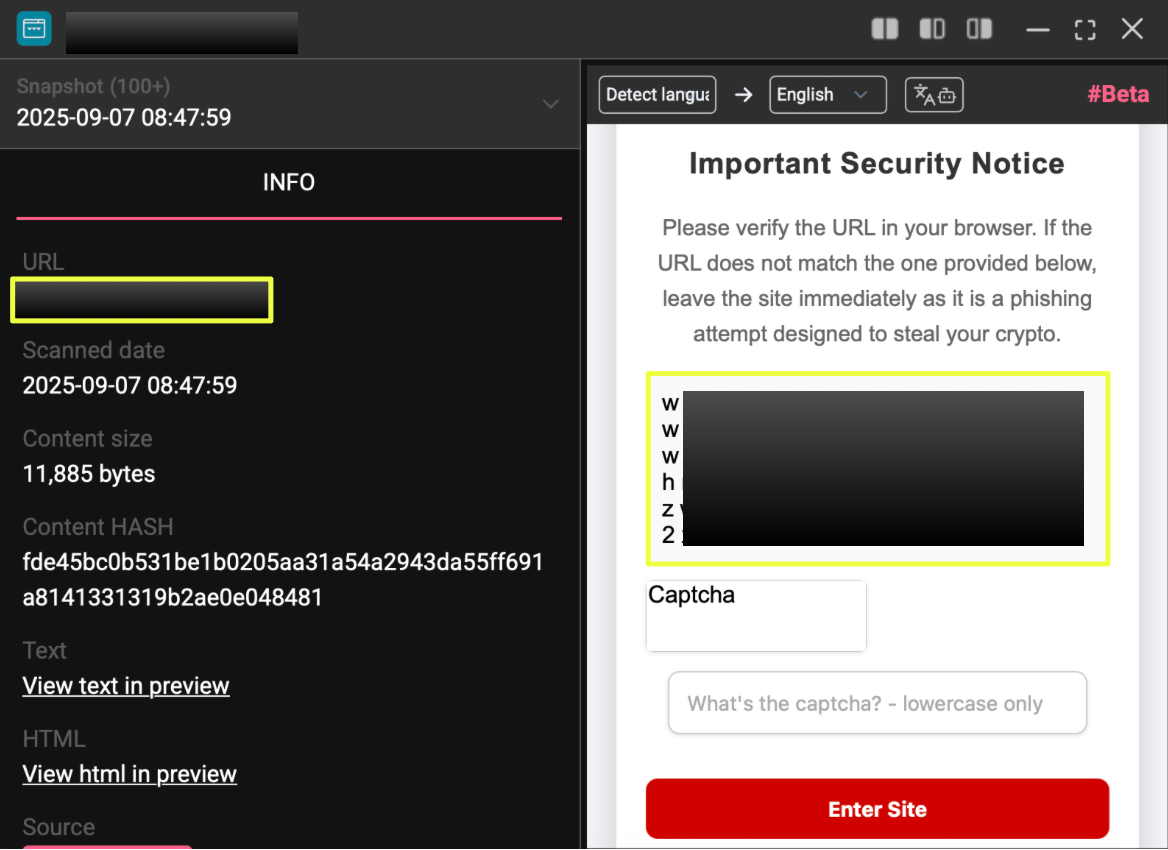
What stood out immediately was the lack of functional distinction between these environments. The surface web domains were not simplified landing pages or redirect-only portals. Instead, they displayed the same interface, layout, and messaging as the Tor service, including the marketplace’s operational notices, access warnings, and entry controls.
At the time of discovery, all four domains presented identical content, including a notice indicating service disruption attributed to a DDoS attack. The message was consistent across environments, listing the same set of access points and reinforcing the idea that these domains were intended to be interchangeable rather than hierarchical.
This approach differs from many darknet marketplaces that restrict full functionality to Tor while using surface domains only as reference points. In WeTheNorth’s case, the boundary between surface and dark web presence appeared intentionally thin, with the same branding and structure replicated across all officially listed domains.
Unlisted Domains and Emerging Look-Alike Infrastructure
After establishing the set of domains explicitly presented as official, the investigation turned to identifying whether the same branding and structure appeared elsewhere. This step was not driven by speculation, but by inconsistencies observed during routine pivots from the known surface web domains.
While expanding from w*********8t.net, multiple additional Tor services surfaced that closely resembled the WeTheNorth marketplace:
- hup**************************************************vad.onion
- hn2**************************************************4ad.onion
- crr**************************************************syd.onion
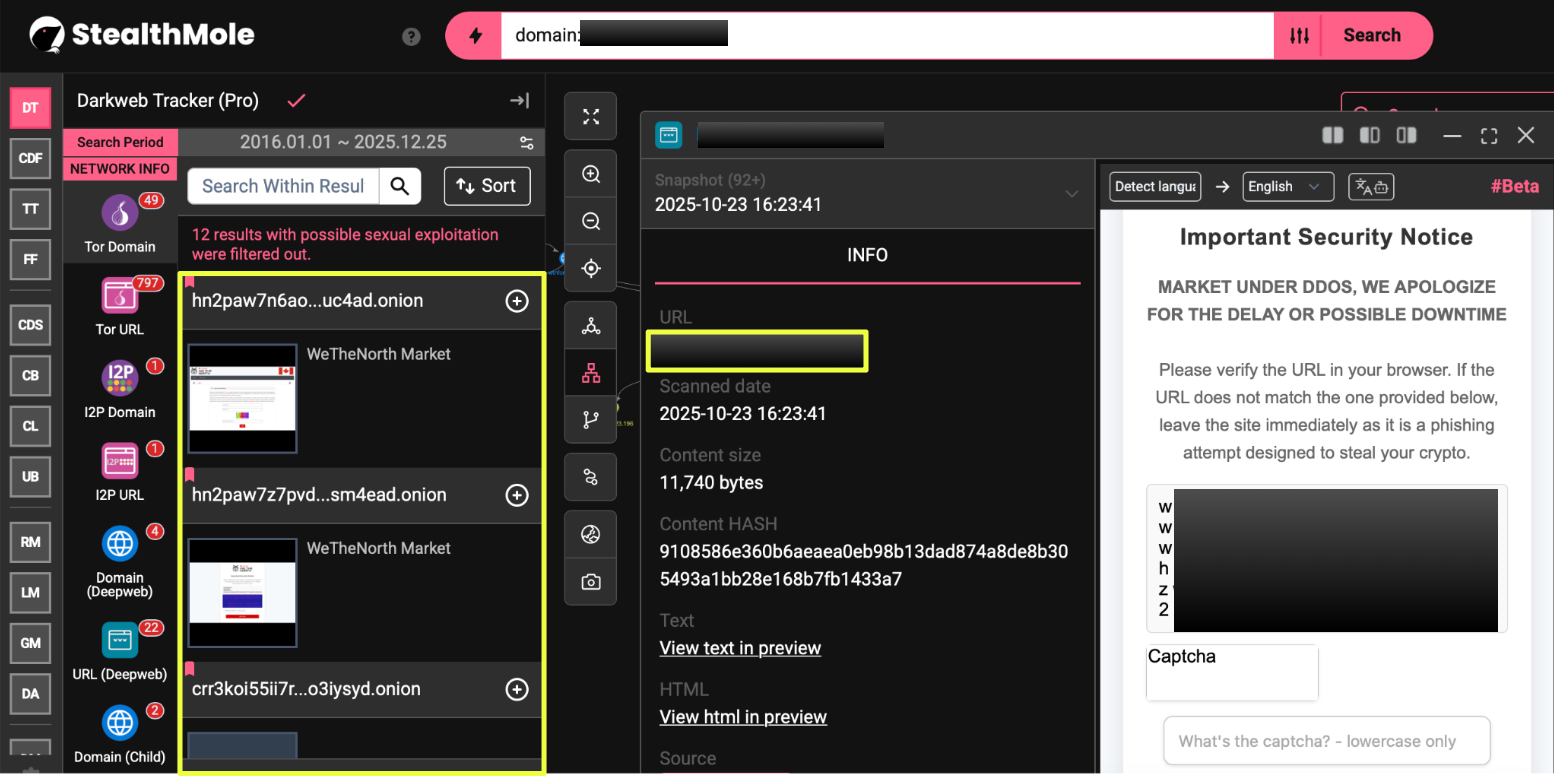
These addresses presented pages that were visually indistinguishable from the officially listed WeTheNorth domains. The layout, language, security notices, and access controls matched what was observed on the endorsed surface and dark web sites. Registration pages were present, and the same Canada-focused framing and operational messaging appeared intact.
What made these domains notable was not their appearance, but their absence. Neither address was referenced on any of the four domains publicly listed by the marketplace. No warnings, acknowledgements, or verification indicators tied them back to the official infrastructure.
As the investigation continued, a fourth unlisted Tor address was identified through a separate dark web post:
- hn2paw7z7pvdmnxng3d2khs4uk3trxzffyl5wldi7wmgd45tuusm4ead.onion
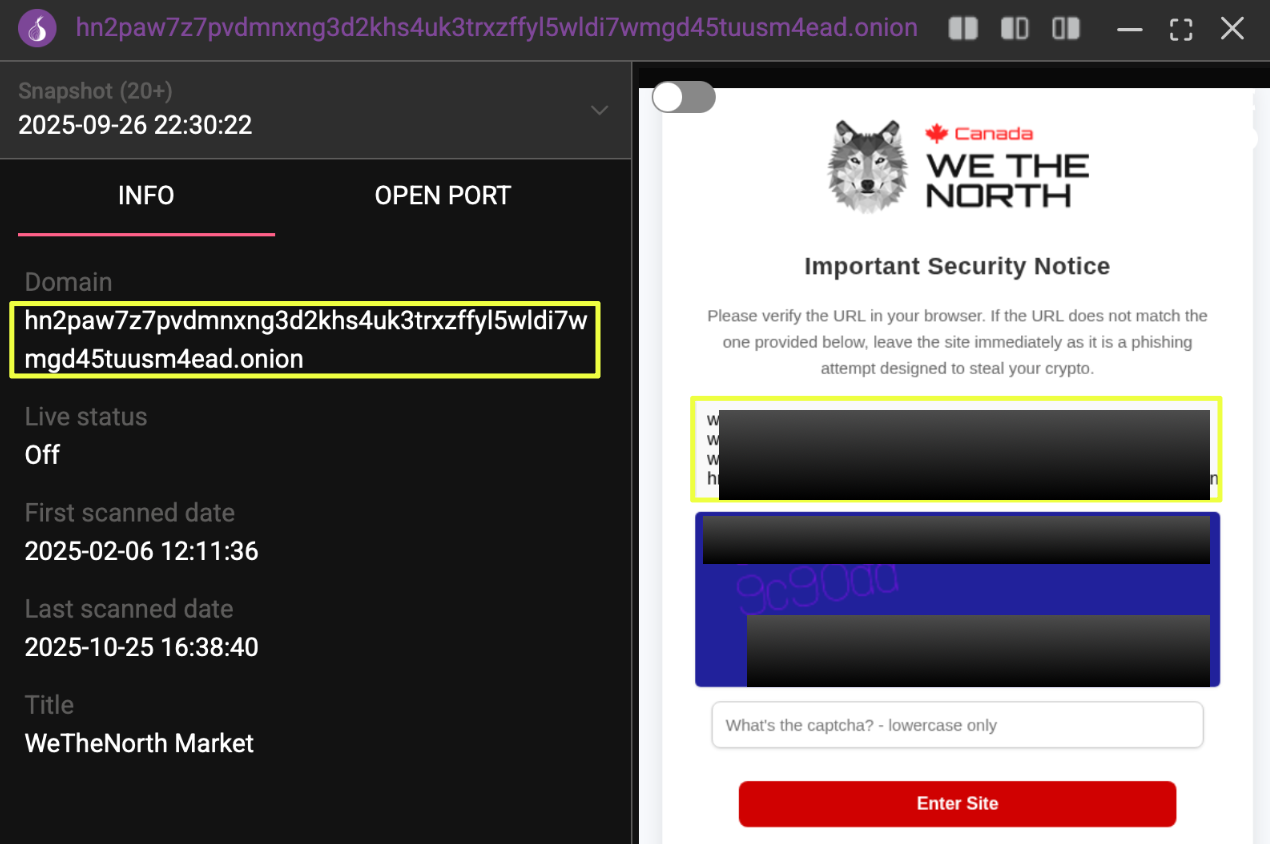
This domain followed the same pattern. It replicated the marketplace interface and included a posted PGP key, further reinforcing the appearance of legitimacy. However, like the earlier discoveries, it was not included in the platform’s published access list.
Whether these domains were abandoned mirrors, unauthorized clones, or deliberate impersonation could not be determined immediately. What was clear, however, was that the marketplace’s identity extended beyond the boundaries it claimed to enforce.
Telegram and Dark Web Forum Mentions
As the investigation moved beyond direct access points, references to WeTheNorth began appearing in third-party spaces where darknet platforms are commonly discussed, cataloged, and redistributed. These mentions did not originate from official market channels, but from external communities that function as discovery layers for users navigating the dark web ecosystem.
On Telegram, multiple channels known for aggregating darknet links and marketplace advertisements contained posts referencing WeTheNorth. These posts typically shared a single access link accompanied by brief descriptive text, positioning the platform alongside other active markets. The framing varied by channel, but consistently treated WeTheNorth as an established marketplace rather than a new or experimental entrant.
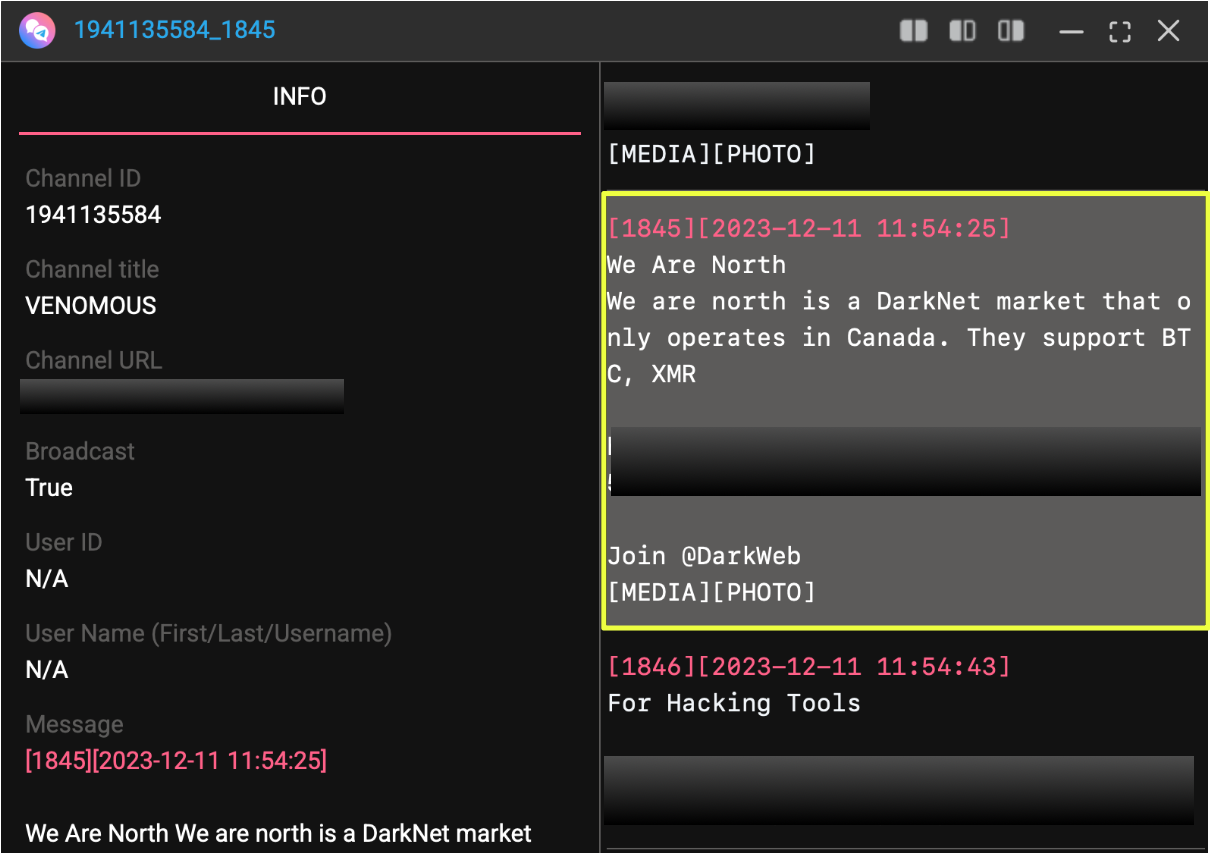
One Telegram channel, VENOMOUS, included a post describing the platform as Canada-focused and claimed that it supported Bitcoin and Monero payments. Notably, these claims were not accompanied by wallet addresses or deposit instructions, and no such payment details were publicly visible on the marketplace pages observed during this investigation. As such, the payment references are best understood as third-party descriptions rather than verified platform disclosures.
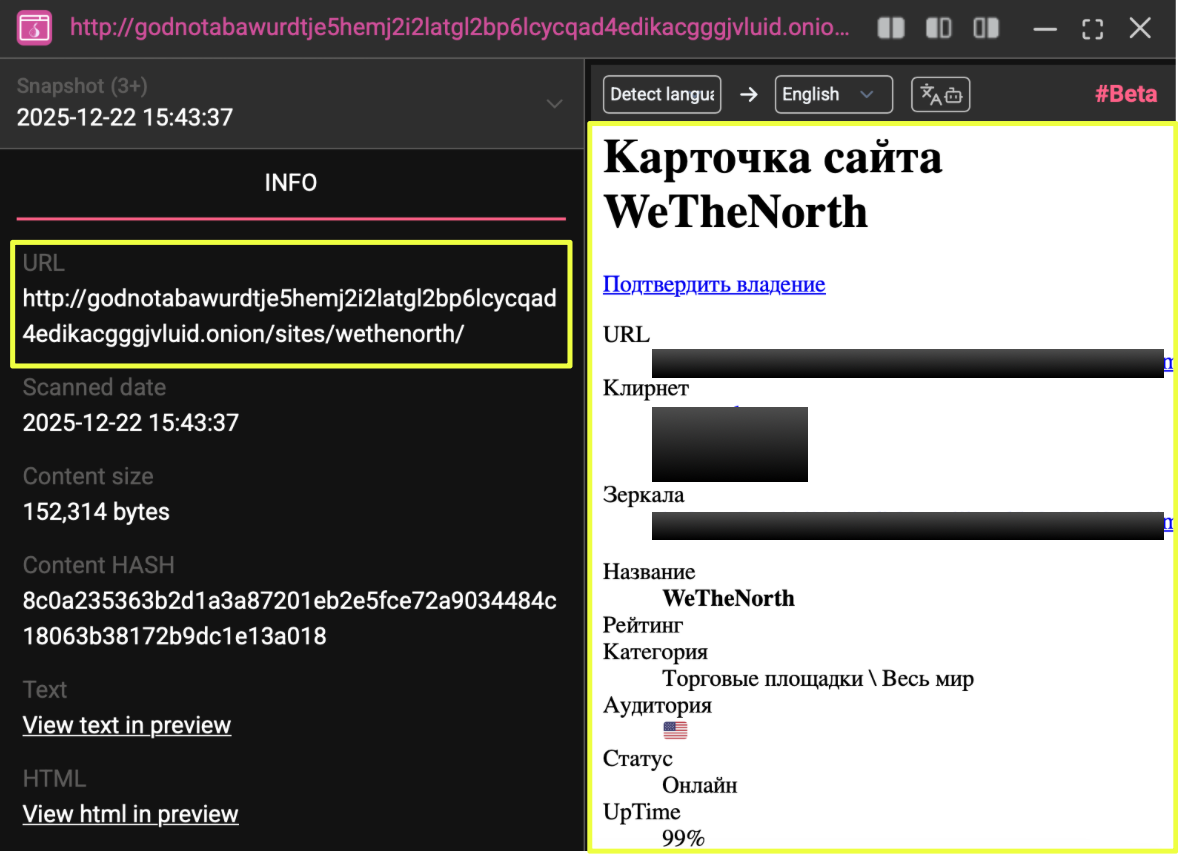
In parallel, a Russian-language dark web site hosting marketplace indexes and discussion threads also contained a dedicated page for WeTheNorth. This page listed access links, summarized platform features, and included user comments discussing availability and performance. The structure and presentation were consistent with a directory or review-style resource rather than an operator-controlled forum.
Across both Telegram and dark web forums, the pattern was consistent: WeTheNorth existed as a name circulating independently of its official infrastructure. Links were reposted, descriptions were paraphrased, and access information was redistributed without context or verification. In these environments, the distinction between endorsed entry points and unverified ones was largely absent.
Credential Exposure and User Risk
As references to WeTheNorth continued to surface across external channels, the investigation shifted toward understanding whether this visibility translated into measurable user exposure. Rather than looking for signs of direct compromise, the focus was placed on whether credentials associated with the platform were appearing in underground datasets commonly linked to malware infections and credential harvesting.
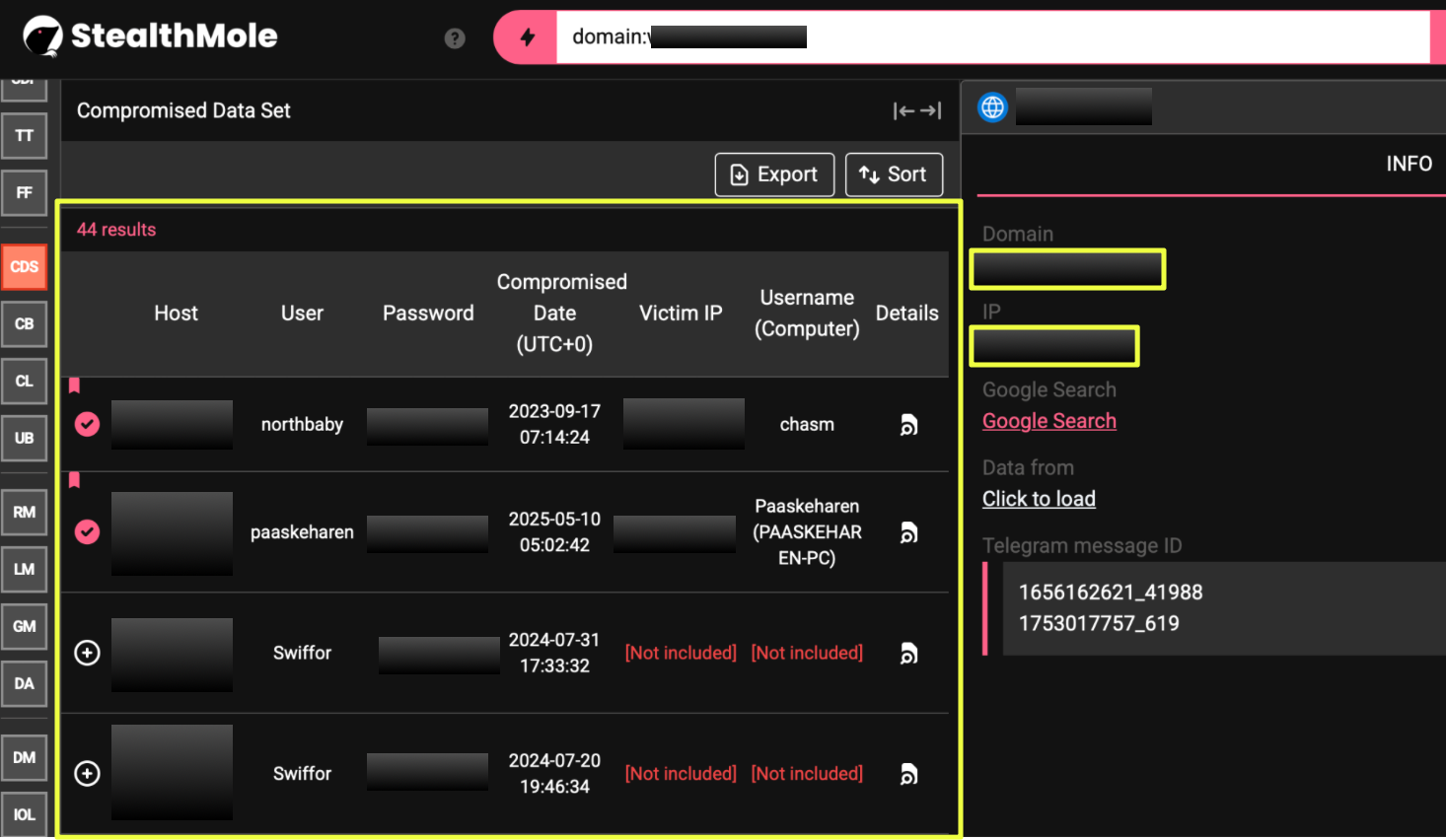
Using StealthMole’s Compromised Data Set (CDS), the surface domain w*******t.net was examined for evidence of leaked user credentials. This query returned 140 distinct credential records associated with the domain. The entries reflected typical stealer-log characteristics, including combinations of usernames, plaintext passwords, and victim-side metadata, rather than structured database exports.
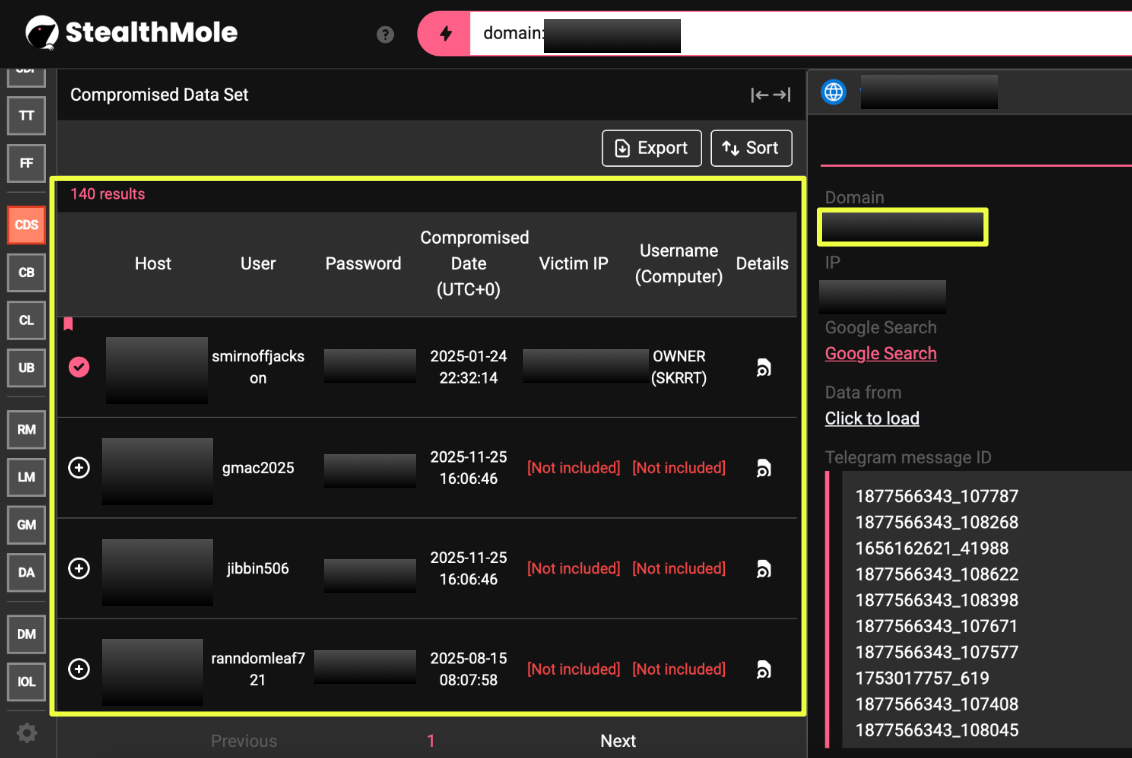
To validate whether this exposure was isolated or part of a broader pattern, the same domain was subsequently analyzed using StealthMole’s ULP Binder. This produced an additional 161 credential records, reinforcing that the presence of WeTheNorth-related credentials was not confined to a single dataset or collection method.
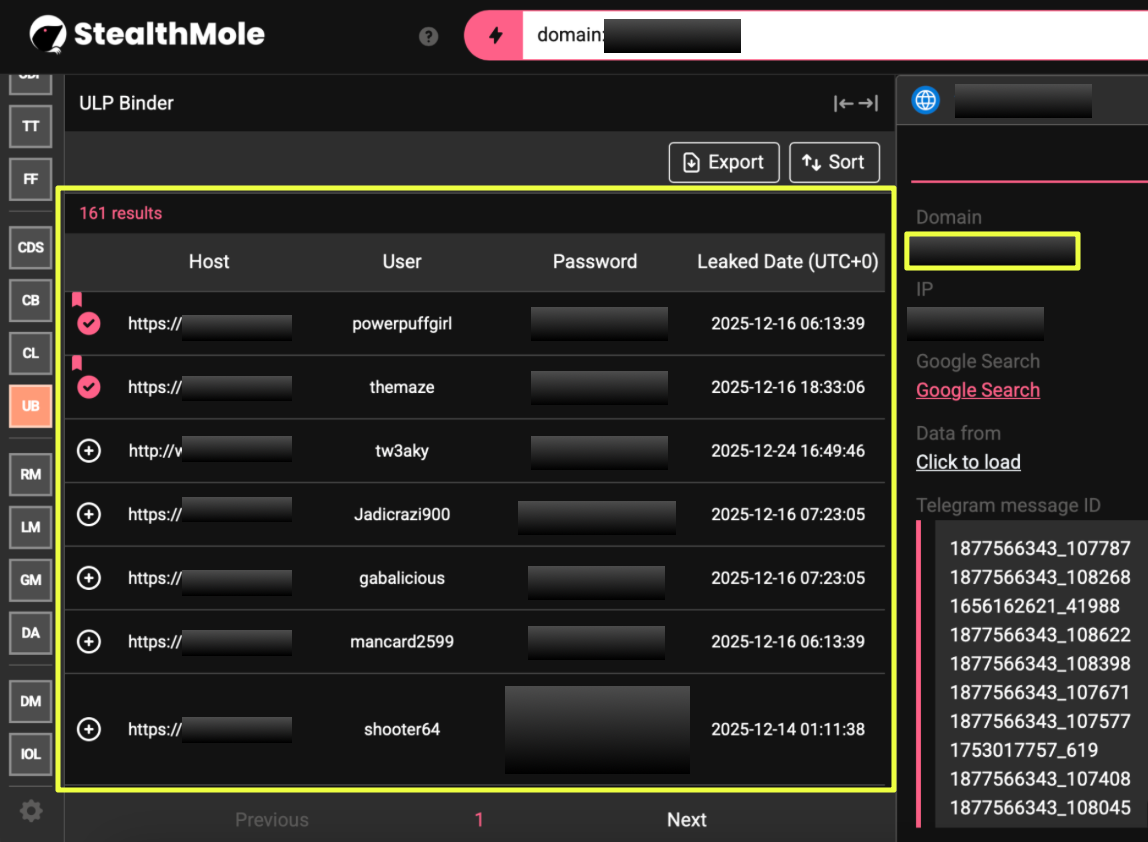
A similar pattern emerged when the forum domain w*******m.net was examined. Running this domain through CDS returned 44 credential records, again consistent with user-side compromise rather than platform-level intrusion. The distribution of victim IPs and timestamps suggested infections occurring across different environments, rather than a centralized breach event.
Infrastructure Signals and Hosting Context
With credential exposure established across multiple surface domains, the investigation next examined whether those domains shared any observable infrastructure characteristics. This step was intended to provide technical context, not to infer ownership or operational control.
The surface domain w*********t.net was observed resolving to the IP address 31.*1.**4.1*4, geolocated to Russia. This IP surfaced during analysis of compromised credentials and was later used as a pivot point for identifying related external references. No evidence was found indicating that this address functioned as a backend marketplace server; rather, it appeared consistent with surface-facing hosting commonly used for mirrors or access layers.
A similar pattern emerged when examining w*******m.net, which resolved to a separate IP address, 1**.*.*9.*9, also geolocated to Russia. This domain, while distinct in function from the main market interface, showed the same exposure profile when analyzed through compromised credential datasets.
The use of Russian-hosted infrastructure across multiple surface domains provides contextual insight but does not, on its own, support conclusions about operator identity or geographic origin. Commercial hosting, reverse proxies, and intermediary infrastructure are frequently employed by darknet platforms to separate public-facing services from core operations.
Conclusion
WeTheNorth presents itself as structured, selective, and security-conscious, yet its presence extends well beyond the boundaries it publicly defines. Once a market’s name and interface begin circulating independently, authority over what is “official” becomes increasingly fragile.
The emergence of multiple unlisted, visually identical domains shows how easily a trusted brand can be replicated in the dark web ecosystem. Whether these domains represent abandoned mirrors, unauthorized clones, or deliberate impersonation is ultimately secondary to their impact. From a user’s perspective, indistinguishable access points collapse trust distinctions, making even careful operational behavior insufficient to guarantee safety.
Credential exposure tied to WeTheNorth-associated domains reinforces this risk. The data does not suggest a direct compromise of the marketplace itself, but it does demonstrate how users operating within a fragmented access environment become vulnerable through malware, credential reuse, or interaction with unverified endpoints. In this context, exposure is not the result of a single failure, but of cumulative friction between visibility, imitation, and user behavior.
Taken together, this case highlights a structural challenge facing modern darknet markets. As platforms seek persistence and resilience through redundancy and visibility, they also expand the surface on which control can be lost. WeTheNorth’s trajectory shows how quickly a market can move from being a defined destination to a dispersed identity and how, in that transition, risk shifts away from infrastructure and toward the users navigating it.
Editorial Note
As with all darkweb investigations, the findings in this report represent only what could be observed and correlated at the time of analysis. Marketplace infrastructure, impersonator networks, and affiliated communication channels frequently shift, disappear, or re-emerge under new identifiers, and visibility into hidden services is inherently partial.
The conclusions presented here reflect a snapshot of WeTheNorth-linked activity based solely on verifiable domains, timestamps, and artefacts surfaced through StealthMole’s tracking capabilities. The aim is not to capture every possible branch of this ecosystem, but to demonstrate how structured, evidence-based analysis can reveal meaningful patterns within environments that are, by design, unstable and continuously evolving.
Labels: Darkweb Marketplace, Featured

.svg)
.svg)
.svg)